CrowdStrike CCFH-202 CrowdStrike Certified Falcon Hunter Exam Practice Test
CrowdStrike Certified Falcon Hunter Questions and Answers
Which structured analytic technique contrasts different hypotheses to determine which is the best leading (prioritized) hypothesis?
Which of the following would be the correct field name to find the name of an event?
In the MITRE ATT&CK Framework (version 11 - the newest version released in April 2022), which of the following pair of tactics is not in the Enterprise: Windows matrix?
Which SPL (Splunk) field name can be used to automatically convert Unix times (Epoch) to UTC readable time within the Flacon Event Search?
Which document provides information on best practices for writing Splunk-based hunting queries, predefined queries which may be customized to hunt for suspicious network connections, and predefined queries which may be customized to hunt for suspicious processes?
You would like to search for ANY process execution that used a file stored in the Recycle Bin on a Windows host. Select the option to complete the following EAM query.
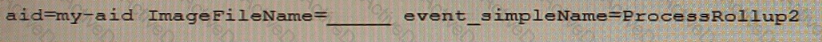
While you're reviewing Unresolved Detections in the Host Search page, you notice the User Name column contains "hostnameS " What does this User Name indicate?
Which of the following is a way to create event searches that run automatically and recur on a schedule that you set?
Lateral movement through a victim environment is an example of which stage of the Cyber Kill Chain?
