A newly identified network access vulnerability has been found in the OS of legacy loT devices. Which of the following would best mitigate this vulnerability quickly?
Which of the following alert types is the most likely to be ignored over time?
A company hired a consultant to perform an offensive security assessment covering penetration testing and social engineering.
Which of the following teams will conduct this assessment activity?
An organization experiences a cybersecurity incident involving a command-and-control server. Which of the following logs should be analyzed to identify the impacted host? (Select two).
A security engineer is implementing FDE for all laptops in an organization. Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
A company is utilizing an offshore team to help support the finance department. The company wants to keep the data secure by keeping it on a company device but does not want to provide equipment to the offshore team. Which of the following should the company implement to meet this requirement?
An attacker posing as the Chief Executive Officer calls an employee and instructs the employee to buy gift cards. Which of the following techniques is the attacker using?
A new employee accessed an unauthorized website. An investigation found that the employee violated the company's rules. Which of the following did the employee violate?
Which of the following is required for an organization to properly manage its restore process in the event of system failure?
Which of the following is a preventive physical security control?
A Chief Information Security Officer (CISO) has developed information security policies that relate to the software development methodology. Which of the following would the CISO most likely include in the organization's documentation?
A penetration test has demonstrated that domain administrator accounts were vulnerable to pass-the-hash attacks. Which of the following would have been the best strategy to prevent the threat actor from using domain administrator accounts?
A company's online shopping website became unusable shortly after midnight on January 30, 2023. When a security analyst reviewed the database server, the analyst noticed the following code used for backing up data:
Which of the following should the analyst do next?
Sine© a recent upgrade (o a WLAN infrastructure, several mobile users have been unable to access the internet from the lobby. The networking team performs a heat map survey of the building and finds several WAPs in the area. The WAPs are using similar frequencies with high power settings. Which of the following installation considerations should the security team evaluate next?
Which of the following threat actors is the most likely to use large financial resources to attack critical systems located in other countries?
Which of the following tools can assist with detecting an employee who has accidentally emailed a file containing a customer’s PII?
A systems administrator wants to use a technical solution to explicitly define file permissions for the entire team. Which of the following should the administrator implement?
A security team receives reports about high latency and complete network unavailability throughout most of the office building. Flow logs from the campus switches show high traffic on TCP 445. Which of the following is most likely the root cause of this incident?
An employee receives a text message from an unknown number claiming to be the company's Chief Executive Officer and asking the employee to purchase several gift cards. Which of the following types of attacks does this describe?
The number of tickets the help desk has been receiving has increased recently due to numerous false-positive phishing reports. Which of the following would be best to help to reduce the false positives?
Which of the following methods to secure credit card data is best to use when a requirement is to see only the last four numbers on a credit card?
A systems administrator works for a local hospital and needs to ensure patient data is protected and secure. Which of the following data classifications should be used to secure patient data?
Which of the following steps in the risk management process involves establishing the scope and potential risks involved with a project?
Which of the following security controls would best guard a payroll system against insider manipulation threats?
An enterprise is trying to limit outbound DNS traffic originating from its internal network. Outbound DNS requests will only be allowed from one device with the IP address 10.50.10.25. Which of the following firewall ACLs will accomplish this goal?
A Chief Information Security Officer would like to conduct frequent, detailed reviews of systems and procedures to track compliance objectives. Which of the following is the best method to achieve this objective?
A visitor plugs a laptop into a network jack in the lobby and is able to connect to the company's network. Which of the following should be configured on the existing network infrastructure to best prevent this activity?
A small business uses kiosks on the sales floor to display product information for customers. A security team discovers the kiosks use end-of-life operating systems. Which of the following is the security team most likely to document as a security implication of the current architecture?
During a penetration test, a vendor attempts to enter an unauthorized area using an access badge Which of the following types of tests does this represent?
During a penetration test in a hypervisor, the security engineer is able to inject a malicious payload and access the host filesystem. Which of the following best describes this vulnerability?
Which of the following best describes the practice of researching laws and regulations related to information security operations within a specific industry?
Which of the following should an organization use to protect its environment from external attacks conducted by an unauthorized hacker?
Which of the following vulnerabilities is associated with installing software outside of a manufacturer’s approved software repository?
Which of the following technologies can achieve microsegmentation?
A security analyst is reviewing the security of a SaaS application that the company intends to purchase. Which of the following documentations should the security analyst request from the SaaS application vendor?
Which of the following is the best method to reduce the attack surface of an enterprise network?
A company is aware of a given security risk related to a specific market segment. The business chooses not to accept responsibility and target their services to a different market segment. Which of the following describes this risk management strategy?
Which of the following would best prepare a security team for a specific incident response scenario?
While troubleshooting a firewall configuration, a technician determines that a “deny any” policy should be added to the bottom of the ACL. The technician updates the policy, but the new policy causes several company servers to become unreachable.
Which of the following actions would prevent this issue?
Which of the following roles, according to the shared responsibility model, is responsible for securing the company’s database in an IaaS model for a cloud environment?
A security officer observes that a software development team is not complying with its corporate security policy on encrypting confidential data. Which of the following categories refers to this type of non-compliance?
A company has yearly engagements with a service provider. The general terms and conditions are the same for all engagements. The company wants to simplify the process and revisit the general terms every three years. Which of the following documents would provide the best way to set the general terms?
A security analyst has determined that a security breach would have a financial impact of $15,000 and is expected to occur twice within a three-year period. Which of the following is the ALE for this risk?
Which of the following best describe why a process would require a two-person integrity security control?
Which of the following activities uses OSINT?
A security analyst is reviewing alerts in the SIEM related to potential malicious network traffic coming from an employee’s corporate laptop. The security analyst has determined that additional data about the executable running on the machine is necessary to continue the investigation. Which of the following logs should the analyst use as a data source?
Which of the following is the best way to securely store an encryption key for a data set in a manner that allows multiple entities to access the key when needed?
Which of the following is a possible consequence of a VM escape?
Which of the following is the most relevant reason a DPO would develop a data inventory?
Which of the following considerations is the most important for an organization to evaluate as it establishes and maintains a data privacy program?
An organization failed to account for the right-to-be-forgotten regulations. Which of the following impacts might this action have on the company?
Which of the following activities is included in the post-incident review phase?
Which of the following is an algorithm performed to verify that data has not been modified?
A company installed cameras and added signs to alert visitors that they are being recorded. Which of the following controls did the company implement? (Select two).
An attacker submits a request containing unexpected characters in an attempt to gain unauthorized access to information within the underlying systems. Which of the following best describes this attack?
Which of the following is a reason why a forensic specialist would create a plan to preserve data after an modem and prioritize the sequence for performing forensic analysis?
Which of the following strategies should an organization use to efficiently manage and analyze multiple types of logs?
Which of the following is the best way to validate the integrity and availability of a disaster recovery site?
A new employee logs in to the email system for the first time and notices a message from human resources about onboarding. The employee hovers over a few of the links within the email and discovers that the links do not correspond to links associated with the company. Which of the following attack vectors is most likely being used?
A company's accounts payable clerk receives a message from a vendor asking to change their bank account before paying an invoice. The clerk makes the change and sends the payment to the new account. Days later, the clerk receives another message from the same vendor with a request for a missing payment to the original bank account. Which of the following has most likely occurred?
Which of the following are the best for hardening end-user devices? (Selecttwo)
A company is expanding its threat surface program and allowing individuals to security test the company’s internet-facing application. The company will compensate researchers based on the vulnerabilities discovered. Which of the following best describes the program the company is setting up?
An enterprise security team is researching a new security architecture to better protect the company's networks and applications against the latest cyberthreats. The company has a fully remote workforce. The solution should be highly redundant and enable users to connect to a VPN with an integrated, software-based firewall. Which of the following solutions meets these requirements?
A company discovered its data was advertised for sale on the dark web. During the initial investigation, the company determined the data was proprietary data. Which of the following is the next step the company should take?
In a rush to meet an end-of-year business goal, the IT department was told to implement a new business application. The security engineer reviews the attributes of the application and decides the time needed to perform due diligence is insufficient from a cybersecurity perspective. Which of the following best describes the security engineer's response?
Which of the following security controls are a company implementing by deploying HIPS? (Select two).
A customer reports that software the customer downloaded from a public website has malware in it. However, the company that created the software denies any malware in its software at delivery time. Which of the following techniques will address this concern?
Which of the following has been implemented when a host-based firewall on a legacy Linux system allows connections from only specific internal IP addresses?
Which of the following describes a security alerting and monitoring tool that collects system, application, and network logs from multiple sources in a centralized system?
Users at a company are reporting they are unable to access the URL for a new retail website because it is flagged as gambling and is being blocked.
Which of the following changes would allow users to access the site?
Which of the following best describes the concept of information being stored outside of its country of origin while still being subject to the laws and requirements of the country of origin?
The Chief Information Officer (CIO) asked a vendor to provide documentation detailing the specific objectives within the compliance framework that the vendor's services meet. The vendor provided a report and a signed letter stating that the services meet 17 of the 21 objectives. Which of the following did the vendor provide to the CIO?
A security consultant needs secure, remote access to a client environment. Which of the following should the security consultant most likely use to gain access?
Which of the following explains why an attacker cannot easily decrypt passwords using a rainbow table attack?
A systems administrator receives a text message from an unknown number claiming to be the Chief Executive Officer of the company. The message states an emergency situation requires a password reset. Which of the following threat vectors is being used?
During the onboarding process, an employee needs to create a password for an intranet account. The password must include ten characters, numbers, and letters, and two special characters. Oncethe password is created, the company will grant the employee access to other company-owned websites based on the intranet profile. Which of the following access management concepts is the company most likely using to safeguard intranet accounts and grant access to multiple sites based on a user's intranet account? (Select two).
Which of the following practices would be best to prevent an insider from introducing malicious code into a company's development process?
The Chief Information Security Officer of an organization needs to ensure recovery from ransomware would likely occur within the organization's agreed-upon RPOs end RTOs. Which of the following backup scenarios would best ensure recovery?
Which of the following describes the difference between encryption and hashing?
Which of the following security principles most likely requires validation before allowing traffic between systems?
Which of the following is a type of vulnerability that refers to the unauthorized installation of applications on a device through means other than the official application store?
While investigating a recent security breach an analyst finds that an attacker gained access by SOL infection through a company website. Which of the following should the analyst recommend to the website developers to prevent this from reoccurring?
Which of the following threat actors would most likely deface the website of a high-profile music group?
Which of the following is the first step to take when creating an anomaly detection process?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
A company must ensure sensitive data at rest is rendered unreadable. Which of the following will the company most likely use?
A security analyst developed a script to automate a trivial and repeatable task. Which of the following best describes the benefits of ensuring other team members understand how the script works?
The Chief Information Security Officer wants to put security measures in place to protect PlI. The organization needs to use its existing labeling and classification system to accomplish this goal. Which of the following would most likely be configured to meet the requirements?
During a SQL update of a database, a temporary field used as part of the update sequence was modified by an attacker before the update completed in order to allow access to the system. Which of the following best describes this type of vulnerability?
Which of the following is a compensating control for providing user access to a high-risk website?
A security analyst is reviewing logs and discovers the following:

Which of the following should be used lo best mitigate this type of attack?
A systems administrator is looking for a low-cost application-hosting solution that is cloud-based. Which of the following meets these requirements?
Which of the following is a benefit of an RTO when conducting a business impact analysis?
An employee fell for a phishing scam, which allowed an attacker to gain access to a company PC. The attacker scraped the PC’s memory to find other credentials. Without cracking these credentials, the attacker used them to move laterally through the corporate network. Which of the following describes this type of attack?
During a security incident, the security operations team identified sustained network traffic from a malicious IP address:
10.1.4.9. A security analyst is creating an inbound firewall rule to block the IP address from accessing the organization’s network. Which of the following fulfills this request?
A company needs to provide administrative access to internal resources while minimizing the traffic allowed through the security boundary. Which of the following methods is most secure?
Which of the following can best contribute to prioritizing patch applications?
A Chief Information Security Officer wants to monitor the company's servers for SQLi attacks and allow for comprehensive investigations if an attack occurs. The company uses SSL decryption to allow traffic monitoring. Which of the following strategies would best accomplish this goal?
An organization's web servers host an online ordering system. The organization discovers that the servers are vulnerable to a malicious JavaScript injection, which could allow attackers to access customer payment information. Which of the following mitigation strategies would be most effective for preventing an attack on the organization's web servers? (Select two).
A company is working with a vendor to perform a penetration test Which of the following includes an estimate about the number of hours required to complete the engagement?
A spoofed identity was detected for a digital certificate. Which of the following are the type of unidentified key and the certificate mat could be in use on the company domain?
Which of the following architecture models ensures that critical systems are physically isolated from the network to prevent access from users with remote access privileges?
Which of the following is a social engineering attack in which a bad actor impersonates a web URL?
An employee clicked a malicious link in an email and downloaded malware onto the company's computer network. The malicious program exfiltrated thousands of customer records. Which of the following should the company implement to prevent this in the future?
Which of the following consequences would a retail chain most likely face from customers in the event the retailer is non-compliant with PCI DSS?
A company is developing a business continuity strategy and needs to determine how many staff members would be required to sustain the business in the case of a disruption. Which of the following best describes this step?
Which of the following activities would involve members of the incident response team and other stakeholders simulating an event?
A penetration test identifies that an SMBvl Is enabled on multiple servers across an organization. The organization wants to remediate this vulnerability in the most efficient way possible. Which of the following should the organization use for this purpose?
A company is discarding a classified storage array and hires an outside vendor to complete the disposal. Which of the following should the company request from the vendor?
A systems administrator is concerned about vulnerabilities within cloud computing instances Which of the following is most important for the administrator to consider when architecting a cloud computing environment?
The analyst wants to move data from production to the UAT server for testing the latest release. Which of the following strategies to protect data should the analyst use?
A security professional discovers a folder containing an employee's personal information on the enterprise's shared drive. Which of the following best describes the data type the securityprofessional should use to identify organizational policies and standards concerning the storage of employees' personal information?
Two companies are in the process of merging. The companies need to decide how to standardize their information security programs. Which of the following would best align the security programs?
An administrator wants to automate an account permissions update for a large number of accounts. Which of the following would best accomplish this task?
Which of the following techniques would identify whether data has been modified in transit?
Which of the following security control types does an acceptable use policy best represent?
The Cruel Information Security Officer (CISO) asks a security analyst to install an OS update to a production VM that has a 99% uptime SLA. The CISO tells me analyst the installation must be done as quickly as possible. Which of the following courses of action should the security analyst take first?
Which of the following must be considered when designing a high-availability network? (Choose two).
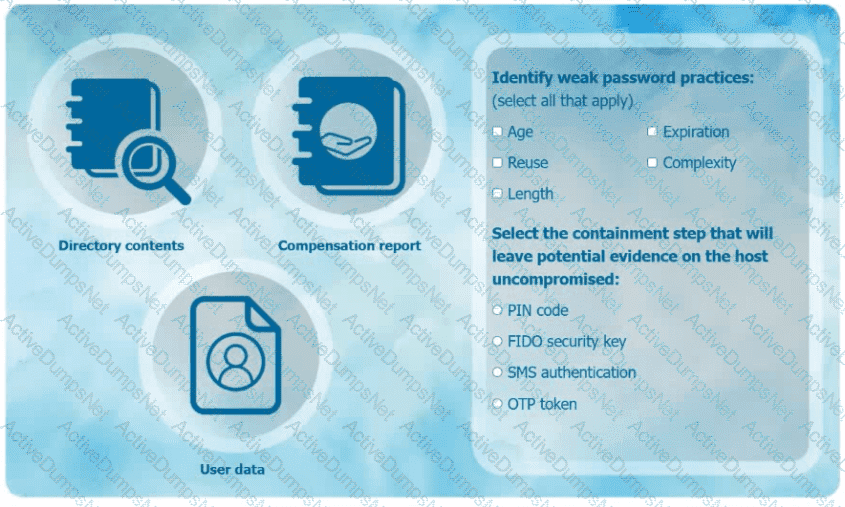
An organization has learned that its data is being exchanged on the dark web. The CIO
has requested that you investigate and implement the most secure solution to protect employee accounts.
INSTRUCTIONS
Review the data to identify weak security practices and provide the most appropriate
security solution to meet the CIO's requirements.
A forensic engineer determines that the root cause of a compromise is a SQL injection attack. Which of the following should the engineer review to identify the command used by the threat actor?
Which of the following should be used to ensure an attacker is unable to read the contents of a mobile device's drive if the device is lost?
An organization recently updated its security policy to include the following statement:
Regular expressions are included in source code to remove special characters such as $, |, ;. &, `, and ? from variables set by forms in a web application.
Which of the following best explains the security technique the organization adopted by making this addition to the policy?
A systems administrator discovers a system that is no longer receiving support from the vendor. However, this system and its environment are critical to running the business, cannot be modified, and must stay online. Which of the following risk treatments is the most appropriate in this situation?
A client asked a security company to provide a document outlining the project, the cost, and the completion time frame. Which of the following documents should the company provide to the client?
An employee decides to collect PII data from the company's system for personal use. The employee compresses the data into a single encrypted file before sending the file to their personal email. The security department becomes aware of the attempted misuse and blocks the attachment from leaving the corporate environment. Which of the following types of employee training would most likely reduce the occurrence of this type of issue?
(Select two).
Which of the following is the best way to remove personal data from a social media account that is no longer being used?
A security administrator is addressing an issue with a legacy system that communicates data using an unencrypted protocol to transfer sensitive data to a third party. No software updates that use an encrypted protocol are available, so a compensating control is needed. Which of the following are the most appropriate for the administrator to suggest? (Select two.)
Which of the following activities should a systems administrator perform to quarantine a potentially infected system?
An organization’s internet-facing website was compromised when an attacker exploited a buffer overflow. Which of the following should the organization deploy to best protect against similar attacks in the future?
A security analyst discovers that a large number of employee credentials had been stolen and were being sold on the dark web. The analyst investigates and discovers that some hourly employee credentials were compromised, but salaried employee credentials were not affected.
Most employees clocked in and out while they were Inside the building using one of the kiosks connected to the network. However, some clocked out and recorded their time after leaving to go home. Only those who clocked in and out while Inside the building had credentials stolen. Each of the kiosks are on different floors, and there are multiple routers, since the business segments environments for certain business functions.
Hourly employees are required to use a website called acmetimekeeping.com to clock in and out. This website is accessible from the internet. Which of the following Is the most likely reason for this compromise?
A company is in the process of cutting jobs to manage costs. The Chief Information Security Officer is concerned about the increased risk of an insider threat. Which of the following would most likely help the security awareness team address this potential threat?
A user is attempting to patch a critical system, but the patch fails to transfer. Which of the following access controls is most likely inhibiting the transfer?
A site reliability engineer is designing a recovery strategy that requires quick failover to an identical site if the primary facility goes down. Which of the following types of sites should the engineer consider?
Which of the following is a risk of conducting a vulnerability assessment?
A company wants to ensure employees are allowed to copy files from a virtual desktop during the workday but are restricted during non-working hours. Which of the following security measures should the company set up?
To which of the following security categories does an EDR solution belong?
The security operations center is researching an event concerning a suspicious IP address A security analyst looks at the following event logs and discovers that a significant portion of the user accounts have experienced faded log-In attempts when authenticating from the same IP address:

Which of the following most likely describes attack that took place?
Which of the following best describe the benefits of a microservices architecture when compared to a monolithic architecture? (Select two).
A security administrator would like to protect data on employees’ laptops. Which of the following encryption techniques should the security administrator use?
Which of the following is the best mitigation for a zero-day vulnerability found in mission-critical production servers that must be highly available?
A new vulnerability enables a type of malware that allows the unauthorized movement of data from a system. Which of the following would detect this behavior?
Which of the following examples would be best mitigated by input sanitization?
Which of the following explains how to determine the global regulations that data is subject to regardless of the country where the data is stored?
An organization is adopting cloud services at a rapid pace and now has multiple SaaS applications in use. Each application has a separate log-in. so the security team wants to reduce the number of credentials each employee must maintain. Which of the following is the first step the security team should take?
A company wants to track modifications to the code used to build new virtual servers. Which of the following will the company most likely deploy?
Which of the following can best protect against an employee inadvertently installing malware on a company system?
A security administrator needs a method to secure data in an environment that includes some form of checks so that the administrator can track any changes. Which of the following should the administrator set up to achieve this goal?
A security analyst needs to propose a remediation plan 'or each item in a risk register. The item with the highest priority requires employees to have separate logins for SaaS solutions and different password complexity requirements for each solution. Which of the following implementation plans will most likely resolve this security issue?
An administrator needs to perform server hardening before deployment. Which of the following steps should the administrator take? (Select two).
A company is implementing a policy to allow employees to use their personal equipment for work. However, the company wants to ensure that only company-approved applications can be installed. Which of the following addresses this concern?
Which of the following would most likely be used by attackers to perform credential harvesting?
Which of the following should an internal auditor check for first when conducting an audit of the organization's risk management program?
Which of the following allows for the attribution of messages to individuals?
The Chief Information Security Officer wants to discuss options for a disaster recovery site that allows the business to resume operations as quickly as possible. Which of the following solutions meets this requirement?
A security team is reviewing the findings in a report that was delivered after a third party performed a penetration test. One of the findings indicated that a web application form field is vulnerable to cross-site scripting. Which of the following application security techniques should the security analyst recommend the developer implement to prevent this vulnerability?
An employee who was working remotely lost a mobile device containing company data. Which of the following provides the best solution to prevent future data loss?
Employees located off-site must have access to company resources in order to complete their assigned tasks These employees utilize a solution that allows remote access without interception concerns. Which of the following best describes this solution?
A company makes a change during the appropriate change window, but the unsuccessful change extends beyond the scheduled time and impacts customers. Which of the following would prevent this from reoccurring?
A group of developers has a shared backup account to access the source code repository. Which of the following is the best way to secure the backup account if there is an SSO failure?
Which of the following can be used to mitigate attacks from high-risk regions?
Which of the following is prevented by proper data sanitization?
Which of the following describes the reason for using an MDM solution to prevent jailbreaking?
An organization is required to provide assurance that its controls are properly designed and operating effectively. Which of the following reports will best achieve the objective?
Which of the following is a use of CVSS?
Which of the following is the final step of the modem response process?
A security report shows that during a two-week test period. 80% of employees unwittingly disclosed their SSO credentials when accessing an external website. The organization purposelycreated the website to simulate a cost-free password complexity test. Which of the following would best help reduce the number of visits to similar websites in the future?
A security administrator needs to reduce the attack surface in the company's data centers. Which of the following should the security administrator do to complete this task?
A security analyst is creating the first draft of a network diagram for the company's new customer-facing payment application that will be hosted by a third-party cloud service
provider.
An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device.
Which of the following best describes the user’s activity?
Which of the following would best allow a company to prevent access to systems from the Internet?
A company is implementing a vendor's security tool in the cloud. The security director does not want to manage users and passwords specific to this tool but would rather utilize the company's standard user directory. Which of the following should the company implement?
A newly appointed board member with cybersecurity knowledge wants the board of directors to receive a quarterly report detailing the number of incidents that impacted the organization. The systems administrator is creating a way to present the data to the board of directors. Which of the following should the systems administrator use?
Which of the following is a feature of a next-generation SIEM system?
A security manager created new documentation to use in response to various types of security incidents. Which of the following is the next step the manager should take?
A network manager wants to protect the company's VPN by implementing multifactor authentication that uses:
. Something you know
. Something you have
. Something you are
Which of the following would accomplish the manager's goal?
Which of the following can be best used to discover a company's publicly available breach information?
A technician wants to improve the situational and environmental awareness of existing users as they transition from remote to in-office work. Which of the following is the best option?
After completing an annual external penetration test, a company receives the following guidance:
Decommission two unused web servers currently exposed to the internet.
Close 18 open and unused ports found on their existing production web servers.
Remove company email addresses and contact info from public domain registration records.
Which of the following does this represent?
A network engineer is increasing the overall security of network devices and needs to harden the devices. Which of the following will best accomplish this task?
Which of the following exercises should an organization use to improve its incident response process?
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
A database administrator is updating the company's SQL database, which stores credit card information for pending purchases. Which of the following is the best method to secure the data against a potential breach?
Several customers want an organization to verify its security controls are operating effectively and have requested an independent opinion. Which of the following is the most efficient way to address these requests?
Which of the following security concepts is the best reason for permissions on a human resources fileshare to follow the principle of least privilege?
Which of the following is used to protect a computer from viruses, malware, and Trojans being installed and moving laterally across the network?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
Which of the following describes a situation where a user is authorized before being authenticated?
An organization is looking to optimize its environment and reduce the number of patches necessary for operating systems. Which of the following will best help to achieve this objective?
A company recently decided to allow employees to work remotely. The company wants to protect us data without using a VPN. Which of the following technologies should the company Implement?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
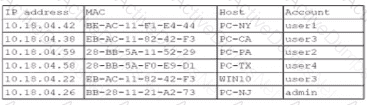
Which of the following is the most likely way a rogue device was allowed to connect?
Which of the following actions best addresses a vulnerability found on a company's web server?
A systems administrator is working on a solution with the following requirements:
• Provide a secure zone.
• Enforce a company-wide access control policy.
• Reduce the scope of threats.
Which of the following is the systems administrator setting up?