ECCouncil 312-96 Certified Application Security Engineer (CASE) JAVA Exam Practice Test
Certified Application Security Engineer (CASE) JAVA Questions and Answers
Which of the following relationship is used to describe security use case scenario?
Ted is an application security engineer who ensures application security activities are being followed during the entire lifecycle of the project. One day, he was analyzing various interactions of users depicted in the use cases of the project under inception. Based on the use case in hand, he started depicting the scenarios where attacker could misuse the application. Can you identify the activity on which Ted is working?
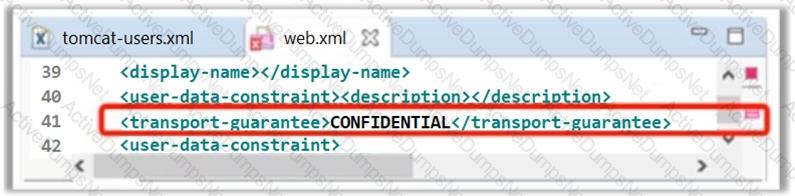
Oliver, a Server Administrator (Tomcat), has set configuration in web.xml file as shown in the following screenshot. What is he trying to achieve?
Identify the type of attack depicted in the figure below:
Jacob, a Security Engineer of the testing team, was inspecting the source code to find security vulnerabilities.
Which type of security assessment activity Jacob is currently performing?
It is recommended that you should not use return, break, continue or throw statements in _________
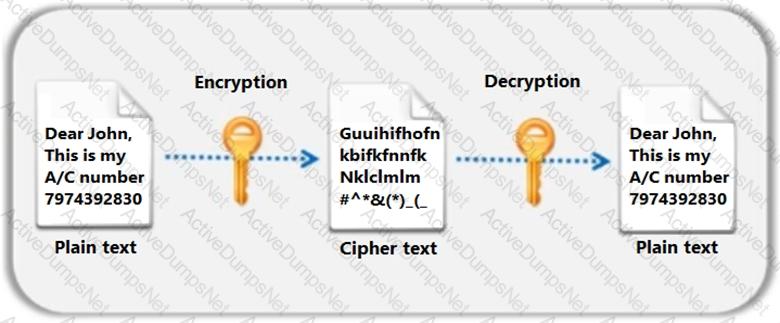
Identify the type of encryption depicted in the following figure.
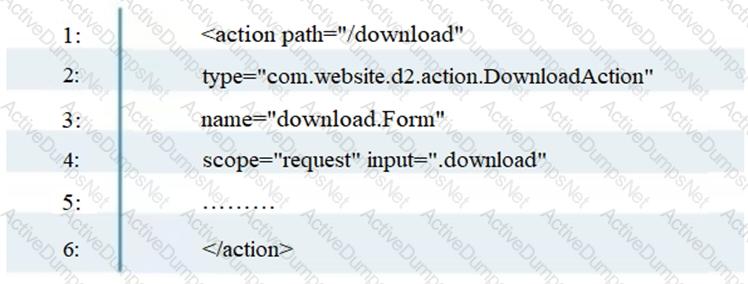
To enable the struts validator on an application, which configuration setting should be applied in the struts validator configuration file?
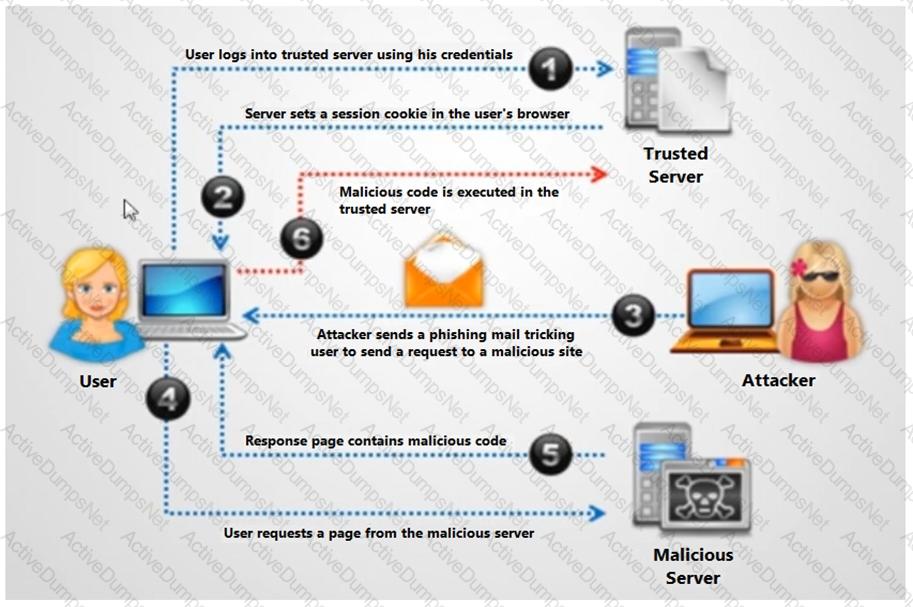
Identify the type of attack depicted in the following figure.
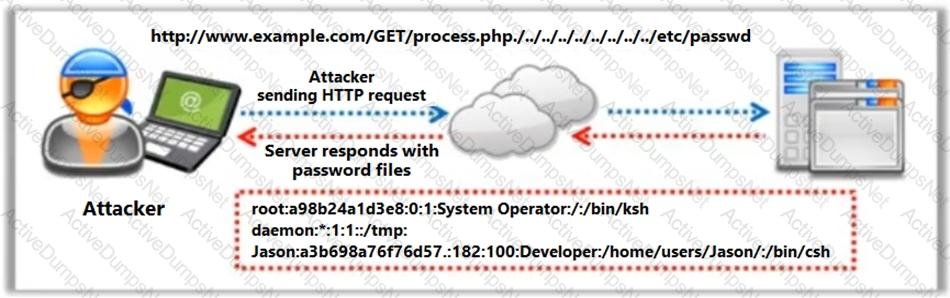
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
Oliver is a web server admin and wants to configure the Tomcat server in such a way that it should not serve index pages in the absence of welcome files. Which of the following settings in CATALINA_HOME/conf/ in web.xml will solve his problem?
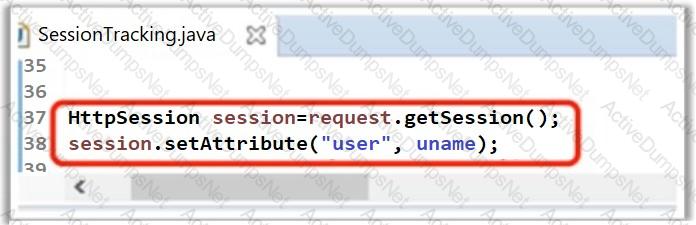
A developer has written the following line of code to handle and maintain session in the application. What did he do in the below scenario?
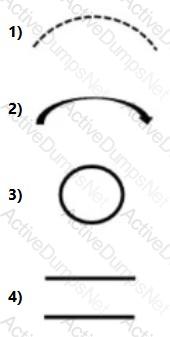
Which of the following DFD component is used to represent the change in privilege levels?
Which of the following configuration settings in server.xml will allow Tomcat server administrator to impose limit on uploading file based on their size?
