A group of developers needs access to a database in a development environment, but the database contains sensitive data. Which of the following should the database administrator do before giving the developers access to the environment?
Which of the following is thebestway to migrate a large data load from one table to another, considering total time and blocking?
A database administrator is new to a company and wants to create a document that illustrates the interaction between tables. Which of the following should the administrator create?
Which of the following cloud delivery models provides users with thehighestlevel of flexibility regarding resource provisioning and administration?
Which of the following is a typical instruction that is found on a Linux command-line script and represents a system shell?
A company is launching a proof-of-concept, cloud-based application. One of the requirements is to select a database engine that will allow administrators to perform quick and simple queries on unstructured data.Which of the following would bebestsuited for this task?
Which of the following scripts would set the database recovery model for sys.database?
A)
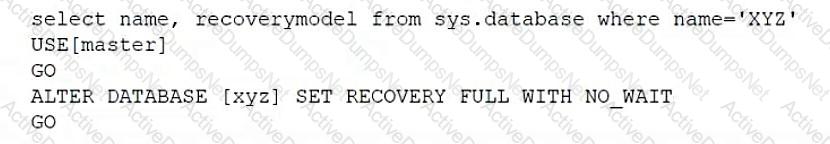
B)
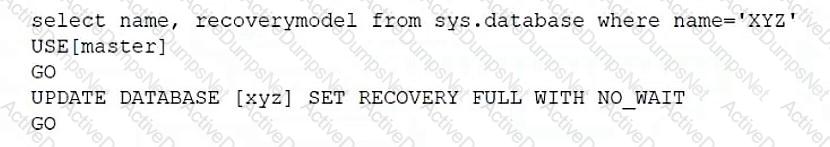
C)

D)

Which of the following database instances are created by default when SQL Server is installed? (Choose two.)
Which of the following is an attack in which an attacker hopes to profit from locking the database software?
Which of the following firewall types allows an administrator to control traffic and make decisions based on factors such as connection information and data flow communications?
A database administrator is migrating the information in a legacy table to a newer table. Both tables contain the same columns, and some of the data may overlap.
Which of the following SQL commands should the administrator use to ensure that records from the two tables are not duplicated?
A database administrator is concerned about transactions in case the system fails. Which of the following properties addresses this concern?
A database is configured to use undo management with temporary undo enabled. AnUPDATEis run on the table.
Which of the following describes where the undo is stored?
A DBA is reviewing the following logs to determine the current data backup plan for a primary data server:
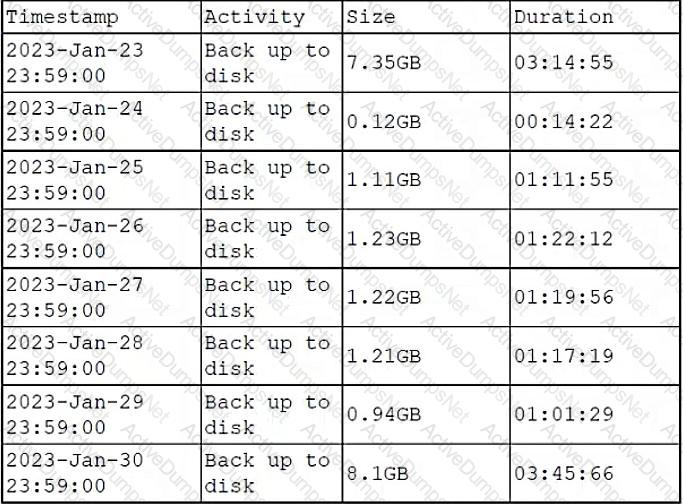
Which of the followingbestdescribes this backup plan?
Which of the following database structures is a type of NoSQL database?
Which of the following is a reason to create a stored procedure?
Which of the following sets the age requirement for data that should be recovered after a major disaster?
A database administrator needs to ensure continuous availability of a database in case the server fails. Which of the following should the administrator implement to ensure high availability of the database?
Which of the following is the correct order of the steps in the database deployment process?
A)
1. Connect
2. Install
3. Configure
4. Confirm prerequisites
5. Validate
6. Test
7. Release
B)
1. Configure
2. Install
3. Connect
4. Test
5. Confirm prerequisites
6. Validate
7. Release
C)
1. Confirm prerequisites
2. Install
3. Configure
4. Connect
5. Test
6. Validate
7. Release
D)
1. Install
2. Configure
3. Confirm prerequisites
4. Connect
5. Test
6. Validate
7. Release
A database administrator manages a database server that is running low on disk space. A lot of backup files are stored on the server's disks.
Which of the following is thebestaction for the administrator to take?
An automated script is using common passwords to gain access to a remote system. Which of the following attacks is being performed?
A business analyst is using a client table and an invoice table to create a database view that shows clients who have not made purchases yet. Which of the following joins ismostappropriate for the analyst to use to create this database view?
A database professional is considering denormalizing a database. Which of the following documents should be used to analyze the database's structure?
Which of the following resources is the best way to lock rows in SQL Server?