EMC DEA-2TT3 Associate - Cloud Infrastructure and Services v.3 Exam Exam Practice Test
Associate - Cloud Infrastructure and Services v.3 Exam Questions and Answers
What is specified by a service attribute?
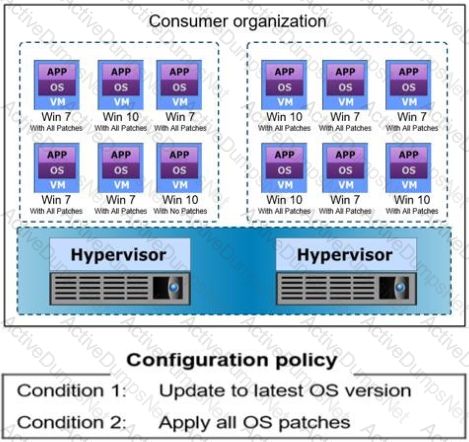
Refer to the exhibit, which represents a consumer environment consisting of multiple VMs running Windows operating systems (OSs).
For compliance reasons, the cloud service provider maintains version control over the OS provided to the consumer. The service provider also ensures that the configurations of the VMs comply with the configuration policy for the OS version. The configuration policy includes the two conditions shown in the exhibit. A monitoring tool verifies VM configurations against the configuration policy and provides the compliance results shown.
What is the percentage of compliance non-adherence?
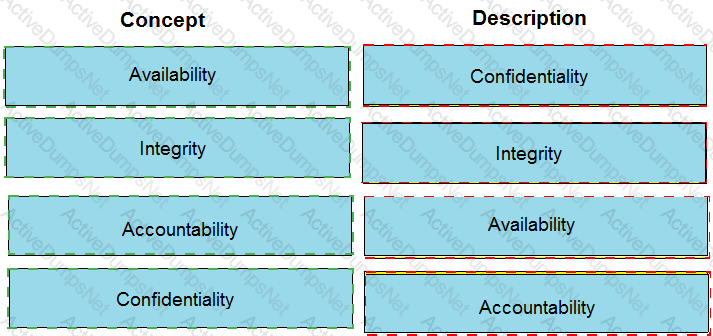
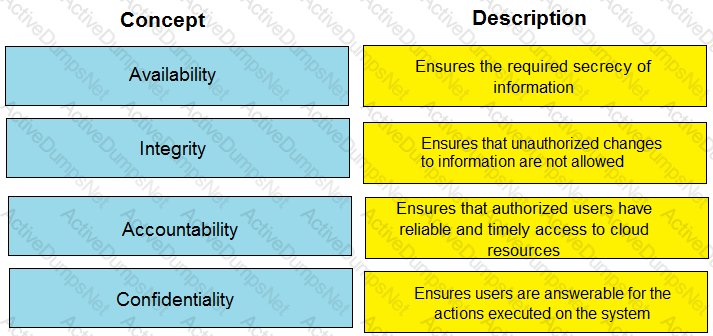
Match each information security concept with its description.
What is a function of the discovery operation during the service operation phase of the cloud service lifecycle?
A compute system is configured to access files from a network-attached storage system. What is a characteristic of the file system?
Which activity is a part of people transformation?
What is a possible cause for incurring high capital expenditures for IT, even though resources may remain underutilized for a majority of the time in a traditional data center?
What is a responsibility of Service manager
What is an advantage of adopting a microservices strategy in an application development environment?
What is a characteristic of storage resource pools?
What is a function of service portfolio management?
What term refers step or a series of steps necessary to complete an attack.