- Home
- Forescout
- Forescout Certified Professional
- FSCP
- FSCP - Forescout Certified Professional Exam
Forescout FSCP Forescout Certified Professional Exam Exam Practice Test
Forescout Certified Professional Exam Questions and Answers
How can scripts be run when the Endpoint Remote Inspection method is set to "Using MS-WMI"?
Options:
Using Task Scheduler but this has limitations
Using WMI, which will allow interactive scripts to run
Using RRP, which will allow interactive scripts to run
Using WMI, but they may not be run interactively using this method
Using fsprocserv.exe, but scripts may not be run interactively using this method
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout CounterACT HPS Inspection Engine Configuration Guide Version 10.8, when the Endpoint Remote Inspection method is set to "Using MS-WMI," scripts are run using WMI, but they may not be run interactively using this method.
MS-WMI Script Execution:
According to the HPS Inspection Engine guide:
"When Remote Inspection uses MS-WMI, run scripts with
MS-WMI – note that interactive scripts are not supported by WMI on all Windows endpoints. Functionality that relies on interactive endpoint scripts is not implemented when you choose this option. For example, the Start Antivirus and Update Antivirus actions require interactive scripts to manage some antivirus packages."
Interactive Script Limitations with WMI:
According to the documentation:
"WMI does not support interactive scripts (such as scripts that support Guest Registration and other HTTP-based actions) on some Windows endpoints."
How WMI Scripts Are Run:
According to the documentation:
When using WMI for script execution:
Background Scripts - Most background scripts can run via WMI
Interactive Scripts - NOT supported by WMI on all endpoints
Workaround for Interactive Scripts - CounterACT uses:
fsprocsvc service (fsprocsvc.exe) - For interactive script support
Microsoft Task Scheduler - Alternative for interactive scripts
WMI vs. Other Methods:
According to the documentation:
Method
Interactive Scripts
Limitations
MS-WMI
Not supported on all endpoints
Limited to background scripts
fsprocsvc
Supported
Service must be running
Task Scheduler
Not on Vista/7
Legacy OS limitations
Script Execution Flow with MS-WMI:
According to the documentation:
"CounterACT runs most background scripts using WMI. WMI does not support interactive scripts (such as scripts that support Guest Registration and other HTTP-based actions) on some Windows endpoints. CounterACT uses the fsprocsvc service or Microsoft Task Scheduler to run interactive scripts on these endpoints."
Why Other Options Are Incorrect:
A. Using Task Scheduler but with limitations - Task Scheduler is an ALTERNATIVE to WMI, not what MS-WMI uses
B. Using WMI, which will allow interactive scripts - Incorrect; WMI does NOT allow interactive scripts
C. Using RRP, which will allow interactive scripts - RRP is Remote Registry Protocol, not the script execution method with MS-WMI
E. Using fsprocserv.exe, but scripts may not be run interactively - fsprocserv.exe (fsprocsvc) DOES support interactive scripts; it's used as an alternative to overcome WMI limitations
Referenced Documentation:
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide v10.8 - Script Execution Services section
When Remote Inspection uses MS-WMI, run scripts with
About MS-WMI
What is the command to monitor system memory and CPU load with 5 second update intervals?
Options:
watch -t 5 vmstat
vmstat 5
vmstat -t 5
watch uptime
watch -n 10 vmstat
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
The correct command to monitor system memory and CPU load with 5 second update intervals is vmstat 5. According to the official Linux documentation and Forescout CLI reference materials, the vmstat command uses a straightforward syntax where the first numerical parameter specifies the delay interval in seconds.
vmstat Command Syntax:
The vmstat (Virtual Memory Statistics) command uses the following syntax:
bash
vmstat [options] [delay] [count]
Where:
delay - The time interval (in seconds) between updates
count - The number of updates to display (optional; if omitted, displays indefinitely)
vmstat 5 Command:
When you execute vmstat 5:
Updates are displayed every 5 seconds
Continues indefinitely until manually stopped
Shows memory and CPU statistics in each update
Example output:
text
procs -----------memory---------- ---swap-- -----io---- -system-- ------cpu-----
r b swpd free buff cache si so bi bo in cs us sy id wa st
1 0 0 1166396 70768 2233228 0 0 0 13 10 24 0 0 100 0 0
0 0 0 1165568 70776 2233352 0 0 0 8 121 224 0 0 99 0 0
0 0 0 1166608 70784 2233352 0 0 0 53 108 209 0 0 100 0 0
Each line represents a new report generated at 5-second intervals.
Memory and CPU Information Provided:
The vmstat output includes:
Memory Columns:
free - Amount of idle memory
buff - Amount of memory used as buffers
cache - Amount of memory used as cache
swpd - Amount of virtual memory used
si/so - Memory swapped in/out
CPU Columns:
us - Time spent running user code
sy - Time spent running kernel code
id - Time spent idle
wa - Time spent waiting for I/O
st - Time stolen from virtual machine
Why Other Options Are Incorrect:
A. watch -t 5 vmstat - Incorrect syntax; -t removes headers, not set intervals; interval flag is -n, not -t
C. vmstat -t 5 - The -t option adds a timestamp to output, but doesn't set the interval; the 5 would be ignored
D. watch uptime - The uptime command displays system uptime and load average but not detailed memory/CPU stats; watch requires -n flag for interval specification
E. watch -n 10 vmstat - While syntactically valid, this uses a 10-second interval, not 5 seconds; also unnecessary since vmstat already supports delay parameter directly
Additional vmstat Examples:
According to documentation:
bash
vmstat 5 5 # Display 5 updates at 5-second intervals
vmstat 1 10 # Display 10 updates at 1-second intervals
vmstat -t 5 5 # Display 5 updates every 5 seconds WITH timestamps
First Report Note:
According to the documentation:
"When you run vmstat without any parameters, it shows system values based on the averages for each element since the server was last rebooted. These results are not a snapshot of current values."
The first report with vmstat 5 shows averages since last reboot; subsequent reports show statistics for each 5-second interval.
Referenced Documentation:
Linux vmstat Command Documentation
RedHat vmstat Command Guide
Oracle Solaris vmstat Manual
Microsoft Azure Linux Troubleshooting Guide
IBM AIX vmstat Documentation
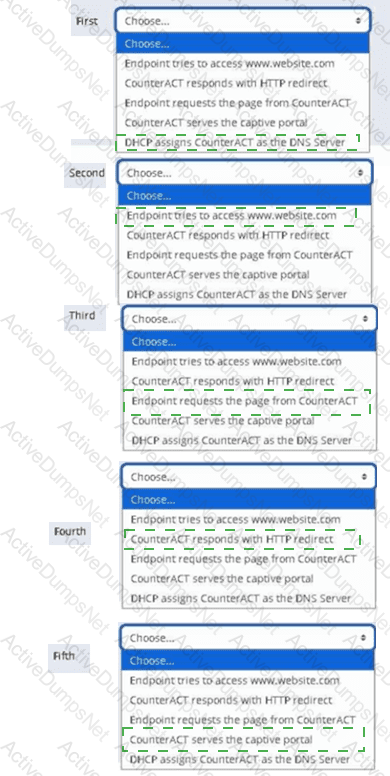
Place the DNS Enforce control actions into the correct workflow order for endpoints which have a pending control action.
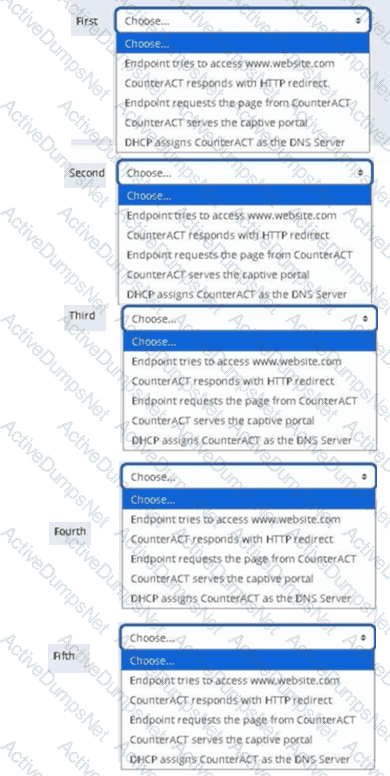
Options:
Answer:
Which of the following is the best way to brand the CounterACT HTTP pages to look like corporate internal web pages?
Options:
Using the "Reports Portal," modify the CSS for the desired skins
This is not possible with CounterACT portal and HTTP pages
Using the "User Portal Builder," modify the CSS for the desired skins
Have a webmaster modify the HTML pages within the Tomcat web server
Using the "User Portal Builder" basic interface
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide, the best way to brand CounterACT HTTP pages to match corporate identity is to use "the 'User Portal Builder' to modify the CSS for the desired skins". This is the officially supported method for customizing the appearance of Forescout portal pages.
User Portal Builder for Branding:
The User Portal Builder provides:
CSS Customization - Modify cascading stylesheets to match corporate branding
Skin Selection - Choose different portal skins/themes
Logo and Colors - Customize logos, color schemes
Supported Customization - Official, supported method through the GUI
Why Option C is Correct:
The User Portal Builder specifically provides CSS modification capabilities to customize the appearance of Forescout HTTP portal pages to match organizational branding standards.
Why Other Options Are Incorrect:
A. Reports Portal - Reports Portal is separate from HTTP portal pages; not for branding
B. Not possible - Customization IS possible through User Portal Builder
D. Modify HTML in Tomcat - While technically possible, this is NOT supported; may break with updates
E. Basic interface only - The full User Portal Builder supports CSS modification, not just basic interface
Supported Customization Methods:
According to the documentation:
✓ User Portal Builder (CSS) - Supported, recommended method
✗ Direct Tomcat HTML modification - Not supported; unsupported method
✗ Manual CSS editing - Unsupported; may conflict with updates
Referenced Documentation:
Forescout Administration Guide - User Portal Builder section
How are additional recipients added to a "Send Mail" action?
Options:
Thru the setting on Tools > Options > General > Mail and adding the recipients separated by commas
Thru the policy "Send Mail" action, under the Parameters tab add the recipients separated by commas
Thru Tools > Options > Advanced - Mail and adding the recipients separated by semi-colons
Thru the Tools > Options > NAC Email and adding the recipients separated by semi-colons
Thru the policy sub rule and adding a condition for each of the desired recipients
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide, additional recipients for the "Send Mail" action are added through the setting on Tools > Options > General > Mail and adding the recipients separated by commas.
Managing Email Notification Addresses:
According to the official documentation:
"From the Tools menu, select Options > General > Mail and DNS. Update any of the following fields: Send Email Alerts/Notifications - List email addresses to receive CounterACT email alerts."
Email Address Separator Options:
According to the documentation:
"Separate multiple addresses using any of the following characters: semicolon (;), blank space or comma (,)."
So while commas are the primary method shown in the documentation, the system also accepts semicolons and spaces as separators. However, the answer that most specifically matches the Forescout documentation interface is Option A.
How to Configure Email Recipients:
According to the administration guide:
Open Tools Menu - Select "Tools" from the menu bar
Select Options - Click on "Options"
Navigate to Mail Settings - Select "General > Mail and DNS"
Add Recipients - Enter email addresses in the "Send Email Alerts/Notifications" field
Separate Multiple Addresses - Use commas, semicolons, or spaces between addresses
Example Recipient Configuration:
According to the documentation:
text
Example 1: user1@example.com,user2@example.com,user3@example.com
Example 2: user1@example.com; user2@example.com; user3@example.com
Policy-Level vs. Global Email Configuration:
According to the documentation:
Global Email Configuration (Tools > Options > General > Mail) - Sets default recipients for all email alerts
Send Email Action (in policy) - Can be configured to send to administrator email or specify alternative recipients
The global configuration in Tools > Options is where the primary recipient list is maintained.
Why Other Options Are Incorrect:
B. Thru the policy "Send Mail" action, under the Parameters tab - This is not where email recipients are configured; the policy action uses the global settings
C. Thru Tools > Options > Advanced - Mail - The correct path is Tools > Options > General > Mail, not Advanced
D. Thru the Tools > Options > NAC Email - There is no "NAC Email" option in Tools > Options
E. Thru the policy sub rule and adding a condition - Sub-rules contain conditions, not email recipient configuration
Send Email Action in Policies:
According to the documentation:
"The Send Email action automatically delivers email to administrators when a policy is matched."
This action uses the email addresses configured in the global mail settings.
Referenced Documentation:
Managing Email Notifications documentation
Initial Setup – Mail section
Managing Email Notification Addresses documentation
Core Extensions Module Reports Plugin Configuration Guide
What Protocol does CounterACT use to verify the revocation status of certificates?
Options:
PKI Certificate Revocation Protocol (PCRP)
Online Certificate Status Protocol (OCSP)
Online Revocation Status Protocol (ORSP)
Certificate Revocation List Protocol (CRLP)
Certificate Revocation Protocol (CRP)
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Platform Administration Guide and Certificate Configuration documentation, Forescout uses the Online Certificate Status Protocol (OCSP) to verify the revocation status of certificates.
OCSP in Forescout:
According to the official Forescout documentation:
"You can also configure the use of Online Certificate Status Protocol (OCSP) and set up validation method failover between CRL and OCSP."
And further:
"The Forescout Platform supports certificate revocation lists (CRL) and Online Certificate Status Protocol (OCSP) for smart card authentication."
What OCSP Does:
According to the Wikipedia and Fortinet OCSP documentation:
"The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate."
OCSP provides:
Real-Time Status Verification - Checks current certificate revocation status
Request/Response Protocol - Sends a query to an OCSP responder
Revocation Status Response - Returns "good," "revoked," or "unknown"
Efficient Alternative to CRL - Smaller data payload than downloading full certificate revocation lists
How OCSP Works:
According to the OCSP documentation:
Request Sent - Client sends OCSP request to OCSP responder (server operated by CA)
Status Verification - Responder checks revocation status with trusted CA
Response Returned - Responder returns current status, revoked, or unknown
Decision Made - Application (like Forescout) accepts or rejects the certificate based on response
Forescout Smart Card Certificate Validation:
According to the Forescout documentation:
When using smart card authentication, Forescout:
Supports OCSP - Sends OCSP requests for certificate revocation status
Supports CRL - Also supports Certificate Revocation Lists as fallback
Failover Configuration - Can be configured to use OCSP with CRL fallback
OCSP vs. Certificate Revocation List (CRL):
According to the documentation:
Aspect
OCSP
CRL
Data Size
Smaller response
Larger list
Update Frequency
Real-time status
Periodic updates
Network Load
Lower burden
Higher burden
Timeliness
Current status
Potentially outdated
Processing
Less complex
More complex parsing
Forescout uses OCSP because it provides real-time, efficient certificate status verification.
Why Other Options Are Incorrect:
A. PKI Certificate Revocation Protocol (PCRP) - This is not a standard protocol; PCRP does not exist
C. Online Revocation Status Protocol (ORSP) - This is not the correct name; the protocol is OCSP, not ORSP
D. Certificate Revocation List Protocol (CRLP) - While Forescout supports CRL, the primary protocol for real-time status is OCSP
E. Certificate Revocation Protocol (CRP) - This is not a standard protocol; the correct protocol is OCSP
Referenced Documentation:
Smart Card Certificate Configuration for Forescout Platform
Using Forescout Platform Smart Card Authentication
Client-Server Connection documentation
Audit Actions - OCSP for Syslog validation
Online Certificate Status Protocol (OCSP) - Wikipedia
What Is Online Certificate Status Protocol (OCSP) - Fortinet
Which of the following is true regarding CounterACT 8 FLEXX Licensing?
Options:
CounterACT 8 can be installed on all CTxx and 51xx models.
Disaster Recovery is used for member appliances.
For member appliances, HA and Failover Clustering are part of Resiliency licensing.
Changing the licensing of the deployment from Per Appliance Licensing to FLEXX Licensing can be done through the Customer Portal.
Failover Clustering is used with EM and RM.
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Licensing and Sizing Guide and Failover Clustering Licensing Requirements documentation, the correct statement is: For member appliances, HA and Failover Clustering are part of Resiliency licensing.
Resiliency Licensing for Member Appliances:
According to the Failover Clustering Licensing Requirements documentation:
"To begin working with Failover Clustering, you need a license for the feature. The license required depends on which licensing mode your deployment is using."
When using FLEXX licensing with member appliances:
High Availability (HA) - Part of Resiliency licensing
Failover Clustering - Part of Resiliency licensing (called "eyeRecover License")
Disaster Recovery - Separate from member appliance resiliency
Resiliency License Components:
According to the documentation:
"When using Flexx licensing, Failover Clustering functionality is supported by the Forescout Platform eyeRecover license (Forescout CounterACT Resiliency license)."
The Resiliency license covers:
For Member Appliances:
High Availability (HA) Pairing
Failover Clustering
For Enterprise Manager:
HA Pairing for EM
FLEXX Licensing Model:
According to the Licensing and Sizing Guide:
"Flexx Licensing: Licenses are independent of hardware appliances, providing an intuitive and flexible way to license, deploy and manage Forescout products across your extended enterprise."
Why Other Options Are Incorrect:
A. Can be installed on all CTxx and 51xx models - FLEXX is for 5100/4100 series and later; CT series supports per-appliance licensing only
B. Disaster Recovery is used for member appliances - Disaster Recovery is separate; member appliances use HA/Failover Clustering from Resiliency license
D. Changing via Customer Portal - Changes from per-appliance to FLEXX must be done through official Forescout channels, not self-service Customer Portal
E. Failover Clustering is used with EM and RM - Failover Clustering is for member appliances; EM has separate HA capability
Referenced Documentation:
Failover Clustering Licensing Requirements v8.4.4 and v9.1.2
Forescout Licensing and Sizing Guide
Switch from Per-Appliance to Flexx Licensing
Which of the following are included in System backups?
Options:
Switch Plugin version 8.7.0 and above
Policies
Hostname and IP address
Failover Clustering plugin
Wireless Plugin version 1.4.0 and above
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Upgrade Guide and System Backup documentation, Policies are included in System backups.
What System Backups Include:
According to the official documentation:
"Each backup saves all Forescout Platform device and Console settings. This data includes the following:
Configuration
License
Operating System settings
Policies
Profiles
Reports
Administrator accounts
And other system data"
System Backup Contents:
According to the backup documentation:
System backups include:
Policies - All configured policies and policy templates
Configuration - System configuration settings
License Information - License keys and licensing data
Administrator Accounts - User accounts and access controls
Reports - Scheduled and saved reports
System Settings - Mail, network, and other system configurations
Profiles - User profiles and system profiles
What System Backups DO NOT Include:
According to the documentation:
System backups are encrypted using AES-256 and include most system data but are separate from:
Appliance-specific firmware - May require separate backup
Component-specific backups - Some modules have separate backup procedures
Log files - Not typically included in system backups
Why Other Options Are Incorrect:
A. Switch Plugin version 8.7.0 and above - Plugin versions are not individually backed up; plugins are part of the module installation, not system configuration backup
C. Hostname and IP address - While these are part of system configuration, they are covered under "Configuration" not listed separately in backup contents
D. Failover Clustering plugin - Plugin software itself is not backed up; configuration related to plugins is backed up
E. Wireless Plugin version 1.4.0 and above - Plugin versions are installed separately; backups contain configuration, not plugin versions
Policy Backup Importance:
According to the documentation:
Policies are one of the most critical items included in system backups because:
Restore Capability - After system recovery, policies are restored automatically
Business Continuity - Restoring policies ensures the same security posture
Compliance - Policies contain compliance rules that must be preserved
Operational Continuity - Restores endpoint management immediately after recovery
System vs. Component Backups:
According to the backup documentation:
System Backup - Includes policies, configuration, licenses, administrator accounts, etc.
Component Backup - Specific modules may have additional backup capabilities
Both backup types - Both are encrypted with AES-256 for security
Backup Encryption:
According to the documentation:
"Both system and component backup files, backed up either manually or via a schedule, are encrypted using AES-256 to protect sensitive file data."
This ensures that backed-up policies and other sensitive configuration remain secure.
Referenced Documentation:
Back Up your Enterprise Manager and/or Appliances - v8.4
Back Up your Enterprise Manager and/or Appliances - v8.5.1
Backing Up System and Component Settings - v8.4
Backing Up Forescout Platform System and Component Settings - v8.5.1
Updates to the Device Profile Library may impact a device's classification if the device was classified using:
Options:
Advanced Classification
External Devices
Client Certificates
HTTP Banner
Guest Registration
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Device Profile Library Configuration Guide, the Device Profile Library uses HTTP Banner (along with other properties like DHCP hostname, NIC vendor, and NMAP scan results) as key classification properties. When the Device Profile Library is updated, devices that were originally classified using HTTP Banner properties will be re-classified based on the new or updated profiles in the library.
Device Profile Library Function:
The Device Profile Library is a Content Module that delivers a library of pre-defined device classification profiles, each composed of properties and corresponding values that match a specific device type. According to the official documentation:
"Each profile maps to a combination of values for function, operating system, and/or vendor & model. For example, the profile defined for Apple iPad considers the set of properties which includes the hostname of the device revealed by DHCP traffic, the HTTP banner, the NIC vendor and Nmap scan results."
How Updates Impact Classification:
According to the documentation:
Library Updates - The Device Profile Library is periodically upgraded to improve classification accuracy and provide better coverage
Profile Changes - Updated profiles may change the properties used for classification or adjust matching criteria
Reclassification - When devices that rely on HTTP Banner information (or other matching properties in profiles) are re-evaluated against new profiles, their classification may change
Pending Changes - After a new version of the Device Profile Library is installed, devices show "pending classification changes" that can be reviewed before applying
Classification Properties in Device Profile Library:
According to the configuration guide, each device profile uses multiple properties including:
HTTP Banner - Information about web services running on the device (e.g., Apache 2.4, IIS 10.0)
DHCP Hostname - Device name revealed in DHCP traffic
NIC Vendor - MAC address vendor information
NMAP Scan Results - Open ports and services detected
When the Device Profile Library is updated, devices that were classified using these properties may be re-classified.
Why Other Options Are Incorrect:
A. Advanced Classification - This refers to custom classification properties, not DPL-based classification
B. External Devices - This is a classification category designation, not a classification method
C. Client Certificates - This is used for certificate-based identification, not DPL classification
E. Guest Registration - This is for guest management, not device classification via DPL
Update Process:
According to the documentation:
"After a new version of the Device Profile Library is installed, it is recommended to run a policy that resolves classification properties. Due to classification profile changes in the new library version, some device classifications may change."
Before these changes are applied, administrators can review all pending changes and decide whether to apply them, modify existing policies first, or cancel the changes and roll back to a previous Device Profile Library version.
Referenced Documentation:
Forescout Device Profile Library Configuration Guide - February 2018
About the Device Profile Library documentation
Update Classification Profiles section
Which type of endpoint can be queried for registry key properties?
Options:
Managed unknown endpoint
Unmanaged Windows endpoint
Managed Windows endpoint
Windows endpoint
Managed Linux endpoint
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Set Registry Key on Windows action, registry key properties can only be queried on "Managed Windows endpoints".
Registry Key Property Requirements:
According to the Set Registry Key on Windows documentation:
"Registry key properties can be queried on managed Windows endpoints only. The endpoint must be a Windows device that is managed (either via SecureConnector deployment or Remote Inspection with appropriate credentials)."
Managed vs. Unmanaged Endpoints:
According to the Windows Properties documentation:
Managed Windows Endpoint -✓Can query registry keys
Has SecureConnector deployed, OR
Has Remote Inspection access via credentials, OR
Is domain-joined with appropriate permissions
Unmanaged Windows Endpoint -✗Cannot query registry keys
No agent or access method available
Registry cannot be accessed remotely
Why Other Options Are Incorrect:
A. Managed unknown endpoint - "Unknown" endpoints are not classified as Windows; classification unknown
B. Unmanaged Windows endpoint - Unmanaged endpoints have no access to registry
D. Windows endpoint - Must be "managed" to query registry; not all Windows endpoints are managed
E. Managed Linux endpoint - Linux systems don't have Windows registry
Registry Access Methods:
According to the documentation:
Registry keys can be queried on Managed Windows endpoints using:
SecureConnector - Preferred method for interactive registry access
Remote Inspection (MS-WMI/RPC) - When credentials are configured
Domain Credentials - When endpoint is domain-joined
Referenced Documentation:
Set Registry Key on Windows - v9.1.4
Set Registry Key on Windows - v8.5.2
Windows Properties
Which of the following switch actions cannot both be used concurrently on the same switch?
Options:
Access Port ACL & Switch Block
Switch Block & Assign to VLAN
Endpoint Address ACL & Assign to VLAN
Access Port ACL & Endpoint Address ACL
Access Port ACL & Assign to VLAN
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide, Access Port ACL and Endpoint Address ACL cannot both be used concurrently on the same endpoint. These two actions are mutually exclusive because they both apply ACL rules to control traffic, but through different mechanisms, and attempting to apply both simultaneously creates a conflict.
Switch Restrict Actions Overview:
The Forescout Switch Plugin provides several restrict actions that can be applied to endpoints:
Access Port ACL - Applies an operator-defined ACL to the access port of an endpoint
Endpoint Address ACL - Applies an operator-defined ACL based on the endpoint's address (MAC or IP)
Assign to VLAN - Assigns the endpoint to a specific VLAN
Switch Block - Completely isolates endpoints by turning off their switch port
Action Compatibility Rules:
According to the Switch Plugin Configuration Guide:
Endpoint Address ACL vs Access Port ACL - These CANNOT be used together on the same endpoint because:
Both actions modify switch filtering rules
Both actions can conflict when applied simultaneously
The Switch Plugin cannot determine priority between conflicting ACL configurations
Applying both would create ambiguous filtering logic on the switch
Actions That CAN Be Used Together:
Access Port ACL + Assign to VLAN -✓Can be used concurrently
Endpoint Address ACL + Assign to VLAN -✓Can be used concurrently
Switch Block + Assign to VLAN - This is semantically redundant (blocking takes precedence) but is allowed
Access Port ACL + Switch Block -✓Can be used concurrently (though Block takes precedence)
Why Other Options Are Incorrect:
A. Access Port ACL & Switch Block - These CAN be used concurrently; Switch Block would take precedence
B. Switch Block & Assign to VLAN - These CAN be used concurrently (though redundant)
C. Endpoint Address ACL & Assign to VLAN - These CAN be used concurrently
E. Access Port ACL & Assign to VLAN - These CAN be used concurrently; they work on different aspects of port management
ACL Action Definition:
According to the documentation:
Access Port ACL - "Use the Access Port ACL action to define an ACL that addresses one or more than one access control scenario, which is then applied to an endpoint's switch port"
Endpoint Address ACL - "Use the Endpoint Address ACL action to apply an operator-defined ACL, addressing one or more than one access control scenario, which is applied to an endpoint's address"
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide Version 8.12
Switch Plugin Configuration Guide v8.14.2
Switch Restrict Actions documentation
Which of the following actions can be performed with Remote Inspection?
Options:
Set Registry Key, Disable dual homing
Send Balloon Notification, Send email to user
Disable External Device, Start Windows Updates
Start Secure Connector, Attempt to open a browser at the endpoint
Endpoint Address ACL, Assign to VLAN
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout HPS Inspection Engine Configuration Guide Version 10.8 and the Remote Inspection and SecureConnector Feature Support documentation, the actions that can be performed with Remote Inspection include "Start Secure Connector" and "Attempt to open a browser at the endpoint".
Remote Inspection Capabilities:
According to the documentation, Remote Inspection uses WMI and other standard domain/host management protocols to query the endpoint, and to run scripts and implement remediation actions on the endpoint. Remote Inspection is agentless and does not install any applications on the endpoint.
Actions Supported by Remote Inspection:
According to the HPS Inspection Engine Configuration Guide:
The Remote Inspection Feature Support table lists numerous actions that are supported by Remote Inspection, including:
Set Registry Key -✓Supported by Remote Inspection
Start SecureConnector -✓Supported by Remote Inspection
Attempt to Open Browser -✓Supported by Remote Inspection
Send Balloon Notification -✓Supported (requires SecureConnector; can also be used with Remote Inspection)
Start Windows Updates -✓Supported by Remote Inspection
Send Email to User -✓Supported action
However, the question asks which actions appear together in one option, and Option D correctly combines two legitimate Remote Inspection actions: "Start Secure Connector" and "Attempt to open a browser at the endpoint".
Start SecureConnector Action:
According to the documentation:
"Start SecureConnector installs SecureConnector on the endpoint, enabling future management via SecureConnector"
This is a supported Remote Inspection action that can deploy SecureConnector to endpoints.
Attempt to Open Browser Action:
According to the HPS Inspection Engine guide:
"Opening a browser window" is a supported Remote Inspection action
However, there are limitations documented:
"Opening a browser window does not work on Windows Vista and Windows 7 if the HPS remote inspection is configured to work as a Scheduled Task"
"When redirected with this option checked, the browser does not open automatically and relies on the packet engine seeing this traffic"
Why Other Options Are Incorrect:
A. Set Registry Key, Disable dual homing - While Set Registry Key is supported, "Disable dual homing" is not a standard Remote Inspection action
B. Send Balloon Notification, Send email to user - Both are notification actions, but the question seeks Remote Inspection-specific endpoint actions; these are general notification actions not specific to Remote Inspection
C. Disable External Device, Start Windows Updates - While Start Windows Updates is supported by Remote Inspection, "Disable External Device" is not a Remote Inspection action; it's a network device action
E. Endpoint Address ACL, Assign to VLAN - These are Switch plugin actions, not Remote Inspection actions; they work on network device level, not endpoint level
Remote Inspection vs. SecureConnector vs. Switch Actions:
According to the documentation:
Remote Inspection Actions (on endpoints):
Set Registry Key on Windows
Start Windows Updates
Start Antivirus
Update Antivirus
Attempt to open browser at endpoint
Start SecureConnector (to deploy SecureConnector)
Switch Actions (on network devices):
Endpoint Address ACL
Access Port ACL
Assign to VLAN
Switch Block
Referenced Documentation:
Forescout CounterACT Endpoint Module HPS Inspection Engine Configuration Guide Version 10.8
Remote Inspection and SecureConnector – Feature Support documentation
Set Registry Key on Windows action documentation
Start Windows Updates action documentation
Send Balloon Notification documentation
The host property 'HTTP User Agent banner' is resolved by what function?
Options:
Device classification engine
NetFlow
NMAP scanning
Packet engine
Device profile library
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Advanced Classification Properties, the host property "HTTP User Agent banner" is resolved by the Packet Engine.
HTTP User Agent Banner Property:
According to the Advanced Classification Properties documentation:
The HTTP User Agent property is captured through passive network traffic analysis by the Packet Engine, which monitors and analyzes HTTP headers in network traffic.
Packet Engine Function:
According to the Packet Engine documentation:
The Packet Engine provides:
Passive Traffic Monitoring - Analyzes network packets without interfering
HTTP Header Analysis - Extracts HTTP headers from captured traffic
User Agent Detection - Identifies HTTP User Agent strings from web requests
Property Resolution - Populates device properties from observed traffic
HTTP User Agent Examples:
Common User Agent banners that identify device types and browsers:
text
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36
Mozilla/5.0 (iPhone; CPU iPhone OS 14_6 like Mac OS X) AppleWebKit/605.1.15
Mozilla/5.0 (Linux; Android 11; SM-G991B) AppleWebKit/537.36
Why Other Options Are Incorrect:
A. Device classification engine - The classification engine uses properties resolved by other components like the Packet Engine
B. NetFlow - NetFlow provides flow statistics, not application-level data like HTTP headers
C. NMAP scanning - NMAP performs active port scanning, not passive HTTP header analysis
E. Device profile library - The profile library uses properties; it doesn't resolve them
Property Resolution by Function:
According to the documentation:
Property
Packet Engine
NMAP
Device Class Engine
Profile Library
HTTP User Agent
✓Yes
✗No
✗No
✗No
Service Banner
✗No
✓Yes
✗No
✗No
OS Classification
Partial
Partial
✓Yes
✗No
Function
✗No
✗No
✓Yes
✓Yes
Referenced Documentation:
Advanced Classification Properties
About the Packet Engine
Forescout Platform Dependencies and Known Issues
Which of the following must be configured in the User Directory plugin to allow active directory credentials to authenticate console logins?
Options:
Include Parent groups
Authentication
Use as directory
Target Group Resolution
Use for console login
Answer:
EExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide, to allow Active Directory credentials to authenticate console logins, the "Use for console login" option must be configured.
Three Key Checkboxes in User Directory Configuration:
According to the User Directory plugin documentation:
When configuring a User Directory server (such as Active Directory), three important checkboxes are available:
Use as directory - Allows LDAP queries for user information
Use for authentication - Allows user authentication via AD credentials
Use for console login - Allows AD credentials to authenticate console logins
"Use for console login" Purpose:
According to the documentation:
"When checked, this option enables Forescout Console administrators to log in using their Active Directory (or other configured directory server) credentials."
This checkbox specifically enables:
Administrators to use their Active Directory usernames and passwords
Console authentication via the configured directory server
Elimination of the need for separate Forescout Console accounts
Separate Functions of Each Checkbox:
According to the configuration guide:
Checkbox
Purpose
Use as directory
LDAP queries for user properties and group membership
Use for authentication
802.1X, RADIUS, and other authentication protocols
Use for console login
Console login authentication for Forescout administrators
Each serves a distinct purpose and must be configured independently.
Why Other Options Are Incorrect:
A. Include Parent groups - This relates to group hierarchy, not console login authentication
B. Authentication - This is the protocol/method name, not a specific configuration checkbox
C. Use as directory - This enables LDAP queries for user information, not console login authentication
D. Target Group Resolution - This is not a standard configuration option for User Directory plugins
Console Login Workflow with Active Directory:
According to the documentation:
When "Use for console login" is enabled:
Administrator enters username and password at Forescout Console login screen
Credentials are sent to the configured Active Directory server
Active Directory validates the credentials
If valid, administrator is granted console access
No separate Forescout password needed
Referenced Documentation:
User Directory Plugin - Name and Type Step configuration
User Directory readiness section
User Directory server configuration documentation
Which type of signed SSL Certificate file formats are compatible with CounterACT?
Options:
.Pfx/.p12, .Pfx/.p7
.p7b, .pem
.X.509, x.507
.Pckcs#7, .pckcs#12
.cer, .crt
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout CLI Reference - Generating CSRs and Importing Signed Certificates documentation, the SSL certificate file formats compatible with CounterACT are ".p7b" and ".pem".
Supported Certificate Formats:
According to the CLI Reference documentation:
"To import a certificate from DER or P7B formatted files, convert it to PEM file format. Then convert the PEM files to a single PFX file as described above."
This indicates that:
P7B format - Supported (PKCS#7 container format)
PEM format - Supported and widely used (ASCII-encoded format)
Certificate Format Conversion Process:
According to the documentation:
The standard import process is:
text
Original Format → Conversion → PEM Format → PFX Format → Import to CounterACT
├─ DER files → Convert → PEM
├─ P7B files → Convert → PEM
└─ PEM files → Direct use or convert to PFX
Why Other Options Are Incorrect:
A. .Pfx/.p12, .Pfx/.p7 - Pfx is the final format used, not input; p7 is not a standard format
C. .X.509, x.507 - X.509 is a standard (not a format); x.507 is not valid
D. .Pckcs#7, .pckcs#12 - Spelling is "PKCS," not "Pckcs"; these are standards, not file formats
E. .cer, .crt - These are certificate formats but not listed as directly compatible in the documentation
Certificate Import Workflow:
According to the documentation:
Compatible workflow formats:
Input Formats (that need conversion):
DER files → Convert to PEM
P7B files → Convert to PEM
CER files → Convert to PEM
Intermediate Format:
PEM (ASCII-encoded, universally compatible)
Final Format:
PFX (used for CounterACT import)
Referenced Documentation:
Generating CSRs and Importing Signed Certificates - CLI Reference
Import and Configure System Certificates
When using MS-WMI for Remote inspection, which of the following properties should be used to test for Windows Manageability?
Options:
Windows Manageable Domain (Current)
MS-RRP Reachable
MS-WMI Reachable
MS-SMB Reachable
Windows Manageable Domain
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout HPS Inspection Engine Configuration Guide Version 10.8, when using MS-WMI for Remote Inspection, MS-WMI Reachable property should be used to test for Windows Manageability.
MS-WMI Reachable Property:
According to the documentation:
"MS-WMI Reachable: Indicates whether Windows Management Instrumentation can be used for Remote Inspection tasks on the endpoint."
This Boolean property specifically tests whether WMI services are available and reachable on a Windows endpoint.
Remote Inspection Reachability Properties:
According to the HPS Inspection Engine guide:
Three reachability properties are available for detecting services on endpoints:
MS-RRP Reachable - Indicates whether Remote Registry Protocol is available
MS-SMB Reachable - Indicates whether Server Message Block protocol is available
MS-WMI Reachable - Indicates whether Windows Management Instrumentation is available (THIS IS FOR MS-WMI)
How to Use MS-WMI Reachable:
According to the documentation:
When Remote Inspection method is set to "Using MS-WMI":
Check the MS-WMI Reachable property value
If True - WMI services are running and available for Remote Inspection
If False - WMI services are not available; fallback methods or troubleshooting required
Property Characteristics:
According to the documentation:
"These properties do not have an Irresolvable state. When HPS Inspection Engine cannot establish connection with the service, the property value is False."
This means:
Always returns True or False (never irresolvable)
False indicates the service is not reachable
No need for "Evaluate Irresolvable Criteria" option
Why Other Options Are Incorrect:
A. Windows Manageable Domain (Current) - This is not the specific property for testing MS-WMI capability
B. MS-RRP Reachable - This tests Remote Registry Protocol, not WMI
D. MS-SMB Reachable - This tests Server Message Block protocol, not WMI
E. Windows Manageable Domain - General manageability property, not specific to WMI testing
Remote Inspection Troubleshooting:
According to the documentation:
When troubleshooting Remote Inspection with MS-WMI:
First verify MS-WMI Reachable = True
Check required WMI services:
Server
Windows Management Instrumentation (WMI)
Verify port 135/TCP is available
If MS-WMI Reachable = False, check firewall and WMI configuration
Referenced Documentation:
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide v10.8
Detecting Services Available on Endpoints
Which of the following are true about the comments field of the CounterACT database? (Choose two)
Options:
Endpoints may have multiple comments assigned to them
It cannot be edited manually by a right click administrator action, it can only be edited in policy by using the action "Run Script on CounterACT"
It can be edited manually by a right click administrator action, or it can be edited in policy by using the action "Run Script on CounterACT"
Endpoints may have exactly one comment assigned to them
It can be edited manually by a right click administrator action, or it can be edited in policy by using the action "Run Script on Windows"
Answer:
A, CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Device Information Properties documentation, the correct statements about the comments field are: Endpoints may have multiple comments assigned to them (A) and it can be edited manually by a right click administrator action, or it can be edited in policy by using the action "Run Script on CounterACT" (C).
Comments Field Overview:
According to the Device Information Properties documentation:
"(Right-click an endpoint in the Detections pane to add a comment. The comment is retained for the life of the endpoint in the Forescout Console.)"
Multiple Comments Support:
According to the ForeScout Administration Guide:
Endpoints support multiple comments that can be added over time:
Manual Comments - Administrators can right-click an endpoint and add comments
Policy-Generated Comments - Policies can automatically add comments when conditions are met
Cumulative - Multiple comments are retained and displayed together
Persistent - Comments are retained for the life of the endpoint
Manual Comments via Right-Click:
According to the documentation:
Administrators can manually edit the comments field by:
Right-clicking on an endpoint in the Detections pane
Selecting "Add comment" or "Edit comment" option
Entering the comment text
Saving the comment
This manual method is readily available and frequently used for operational notes.
Policy-Based Comments via "Run Script on CounterACT":
According to the Administration Guide:
Policies can also edit the comments field using the "Run Script on CounterACT" action:
Create or edit a policy
Add the "Run Script on CounterACT" action
The script can modify the Comments host property
When the policy condition is met, the script runs and updates the comment field
Why Other Options Are Incorrect:
B. Cannot be edited manually...only via Run Script on CounterACT - Incorrect; manual right-click editing is explicitly supported
D. Endpoints may have exactly one comment - Incorrect; multiple comments are supported
E. Can be edited...by using action "Run Script on Windows" - Incorrect; the action is "Run Script on CounterACT," not "Run Script on Windows"
Comments Field Characteristics:
According to the documentation:
The Comments field:
Supports Multiple Entries - More than one comment can be added
Manually Editable - Right-click administrative action available
Policy Editable - "Run Script on CounterACT" action can modify it
Persistent - Retained for the life of the endpoint
Searchable - Comments can be used in policy conditions
Audit Trail - Provides documentation of endpoint history
Usage Examples:
According to the Administration Guide:
Manual Comments:
"Device moved to Building C - 2024-10-15"
"User reported software issue"
"Awaiting quarantine release approval"
Policy-Generated Comments:
Vulnerability compliance policy: "Failed patch compliance check"
Security policy: "Detected unauthorized application"
Remediation policy: "Scheduled for antivirus update"
Multiple such comments can accumulate on a single endpoint over time.
Referenced Documentation:
Forescout Administration Guide - Device Information Properties
ForeScout CounterACT Administration Guide - Comments field section
Which field in the User Directory plugin should be configured for Active Directory subdomains?
Options:
Replicas
Address
Parent Groups
Domain Aliases
DNS Detection
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide - Microsoft Active Directory Server Settings, the field that should be configured for Active Directory subdomains is "Domain Aliases".
Domain Aliases for Subdomains:
According to the Microsoft Active Directory Server Settings documentation:
"Configure the following additional server settings in the Directory and Additional Domain Aliases sections: Domain Aliases - Configure additional domain names that users can use to log in, such as subdomains."
Purpose of Domain Aliases:
According to the documentation:
Domain Aliases are used to specify:
Subdomains - Alternative domain names like subdomain.company.com
Alternative Domain Names - Other domain name variations
User Login Options - Additional domains users can use to authenticate
Alias Resolution - Maps aliases to the primary domain
Example Configuration:
For an organization with the primary domain company.com and subdomain accounts.company.com:
Domain Field - Set to: company.com
Domain Aliases Field - Add: accounts.company.com
This allows users from either domain to authenticate successfully.
Why Other Options Are Incorrect:
A. Replicas - Replicas configure redundant User Directory servers, not subdomains
B. Address - Address field specifies the server IP/FQDN, not domain aliases
C. Parent Groups - Parent Groups relate to group hierarchy, not domain subdomains
E. DNS Detection - DNS Detection is not a User Directory configuration field
Additional Domain Configuration:
According to the documentation:
text
Primary Configuration:
├─ Domain: company.com
├─ Domain Aliases: accounts.company.com
│ services.company.com
│ mail.company.com
└─ Port: 636 (default)
Referenced Documentation:
Microsoft Active Directory Server Settings
Define User Directory Servers - Domain Aliases section
When troubleshooting an issue that affects multiple endpoints, why might you choose to view Policy logs before Host logs?
Options:
Because you can gather more pertinent information about a single host
Because Policy logs show details for a range of endpoints
You would not. Host logs are the best choice for a range of endpoints
Policy logs may help to pinpoint the issue for a specific host
Looking at Host logs is always the first step in the process
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
When troubleshooting an issue that affects multiple endpoints, you should view Policy logs before Host logs because Policy logs show details for a range of endpoints. According to the Forescout Administration Guide, Policy Logs are specifically designed to "investigate the activity of specific endpoints, and display information about how those endpoints are handled" across multiple devices.
Policy Logs vs. Host Logs - Purpose and Scope:
Policy Logs:
Scope - Shows policy activity across multiple endpoints simultaneously
Purpose - Investigates how multiple endpoints are handled by policies
Information - Displays which endpoints match which policies, what actions were taken, and policy evaluation results
Use Case - Best for understanding policy-wide impact and identifying patterns across multiple endpoints
Host Logs:
Scope - Shows detailed activity for a single specific endpoint
Purpose - Investigates specific activity of individual endpoints
Information - Displays all events and actions pertaining to that single host
Use Case - Best for deep-diving into a single endpoint's detailed history
Troubleshooting Methodology for Multiple Endpoints:
When troubleshooting an issue affecting multiple endpoints, the recommended approach is:
Start with Policy Logs - Determine which policy or policies are affecting the multiple endpoints
Identify Pattern - Look for common policy matches or actions across the affected endpoints
Pinpoint Root Cause - Determine if the issue is policy-related or host-related
Then Use Host Logs - After identifying the affected hosts, examine individual Host Logs for detailed troubleshooting
Policy Log Information:
Policy Logs typically display:
Endpoint IP and MAC address
Policy name and match criteria
Actions executed on the endpoint
Timestamp of policy evaluation
Status of actions taken
Efficient Troubleshooting Workflow:
According to the documentation:
When multiple endpoints are affected, examining Policy Logs first allows you to:
Identify Common Factor - Quickly see if all affected endpoints are in the same policy
Spot Misconfiguration - Determine if a policy condition is incorrectly matching endpoints
Track Action Execution - See what policy actions were executed across the range of endpoints
Save Time - Avoid reviewing individual host logs when a policy-level issue is evident
Example Scenario:
If 50 endpoints suddenly lose network connectivity:
First, check Policy Logs - Determine if all 50 endpoints matched a policy that executed a blocking action
Identify the Policy - Look for a common policy match across all 50 hosts
Examine Root Cause - Policy logs will show if a Switch Block action or VLAN assignment action was executed
Then, check individual Host Logs - If further detail is needed, examine specific host logs for those 50 endpoints
Why Other Options Are Incorrect:
A. Because you can gather more pertinent information about a single host - This describes Host Logs, not Policy Logs; wrong log type
C. You would not. Host logs are the best choice for a range of endpoints - Incorrect; Host logs are for single endpoints, not ranges
D. Policy logs may help to pinpoint the issue for a specific host - While true, this describes singular host troubleshooting, not multiple endpoints
E. Looking at Host logs is always the first step in the process - Incorrect; Policy logs are better for multiple endpoints to identify patterns
Policy Logs Access:
According to documentation:
"Use the Policy Log to investigate the activity of specific endpoints, and display information about how those endpoints are handled."
The Policy Log interface typically allows filtering and viewing multiple endpoints simultaneously, making it ideal for identifying patterns across a range of affected hosts.
Referenced Documentation:
Forescout Administration Guide - Policy Logs
Generating Forescout Platform Reports and Logs
Host Log – Investigate Endpoint Activity
"Quickly Access Forescout Platform Endpoints with Troubleshooting Issues" section in Administration Guide
Which of the following is true regarding the Windows Installed Programs property which employs the "for any/for all" logic mechanism?
Options:
Although the condition has multiple sub-properties, when "ANY" is selected it evaluates the programs for any of the configured sub-properties.
The condition does not have any sub-properties. The "any/all" refers to the multiple programs.
Although the condition has sub-properties which could refer to a single program on multiple endpoints, the "any/all" refers to the program's properties.
Although the condition has multiple sub-properties, the "any/all" refers to the sub-properties and not the programs.
Although the condition has multiple sub-properties, the "any/all" refers to the programs and not the sub-properties.
Answer:
EExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
The Windows Installed Programs property condition utilizes multiple sub-properties including Program Name, Program Version, Program Vendor, and Program Path. However, when using the "for ANY/for ALL" logic mechanism, the "any/all" refers to the PROGRAMS and not to the sub-properties.
How the "Any/All" Logic Works with Windows Installed Programs:
When configuring a policy condition with the Windows Installed Programs property, the "any/all" logic determines whether an endpoint should match the condition based on:
"For ANY" - The endpoint matches the policy condition if ANY of the configured programs are installed on the endpoint
"For ALL" - The endpoint matches the policy condition if ALL of the configured programs are installed on the endpoint
Example: If an administrator creates a condition like:
Windows Installed Programs contains "Microsoft Office" OR "Adobe Reader"
Using "For ANY": The endpoint matches if it has EITHER Microsoft Office OR Adobe Reader installed
Using "For ALL": The endpoint matches only if it has BOTH Microsoft Office AND Adobe Reader installed
The sub-properties (Program Name, Version, Vendor, Path) are used to define and identify which specific programs to match against, but the "any/all" logic applies to the PROGRAMS themselves, not to the sub-properties.
Why Other Options Are Incorrect:
A - Incorrectly states the "any/all" evaluates the programs for the sub-properties
B - Factually incorrect; the condition definitely has multiple sub-properties (Name, Version, Vendor, Path)
C - Confuses the scope; the "any/all" does not refer to "program's properties" but to multiple programs
D - Inverted logic; the "any/all" refers to the programs, not the sub-properties
Referenced Documentation:
Forescout Administration Guide v8.3, v8.4
Working with Policy Conditions - List of Properties by Category
Windows Applications Content Module Configuration Guide
What best defines a 'Post-Connect Methodology'?
Options:
802.1X is a flavor of Post-Connect
Guilty until proven innocent
Innocent until proven guilty
Used subsequent to pre-connect
Assessed for critical compliance before IP address is assigned
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Blog on Post-Connect Access Controls and the Comply-to-Connect framework documentation, a Post-Connect Methodology is best defined as treating endpoints as "Innocent until proven guilty".
Definition of Post-Connect Methodology:
According to the official documentation:
"Post-connect" is described as treating endpoints as innocent until they are proven guilty. They can connect to the network, during and after which they are assessed for acceptance criteria."
How Post-Connect Works:
According to the Post-Connect Access Controls blog:
Initial Connection - Endpoints are allowed to connect to the network immediately (innocent)
Assessment During/After Connection - After connecting, endpoints are assessed for acceptance criteria
Compliance Checking - Endpoints are checked for:
Corporate asset status (must be company-owned)
Security compliance (antivirus, patches, encryption, etc.)
Remediation or Quarantine - Based on assessment results:
Compliant endpoints: Full access
Non-compliant endpoints: Placed in quarantine for remediation
Post-Connect vs. Pre-Connect:
According to the Comply-to-Connect documentation:
Pre-Connect - "Guilty until proven innocent" - Endpoint must prove compliance BEFORE getting network access
Post-Connect - "Innocent until proven guilty" - Endpoint connects first, then compliance is assessed
Benefits of Post-Connect Methodology:
According to the documentation:
"The greatest benefit to the post-connect approach is a positive user experience. Unless a system is out of compliance and ends up in a quarantine, your company's users have no idea access controls are even taking place on the network."
Acceptance Criteria in Post-Connect:
According to the framework:
Corporate Asset Verification - Determines if the endpoint belongs to the organization
Compliance Assessment - Checks for:
Updated antivirus
Patch levels
Disk encryption status
Security tool functionality
If an endpoint fails these criteria, it's placed in quarantine (controlled network access) rather than being completely blocked.
Why Other Options Are Incorrect:
A. 802.1X is a flavor of Post-Connect - 802.1X is a pre-connect access control method (requires authentication before network access)
B. Guilty until proven innocent - This describes pre-connect methodology, not post-connect
D. Used subsequent to pre-connect - While post-connect can follow pre-connect, this doesn't define what post-connect is
E. Assessed for critical compliance before IP address is assigned - This describes pre-connect methodology
Referenced Documentation:
Forescout Blog - Post-Connect Access Controls
Comply-to-Connect Brief - Pre-connect vs Post-connect comparison
Achieving Comply-to-Connect Requirements with Forescout
Why is SMB required for Windows Manageability?
Options:
Scripts run on CounterACT are copied to a temp directory and run locally on the endpoint
Scripts run on endpoints are copied to a Linux script repository and run locally on the endpoint
Scripts run on endpoints are copied to a temp directory and run remotely from CounterACT
Scripts run on CounterACT are copied to a script repository and run remotely from CounterACT
Scripts run on endpoints are copied to a temp directory and run locally on the endpoint
Answer:
EExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout CounterACT HPS Inspection Engine Configuration Guide Version 10.8, SMB (Server Message Block) is required for Windows Manageability because scripts run on endpoints are copied to a temp directory and run locally on the endpoint.
SMB Purpose for Windows Management:
According to the HPS Inspection Engine guide:
"Server Message Block (SMB) is a protocol for file and resource sharing. CounterACT uses this protocol with WMI or RPC methods to inspect and manage endpoints. This protocol must be available to perform the following:
Resolve file-related properties
Resolve script properties
Run script actions"
Script Execution Process Using SMB:
According to the documentation:
When WMI is used for Remote Inspection:
CounterACT downloads scripts - Scripts are transferred FROM CounterACT TO the endpoint using SMB protocol
Scripts stored in temp directory - By default, scripts are downloaded to and run from:
Non-interactive scripts: %TEMP%\fstmp\ directory
Interactive scripts: %TEMP% directory of currently logged-in user
Scripts execute locally - Scripts are executed ON the endpoint itself (not remotely executed from CounterACT)
Script Execution Locations:
According to the detailed documentation:
For Remote Inspection on Windows endpoints:
text
Non-interactive scripts are downloaded to and run from:
%TEMP%\fstmp\
(Typically %TEMP% is c:\windows\temp\)
Interactive scripts are downloaded to and run from:
%TEMP% directory of the currently logged-in user
For SecureConnector on Windows endpoints:
text
When deployed as a Service:
%TEMP%\fstmpsc\
When deployed as a Permanent Application:
%TEMP% directory of the currently logged-in user
SMB Requirements for Script Execution:
According to the documentation:
To execute scripts via SMB on Windows endpoints:
Port Requirements:
Windows 7 and above: Port 445/TCP
Earlier versions (XP, Vista): Port 139/TCP
Required Services:
Server service
Remote Procedure Call (RPC)
Remote Registry service
SMB Signing (optional but recommended):
Can be configured to require digitally signed SMB communication
Helps prevent SMB relay attacks
Why Other Options Are Incorrect:
A. Scripts run on CounterACT are copied to a temp directory and run locally on the endpoint - Scripts don't RUN on CounterACT; they're copied FROM CounterACT TO the endpoint
B. Scripts run on endpoints are copied to a Linux script repository - Forescout endpoints are Windows machines, not Linux; also no "Linux script repository" is involved
C. Scripts run on endpoints are copied to a temp directory and run remotely from CounterACT - Scripts run LOCALLY on the endpoint, not remotely from CounterACT
D. Scripts run on CounterACT are copied to a script repository and run remotely from CounterACT - Inverts the direction; CounterACT doesn't copy TO a repository; it copies TO endpoints
Script Execution Flow:
According to the documentation:
text
CounterACT --> (copies via SMB) --> Endpoint Temp Directory --> (executes locally) --> Result
The SMB protocol is essential for this file transfer step, which is why it's required for Windows manageability and script execution.
Referenced Documentation:
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide v10.8
Script Execution Services documentation
About SMB documentation
When using Remote Inspection for Windows, which of the following properties require fsprocsvc.exe interactive scripting?
Options:
User Directory Common Name
Update Microsoft Vulnerabilities
Windows Expected Script Result
Antivirus Running
Windows Service Running
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
The Windows Expected Script Result property is the correct answer. According to the official Forescout CounterACT Endpoint Module: HPS Inspection Engine Configuration Guide Version 10.8, the fsprocsvc.exe service is required to run interactive scripts for several CounterACT tasks during Remote Inspection operations on Windows endpoints.
The documentation explicitly lists the following Properties requiring the fsprocsvc service (with Remote Inspection, i.e., not via SecureConnector):
Windows Expected Script Result ✓
Device Interfaces
Number of IP Addresses
External Devices
Windows File MD5 Signature
Windows Is Behind NAT
Microsoft Vulnerabilities
About fsprocsvc.exe Service:
The fsprocsvc.exe service is a proprietary ForeScout service utility that is downloaded by the HPS Inspection Engine to endpoints. It is used to run interactive scripts for several CounterACT tasks. Key characteristics include:
Size on disk: Approximately 250KB
Memory acquired during runtime: 2 MB
Runs under: System context
Start type: Automatic
Inactivity timeout: After 2 hours of inactivity, the service stops automatically
Communication: Does not open any new network connection. Communication is carried out over Microsoft's SMB/RPC (445/TCP and 139/TCP) with domain credentials authentication
Why Other Options Are Incorrect:
A. User Directory Common Name - This property is derived from User Directory plugin queries and does not require fsprocsvc interactive scripting
B. Update Microsoft Vulnerabilities - This is an action, not a property. While Microsoft Vulnerabilities property does require fsprocsvc, "Update" is not the property name listed
D. Antivirus Running - This is a basic WMI-based property that does not require interactive scripting via fsprocsvc
E. Windows Service Running - This is a basic property that can be determined through WMI queries without requiring fsprocsvc interactive scripting
Interactive Scripts Requirement:
According to the HPS Inspection Engine Configuration Guide, WMI does not support interactive scripts on all Windows endpoints. When WMI is used for Remote Inspection, CounterACT uses the fsprocsvc service to run interactive scripts on endpoints that require them. The Windows Expected Script Result property specifically requires running a custom script on the endpoint, which necessitates the fsprocsvc service for proper execution.
Referenced Documentation:
Forescout CounterACT Endpoint Module: HPS Inspection Engine Configuration Guide Version 10.8
Section: "About fsprocsvc.exe" and "Properties requiring the service (With remote inspection, i.e. not via SecureConnector)"
Select the action that requires symmetrical traffic.
Options:
Assign to VLAN
WLAN block
Endpoint ACL
Start SecureConnector
Virtual Firewall
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide and Switch Plugin documentation, the action that requires symmetrical traffic is the Endpoint Address ACL action (C).
What "Symmetrical Traffic" Means:
Symmetrical traffic refers to network traffic where CounterACT can monitor BOTH directions of communication:
Inbound - Traffic from the endpoint
Outbound - Traffic to the endpoint
This allows CounterACT to see the complete conversation flow.
Endpoint Address ACL Requirements:
According to the Switch Plugin documentation:
"The Endpoint Address ACL action applies an ACL that delivers blocking protection when endpoints connect to the network. Other benefits of Endpoint Address ACL include..."
For the Endpoint Address ACL to function properly, CounterACT must:
See bidirectional traffic - Monitor packets in both directions
Apply dynamic ACLs - Create filtering rules based on both source and destination
Verify endpoints - Ensure the endpoint IP/MAC matches expected patterns in both directions
Why Symmetrical Traffic is Required:
According to the documentation:
Endpoint Address ACLs work by:
Identifying the endpoint's MAC address and IP address through bidirectional observation
Creating switch ACLs that filter based on the endpoint's communication patterns
Verifying the endpoint is communicating in expected ways (symmetrically)
Without symmetrical traffic visibility, CounterACT cannot reliably identify and apply address-based filtering.
Why Other Options Do NOT Require Symmetrical Traffic:
A. Assign to VLAN - Only requires knowing the switch port; doesn't need traffic monitoring
B. WLAN block - Works at the wireless access point level without needing symmetrical traffic observation
D. Start SecureConnector - Deployment action that doesn't require traffic symmetry
E. Virtual Firewall - Works at the endpoint level and can function with asymmetrical or passive monitoring
Asymmetrical vs. Symmetrical Deployment:
According to the administrative guide:
Asymmetrical Deployment - CounterACT sees traffic from one direction only
Used for passive monitoring of device discovery
Sufficient for many actions
Symmetrical Deployment - CounterACT sees traffic in both directions
Required for endpoint ACL actions
Necessary for accurate address-based filtering
Referenced Documentation:
Endpoint Address ACL Action documentation
ForeScout CounterACT Administration Guide - Switch Plugin actions
Unlock FSCP Features
- FSCP All Real Exam Questions
- FSCP Exam easy to use and print PDF format
- Download Free FSCP Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
Questions & Answers PDF Demo
- FSCP All Real Exam Questions
- FSCP Exam easy to use and print PDF format
- Download Free FSCP Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
