CyberArk PAM-CDE-RECERT CyberArk CDE Recertification Exam Practice Test
CyberArk CDE Recertification Questions and Answers
Which user is automatically added to all Safes and cannot be removed?
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
Which of the following Privileged Session Management solutions provide a detailed audit log of session activities?
Ad-Hoc Access (formerly Secure Connect) provides the following features. Choose all that apply.
You are installing multiple PVWAs behind a load balancer. Which statement is correct?
Select the best practice for storing the Master CD.
Which service should NOT be running on the DR Vault when the primary Production Vault is up?
A customer is deploying PVWAs in the Amazon Web Services Public Cloud. Which load balancing option does CyberArk recommend?
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
A Reconcile Account can be specified in the Master Policy.
You have been asked to turn off the time access restrictions for a safe.
Where is this setting found?
What is the primary purpose of Dual Control?
Which of the following statements are NOT true when enabling PSM recording for a target Windows server? (Choose all that apply)
You have been asked to limit a platform called "Wmdows_Servers" to safes called "WindowsDCT and "WindowsDC2" The platform must not be assigned to any other safe What is the correct way to accomplish this?
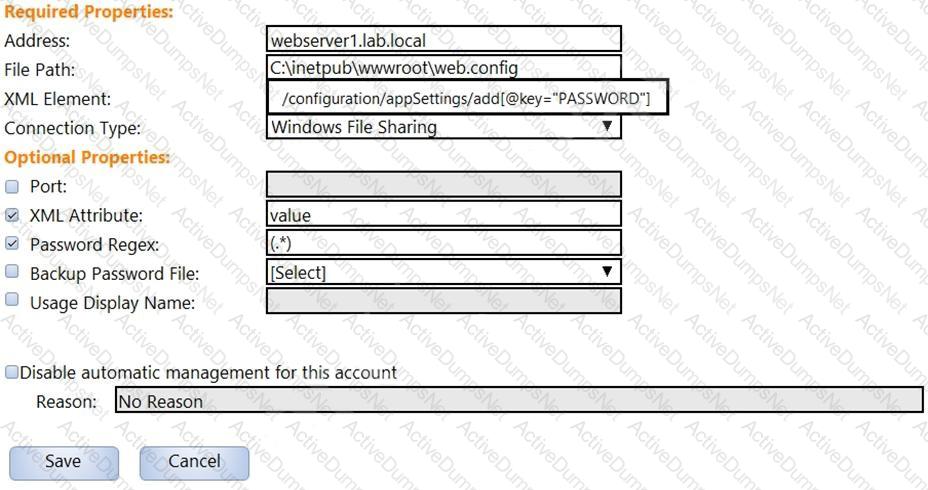
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
Which PTA sensors are required to detect suspected credential theft?
An auditor initiates a live monitoring session to PSM server to view an ongoing live session. When the auditor’s machine makes an RDP connection the PSM server, which user will be used?
You are configuring the vault to send syslog audit data to your organization's SIEM solution. What is a valid value for the SyslogServerProtocol parameter in DBPARM.ini file?
A user has successfully conducted a short PSM session and logged off. However, the user cannot access the Monitoring tab to view the recordings.
What is the issue?
A Vault administrator have associated a logon account to one of their Unix root accounts in the vault. When attempting to verify the root account’s password the Central Policy Manager (CPM) will:
What is the purpose of the PrivateArk Server service?
Which of the following PTA detections are included in the Core PAS offering?
Your customer has five main data centers with one PVWA in each center under different URLs. How can you make this setup fault tolerant?
When a DR Vault Server becomes an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission.
Where do you update this permission for all auditors?
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys.
How are these keys managed?
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
You are onboarding 5,000 UNIX root accounts for rotation by the CPM. You discover that the CPM is unable to log in directly with the root account and will need to use a secondary account.
How should this be configured to allow for password management using least privilege?
According to the DEFAULT Web Options settings, which group grants access to the REPORTS page?
As vault Admin you have been asked to configure LDAP authentication for your organization's CyberArk users. Which permissions do you need to complete this task?
CyberArk implements license limits by controlling the number and types of users that can be provisioned in the vault.
Users who have the 'Access Safe without confirmation' safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
Which permissions are needed for the Active Directory user required by the Windows Discovery process?
To use PSM connections while in the PVWA, what are the minimum safe permissions a user or group will need?
In your organization the “click to connect” button is not active by default.
How can this feature be activated?
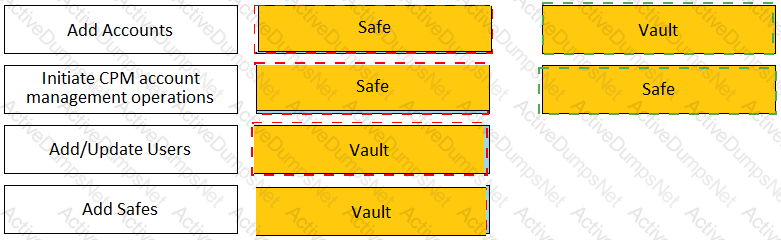
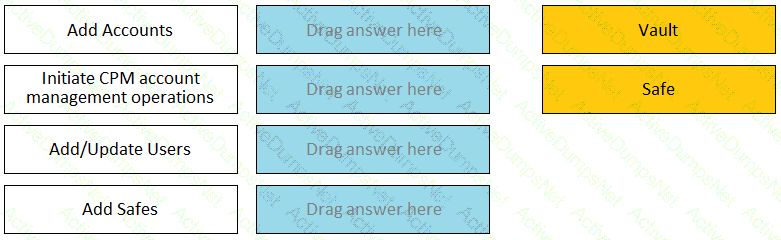
Match each permission to where it can be found.
Which usage can be added as a service account platform?
Customers who have the ‘Access Safe without confirmation’ safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
The Password upload utility can be used to create safes.
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
When on-boarding account using Accounts Feed, Which of the following is true?
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
You are helping a customer prepare a Windows server for PSM installation. What is required for a successful installation?
In a rule using “Privileged Session Analysis and Response” in PTA, which session options are available to configure as responses to activities?
Which user(s) can access all passwords in the Vault?
A customer is moving from an on-premises to a public cloud deployment. What is the best and most cost-effective option to secure the server key?
Which of the following PTA detections require the deployment of a Network Sensor or installing the PTA Agent on the domain controller?
Which option in the PrivateArk client is used to update users' Vault group memberships?
If a user is a member of more than one group that has authorizations on a safe, by default that user is granted________.
What is the purpose of a linked account?
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication.
Which locations must you update?
Which report provides a list of account stored in the vault.
Which components can connect to a satellite Vault in distributed Vault architecture?
Secure Connect provides the following. Choose all that apply.
Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?
You are creating a new Rest API user that utilizes CyberArk Authentication.
What is a correct process to provision this user?
Your organization has a requirement to allow users to “check out passwords” and connect to targets with the same account through the PSM.
What needs to be configured in the Master policy to ensure this will happen?
Within the Vault each password is encrypted by:
Which option in the Private Ark client is used to update users’ Vault group memberships?
When Dual Control is enabled a user must first submit a request in the Password Vault Web Access (PVWA) and receive approval before being able to launch a secure connection via PSM for Windows (previously known as RDP Proxy).
Which parameter controls how often the CPM looks for Soon-to-be-expired Passwords that need to be changed.
PSM captures a record of each command that was executed in Unix.
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?
CyberArk user Neil is trying to connect to the Target Linux server 192.168.1.64 using a domain account ACME/linuxuser01 on Domain Acme.corp using PSM for SSH server 192.168.65.145. What is the correct syntax?