A company recently implemented a videoconferencing system that utilizes large amounts of bandwidth. Users start reporting slow internet speeds and an overall decrease in network performance. Which of the following are most likely the causes of the network performance issues? (Select two)
Which of the following network topologies contains a direct connection between every node in the network?
A network administrator is notified that a user cannot access resources on the network. The network administrator checks the physical connections to the workstation labeled User 3 and sees the Ethernet is properly connected. However, the network interface’s indicator lights are not blinking on either the computer or the switch. Which of the following Is the most likely cause?
Which of the following can also provide a security feature when implemented?
Which of the following steps of the troubleshooting methodology comes after testing the theory to determine cause?
A systems administrator is investigating why users cannot reach a Linux web server with a browser but can ping the server IP. The server is online, the web server process is running, and the link to the switch is up. Which of the following commands should the administrator run on the server first?
A technician is troubleshooting a user's laptop that is unable to connect to a corporate server. The technician thinks the issue pertains to routing. Which of the following commands should the technician use to identify the issue?
Which of the following is created to illustrate the effectiveness of wireless networking coverage in a building?
Which of the following protocols uses the Dijkstra's Link State Algorithm to establish routes inside its routing table?
A network technician needs to install patch cords from the UTP patch panel to the access switch for a newly occupied set of offices. The patch panel is not labeled for easy jack identification. Which of the following tools provides the easiest way to identify the appropriate patch panel port?
Which of the following protocol ports should be used to securely transfer a file?
A network engineer configures the network settings in a new server as follows:
IP address = 192.163.1.15
Subnet mask = 255.255.255.0
Gateway = 192.163.1.255
The server can reach other hosts on the same subnet successfully, but it cannot reach hosts on different subnets. Which of the following is most likely configured incorrectly?
A network administrator needs to assign IP addresses to a newly installed network. They choose 192.168.1.0/24 as their network address and need to create three subnets with 30 hosts on each subnet. Which of the following is a valid subnet mask that will meet the requirements?
A network administrator is unable to ping a remote server from a newly connected workstation that has been added to the network. Ping to 127.0.0.1 on the workstation is failing. Which of the following should the administrator perform to diagnose the problem?
As part of an attack, a threat actor purposefully overflows the content-addressable memory (CAM) table on a switch. Which of the following types of attacks is this scenario an example of?
A network engineer runs ipconfig and notices that the default gateway is 0.0.0.0. Which of the following address types is in use?
Which of the following is most commonly associated with many systems sharing one IP address in the public IP-addressing space?
A network administrator deploys several new desk phones and workstation cubicles. Each cubicle has one assigned switchport. The administrator runs the following commands:
nginx
CopyEdit
switchport mode access
switchport voice vlan 69
With which of the following VLANs will the workstation traffic be tagged?
A user cannot access an external server for a client after connecting to a VPN. Which of the following commands would a support agent most likely use to examine the issue? (Select two).
Which of the following devices can operate in multiple layers of the OSI model?
Which of the following is a characteristic of the application layer?
A network technician is troubleshooting the connection to the company website. The traceroute command produces the following output:
Traceroute towww.mysite.com(8.8.8.8) over a maximum of 30 hops
10.1.1.1 <1 ms 2. * <1 ms <1 ms
k k
k kTraceroute completeWhich of the following should the technician do to identify the path to the server?
You have been tasked with implementing an ACL on the router that will:
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network technician sets up a computer on the accounting department floor for a user from the marketing department. The user reports that they cannot access the marketing department’s shared drives but can access the internet. Which of the following is the most likely cause of this issue?
A storage network requires reduced overhead and increased efficiency for the amout of data being sent. Which of the following should an engineer likely configure to meet these requirements>?
Which of the following should be used to obtain remote access to a network appliance that has failed to start up properly?
Which of the following protocols has a default administrative distance value of 90?
A network engineer needs to order cabling to connect two buildings within the same city. Which of the following media types should the network engineer use?
Which of the following disaster recovery concepts is calculated by dividing the total hours of operation by the total number of units?
A network engineer is setting up a new VoIP network for a customer. The current network is segmented only for computers and servers. No additional switch ports can be used in the new network. Which of the following does the engineer need to do to configure the network correctly? (Select TWO).
Which of the following attacks utilizes a network packet that contains multiple network tags?
Which of the following does a full-tunnel VPN provide?
Which of the following allows a standard user to log in to multiple resources with one account?
A network administrator installed a new VLAN to the network after a company added an additional floor to the office. Users are unable to obtain an IP address on the new VLAN, but ports on existing VLANs are working properly. Which of the following configurations should the administrator update?
A network administrator wants to restrict inbound traffic to allow only HTTPS to the company website, denying all other inbound traffic from the internet. Which of the following would best accomplish this goal?
Which of the following network devices converts wireless signals to electronic signals?
A systems administrator is configuring a new device to be added to the network. The administrator is planning to perform device hardening prior to connecting the device. Which of the following should the administrator do first?
A user's desk has a workstation and an IP phone. The user is unable to browse the internet on the workstation, but the phone works. Which of the following configurations is required?
An employee in a corporate office clicks on a link in an email that was forwarded to them. The employee is redirected to a splash page that says the page is restricted. Which of the following security solutions is most likely in place?
A user's home mesh wireless network is experiencing latency issues. A technician has:
•Performed a speed test.
•Rebooted the devices.
•Performed a site survey.
•Performed a wireless packet capture.
The technician reviews the following information:
The technician notices in the packet capture that frames were retransmitted. Which of the following is the most likely cause of the user's network issue?
Which of the following is the most cost-effective way for a network administrator to establish a persistent, secure connection between two facilities?
A company wants to implement data loss prevention by restricting user access to social media platforms and personal cloud storage on workstations. Which of the following types of filtering should the company deploy to achieve these goals?
A technician is deploying new networking hardware for company branch offices. The bridge priority must be properly set. Which of the following should the technician configure?
While troubleshooting a VoIP handset connection, a technician's laptop is able to successfully connect to network resources using the same port. The technician needs to identify the port on the switch. Which of the following should the technician use to determine the switch and port?
Which of the following layers in the OSI model is responsible for establishing, maintaining, and terminating connections between nodes?
A network administrator is configuring access points for installation in a dense environment where coverage is often overlapping. Which of the following channel widths should the administrator choose to help minimize interference in the 2.4GHz spectrum?
A newtwork administrator needs to create an SVI on a Layer 3-capable device to separate voice and data traffic. Which of the following best explains this use case?
A detective is investigating an identity theft case in which the target had an RFID-protected payment card issued and compromised in the same day. The only place the target claims to have used the card was at a local convenience store. The detective notices a video camera at the store is placed in such a way that customers' credentials can be seen when they pay. Which of the following best explains this social engineering technique?
A network manager wants to implement a SIEM system to correlate system events. Which of the following protocols should the network manager verify?
A virtual machine has the following configuration:
•IPv4 address: 169.254.10.10
•Subnet mask: 255.255.0.0
The virtual machine can reach colocated systems but cannot reach external addresses on the Internet. Which of the following Is most likely the root cause?
A network technician is installing a new switch that does not support STP at the access layer of a network. The technician wants a redundant connection to the distribution switch. Which of the following should the technician use?
A network administrator changed an external DNS to point customers to a new server. Which of the following tools should the administrator use to test the new server's configuration?
A network administrator notices uncommon communication between VMs on ephemeral ports on the same subnet. The administrator is concerned about that traffic moving laterally within the network. Which of the following describes the type of traffic flow the administrator is analyzing?
A network engineer is deploying switches at a new remote office. The switches have been preconfigured with hostnames and STP priority values. Based on the following table:
Switch Name
Priority
core-sw01
24576
access-sw01
28672
distribution-sw01
32768
access-sw02
36864
Which of the following switches will become the root bridge?
Which of the following is the most likely reason an insurance brokerage would enforce VPN usage?
An organization wants to ensure that incoming emails were sent from a trusted source. Which of the following DNS records is used to verify the source?
After installing a series of Cat 8 keystones, a data center architect notices higher than normal interference during tests. Which of the following steps should the architect take to troubleshoot the issue?
Which of the following routing technologies uses an attribute list for path selection?
Which of the following is enforced through legislation?
An administrator is setting up an SNMP server for use in the enterprise network and needs to create device IDs within a MIB. Which of the following describes the function of a MIB?
A network administrator needs to connect a department to a new network segment. They need to use a DHCP server located on another network. Which of the following can the administrator use to complete this task?
A technician is planning an equipment installation into a rack in a data center that practices hot aisle/cold aisle ventilation. Which of the following directions should the equipment exhaust face when installed in the rack?
A client wants to increase overall security after a recent breach. Which of the following would be best to implement? (Select two.)
Which of the following requires network devices to be managed using a different set of IP addresses?
A customer calls the help desk to report issues connection to the internet. The customer can reach a local database server. A technician goes to the site and examines the configuration:
Which of the following is causing the user's issue?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host's TCP/IP stack first. Which of the following commands should the network administrator run?
Which of the following is the step that a troubleshooter should take immediately after implementing a solution?
Which of the following can be used when a server at a remote site is physically unreachable?
A technician is designing a cloud service solution that will accommodate the company's current size, compute capacity, and storage capacity. Which of the following cloud deployment models will fulfill these requirements?
Which of the following OSI model layers can utilize a connectionless protocol for data transmission?
A network technician is attempting to harden a commercial switch that was recently purchased. Which of the following hardening techniques best mitigates the use of publicly available information?
Which of the following would be violated if an employee accidentally deleted a customer's data?
A network technician is terminating a cable to a fiber patch panel in the MDF. Which of the following connector types is most likely in use?
A network administrator wants to configure a backup route in case the primary route fails. A dynamic routing protocol is not installed on the router. Which of the following routing features should the administrator choose to accomplish this task?
Newly crimped 26ft (8m) STP Cat 6 patch cables were recently installed in one room to replace cables that were damaged by a vacuum cleaner. Now, users in that room are unable to connect to the network. A network technician tests the existing cables first. The 177ft (54m) cable that runs from the core switch to the access switch on the floor is working, as is the 115ft (35m) cable run from the access switch to the wall jack in the office. Which of the following is the most likely reason the users cannot connect to the network?
A network engineer is designing an internal network that needs to support both IPv4 and IPv6 routing. Which of the following routing protocols is capable of supporting both IPv4 and IPv6?
Which of the following is the next step to take after successfully testing a root cause theory?
A network administrator is planning to host a company application in the cloud, making the application available for all internal and third-party users. Which of the following concepts describes this arrangement?
A network architect needs to create a wireless field network to provide reliable service to public safety vehicles. Which of the following types of networks is the best solution?
A network administrator recently upgraded a wireless infrastructure with new APs. Users report that when stationary, the wireless connection drops and reconnects every 20 to 30 seconds. While reviewing logs, the administrator notices the APs are changing channels.
Which of the following is the most likely reason for the service interruptions?
A company is implementing a wireless solution in a high-density environment. Which of the following 802.11 standards is used when a company is concerned about device saturation and converage?
Users at an organization report that the wireless network is not working in some areas of the building. Users report that other wireless network SSIDs are visible when searching for the network, but the organization's network is not displayed. Which of the following is the most likely cause?
A network administrator needs to fail over services to an off-site environment. This process will take four weeks to become fully operational. Which of the following DR (Disaster Recovery) concepts does this describe?
During a recent security assessment, an assessor attempts to obtain user credentials by pretending to be from the organization's help desk. Which of the following attacks is the assessor using?
A small business is deploying new phones, and some of the phones have full HD videoconferencing features. The Chief Information Officer (CIO) is concerned that the network might not be able to handle the traffic if it reaches a certain threshold. Which of the following can the network engineer configure to help ease these concerns?
A network administrator notices interference with industrial equipment in the 2.4GHz range. Which of the following technologies would most likely mitigate this issue? (Select two).
A network architect is implementing an off-premises computing facility and needs to ensure that operations will not be impacted by major outages. Which of the following should the architect consider?
A network administrator is planning to implement device monitoring to enhance network visibility. The security that the solution provides authentication and encryption. Which of the following meets these requirements?
A network administrator suspects users are being sent to malware sites that are posing as legitimate sites. The network administrator investigates and discovers that user workstations are configured with incorrect DNS IP addresses. Which of the following should the network administrator implement to prevent this from happening again?
Which of the following routing protocols is most commonly used to interconnect WANs?
After installing a new wireless access point, an engineer tests the device and sees that it is not performing at the rated speeds. Which of the following should the engineer do to troubleshoot the issue? (Select two.)
A network engineer wants to implement a new IDS between the switch and a router connected to the LAN. The engineer does not want to introduce any latency by placing the IDS in line with the gateway. The engineer does want to ensure that the IDS sees all packets without any loss. Which of the following is the best way for the engineer to implement the IDS?
An IT department asks a newly hired employee to use a personal laptop until the company can provide one. Which of the following policies is most applicable to this situation?
A Chief Executive Officer (CEO) of a company purchases a new phone that will be used while traveling to different countries. The CEO needs to be able to place outgoing calls and receive incoming calls on the phone using a SIM card. Which of the following cellular technologies does the CEO's phone need?
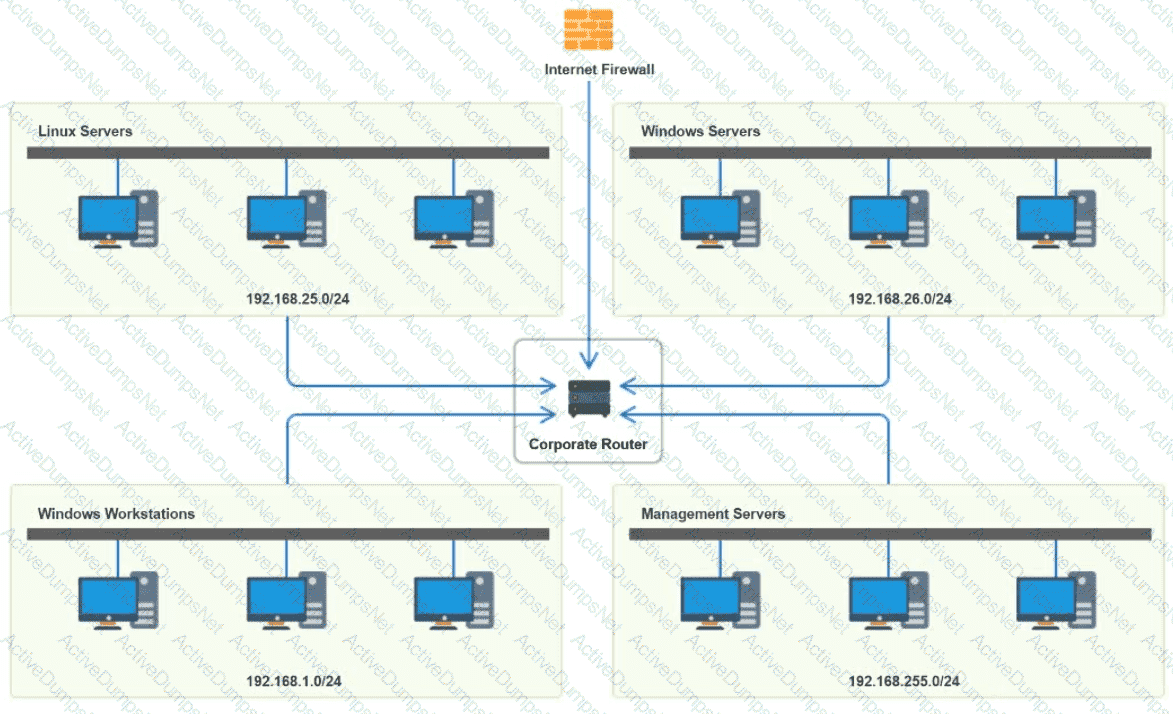
A network technician is troubleshooting network latency and has determined the issue to be occuring two network switches( Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying. Given the following informtion:
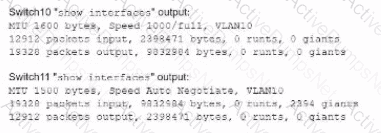
Which of the following should the technician most likely do to resolve the issue?
Which of the following connectors provides console access to a switch?
Which of the following indicates a computer has reached end-of-support?
A network administrator upgraded the wireless access points and wants to implement a configuration that will give users higher speed and less channel overlap based on device compatibility. Which of the following will accomplish this goal?
A user reports having intermittent connectivity issues to the company network. The network configuration for the user reveals the following:
IP address: 192.168.1.10
Subnet mask: 255.255.255.0
Default gateway: 192.168.1.254
The network switch shows the following ARP table:
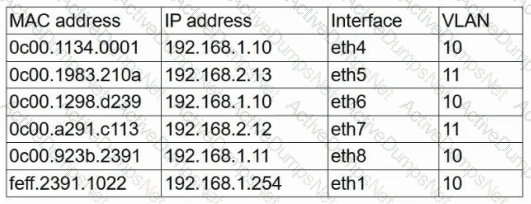
Which of the following is the most likely cause of the user's connection issues?