F5 101 Application Delivery Fundamentals Exam Practice Test
Application Delivery Fundamentals Questions and Answers
An administrator needs to do the following
* install a load balancer in front of an existing application
* test application performance
* avoid reconfiguration of the application server
* avoid interruption of users accessing the application
Which function does the Presentation Layer provide?
A load balancing decision needs to be made based on custom a What is the most appropriate F5 feature (or this purpose?
An administrator needs to protect a web application from cross-site scripting (CSS) exploits. Which F5 protocol provide this functionality
What are Iwo examples of failover capabilities of BIG-IP? (Choose two )
A BIG-IP Administrator contacts F5 Support and is asked to upload a Support Snapshot. Which command should be entered to the CLI to generate the requested file?
What are three functions commonly performed by HTTP cookies? (Choose three)
Cryptographic hash functions can be used to provide which service?
A VoIP application requires that data payloads will NOT be fragmented. Which protocol controls network behavior in this situation?
An administrator needs to load balance connections to the application server with the lowest number of
Which load balancing method meets these requirements?
Which HTTP response code indicates an OK status?
Which security model provides protection from unknown attacks?
The administrator wants client request to be directed to the same pool member through the session based on the client IP address.
Which persistence method should the administrator choose?
A BIG IP Administrator observes that the pool member status is a blue square What does this status indicate?
The 2001:db8: : IP6 address block is allocated to a load balancer for use as virtual server addresses. The address block is routed to a balancer self IP address using a static route. What is the correct representation for the last address in the address block that a virtual server can use?
An administrator points the browser at h.tp://www mydomain com.The destination server listens on TCP port 8080 Which feature must be enabled on the virtual server for this configuration to work?
A load balancer receives a TCP SYN packet from a client and immediately sends the packet on to a server.
This is an example of which type of solution?
An Administrator enables HTTP keep alive.
How does this affect the network?
Why is it important that devices in a high availability pair share the same configuration?
Which method should an administrator of the BIG-IP use to sync the configuration to only certain other BIG-IPs?
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named LACP01) connected to the BIG IP device, Multiple other VLANs exist on LACP01.Which TMSH command should the BIG IP Administrator issue to add the new VLAN lo the existing LAC?
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named IACP01) connected to the BIG IP device Multiple other VLANs exist on LACP01. Which TMSH command should the BIG IP Administrator issue to add the new VLAN to the existing LAC?
What does response code HTTP 302 represent?
AD VLAN must be created with an 802.19 tag of 705 on interface 11. What is the proper TSH command to create this new VLAN on the BIG-IP?
In wh.ch layer of the OSI model is the data transported in the form of a packet?
Which HTTP response code is returned when a web
server requires authentication to access a resource?
A BIO IP Administrator is troubleshooting a slow web application. A packet capture shows that some of the packets coming from a window size of zero A packet capture shows that som a window size of zero
What does this mean?
What is the primary function of a certificate authority?
An administrator needs to create a structured application delivery configuration that will prevent individual objects from being modified directly
Which F5 technology should the administrator use?
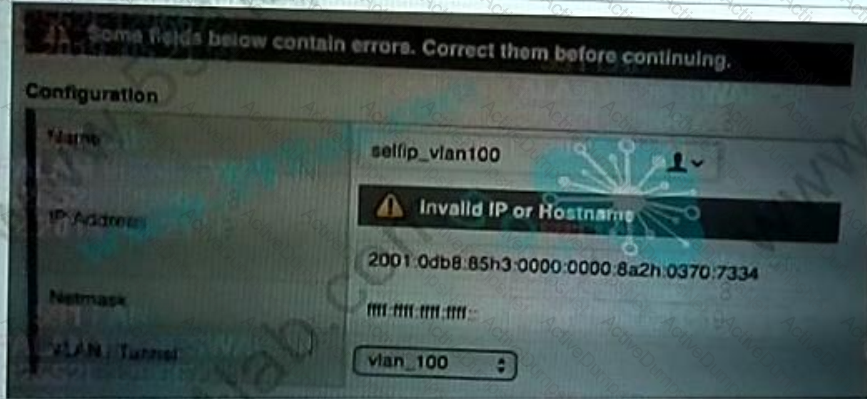
An administrate receives an error message when attempting to create a self-IP address on a BIG-IP appliance Which address should the administrator use to resolve the issue?
A 2001 0db8.85a3 0000 0000 8a2e 0370 7334
B. 2001:db8:85a3 Bd3.Ba2e.370 7334
C. 2001:0db8:85i3:0000:0000: : 8a2i:0370:7334
Which two functions of AAA does Security Assertion Markup Language (SAML) identity Provider (IdP) offer (Choose two)?
A BIG-IP Administrator needs to make sure that requests from a single user are directed to the server that was initially selected (unless that server is marked down). What should the administrator configure?
In the Network Map a red diamond appears next to the three member servers in the Virtual Server’s pool. The nodes in the pool each show a green circle. What is the most likely reason for this scenario?
A BIG IP Administrator need to perform a packet capture and identify the source IP that is connecting to the Virtual Server.
Which utility should the administrator use on the BIG IP device?
When using LDAP for authentication, what is the purpose of the base ON?
In a load balanced scenario which service would require persistence to function correctly?
Which service should be configured to allow BIG-IP devices to be externally monitored?
