Which of the following diagnostic commands relies on proper forwarding of ICMP ECHO packets?
A company has attempted to introduce a new major network segment to allow growth in capacity. On the core switch, a GBIC was used to interconnect with a newly placed downstream distribution switch for the first time. Soon after this implementation, a network flood and an outage occurred between the core and new distribution network modules. Which of the following should the network administrator troubleshoot FIRST in order to rectify the issue?
The network technician is working in an office that has both VoIP telephone lines and analog lines. A user states that the fax machine is not sending or receiving faxes. The network technician determines that the fax machine uses an analog phone line. Which of the following tools would the technician use to troubleshoot the issue?
Which of the following DNS records is used to identify a domain’s SMTP server?
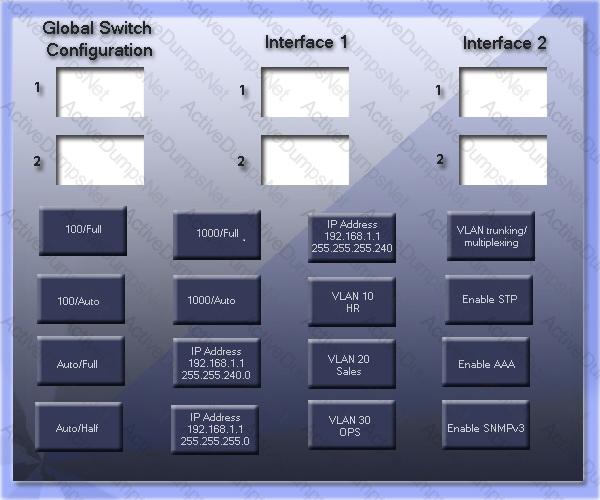
GigSwitch1 is currently configured with a speed of 100 and Duplex is set to Auto on all interfaces. Interface 2 will be connected to GigSwitch2 which is used for all departments. Interface 1 will be used for HR traffic only.
GigSwitch1 needs to be configured with the following parameters:
Configure the necessary protocol to prevent switching loops
Configure GigSwitch1 with a /24 IP address for management
Traffic across Interface 1 needs to be forced to accept and receive up to 100Mbps data at the same time
Traffic across Interface 2 needs to be forced to use Gigabit speeds and maximum performance
Drag and drop the appropriate configurations to their corresponding requirements. All placeholders must be filled. Not all configurations will be used.
Companies trying to cut down on constant documentation of IP addresses could use which of the following?
A supervisor requests that a technician downloads a MIB for a particular server. Which of the following protocols requires MIBs?
Which of the following connector types are used in terminating singlemode fiber cables? (Select TWO).
A home user wishes to secure the wireless network using strong encryption, so they decide to use AES. Which of the following would be used as the encryption method?
A company wants to secure its WAPs from unauthorized access. Which of the following is the MOST secure wireless encryption method?
Which of the following is the correct representation of an IPv6 address?
Which of the following can be used to decrypt SSL packets which encapsulate internal network addresses in the payload?
On which of the following layers of the OSI model does IP operate?
Which of the following problems is MOST likely to arise when configuring an IPv6 over IPv4 tunnel?
Ann, a new user, is unable to communicate on the network from her computer. A technician has verified that the cables are functioning properly. Based on the information below, which action should the technician take to correct Ann’s problem?
Computer_ASwitch_A
IP: 10.0.0.60Int VLAN10
SM: 255.255.255.0IP address 10.0.0.1/28
GW: 10.0.0.1Speed 100 Duplex Full
Which of the following port numbers needs to be open on a firewall to allow FTP traffic?
Which of the following can a technician use when installing a wireless network in a lounge to prevent inappropriate website images?
A user calls the helpdesk to report not being able to access network resources over the company’s Wi-Fi connection. During information gathering, the user mentions that the wireless network their computer is signed into is not the same name as it had been previously. Which of the following is the underlying cause?
Which of the following can determine the last time an address lease was renewed on a network device?
Which of the following is used to assign an IP address to a device?
A user is getting very weak signals while trying to connect to the wireless. Which of the following should the user do to help with signal strength?
Lisa, a technician, has configured a new switch that is remotely accessed using SSH. The switch is working properly but cannot be accessed remotely. Which of the following items is MOST likely missing in the configuration?
Which of the following is the Telco end of a T1 demarc?
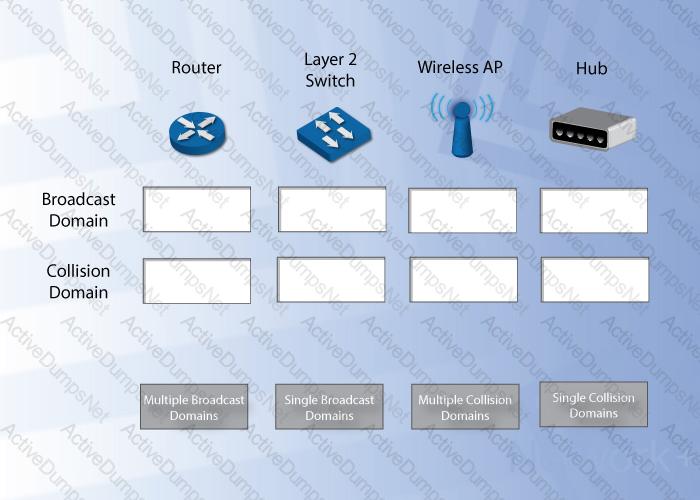
Under each network device, drag and drop the associated broadcast and/or collison description. Objects may be used multiple times, as needed.
Which of the following attacks would allow an intruder to do port mapping on a company’s internal server from a separate company server on the Internet?
Which of the following capabilities of a firewall allows Zach, an administrator, to block traffic based on key words determined by the company?
A technician needs to enter a username and password and have their fingerprint scanned to access a server. Which of following types of authentication is this an example of?
Which of the following is an authentication, authorization, and accounting method that provides administrative access to network devices?
Which of the following tools will scan a network for hosts and provide information on the installed operating system?
A company has only three laptops that connect to their wireless network. The company is currently using WEP encryption on their wireless network. They have noticed unauthorized connections on their WAP and want to secure their wireless connection to prevent this. Which of the following security measures would BEST secure their wireless network? (Select TWO).
Which of the following security appliances would be used to only analyze traffic and send alerts when predefined patterns of unauthorized traffic are detected on the network?
A user receives a phone call at home from someone claiming to be from their company’s IT help desk. The help desk person wants to verify their username and password to ensure that the user’s account has not been compromised. Which of the following attacks has just occurred?
A technician is asked to filter inbound and outbound traffic of a specific service on the network. Which of the following would BEST allow the technician to comply with the request?
Which of the following is used to determine whether or not a user’s account is authorized to access a server remotely?
Which of the following network tools is used to identify running services on host devices?
Which of the following network access security methods ensures communication occurs over a secured, encrypted channel, even if the data uses the Internet?
Lisa, a network administrator, wants to be able to block all already known malicious activity. Which of the following would allow her to perform this activity?
A network administrator wishes to limit the number of potential wireless clients to 20 on a specific AP. Which of the following settings needs to be changed?
An administrator determines there are an excessive number of packets being sent to a web server repeatedly by a small number of external IP addresses. This is an example of which of the following attacks?
A network administrator is tasked with blocking unwanted spam which is being relayed by an internal email server. Which of the following is the FIRST step in preventing spam that is originating from bots on the network?
A user is connecting to the Internet at an airport through an ad-hoc connection. Which of the following is the MOST likely security threat?
Joe, a network technician, is implementing a wireless network and needs to support legacy devices. He has selected to use WPA mixed mode. WPA mixed mode is normally implemented with which of the following encryption factors? (Select TWO).
The company requires all users to authenticate to the network with a smart card, a pin number, and a fingerprint scan. Which of the following BEST describes the user authentication being used?
Which of the following is the MOST secure way to prevent malicious changes to a firewall?
Before installing a wireless network, which of the following should Karen, a network technician, take into consideration to reduce signal exposure for war drivers?
Which of the following tools could attempt to detect operating system vulnerabilities?
Which of the following should be mitigated by employing proper coding techniques when developing software?
A company wishes to have a wireless signal broadcast only through a specific stretch of a highway tunnel. Which of the following measures will accomplish this?
Which of the following tools would a technician use to terminate CAT6 wires to the inside of the wall jack?
Which of the following hardware tools would MOST likely be used to verify Layer 1 connectivity?
A technician testing an Ethernet card uses a cable wired with pins 1,2 to pins 3,6 on the same RJ-45 plug. Which of the following describes what the technician is using?
Kim, a network technician, wants to use a packet analyzer to troubleshoot a reported problem with a user’s workstation with IP address 192.168.1.45. To identify the workstation’s packets Kim wants to use the workstation’s MAC address. Which of the following protocols would provide the needed information?
Which of the following network appliances can BEST be described as allowing multiple servers to share requests for a website through the same public IP address?
Which of the following features can BEST be used to facilitate authorized remote access to a network?
Teachers and students at a school currently share the same bandwidth. The Internet performance for the teachers in the classroom is becoming extremely slow. Which of the following is the BEST method to mitigate the issue?
An administrator would like to decrease the load time of common websites that employees review daily. Which of the following can be installed?
A network administrator suspects that recent traffic problems could be caused by a high CPU load on company routers. Which of the following would BEST be used to monitor CPU cycles on the routers?
Jeff, a network technician, arrives to work and discovers users are having a problem connecting the company server. The server operator was working on upgrades the night before. Which of the following documents should Jeff use to attempt to discover the problem?
Port scanners and packet sniffers differ in functionality because:
A security appliance is blocking a DDoS attack on the network. Which of the following logs would be used to troubleshoot the traffic patterns trying to go across the network?
After installing new cabling, Karen, a technician, notices that several computers are connecting to network resources very slowly. Which of the following tools would BEST help in determining if the new cabling is the cause of the problem?
Karen, a network technician, is troubleshooting in a wiring closet in 2011. The cabling to all the equipment does not match the documentation from 2007. Which of the following configuration management methods has been overlooked?
Which of the following is used to filter outgoing network requests?
Lisa, an administrator, wants to limit the wireless guest network traffic to 100Kbps so that utilization issues do not occur on the company’s T1 Internet access network. Which of the following optimizations should Lisa implement?
Which of the following devices should Jeff, an administrator, connect to a protocol analyzer in order to collect all of the traffic on a LAN segment?
A VPN concentrator is used for which of the following purposes?
A server that filters traffic between a WAN and a LAN is which of the following?
Which of the following does SNMPv3 BEST provide over previous versions?
A network administrator is reviewing logs and notices that a device with a public IP address is trying to access the web server RDP port. Which of the following tools can be used to resolve the domain of the public IP address?
Which of the following is used to limit the amount of bandwidth used on a link for different applications to improve overall performance?
Users have reported choppy audio in phone conversations since the implementation of SIP phones on the network. Which of the following should be implemented to alleviate the delays?
A technician has traced a POTS line to a 110 block. Which of the following devices would the technician MOST likely use to see if the line carries a dial tone?
A patch cable terminated with one end as T568A and the other as T568B will create which of the following cable types?
An 802.11b wireless network has a maximum data rate of:
The network technician needs to install fiber cabling to connect two buildings less than 984 feet (300 meters) apart. Which of the following fiber types should be installed?
Which of the following connector types would require a punch down tool to attach a network cable to it?
After Karen, a new user, moves furniture into a cubicle, the computer does not connect to the network any longer. Which of the following would be the MOST likely reason? (Select TWO).
Which of the following colors represents the outer leads on a connector head of a 568B patch cable? (Select TWO).
Which of the following defines the pinout of an 8P8C eight pin modular jack for a CAT6a cable?
A network administrator has just been notified about the loss of Internet connectivity. Another technician had just performed non-scheduled maintenance and mentioned that some cabling may have been moved. Which of the following MOST likely caused the loss of Internet connectivity?
Which of the following network topologies is MOST likely used in remote access VPN?
Lisa, a technician, is reporting wireless transmission speeds of 300Mbps. Which of the following wireless standards is being used?
Which of the following connectors would be found on a fiber optic cable?
Which of the following cable types would have the LEAST amount of EMI?
Which of the following cable types is required to run through an air duct?
Which of the following 802.3 classifications has a MAXIMUM segment distance of 984 feet (300 meters)?
When examining a suspected faulty copper network cable, Kim, the administrator, notices that some of the pairs are untwisted too much. This is MOST likely causing which of the following?
Which of the following uses a ring topology?
Which of the following technologies is used on cellular networks?
A technician is tasked with replacing some older RS-232 serial printers. Which of the following ports would the technician most likely find on these printers?
A technician notices a newly installed CAT5 cable is longer than the standard maximum length. Which of the following problems would this MOST likely cause?
Which of the following improves wireless performance by allowing only one wireless transmission on the network at a time?
Ann, a technician, is installing network cables for an office building. Some of the cables are not showing active on the switch even when moved to different ports. Which of the following is MOST likely the cause?
Which of the following cable types is MOST commonly used with POTS?
Which of the following BEST describes the point at which an ISP’s responsibility for an Internet connection ends?
In which of the following would Sandy, a technician, find the LARGEST number of 110 block patch panels?
Kurt, a user, cannot access any network resources. The technician has determined that the problem is isolated to Kurt, and that there have not been any changes to his workstation or switch port recently. Which of the following steps in the troubleshooting methodology should the technician do NEXT?
A network consultant arrives at a customer’s site to troubleshoot their email server. The server is running a Linux operating system, but the consultant is only familiar with Windows operating systems. Which of the following troubleshooting steps should the consultant take?
Which of the following has the LEAST amount of collisions in a domain?
Which of the following describes the amount of time it takes for a packet to transmit from one switch to another?
Which of the following protocols does DNS utilize on port 53?
Which of the following protocols is MOST commonly associated with VoIP?
Which of the following BEST describes a switch port?
Multiple networked devices running on the same physical hardware that provide central access to applications and files, where each device runs as a piece of software are known as:
If a NIC does not have a link light, there is a failure at which of the following OSI layers?
A network technician has determined a managed network switch has failed. The technician knows how to install a new switch, but not how to properly configure it. Which of the following troubleshooting steps should the technician take NEXT?
Which of the following is a link state routing protocol?
A web server that provides shopping cart capabilities for external end users will likely function with which of the following protocols?
Which of the following uses eight groups of characters for addressing?
Which of the following would Kim, a technician, use in voice over IP communications?
Layers 5, 6, and 7 from the OSI model correspond to which of the following layers of the TCP/IP model?
Which of the following exterior routing protocols uses an algorithm to determine the quickest route to a destination?
Which of the following defines an IP address that is NOT routed on the Internet?
In order for switching loops to be automatically disabled, which of the following needs to be implemented?
In which of the following layers of the OSI model would MAC addressing be found?
Which of the following is the MOST appropriate to use when routing Internet traffic through multiple ISP connections?
Which of the following routing protocols utilizes the DUAL algorithm for determining best path?
A forward lookup zone converts which of the following?
Which of the following exist at layer three of the OSI model? (Select TWO).
After a new firewall is installed, users report that they do not have connectivity to the Internet. The output of the ipconfig command shows an IP address of 169.254.0.101. Which of the following ports would need to be opened on the firewall to allow the users to obtain an IP address? (Select TWO).