Which of the following is MOST dangerous to the client environment during a vulnerability assessment penetration test?
An intrusion detection analyst reported an inbound connection originating from an unknown IP address recorded on the VPN server for multiple internal hosts. During an investigation, a security analyst determines there were no identifiers associated with the hosts. Which of the following should the security analyst enforce to obtain the best information?
An analyst is coordinating with the management team and collecting several terabytes of data to analyze using advanced mathematical techniques in order to find patterns and correlations in events and activities. Which of the following describes what the analyst is doing?
A developer downloaded and attempted to install a file transfer application in which the installation package is bundled with acKvare. The next-generation antivirus software prevented the file from executing, but it did not remove the file from the device. Over the next few days, more developers tried to download and execute the offending file. Which of the following changes should be made to the security tools to BEST remedy the issue?
A security analyst recently observed evidence of an attack against a company's web server. The analyst investigated the issue but was unable to find an exploit that adequately explained the observations.
Which of the following is the MOST likely cause of this issue?
A cybersecurity analyst is researching operational data to develop a script that will detect the presence of a threat on corporate assets. Which of the following contains the most useful information to produce this script?
An employee observes degraded system performance on a Windows workstation. While attempting to access documents, the employee notices the file icons appear abnormal and the file extensions have been changed. The employee instantly shuts down the machine and alerts a supervisor.
Which of the following forensic evidence will be lost as a result of these actions?
Which of the following is the best method to ensure secure boot UEFI features are enabled to prevent boot malware?
A company's Chief Information Officer wants to use a CASB solution to ensure policies are being met during cloud access. Due to the nature of the company's business and risk appetite, the management team elected to not store financial information in the cloud. A security analyst needs to recommend a solution to mitigate the threat of financial data leakage into the cloud. Which of the following should the analyst recommend?
A security analyst is reviewing vulnerability scans from an organization's internet-facing web services. The following is from an output file called ssl-test_webapps.comptia.org:
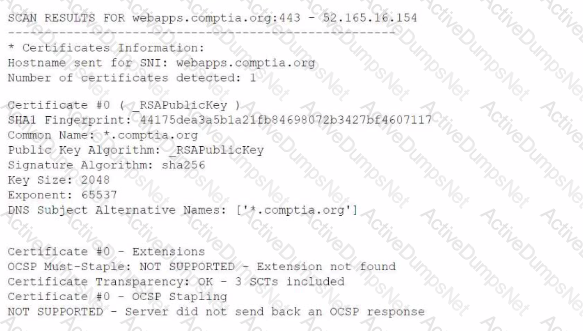
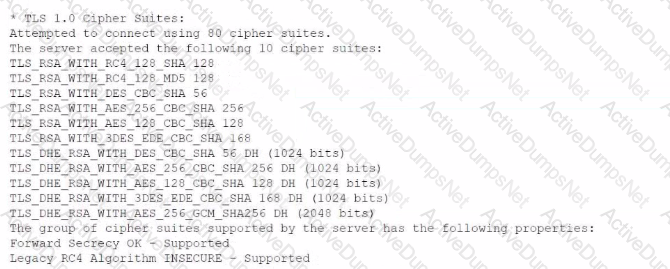
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
A new government regulation requires that organizations only retain the minimum amount of data on a person to perform the organization's necessary activities. Which of the following techniques would help an organization comply with this new regulation?
A company recently experienced a breach of sensitive information that affects customers across multiple geographical regions. Which of the following roles would be BEST suited to determine the breach notification requirements?
The help desk is having difficulty keeping up with all onboarding and offboarding requests. Managers often submit, requests for new users at the last minute. causing the help desk to scramble to create accounts across many different Interconnected systems. Which of the following solutions would work BEST to assist the help desk with the onboarding and offboarding process while protecting the company's assets?
A security analyst scans the company's external IP range and receives the following results from one of the hosts:
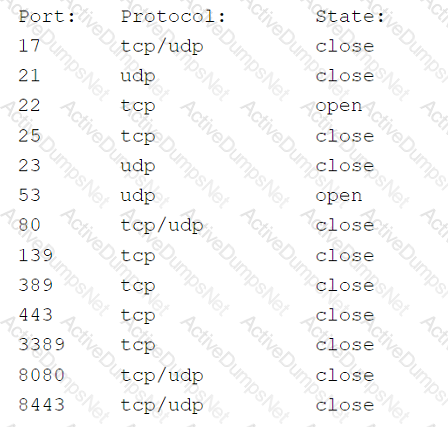
Which of the following best represents the security concern?
While conoXicting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report:
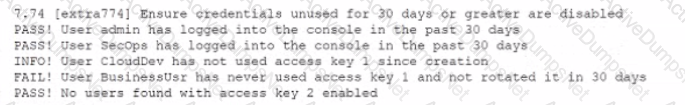
Based on the Prowler report, which of the following is the BEST recommendation?
An analyst receives artifacts from a recent Intrusion and is able to pull a domain, IP address, email address, and software version. When of the following points of the Diamond Model of Intrusion Analysis does this intelligence represent?
Which of the following is MOST important when developing a threat hunting program?
After examine a header and footer file, a security analyst begins reconstructing files by scanning the raw data bytes of a hard disk and rebuilding them. Which of the following techniques is the analyst using?
A security analyst is reviewing a new Internet portal that will be used for corporate employees to obtain their pay statements. Corporate policy classifies pay statement information as confidential, and it must be protected by MFA. Which of the following would best fulfill the MFA requirement while keeping the portal accessible from the internet?
Which of the following activities is designed to handle a control
failure that leads to a breach?
A security analyst wants to capture large amounts of network data that will be analyzed at a later time. The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called "packetCapture." The capture must be as efficient as possible, and the analyst wants to minimize the likelihood that packets will be missed. Which of the following commands will best accomplish the analyst's objectives?
A financial institution's business unit plans to deploy a new technology in a manner that violates existing information security standards. Which of the following actions should the Chief Information Security Officer (CISO) take to manage any type of violation?
An analyst is responding 10 an incident involving an attack on a company-owned mobile device that was being used by an employee to collect data from clients in the held. Maiware was loaded on the device via the installation of a third-party software package The analyst has baselined the device Which of the following should the analyst do to BEST mitigate future attacks?
The management team has asked a senior security engineer to explore DLP security solutions for the company's growing use of cloud-based storage. Which of the following is an appropriate solution to control the sensitive data that is being stored in the cloud?
Which of the following can detect vulnerable third-parly libraries before code deployment?
A security analyst reviews the following post-incident information to determine the origin and cause of a breach:
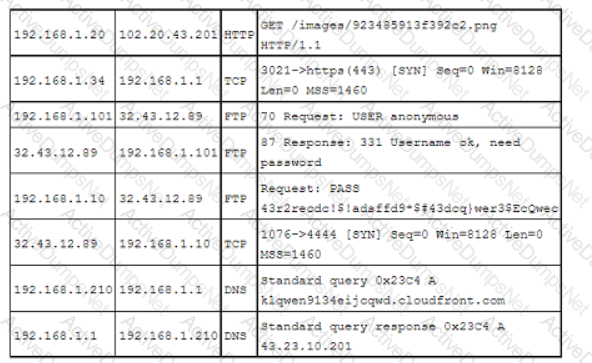
Based on this information, which of the following should the analyst record in the incident report related to the breach? (Select two).
An information security analyst discovered a virtual machine server was compromised by an attacker. Which of the following should be the first steps to confirm and respond to the incident? (Select two).
A security analyst is investigating a reported phishing attempt that was received by many users throughout the company The text of one of the emails is shown below:
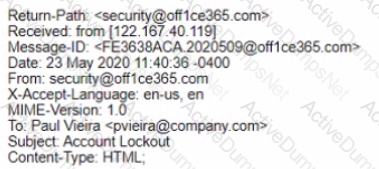
Office 365 User.
It looks like you account has been locked out Please click this link and follow the pfompts to restore access
Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques. Which of the following would best mitigate such attacks?
Ensuring that all areas of security have the proper controls is a primary reason why organizations use:
An organization is adopting loT devices at an increasing rate and will need to account for firmware updates in its vulnerability management programs. Despite the number of devices being deployed, the organization has only focused on software patches so far. leaving hardware-related weaknesses open to compromise. Which of the following best practices will help the organization to track and deploy trusted firmware updates as part of its vulnerability management programs?
An organization discovers motherboards within the environment that appear to have been physically altered during the manufacturing process. Which of the following is the BEST course of action to mitigate the risk of this reoccurring?
An incident response team detected malicious software that could have gained access to credit card data. The incident response team was able to mitigate significant damage and implement corrective actions. By having incident response mechanisms in place. Which of the following should be notified for lessons learned?
Which of the following is a vulnerability associated with the Modbus protocol?
A product manager is working with an analyst to design a new application that will perform as a data analytics platform and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application. Which of the following is a security concern when using a PaaS solution?
A product security analyst has been assigned to evaluate and validate a new products security capabilities Part of the evaluation involves reviewing design changes at specific intervals tor security deficiencies recommending changes and checking for changes at the next checkpoint Which of the following BEST defines the activity being conducted?
Which of the following BEST describes HSM?
Which of the following is a reason to use a nsk-based cybersecunty framework?
The Chief Information Security Officer (CISO) of a large financial institution is seeking a solution that will block a predetermined set of data points from being transferred or downloaded by employees. The CISO also wants to track the data assets by name, type, content, or data profile.
Which of the following BEST describes what the CIS wants to purchase?
An incident response plan requires systems that contain critical data to be triaged first in the event of a compromise. Which of the following types of data would most likely be classified as critical?
Which of the following are considered PII by themselves? (Select TWO).
A company wants to ensure a third party does not take intellectual property and build a competing product. Which of the following is a non-technical data and privacy control that would best protect the company?
While going through successful malware cleanup logs, an analyst notices an old worm that has been replicating itself across the company's network Reinfection of the malware can be prevented with a patch; however, most of the affected systems cannot be patched because the patch would make the system unstable. Which of the following should the analyst recommend to best prevent propagation of the malware throughout the network?
A company has alerted planning the implemented a vulnerability management procedure. However, to security maturity level is low, so there are some prerequisites to complete before risk calculation and prioritization. Which of the following should be completed FIRST?
A security analyst is reviewing the following server statistics:
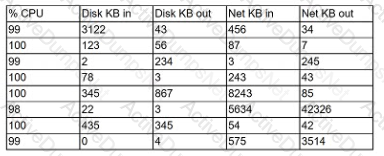
Which of the following Is MOST likely occurring?
A security analyst performed a targeted system vulnerability scan to obtain critical information. After the output result, the analyst used the OVAL XML language to review and calculate the discovered risk. Which of the following types of scans did the security analyst perform?
A security analyst notices the following proxy log entries:
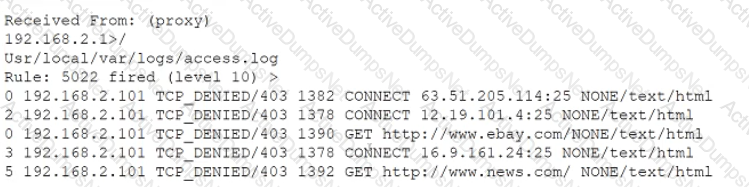
Which of the following is the user attempting to do based on the log entries?
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's singe internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT Department?
White reviewing incident reports from the previous night, a security analyst notices the corporate websites were defaced with po mcai propaganda. Which of the following BEST Describes this type of actor?
During the onboarding process for a new vendor, a security analyst obtains a copy of the vendor's latest penetration test summary:
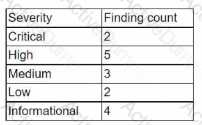
Performed by: Vendor Red Team Last performed: 14 days ago
Which of the following recommendations should the analyst make first?
Which of the following BEST describes what an organizations incident response plan should cover regarding how the organization handles public or private disclosures of an incident?
An analyst is performing a BIA and needs to consider measures and metrics. Which of the following would help the analyst achieve this objective? (Select two).
A systems administrator believes a user's workstation has been compromised. The workstation's performance has been lagging significantly for the past several hours. The administrator runs the task list
/ v command and receives the following output:
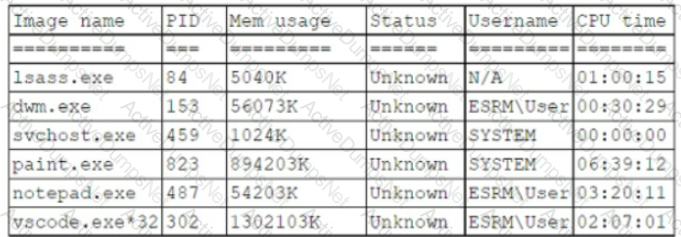
Which of the following should a security analyst recognize as an indicator of compromise?
A security analyst is handling an incident in which ransomware has encrypted the disks of several company workstations. Which of the following would work BEST to prevent this type of Incident in the future?
Legacy medical equipment, which contains sensitive data, cannot be patched. Which of the following is the best solution to improve the equipment's security posture?
During an incident response procedure, a security analyst acquired the needed evidence from the hard drive of a compromised machine. Which of the following actions should the analyst perform next to ensure the data integrity of the evidence?
While reviewing system logs, a network administrator discovers the following entry:
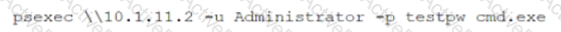
Which of the following occurred?
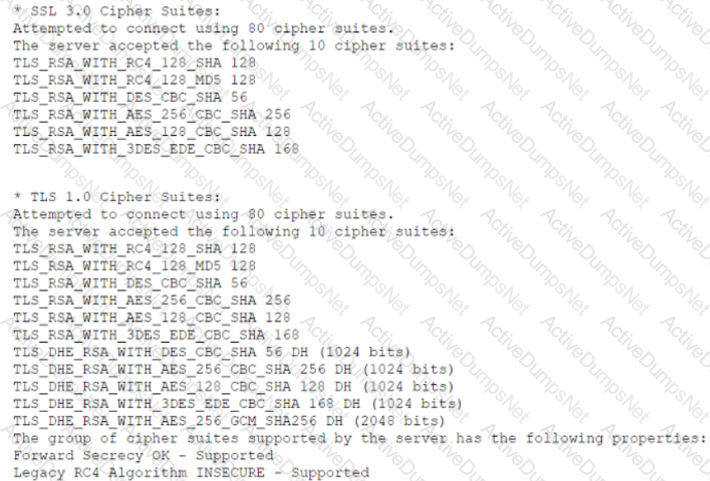
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
A manufacturing company uses a third-party service provider lor Tier 1 security support One of the requirements is that the provider must only source talent from its own country due to geopolitical and national security interests Which of the following can the manufacturing company implement to ensure the third-party service provider meets this requirement?
A new prototype for a company's flagship product was leaked on the internet As a result, the management team has locked out all USB drives Optical drive writers are not present on company computers The sales team has been granted an exception to share sales presentation files with third parties Which of the following would allow the IT team to determine which devices are USB enabled?
An organization is concerned about the security posture of vendors with access to its facilities and systems. The organization wants to implement a vendor review process to ensure \hi> policies implemented by vendors are in line with its own. Which of the following will provide the highest assurance of compliance?
An IT security analyst has received an email alert regarding a vulnerability within the new fleet of vehicles the company recently purchased. Which of the following attack vectors is the vulnerability MOST likely targeting?
An organization announces that all employees will need to work remotely for an extended period of time. All employees will be provided with a laptop and supported hardware to facilitate this requirement. The organization asks the information security division to reduce the risk during this time. Which of the following is a technical control that will reduce the risk of data loss if a laptop is lost or stolen?
An organization has specific technical nsk mitigation configurations that must be implemented before a new server can be approved for production Several critical servers were recently deployed with the antivirus missing unnecessary ports disabled and insufficient password complexity Which of the following should the analyst recommend to prevent a recurrence of this risk exposure?
A company is required to monitor for unauthorized changes to baselines on all assets to comply with industry regulations. Two of the remote units did not recover after scans were performed on the assets. An analyst needs to recommend a solution to prevent recurrence. Which of the following is the best way to satisfy the regulatory requirement without impacting the availability to similar assets and creating an unsustainable process?
The majority of a company's employees have stated they are unable to perform their job duties due to outdated workstations, so the company has decided to institute BYOD. Which of the following would a security analyst MOST likely recommend for securing the proposed solution?
A software developer is correcting the error-handling capabilities of an application following the initial coding of the fix. Which of the following would the software developer MOST likely performed to validate the code poor to pushing it to production?
A manufacturing company has joined the information sharing and analysis center for its sector. As a benefit, the company will receive structured loC data contributed by other members. Which of the following best describes the utility of this data?
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
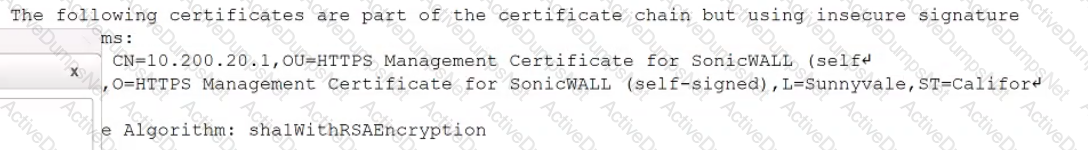 this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
Which of the following SCAP standards provides standardization tor measuring and describing the seventy of security-related software flaws?
A development team has asked users to conduct testing to ensure an application meets the needs of the business. Which of the fallowing types of testing docs This describe?
An organization has the following policies:
*Services must run on standard ports.
*Unneeded services must be disabled.
The organization has the following servers:
*192.168.10.1 - web server
*192.168.10.2 - database server
A security analyst runs a scan on the servers and sees the following output:
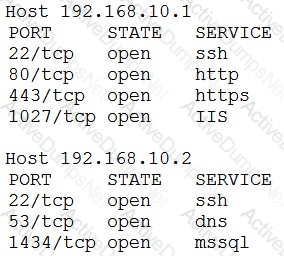
Which of the following actions should the analyst take?
A security analyst sees the following OWASP ZAP output from a scan that was performed against a modern version of Windows while testing for client-side vulnerabilities:
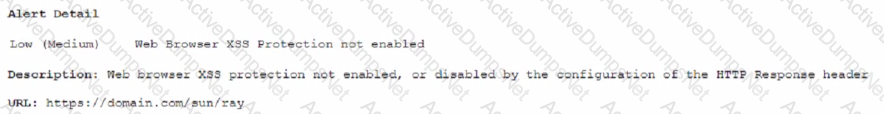
Which of the following is the MOST likely solution to the listed vulnerability?
A cybersecurity analyst is supporting an Incident response effort via threat Intelligence Which of the following is the analyst most likely executing?
A threat feed disclosed a list of files to be used as an loC for a zero-day vulnerability. A cybersecurity analyst decided to include a custom lookup for these files on the endpoint's log-in script as a mechanism to:
A security analyst is running a tool against an executable of an unknown source. The Input supplied by the tool to the executable program and the output from the executable are shown below:
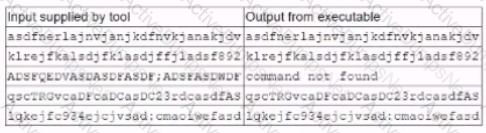
Which of the following should the analyst report after viewing this Information?
A security analyst is reviewing the network security monitoring logs listed below:
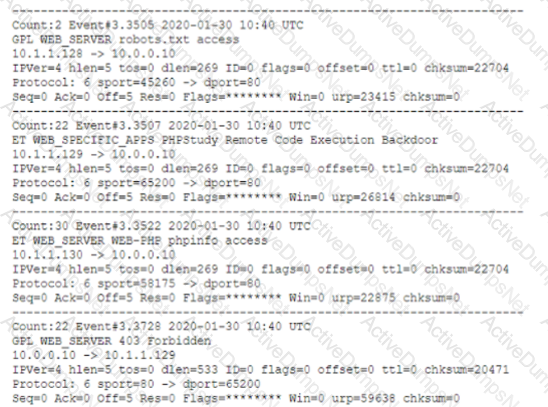
Which of the following is the analyst most likely observing? (Select two).
A forensic analyst is conducting an investigation on a compromised server Which of the following should the analyst do first to preserve evidence''
An analyst is reviewing the following output as part of an incident:
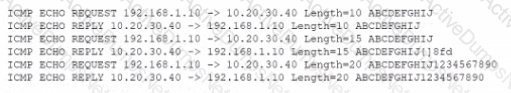
Which of the Wowing is MOST likely happening?
A company is building a new fabrication plant and designing its production lines based on the products it manufactures and the networks to support them. The security engineer has the following requirements:
• Each production line must be secured using a single posture.
• Each production line must only communicate with the other lines in a least privilege method.
• Access to each production line from the rest of the network must be strictly controlled.
To best provide the protection that meets these requirements, each product line should be:
When of the following techniques can be implemented to safeguard the confidentiality of sensitive information while allowing limited access to authorized individuals?
An analyst is responding to an incident within a cloud infrastructure Based on the logs and traffic analysis, the analyst thinks a container has been compromised Which of the following should Ihe analyst do FIRST?
An incident response team is responding to a breach of multiple systems that contain Pll and PHI Disclosure of the incident to external entities should be based on:
Due to continued support of legacy applications, an organization's enterprise password complexity rules are inadequate for its required security posture. Which of the following is the BEST compensating control to help reduce authentication compromises?
A security analyst is attempting to resolve an incident in which highly confidential company pricing information was sent to clients. It appears this information was unintentionally sent by an employee who attached it to public marketing material. Which of the following configuration changes would work BEST to limit the risk of this incident being repeated?
An analyst receives an alert from the continuous-monitoring solution about unauthorized changes to the firmware versions on several field devices. The asset owners confirm that no firmware version updates were performed by authorized technicians, and customers have not reported any performance issues or outages. Which Of the following actions would be BEST for the analyst to recommend to the asset owners to secure the devices from further exploitation?
An employee contacts the SOC to report a high-severity bug that was identified in a new, internally developed web application, which went live in production last week. The SOC staff did not receive contact details or escalation procedures to follow. Which of the following stages of the SDLC
process was overlooked?
A security learn implemented a SCM as part for its security-monitoring program there is a requirement to integrate a number of sources Into the SIEM to provide better context relative to the events being processed. Which of the following B€ST describes the result the security learn hopes to accomplish by adding these sources?
A company stores all of its data in the cloud. All company-owned laptops are currently unmanaged, and all users have administrative rights. The security team is having difficulty identifying a way to secure the environment. Which of the following would be the BEST method to protect the company's data?
An analyst received an alert regarding an application spawning a suspicious command shell process Upon further investigation, the analyst observes the following registry change occurring immediately after the suspicious event:
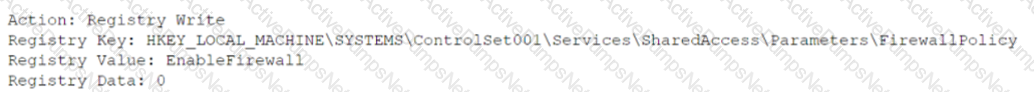
Which of the following was the suspicious event able to accomplish?
An organization has the following policy statements:
• AlI emails entering or leaving the organization will be subject to inspection for malware, policy violations, and unauthorized coolant.
•AM network activity will be logged and monitored.
• Confidential data will be tagged and tracked
• Confidential data must never be transmitted in an unencrypted form.
• Confidential data must never be stored on an unencrypted mobile device.
Which of the following is the organization enforcing?
Which of the following is a reason for correctly identifying APTs that might be targeting an organization?
A security analyst is reviewing the following Internet usage trend report:
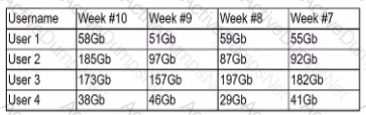
Which of the following usernames should the security analyst investigate further?
An organization's internal department frequently uses a cloud provider to store large amounts of sensitive data. A threat actor has deployed a virtual machine to at the use of the cloud hosted hypervisor, the threat actor has escalated the access rights. Which of the following actions would be BEST to remediate the vulnerability?
A forensics investigator is analyzing a compromised workstation. The investigator has cloned the hard drive and needs to verify that a bit-level image copy of a hard drive is an exact clone of the original hard drive that was collected as evidence. Which of the following should the investigator do?
A security analyst needs to recommend the best approach to test a new application that simulates abnormal user behavior to find software bugs. Which of the following would best accomplish this task?
Which of the following organizational initiatives would be MOST impacted by data severighty issues?
A customer notifies a security analyst that a web application is vulnerable to information disclosure The analyst needs to indicate the seventy of the vulnerability based on its CVSS score, which the analyst needs to calculate When analyzing the vulnerability the analyst realizes that tor the attack to be successful, the Tomcat configuration file must be modified Which of the following values should the security analyst choose when evaluating the CVSS score?
An organizational policy requires one person to input accounts payable and another to do accounts receivable. A separate control requires one person to write a check and another person to sign all checks greater than $5,000 and to get an additional signature for checks greater than $10,000. Which of the following controls has the organization implemented?
A cybersecunty analyst needs to harden a server that is currently being used as a web server The server needs to be accessible when entenng www company com into the browser Additionally web pages require frequent updates which are performed by a remote contractor Given the following output:
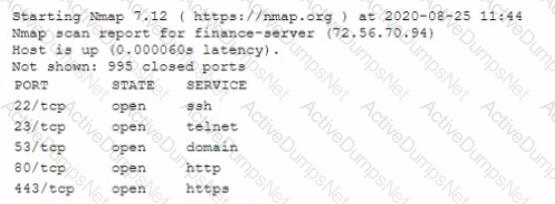
Which of the following should the cybersecunty analyst recommend to harden the server? (Select TWO).
An organization has the following risk mitigation policy:
Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
All other prioritization will be based on risk value.
The organization has identified the following risks:
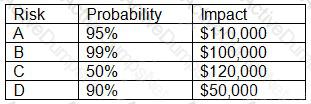
Which of the following is the order of priority for risk mitigation from highest to lowest?
A security analyst needs to automate the incident response process for malware infections. When the following logs are generated, an alert email should automatically be sent within 30 minutes:
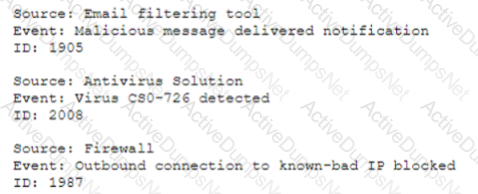
Which of the following is the best way for the analyst to automate alert generation?
An online gaming company was impacted by a ransomware attack. An employee opened an attachment that was received via an SMS attack on a company-issue firewall. Which following actions would help during the forensic analysis of the mobile device? (Select TWO).
A financial organization has offices located globally. Per the organization’s policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's data. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
industry partners from critical infrastructure organizations were victims of attacks on their SCADA devices. The attacks used privilege escalation to gain access to SCADA administration and access management solutions would help to mitigate this risk?
A security analyst discovers suspicious activity going to a high-value corporate asset. After reviewing the traffic, the security analyst identifies that
malware was successfully installed on a machine. Which of the following should be completed first?
An organization supports a large number of remote users. Which of the following is the best option to protect the data on the remote users' laptops?
During an incident investigation, a security analyst discovers the web server is generating an unusually high volume of logs The analyst observes the following response codes:
• 20% of the logs are 403
• 20% of the logs are 404
• 50% of the logs are 200
• 10% of the logs are other codes
The server generates 2MB of logs on a daily basis, and the current day log is over 200MB. Which of the following commands should the analyst use to identify the source of the activity?
An analyst Is reviewing a web developer's workstation for potential compromise. While examining the workstation's hosts file, the analyst observes the following:
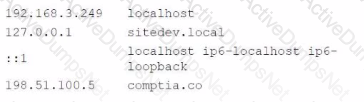
Which of the following hosts file entries should the analyst use for further investigation?
An internally developed file-monitoring system identified the following except as causing a program to crash often:
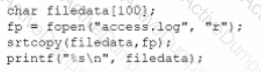
Which of the following should a security analyst recommend to fix the issue?
A security analyst performs a weekly vulnerability scan on a network that has 240 devices and receives a report with 2.450 pages. Which of the following would most likely decrease the number of false positives?