ECCouncil 312-50 Certified Ethical Hacker Exam Exam Practice Test
Certified Ethical Hacker Exam Questions and Answers
Which of the following is a detective control?
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
A covert channel is a channel that
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
Which of the following techniques will identify if computer files have been changed?
Which system consists of a publicly available set of databases that contain domain name registration contact information?
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
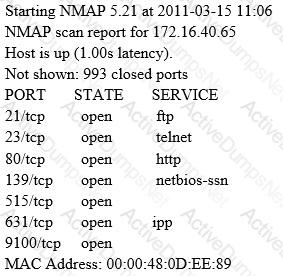
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
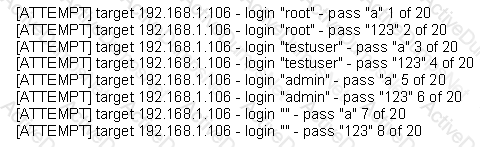
What is most likely taking place?
Least privilege is a security concept that requires that a user is
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
If the final set of security controls does not eliminate all risk in a system, what could be done next?
Which of the following programs is usually targeted at Microsoft Office products?
Which of the following describes the characteristics of a Boot Sector Virus?
Bluetooth uses which digital modulation technique to exchange information between paired devices?
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
In order to show improvement of security over time, what must be developed?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
Which of the following is an application that requires a host application for replication?
Which of the following scanning tools is specifically designed to find potential exploits in Microsoft Windows products?
A security consultant is trying to bid on a large contract that involves penetration testing and reporting. The company accepting bids wants proof of work so the consultant prints out several audits that have been performed. Which of the following is likely to occur as a result?
A pentester gains access to a Windows application server and needs to determine the settings of the built-in Windows firewall. Which command would be used?
Which of the following ensures that updates to policies, procedures, and configurations are made in a controlled and documented fashion?
Which type of security document is written with specific step-by-step details?
Which United States legislation mandates that the Chief Executive Officer (CEO) and the Chief Financial Officer (CFO) must sign statements verifying the completeness and accuracy of financial reports?
When does the Payment Card Industry Data Security Standard (PCI-DSS) require organizations to perform external and internal penetration testing?
Which method can provide a better return on IT security investment and provide a thorough and comprehensive assessment of organizational security covering policy, procedure design, and implementation?
Which of the following tools would be the best choice for achieving compliance with PCI Requirement 11?
International Organization for Standardization (ISO) standard 27002 provides guidance for compliance by outlining
How do employers protect assets with security policies pertaining to employee surveillance activities?
Which of the following guidelines or standards is associated with the credit card industry?
How can a policy help improve an employee's security awareness?
Which of the statements concerning proxy firewalls is correct?
Which type of intrusion detection system can monitor and alert on attacks, but cannot stop them?
Which of the following processes of PKI (Public Key Infrastructure) ensures that a trust relationship exists and that a certificate is still valid for specific operations?
Which of the following levels of algorithms does Public Key Infrastructure (PKI) use?
Which of the following items is unique to the N-tier architecture method of designing software applications?
To reduce the attack surface of a system, administrators should perform which of the following processes to remove unnecessary software, services, and insecure configuration settings?
When setting up a wireless network, an administrator enters a pre-shared key for security. Which of the following is true?
Which of the following is a common Service Oriented Architecture (SOA) vulnerability?
Which of the following network attacks takes advantage of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
Which cipher encrypts the plain text digit (bit or byte) one by one?
Some passwords are stored using specialized encryption algorithms known as hashes. Why is this an appropriate method?
Advanced encryption standard is an algorithm used for which of the following?
Which of the following is an example of IP spoofing?
Which of the following network attacks relies on sending an abnormally large packet size that exceeds TCP/IP specifications?
A certified ethical hacker (CEH) is approached by a friend who believes her husband is cheating. She offers to pay to break into her husband's email account in order to find proof so she can take him to court. What is the ethical response?
A certified ethical hacker (CEH) completed a penetration test of the main headquarters of a company almost two months ago, but has yet to get paid. The customer is suffering from financial problems, and the CEH is worried that the company will go out of business and end up not paying. What actions should the CEH take?
Which initial procedure should an ethical hacker perform after being brought into an organization?
A consultant has been hired by the V.P. of a large financial organization to assess the company's security posture. During the security testing, the consultant comes across child pornography on the V.P.'s computer. What is the consultant's obligation to the financial organization?
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems and intrusion detection/prevention tools in your company's network. You have configured the most secure policies and tightened every device on your network. You are confident that hackers will never be able to gain access to your network with complex security system in place.
Your peer, Peter Smith who works at the same department disagrees with you.
He says even the best network security technologies cannot prevent hackers gaining access to the network because of presence of "weakest link" in the security chain.
What is Peter Smith talking about?
Which of the following is considered an exploit framework and has the ability to perform automated attacks on services, ports, applications and unpatched security flaws in a computer system?
While doing a Black box pen test via the TCP port (80), you noticed that the traffic gets blocked when you tried to pass IRC traffic from a web enabled host. However, you also noticed that outbound HTTP traffic is being allowed. What type of firewall is being utilized for the outbound traffic?
Which of the following is assured by the use of a hash?
A company's security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?
The chance of a hard drive failure is known to be once every four years. The cost of a new hard drive is $500. EF (Exposure Factor) is about 0.5. Calculate for the Annualized Loss Expectancy (ALE).
