ECCouncil 312-38 Certified Network Defender (CND) Exam Practice Test
Certified Network Defender (CND) Questions and Answers
What represents the ability of an organization to respond under emergency in order to minimize the damage to its brand name, business operation, and profit?
Which of the following filters car be applied to detect an ICMP ping sweep attempt using Wireshark?
A company wants to implement a data backup method that allows them to encrypt the data ensuring its security as well as access it at any time and from any location. What is the appropriate backup method
that should be implemented?
Identify the attack signature analysis technique carried out when attack signatures are contained in packet headers.
James is a network administrator working at a student loan company in Minnesota. This company processes over 20,000 student loans a year from colleges all over the state. Most communication between the company
schools, and lenders is carried out through emails. Much of the email communication used at his company contains sensitive information such as social security numbers. For this reason, James wants to utilize email
encryption. Since a server-based PKI is not an option for him, he is looking for a low/no cost solution to encrypt emails. What should James use?
Identify the network topology where each computer acts as a repeater and the data passes from one computer to the other in a single direction until it reaches the destination.
Which RAID level does not provide data redundancy?
Which of the following connects the SDN application layer and SDN controller and allows communication between the network services and business applications?
A VPN Concentrator acts as a bidirectional tunnel endpoint among host machines. What are the other f unction(s) of the device? (Select all that apply)
The Circuit-level gateway firewall technology functions at which of the following OSI layer?
Which among the following tools can help in identifying IoEs to evaluate human attack surface?
Steven is a Linux system administrator at an IT company. He wants to disable unnecessary services in the system, which can be exploited by the attackers. Which among the following is the correct syntax for
disabling a service?
Identity the method involved in purging technique of data destruction.
Ryan works as a network security engineer at an organization the recently suffered an attack. As a countermeasure, Ryan would like to obtain more information about the attacker and chooses to deploy a honeypot into the organizations production environment called Kojoney. Using this honeypot, he would like to emulate the network vulnerability that was attacked previously. Which type of honeypot is he trying to implement?
According to standard loT security practice, loT Gateway should be connected to a -------------
Wallcot, a retail chain in US and Canada, wants to improve the security of their administration
offices. They want to implement a mechanism with two doors. Only one of the doors can be opened at a
time. Once people enter from the first door, they have to be authorized to open the next one. Failing
the authorization, the person will be locked between the doors until an authorized person lets him or
her out. What is such a mechanism called?
Which of the following is a windows in-built feature that provides filesystem-level encryption in the OS (starting from Windows 2000). except the Home version of Windows?
Based on which of the following registry key, the Windows Event log audit configurations are recorded?
In ______ method, event logs are arranged in the form of a circular buffer.
In Public Key Infrastructure (PKI), which authority is responsible for issuing and verifying the certificates?
------------is a group of broadband wireless communications standards for Metropolitan Area Networks (MANs)
Which of the following can be used to suppress fire from Class K sources?
Rick has implemented several firewalls and IDS systems across his enterprise network. What should he do to effectively correlate all incidents that pass through these security controls?
Jorge has developed a core program for a mobile application and saved it locally on his system. The
next day, when he tried to access the file to work on it further, he found it missing from his system.
Upon investigation, it was discovered that someone got into his system since he had not changed his
login credentials, and that they were the ones that were given to him by the admin when he had joined
the organization. Which of the following network security vulnerabilities can be attributed to Jorge’s
situation?
John has planned to update all Linux workstations in his network. The organization is using various Linux distributions including Red hat, Fedora and Debian. Which of following commands will he use to
update each respective Linux distribution?
XX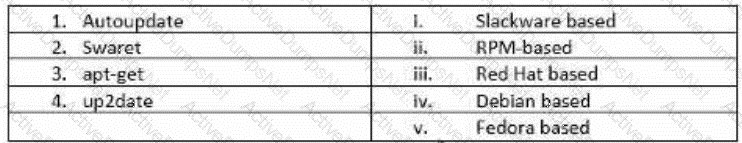
Identify the spread spectrum technique that multiplies the original data signal with a pseudo random noise spreading code.
John is a senior network security administrator working at a multinational company. He wants to block specific syscalls from being used by container binaries. Which Linux kernel feature restricts actions
within the container?
Byron, a new network administrator at FBI, would like to ensure that Windows PCs there are up-to-date and have less internal security flaws. What can he do?
What is the correct order of activities that a IDS is supposed to attempt in order to detect an intrusion?
Which antenna's characteristic refer to the calculation of radiated in a particular direction. It is generally the ratio of radiation intensity in a given direction to the average radiation intensity?
Implementing access control mechanisms, such as a firewall, to protect the network is an example of which of the following network defense approach?
Who acts as an intermediary to provide connectivity and transport services between cloud consumers and providers?
John wants to implement a firewall service that works at the session layer of the OSI model. The firewall must also have the ability to hide the private network information. Which type of firewall service is John thinking of
implementing?
Identify the correct statements regarding a DMZ zone:
Which Internet access policy starts with all services blocked and the administrator enables safe and necessary services individually, which provides maximum security and logs everything, such as system
and network activities?
Assume that you are a network administrator and the company has asked you to draft an Acceptable Use Policy (AUP) for employees. Under which category of an information security policy does AUP fall into?
Identify the network topology in which the network devices are connected such that every device has a point-to-point link to all the other devices.
David is working in a mid-sized IT company. Management asks him to suggest a framework that can be used effectively to align the IT goals to the business goals of the company. David suggests the______framework,
as it provides a set of controls over IT and consolidates them to form a framework.
Bryson is the IT manager and sole IT employee working for a federal agency in California. The agency was just given a grant and was able to hire on 30 more employees for a new extended project. Because of this,
Bryson has hired on two more IT employees to train up and work. Both of his new hires are straight out of college and do not have any practical IT experience. Bryson has spent the last two weeks teaching the new
employees the basics of computers, networking, troubleshooting techniques etc. To see how these two new hires are doing, he asks them at what layer of the OSI model do Network Interface Cards (NIC) work on. What
should the new employees answer?
What is the best way to describe a mesh network topology?
Which among the following control and manage the communication between VNF with computing, storage, and network resources along with virtualization?
You are monitoring your network traffic with the Wireshark utility and noticed that your network is experiencing a large amount of traffic from a certain region. You suspect a DoS incident on the network. What will be your
first reaction as a first responder?
John is working as a network defender at a well-reputed multinational company. He wanted to implement security that can help him identify any future attacks that can be targeted toward his organization and
take appropriate security measures and actions beforehand to defend against them. Which one of the following security defense techniques should be implement?
Which of the following indicators are discovered through an attacker's intent, their end goal or purpose, and a series of actions that they must take before being able to successfully launch an attack?
How can organizations obtain information about threats through human intelligence?
Which of the following characteristics represents a normal TCP packet?
Alex is administrating the firewall in the organization's network. What command will he use to check the ports applications open?
Which of the following is a best practice for wireless network security?
Identify the Password Attack Technique in which the adversary attacks cryptographic hash functions based on the probability, that if a hashing process is used for creating a key, then the same is
used for other keys?
Which of the following examines Recovery Point Objectives (RPOs) and Recovery Time Objectives (RTOs) for a disaster recovery strategy?
Which authentication technique involves mathematical pattern-recognition of the colored part of the eye behind the cornea?
Which of the following network monitoring techniques requires extra monitoring software or hardware?
James, a network admin in a large US based IT firm, was asked to audit and implement security
controls over all network layers to achieve Defense-in-Depth. While working on this assignment, James
has implemented both blacklisting and whitelisting ACLs. Which layer of defense-in-depth architecture is
Jason working on currently?
The network administrator wants to strengthen physical security in the organization. Specifically, to
implement a solution stopping people from entering certain restricted zones without proper credentials.
Which of following physical security measures should the administrator use?
Which type of antenna is based on the principle of a satellite dish and can pick up Wi-Fi signals from a distance of ten miles of more?
Which of the following data security technology can ensure information protection by obscuring specific areas of information?
Which of the following can be used to disallow a system/user from accessing all applications except a specific folder on a system?
Which type of attack is used to hack an IoT device and direct large amounts of network traffic toward a web server, resulting in overloading the server with connections and preventing any new connections?
Which type of firewall consists of three interfaces and allows further subdivision of the systems based on specific security objectives of the organization?
Ivan needs to pick an encryption method that is scalable even though it might be slower. He has settled on a method that works where one key is public and the other is private. What encryption method did Ivan settle
on?
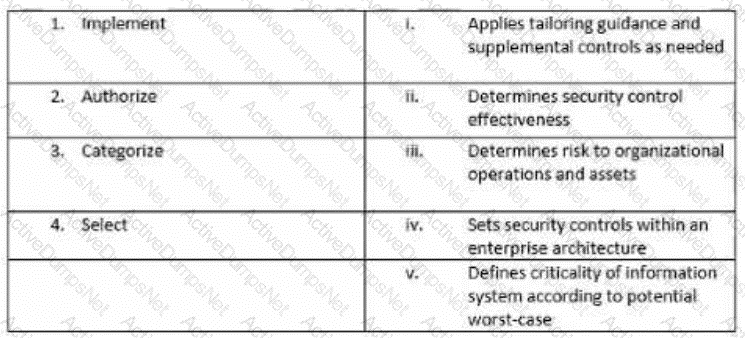
Match the following NIST security life cycle components with their activities:
Which OSI layer does a Network Interface Card (NIC) work on?
Kyle is an IT consultant working on a contract for a large energy company in Houston. Kyle was hired on to do contract work three weeks ago so the company could prepare for an external IT security audit. With
suggestions from upper management, Kyle has installed a network-based IDS system. This system checks for abnormal behavior and patterns found in network traffic that appear to be dissimilar from the traffic
normally recorded by the IDS. What type of detection is this network-based IDS system using?
Docker provides Platforms-a-Service (PaaS) through __________ and deliver*; containerized software packages
Which type of wireless network attack is characterized by an attacker using a high gain amplifier from a nearby location to drown out the legitimate access point signal?
Harry has sued the company claiming they made his personal information public on a social networking site in the United States. The company denies the allegations and consulted a/an _______ for legal
advice to defend them against this allegation.
How can a WAF validate traffic before it reaches a web application?
John is a network administrator and is monitoring his network traffic with the help of Wireshark. He suspects that someone from outside is making a TCP OS fingerprinting attempt on his organization's network. Which
of the following Wireshark filter(s) will he use to locate the TCP OS fingerprinting attempt?
Fred is a network technician working for Johnson Services, a temporary employment agency in Boston. Johnson Services has three remote offices in New England and the headquarters in Boston where Fred works.
The company relies on a number of customized applications to perform daily tasks and unfortunately these applications require users to be local administrators. Because of this, Fred's supervisor wants to implement
tighter security measures in other areas to compensate for the inherent risks in making those users local admins. Fred's boss wants a solution that will be placed on all computers throughout the company and
monitored by Fred. This solution will gather information on all network traffic to and from the local computers without actually affecting the traffic. What type of solution does Fred's boss want to implement?
Consider a scenario consisting of a tree network. The root Node N is connected to two man nodes N1 and N2. N1 is connected to N11 and N12. N2 is connected to N21 and N22. What will happen if any one of the main
nodes fail?
An US-based organization decided to implement a RAID storage technology for their data backup plan. John wants to setup a RAID level that require a minimum of six drives but will meet high fault tolerance and with a
high speed for the data read and write operations. What RAID level is John considering to meet this requirement?
Michael decides to view the-----------------to track employee actions on the organization's network.
As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2's _________integrity check mechanism provides security against a replay attack
The agency Jacob works for stores and transmits vast amounts of sensitive government data that cannot be compromised. Jacob has implemented Encapsulating Security Payload (ESP) to encrypt IP traffic. Jacob
wants to encrypt the IP traffic by inserting the ESP header in the IP datagram before the transport layer protocol header. What mode of ESP does Jacob need to use to encrypt the IP traffic?
Malone is finishing up his incident handling plan for IT before giving it to his boss for review. He is outlining the incident response methodology and the steps that are involved. Which step should Malone list as the last step in the incident response methodology?
Which of the following manages the Docker images, containers, networks, and storage volume and processes the request of Docker API?
Sean has built a site-to-site VPN architecture between the head office and the branch office of his company. When users in the branch office and head office try to communicate with each other, the traffic is
encapsulated. As the traffic passes though the gateway, it is encapsulated again. The header and payload both are encapsulated. This second encapsulation occurs only in the __________implementation of a VPN.
Jeanne is working as a network administrator in an IT company. She wants to control/limit container
access to CPU, memory, swap, block IO (rates), network. Which Linux kernel feature allows Jeanne to
manage, restrict, and audit groups of the process?
Which of the following is consumed into SIEM solutions to take control of chaos, gain in-depth knowledge of threats, eliminate false positives, and implement proactive intelligence-driven defense?
The SNMP contains various commands that reduce the burden on the network administrators.
Which of the following commands is used by SNMP agents to notify SNMP managers about an event occurring in the network?
Which of the following VPN topologies establishes a persistent connection between an organization's main office and its branch offices using a third-party network or the Internet?
James is working as a Network Administrator in a reputed company situated in California. He is monitoring his network traffic with the help of Wireshark. He wants to check and analyze the traffic against a PING sweep
attack. Which of the following Wireshark filters will he use?
Chris is a senior network administrator. Chris wants to measure the Key Risk Indicator (KRI) to assess the organization. Why is Chris calculating the KRI for his organization? It helps Chris to:
Which of the following RAID storage techniques divides the data into multiple blocks, which are further written across the RAID system?
USB ports enabled on a laptop is an example of____
Mark is monitoring the network traffic on his organization's network. He wants to detect a TCP and UDP ping sweep on his network. Which type of filter will be used to detect this on the network?
If Myron, head of network defense at Cyberdyne, wants to change the default password policy settings on the company’s Linux systems, which directory should he access?
Which of the following is true regarding any attack surface?
Which BC/DR activity includes action taken toward resuming all services that are dependent on business-critical applications?
Which encryption algorithm does S/MIME protocol implement for digital signatures in emails?
If a network is at risk from unskilled individuals, what type of threat is this?
Daniel is monitoring network traffic with the help of a network monitoring tool to detect any abnormalities. What type of network security approach is Daniel adopting?
Henry needs to design a backup strategy for the organization with no service level downtime. Which backup method will he select?
Ross manages 30 employees and only 25 computers in the organization. The network the company uses is a peer-to-peer. Ross configures access control measures allowing the employees to set their own control
measures for their files and folders. Which access control did Ross implement?
George was conducting a recovery drill test as a part of his network operation. Recovery drill tests are conducted on the______________.
Which of the following Wireshark filters allows an administrator to detect SYN/FIN DDoS attempt on
the network?
John has implemented________in the network to restrict the limit of public IP addresses in his organization and to enhance the firewall filtering technique.
Which of the following standards does a cloud service provider has to comply with, to protect the privacy of its customer’s personal information?
What is the IT security team responsible for effectively managing the security of the organization’s IT infrastructure, called?
Michelle is a network security administrator working in an MNC company. She wants to set a
resource limit for CPU in a container. Which command-line allows Michelle to limit a container to 2
CPUs?
James was inspecting ARP packets in his organization's network traffic with the help of Wireshark. He is checking the volume of traffic containing ARP requests as well as the source IP address from which they are
originating. Which type of attack is James analyzing?
A network is setup using an IP address range of 0.0.0.0 to 127.255.255.255. The network has a default subnet mask of 255.0.0.0. What IP address class is the network range a part of?
Which IEEE standard does wireless network use?
Assume that you are working as a network administrator in the head office of a bank. One day a bank employee informed you that she is unable to log in to her system. At the same time, you get a call from another
network administrator informing you that there is a problem connecting to the main server. How will you prioritize these two incidents?
Which of the following wireless encryption provides enhanced password protection, secured IoT connections, and encompasses stronger encryption techniques?
Which type of information security policy addresses the implementation and configuration of technology and user behavior?
Mark is monitoring the network traffic on his organization’s network. He wants to detect TCP and UDP ping sweeps on his network. Which type of filter will be used to detect this?
Which of the following defines the extent to which an interruption affects normal business operations and the amount of revenue lost due to that interruption?
