EMC D-CIS-FN-01 Dell Cloud Infrastructure and Services Foundations v2 Exam Exam Practice Test
Dell Cloud Infrastructure and Services Foundations v2 Exam Questions and Answers
How is application functionality segmented when using a microservices approach in an application development environment?
When implementing an initial IT service center using ITILframework. In service strategy state which process needs to be considered for automation?
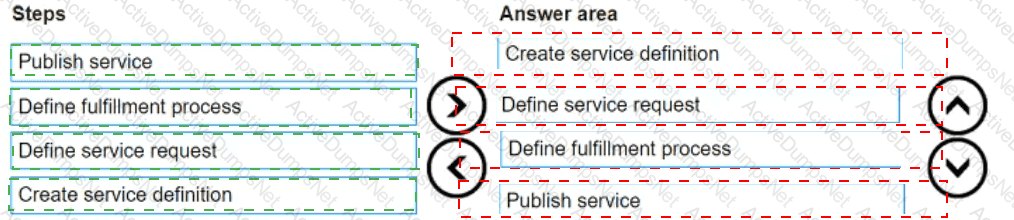
What steps appear in the service enablement roadmap?
A cloud service provider must improve the utilization of resources by sharing them with multiple customers.
What mechanism should the cloud provider deploy to prevent one consumer from accessing the virtual machines of another consumer?
What is a benefit of link aggregation?
What is a key function of service operation management?
Which cloud security control mechanism monitors activity using video surveillance cameras and detects unusual activities using sensors and alarms?
What is true about change management?
An administrator must design a fault-tolerant IT environment for applications.
Which techniques meet this requirement?
Which tool should be recommended to customers for Infrastructure automation?
An organization requires double the processing capacity for a specific duration to handle increased workload. For the remaining period, the organization might want to release the idle resources to save costs. The workload variations may be seasonal or transient.
Which cloud characteristic enables the consumer to handle such variations in workloads and IT resource requirements?
Which condition triggers a warning level alert?
Why do organizations take advantage of virtual infrastructure?
Which plane in a software-defined storage environment manages and provisions storage?
How is a container different from a virtual machine?
What is a benefit of synchronous remote replication?
Which risk management step deploys various security mechanisms that minimize risks impacts?
What is the effect of a denial-of-service attack?
What condition can result in the development of a "shadow IT" organization?
What term refers to businesses that cautiously and gradually embrace digital transformation?
What activity is included in a compliance checklist when moving data to the cloud?
What is a key responsibility of a security governance board?
Which network feature enables dynamic distribution of applications I/O traffic across VMs?
An organization wants to deliver applications quickly and effectively. They believe that it is the only way to stay competitive in this ever-changing digital world. The organization wants to adopt practices that promote collaboration across teams during various phases of the software development lifecycle.
Which practice will meet the organization’s requirements?
What is a characteristic of a best-of-breed infrastructure?
Which component presents service catalog and cloud interfaces, enabling consumers to order and manager cloud services?
Which two are key requirements for fault tolerance?
What does a service attribute specify?
What is a characteristic of an object-based storage system?
Which phase of the cloud service lifecycle involves ongoing management activities to maintain cloud infrastructure and deployed services?
What is a characteristic of reporting?
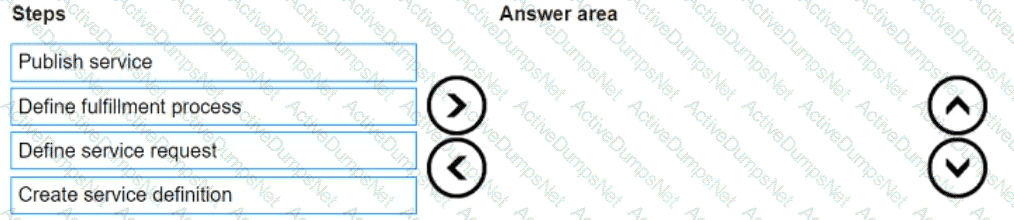
What is the correct sequence of steps in the service catalog design and implementation process?
What is used to update information in a configuration management database?
What is a possible cause for incurring high capital expenditures for IT, even though resources may remain underutilized for a majority of the time in a traditional data center?
What is an advantage of asynchronous remote replication?
What term refers to the entry points from which an attack can be launched?