CyberArk ACCESS-DEF CyberArk Defender Access (ACC-DEF) Exam Practice Test
CyberArk Defender Access (ACC-DEF) Questions and Answers
Which protocols can CyberArk provide MFA for VPN? (Choose two.)
You get the following error: "Not Authorized. You do not have permission to access this feature".
What is most likely the cause of the error?
When can 2FA/MFA be prompted? (Choose two.)
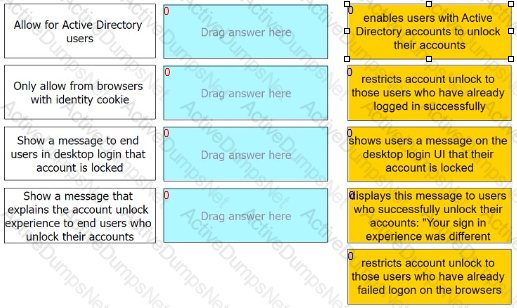
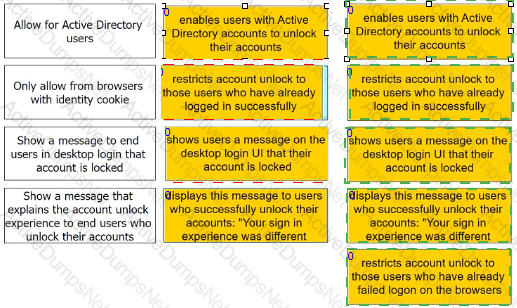
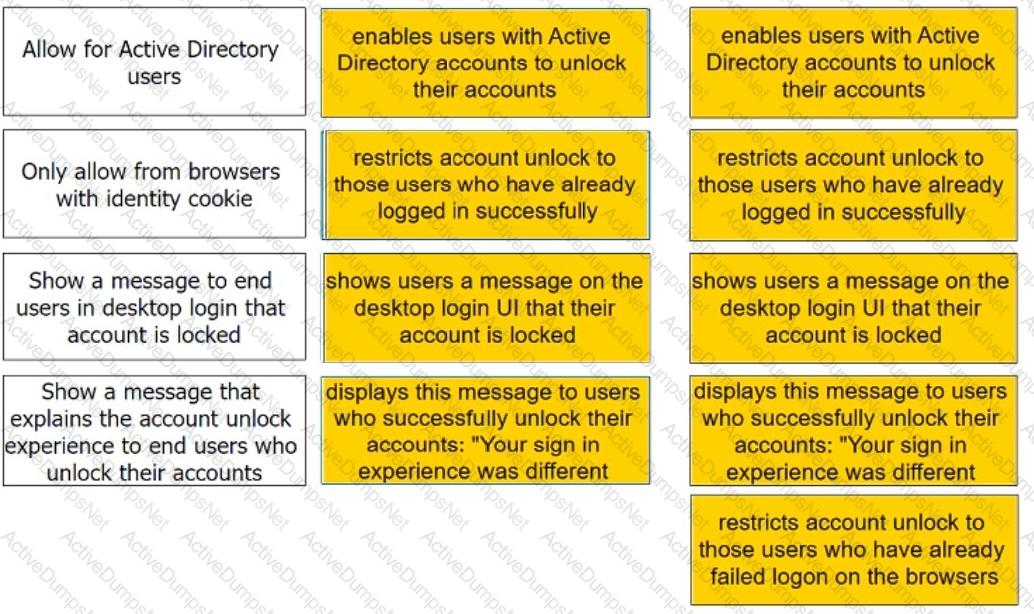
Admins can enable self-service for users to unlock their accounts. There are four options under the Admin Portal Core Services > Policies > User Security Policies > Self Service > Account Unlock options.
Match each option to the correct description.
Your organization wants to implement passwordless authentication for business critical web applications. CyberArk Identity manages access to these applications.
What can you do to facilitate the enforcement of this passwordless authentication initiative? (Choose two.)
Which dashboard can display the applications launched by users, the application type, and the number of times they were launched?
Which options are available with Self-Service Password Reset? (Choose three.)
Which device enrollment settings are valid? (Choose two.)
CyberArk Identity has created a CLI integration with which vendor?
Where can you download the CyberArk Identity mobile app? (Choose two.)
As part of an ongoing incident investigation, you want to examine all data/events that are relevant to updating user profiles.
Which dataset from the UBA portal should you use?
Refer to the exhibit.
Which statements are correct regarding this Authentication Policy? (Choose two.)

Which browsers are supported for the "Land and Catch" feature? (Choose three.)
Cindy just joined a company's IT Audit Department and needs CyberArk Identity access to perform her daily job activities.
Which administrative right(s) should she be assigned to match her job requirement?
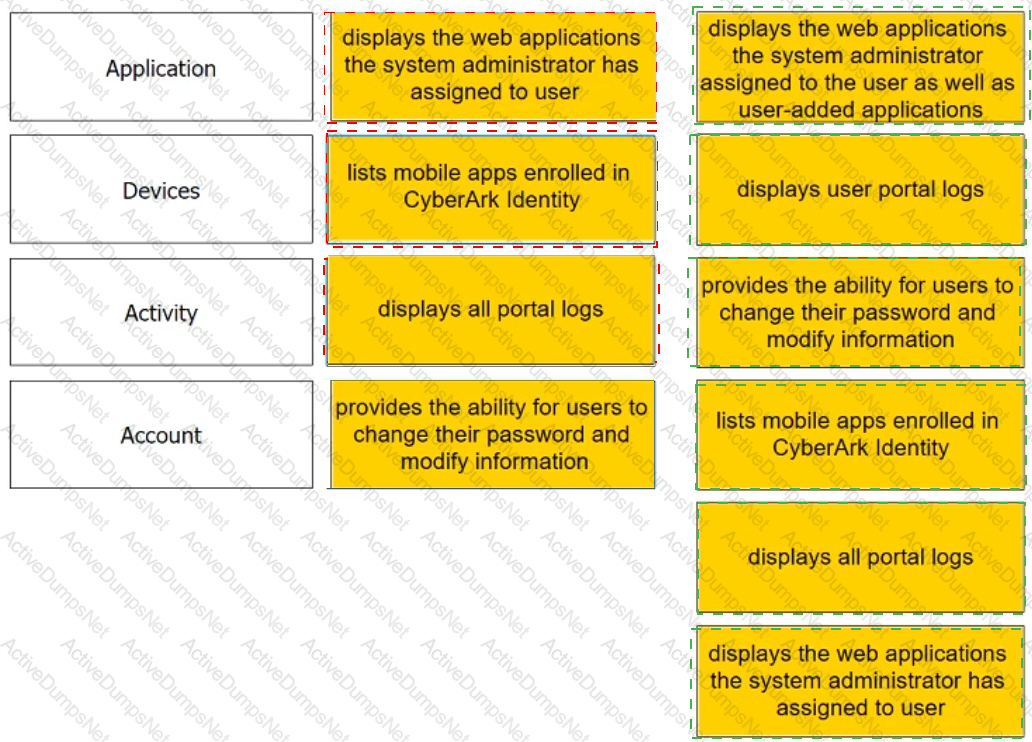
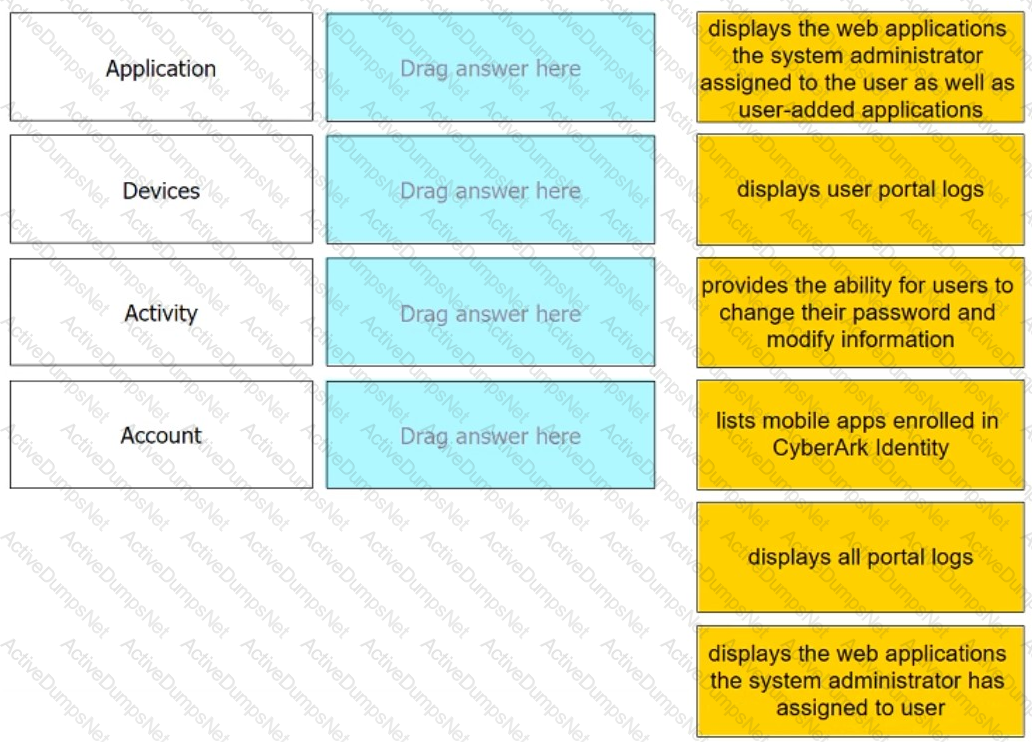
Match each User Portal tab to the correct description.
Your organization wants to limit access to the CyberArk Identity user portal to only corporate issued domain-joined laptops without the use of a VPN.
How can you achieve this?
What can cause users to be prompted for unrecognized MFA factors, such as a wrong phone number or unregistered MFA factor?
ACME Corporation employees access critical business web applications through CyberArk Identity. You notice a constant high volume of unauthorized traffic from 103.1.200.0/24 trying to gain access to the CyberArk Identity portal. Access to the CyberArk Identity portal is time sensitive. ACME decides to enforce IP restrictions to reduce vulnerability.
Which configuration can help achieve this?
When a user enrolls a mobile device (iOS or Android) without enabling mobile device management, what happens? (Choose three.)

 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg