EMC DES-9131 Specialist - Infrastructure Security Exam Exam Practice Test
Specialist - Infrastructure Security Exam Questions and Answers
You need to review your current security baseline policy for your company and determine which security
controls need to be applied to the baseline and what changes have occurred since the last update.
Which category addresses this need?
What supports an organization in making risk management decisions to address their security posture in real time?
Refer to the exhibit.
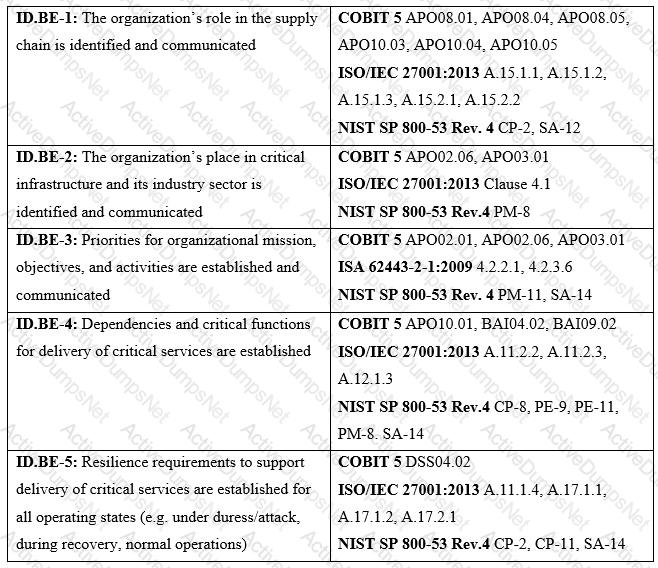
What type of item appears in the second column of the table?
What contains a predefined set of instructions or processes that describes the management policy,
procedures, and written plan defining recovery of information systems?
Your data center uses a diesel generator as backup for two different power grids provided by your regional power company. During a period of unprecedented heat, you experience brown-outs on both grids simultaneously. The diesel generator starts up but only runs for two minutes before it also shuts down, leaving your entire data center down until grid power can be restored. Further inspection reveals a clogged fuel filter.
Failing to schedule preventive service for the backup generator is a failure in which function?
An incident has occurred. You restore backups onto mission/business critical assets. After restoration of the
backups your services are still inaccessible on numerous assets.
What could be the cause of the issue?
Assume that a DDoS attack has been occurring for 72 minutes. What determines who talks to external
stakeholders?
During what activity does an organization identify and prioritize technical, organizational, procedural,
administrative, and physical security weaknesses?
What must be done before returning a compromised laptop to normal operations in the environment?
