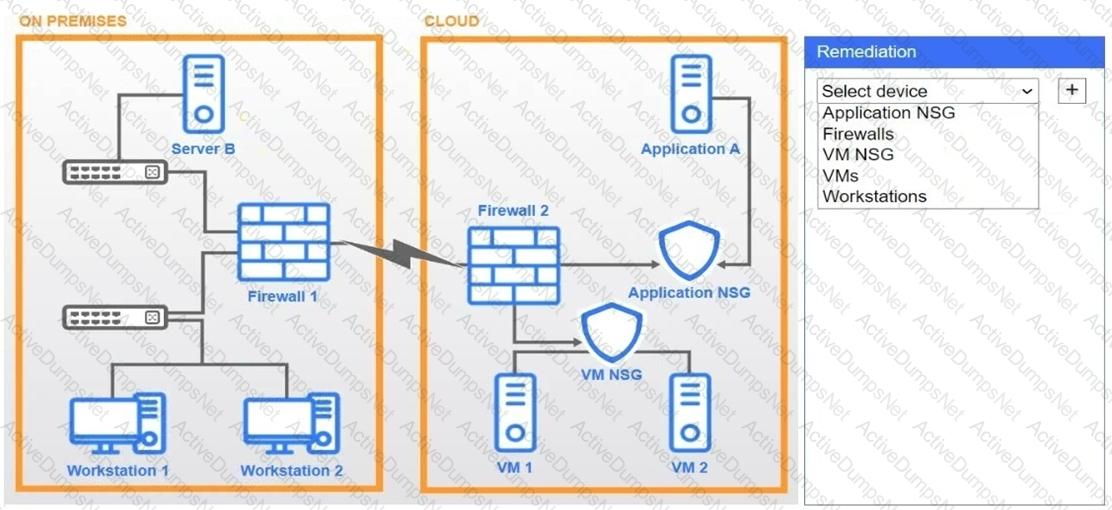
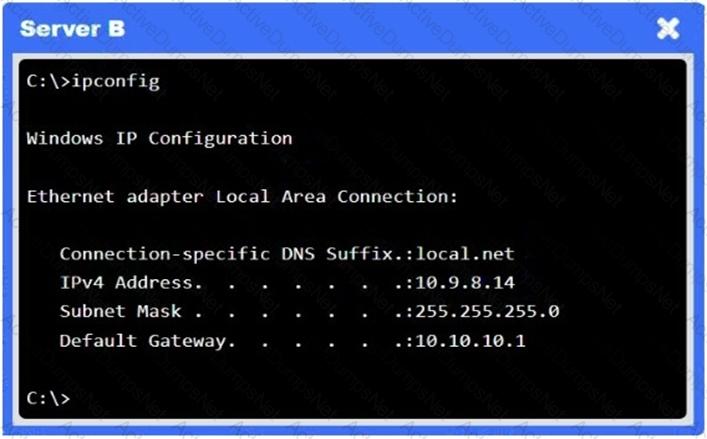
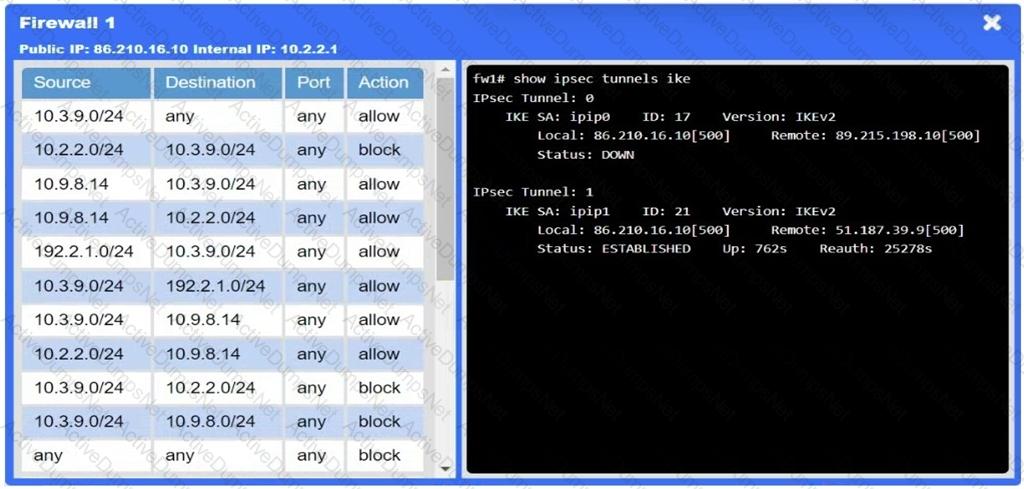
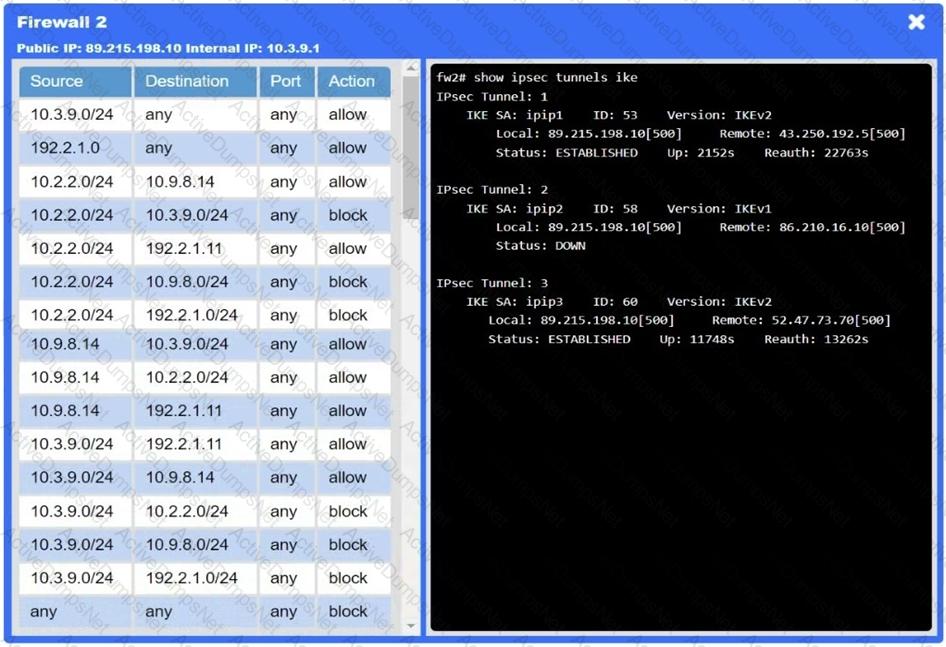
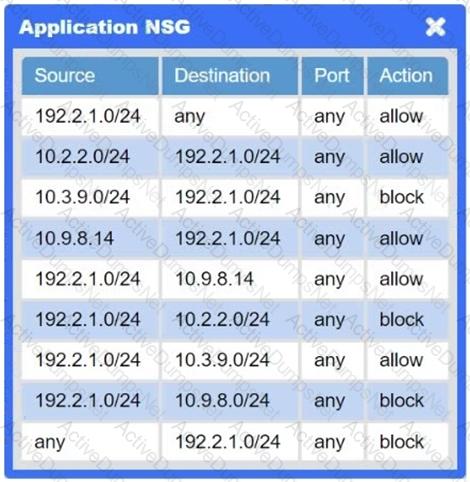
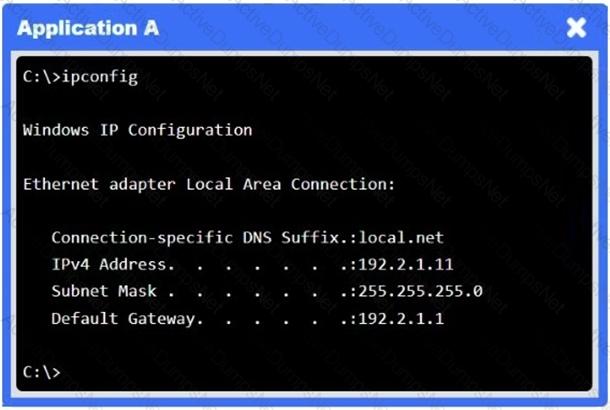
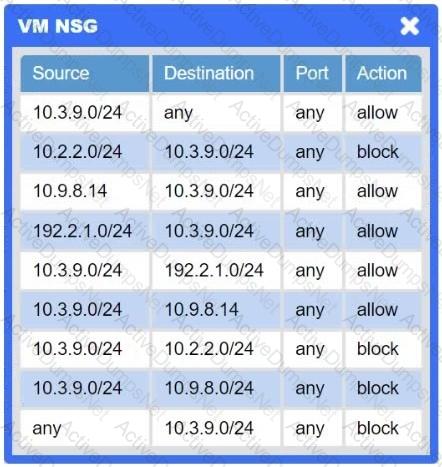
A network administrator needs to resolve connectivity issues in a hybrid cloud setup. Workstations and VMs are not able to access Application A. Workstations are able to access Server B.
INSTRUCTIONS
Click on workstations, VMs, firewalls, and NSGs to troubleshoot and gather information. Type help in the terminal to view a list of available commands.
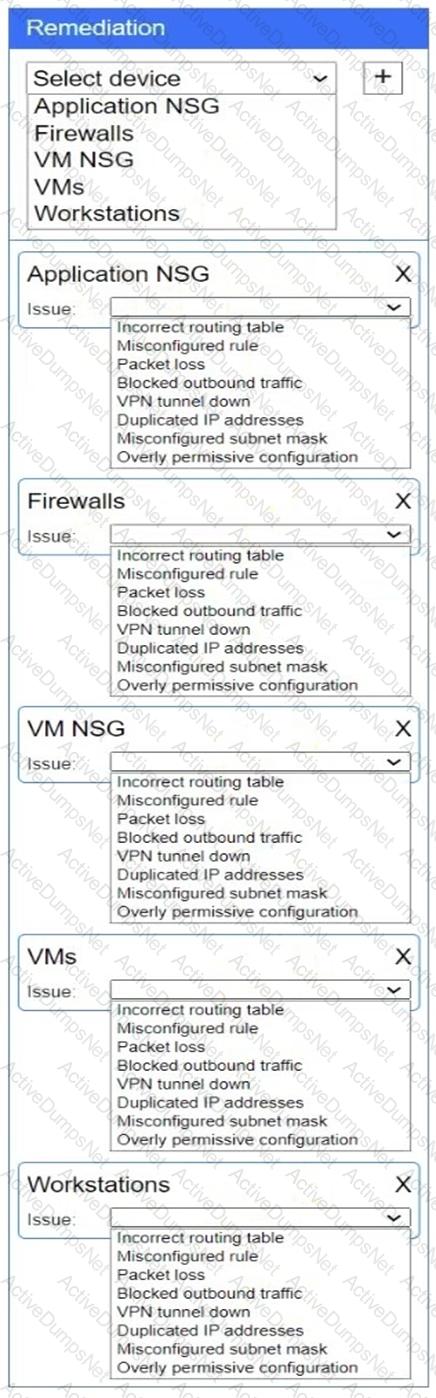
Select the appropriate device(s) requiring remediation and identify the associated issue(s).
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


A network engineer identified several failed log-in attempts to the VPN from a user's account. When the engineer inquired, the user mentioned the IT help desk called and asked them to change their password. Which of the following types of attacks occurred?
A cloud network engineer needs to enable network flow analysis in the VPC so headers and payload of captured data can be inspected. Which of the following should the engineer use for this task?
A company's IT department is expected to grow from 100 to 200 employees, and the sales department is expected to grow from 1,000 to a maximum of 2,000 employees. Each employee owns a single laptop with a single IP allocated. The network architect wants to deploy network segmentation using the IP range 10.0.0.0/8. Which of the following is the best solution?
After a company migrated all services to the cloud, the security auditor discovers many users have administrator roles on different services. The company needs a solution that:
Protects the services on the cloud
Limits access to administrative roles
Creates a policy to approve requests for administrative roles on critical services within a limited time
Forces password rotation for administrative roles
Audits usage of administrative roles
Which of the following is the best way to meet the company's requirements?
A cafe uses a tablet-based point-of-sale system. Customers are complaining that their food is taking too long to arrive. During an investigation, the following is noticed:
Every kitchen printer did not print the orders
Payments are processing correctly
The cloud-based system has record of the orders
This issue occurred when the cafe was busy
Which of the following is the best way to mitigate this issue?
A network engineer is establishing a wireless network for handheld inventory scanners in a manufacturing company's warehouse. The engineer needs an authentication mechanism for these scanners that uses the Wi-Fi network and works with the company's Active Directory. The business requires that the solution authenticate the users and authorize the scanners. Which of the following provides the best solution for authentication and authorization?
A company hosts its applications on the cloud and is expanding its business to Europe. Thecompany must comply with General Data Protection Regulation (GDPR) to limit European customers' access to data. The network team configures the firewall rules but finds that some customers in the United States can access data hosted in Europe. Which of the following is the best option for the network team to configure?
A large commercial enterprise that runs a global video streaming platform recently acquired a small business that serves customers in a geographic area with limited connectivity to the global telecommunications infrastructure. The executive leadership team issued a mandate to deliver the highest possible video streaming quality to all customers around the world. Which of the following solutions should the enterprise architect suggest to meet the requirements?
Which of the following helps the security of the network design to align with industry best practices?
An organization wants to evaluate network behavior with a network monitoring tool that is not inline. The organization will use the logs for further correlation and analysis of potential threats. Which of the following is the best solution?
A cloud architect needs to change the network configuration at a company that uses GitOps to document and implement network changes. The Git repository uses main as the default branch, and the main branch is protected. Which of the following should the architect do after cloning the repository?
A network architect is creating a network topology for a global SD-WAN deployment. The business has offices in Asia, Europe, and the United States and makes use of data centers in theUnited States and Europe. Most traffic between sites must have the lowest latency possible. Which of the following topologies best meets this requirement?
A network architect is designing a new network for a rural hospital system. Given the following requirements:
Highly available
Consistent data transmission
Resilient to simultaneous failures
Which of the following topologies should the architect use?
A network architect needs to design a solution to ensure every cloud environment network is built to the same baseline. The solution must meet the following requirements:
Use automated deployment.
Easily update multiple environments.
Share code with a community of practice.
Which of the following are the best solutions? (Choose two.)
A network engineer needs to implement a cloud-native solution. The solution must allow the recording of network conversation metadata of the host and appliances attached to a VPC. Which of the following will accomplish these goals with the least effort?
A network administrator is troubleshooting an outage at a remote site. The administrator examines the logs and determines that one of the internet links at the site appears to be down. After the service provider confirms this information, the administrator fails over traffic to the backup link. Which of the following should the administrator do next?
A customer asks a MSP to propose a ZTA (Zero Trust Architecture) design for its globally distributed remote workforce. Given the following requirements:
Authentication should be provided through the customer's SAML identity provider.
Access should not be allowed from countries where the business does not operate.
Secondary authentication should be added to the workflow to allow for passkeys.
Changes to the user's device posture and hygiene should require reauthentication into the network.
Access to the network should only be allowed to originate from corporate-owned devices.
Which of the following solutions should the MSP recommend to meet the requirements?
Application development team users are having issues accessing the database server within the cloud environment. All other users are able to use SSH to access this server without issues. The network architect reviews the following information to troubleshoot the issue:
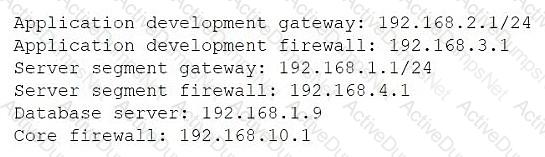
Traceroute output from an application developer's machine with the assigned IP 192.168.2.7:
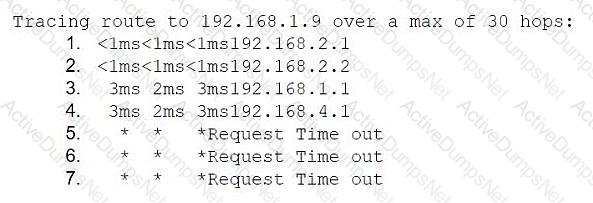
Application development gateway: 192.168.2.1/24
Server segment gateway: 192.168.1.1/24
Database server: 192.168.1.9
Application developer machine IP: 192.168.2.7
Traceroute ends at hop 4: 192.168.4.1 (server segment firewall), then times out
Which of the following is the most likely cause of the issue?
A cloud architect must recommend an architecture approach for a new medical application that requires the lowest downtime possible. Which of the following is the best application deployment strategy given the high-availability requirement?
A network architect must design a new branch network that meets the following requirements:
No single point of failure
Clients cannot be impacted by changes to the underlying medium
Clients must be able to communicate directly to preserve bandwidth
Which of the following network topologies should the architect use?
A global company has depots in various locations. A proprietary application was deployed locally at each of the depots, but issues with getting the consolidated data instantly occurred. The Chief Information Officer decided to centralize the application and deploy it in the cloud. After the cloud deployment, users report the application is slow. Which of the following is most likely the issue?
A company just launched a cloud-based application. Some users are reporting the application will not load. A cloud engineer investigates the issues and reports the following:
Not all users are experiencing the issue
The application infrastructure is optimal
Users experiencing the issue belong to the company's remote sales team
Which of the following is most likely misconfigured?
A network architect needs to design a new network to connect multiple private data centers. The network must:
Provide privacy for all traffic between locations
Use preexisting internet connections
Use intelligent steering of application traffic over the best path
Which of the following best meets these requirements?
As part of a project to modernize a sports stadium and improve the customer service experience for fans, the stadium owners want to implement a new wireless system. Currently, all tickets are electronic and managed by the stadium mobile application. The new solution is required to allow location tracking precision within 5ft (1.5m) of fans to deliver the following services:
Emergency/security assistance
Mobile food order
Event special effects
Raffle winner location displayed on the giant stadium screen
Which of the following technologies enables location tracking?