Due to an infrastructure optimization plan, a company has moved from a unified architecture to a federated architecture divided by region. Long-term employees now have a better experience, but new employees are experiencing major performance issues when traveling between regions. The company is reviewing the following information:
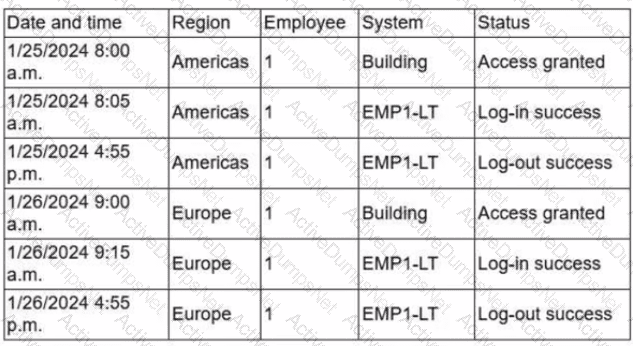
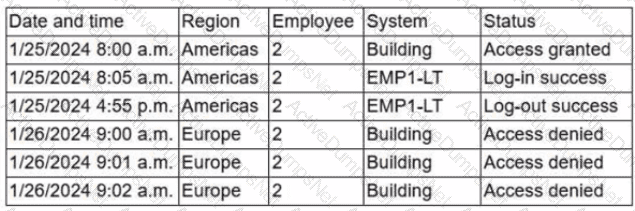
Which of the following is the most effective action to remediate the issue?
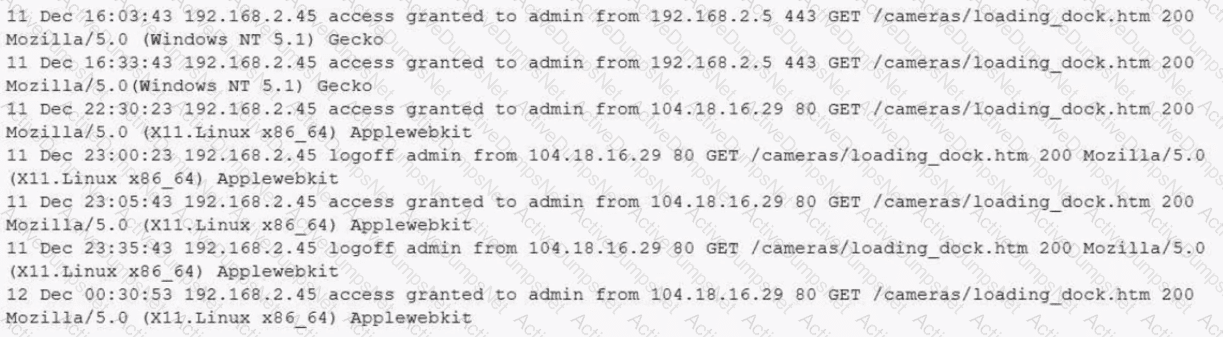
A building camera is remotely accessed and disabled from the remote console application during off-hours. A security analyst reviews the following logs:
A security architect is onboarding a new EDR agent on servers that traditionally do not have internet access. In order for the agent to receive updates and report back to the management console, some changes must be made. Which of the following should the architect do to best accomplish this requirement? (Select two).
A web application server that provides services to hybrid modern and legacy financial applications recently underwent a scheduled upgrade to update common libraries, including OpenSSL. Multiple users are now reporting failed connection attempts to the server. The technician performing initial triage identified the following:
• Client applications more than five years old appear to be the most affected.
• Web server logs show initial connection attempts by affected hosts.
• For the failed connections, logs indicate "cipher unavailable."
Which of the following is most likely to safely remediate this situation?
A security analyst is performing a review of a web application. During testing as a standard user, the following error log appears:
Error Message in Database Connection
Connection to host USA-WebApp-Database failed
Database "Prod-DB01" not found
Table "CustomerInfo" not found
Please retry your request later
Which of the following best describes the analyst’s findings and a potential mitigation technique?
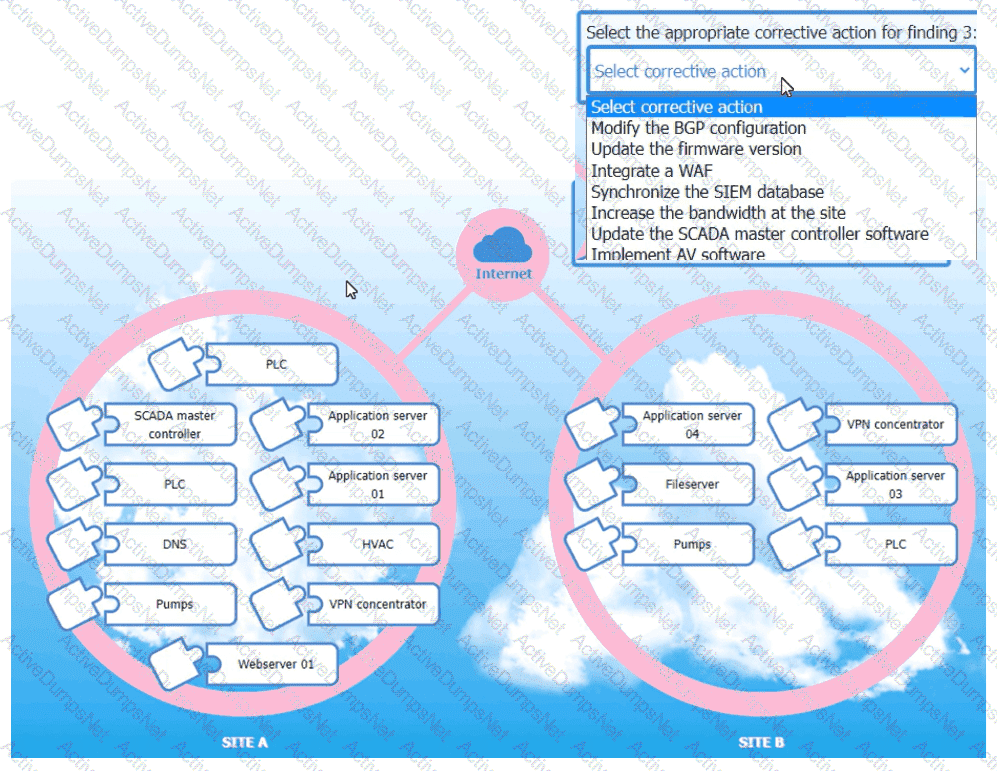
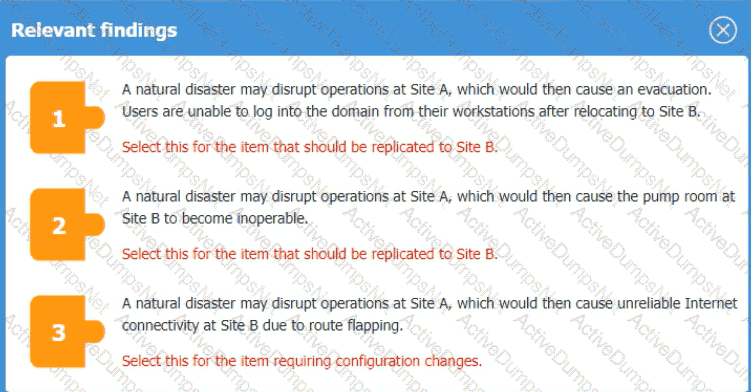
An organization is planning for disaster recovery and continuity ofoperations, and has noted the following relevant findings:
1. A natural disaster may disrupt operations at Site A, which would then cause an evacuation. Users are
unable to log into the domain from-their workstations after relocating to Site B.
2. A natural disaster may disrupt operations at Site A, which would then cause the pump room at Site B
to become inoperable.
3. A natural disaster may disrupt operations at Site A, which would then cause unreliable internet
connectivity at Site B due to route flapping.
INSTRUCTIONS
Match each relevant finding to the affected host by clicking on the host name and selecting the appropriate number.
For findings 1 and 2, select the items that should be replicated to Site B. For finding 3, select the item requiring configuration changes, then select the appropriate corrective action from the drop-down menu.
An organization determines existing business continuity practices areinadequateto support critical internal process dependencies during a contingency event. Acompliance analystwants the Chief Information Officer (CIO) to identify the level ofresidual riskthat is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped. The files were transferred via TLS-protected HTTP sessions from systems that do not normally send traffic to those sites. The technician will define this threat as:
An organization recently implemented a purchasing freeze that has impacted endpoint life-cycle management efforts. Which of the following should a security manager do to reduce risk without replacing the endpoints?
A company wants to use loT devices to manage and monitor thermostats at all facilities The thermostats must receive vendor security updates and limit access to other devices within the organization Which of the following best addresses the company's requirements''
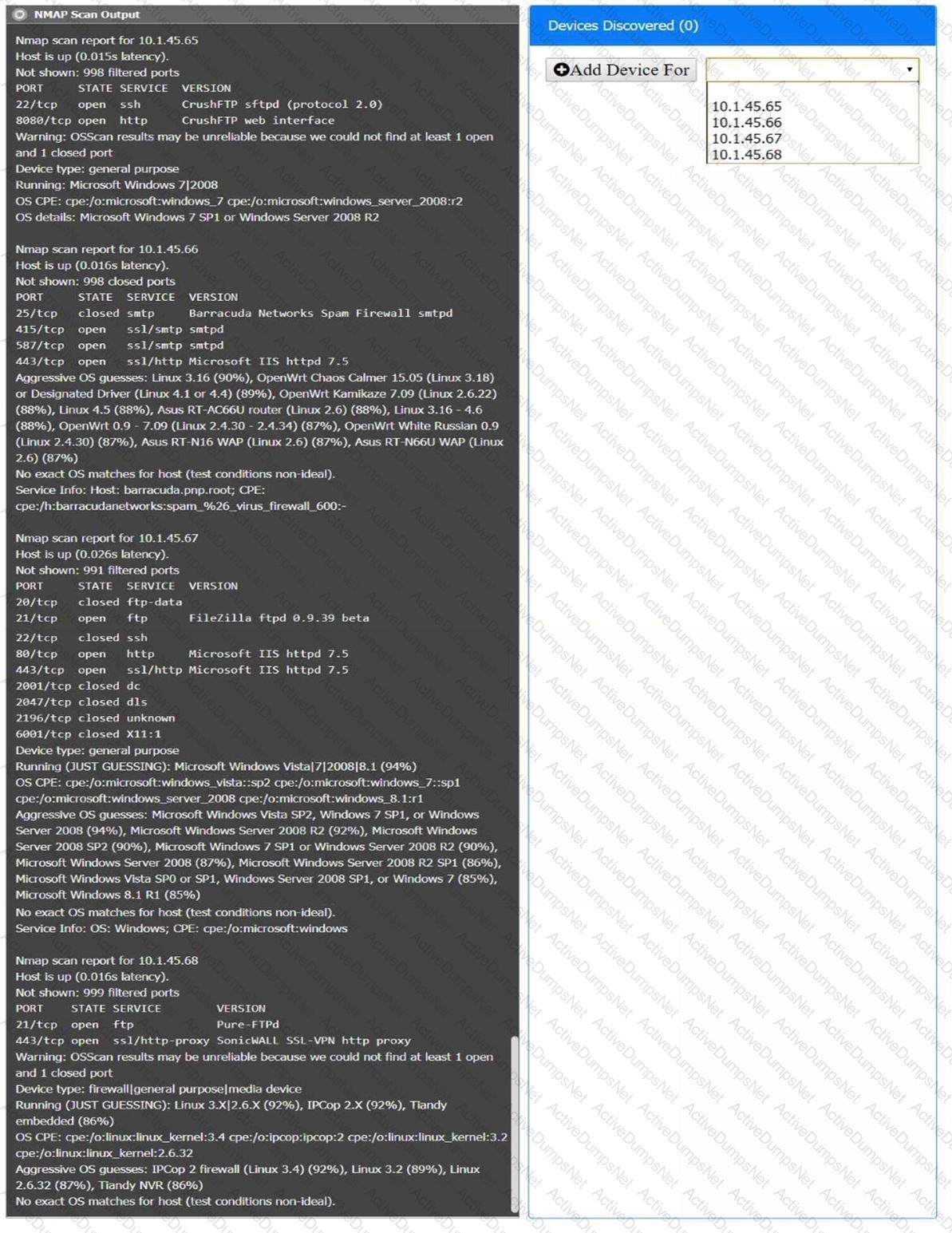
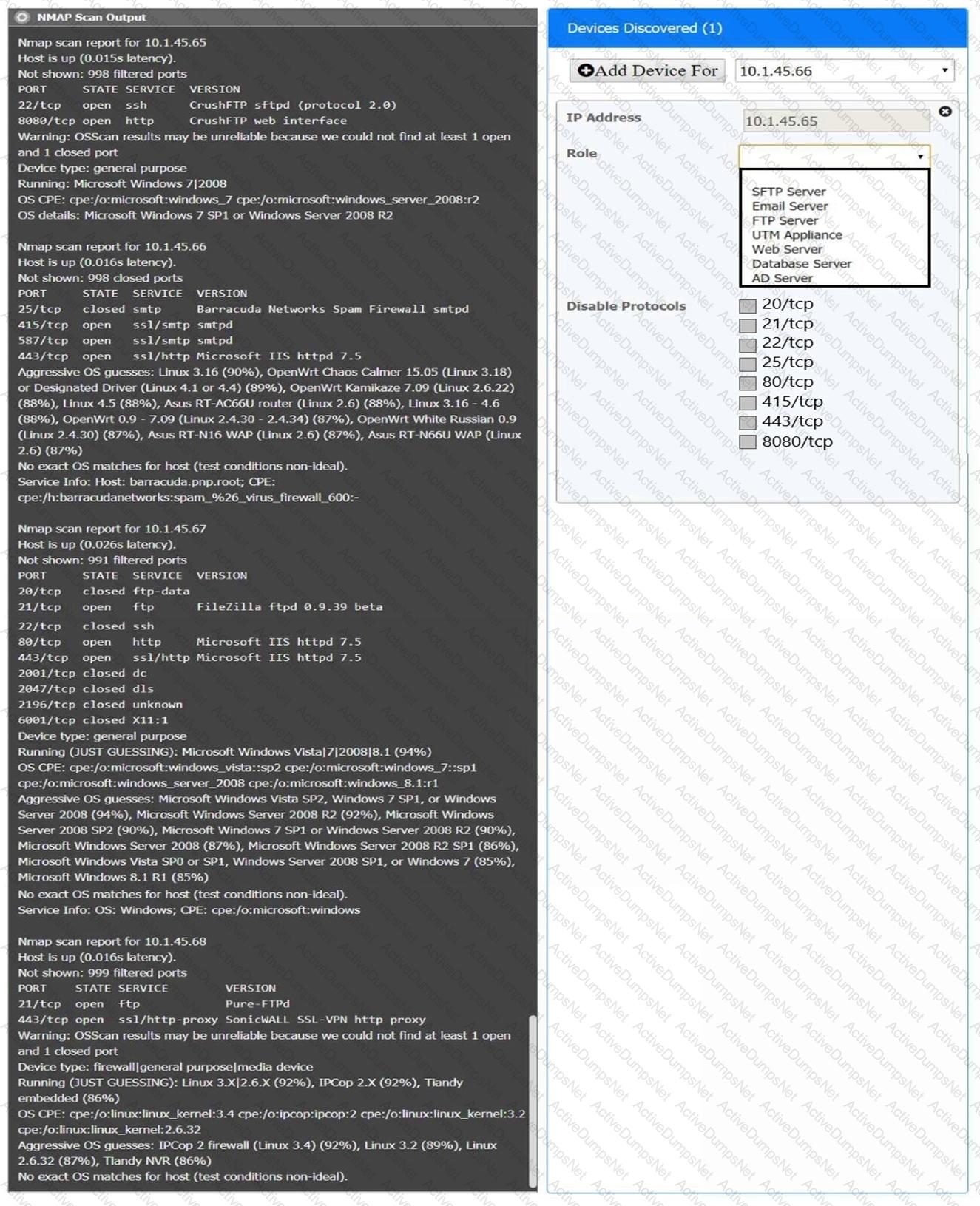
You are a security analyst tasked with interpreting an Nmap scan output from company’s privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A security review revealed that not all of the client proxy traffic is being captured. Which of the following architectural changes best enables the capture of traffic for analysis?
A company wants to improve and automate the compliance of its cloud environments to meet industry standards. Which of the following resources should the company use to best achieve this goal?
During a forensic review of a cybersecurity incident, a security engineer collected a portion of the payload used by an attacker on a comprised web server Given the following portion of the code:
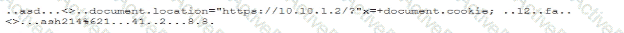
Which of the following best describes this incident?
After an incident occurred, a team reported during the lessons-learned review that the team.
* Lost important Information for further analysis.
* Did not utilize the chain of communication
* Did not follow the right steps for a proper response
Which of the following solutions is the best way to address these findinds?
A security analyst isreviewing the following event timeline from an COR solution:
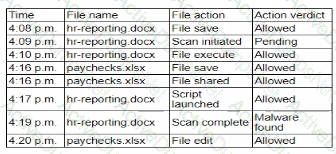
Which of the following most likely has occurred and needs to be fixed?
Third partiesnotified a company's security team about vulnerabilities in the company's application. The security team determined these vulnerabilities were previously disclosed in third-party libraries. Which of the following solutions best addresses the reported vulnerabilities?
A company wants to invest in research capabilities with the goal to operationalize the research output. Which of the following is the best option for a security architect to recommend?
Users are experiencing a variety of issueswhen trying to access corporate resources examples include
• Connectivity issues between local computers and file servers within branch offices
• Inability to download corporate applications on mobile endpoints wtiilc working remotely
• Certificate errors when accessing internal web applications
Which of the following actions are the most relevant when troubleshooting the reported issues? (Select two).
A security professional is investigating a trend in vulnerability findings for newly deployed cloud systems Given the following output:
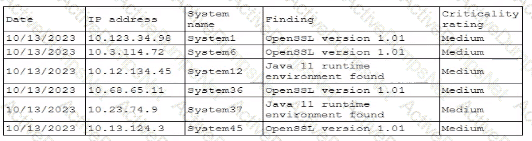
Which of the following actions would address the root cause of this issue?
An administrator brings the company's fleet of mobile devices into its PKI in order to align device WLAN NAC configurations with existing workstations and laptops. Thousands of devices need to be reconfigured in a cost-effective, time-efficient, and secure manner. Which of the following actions best achieve this goal? (Select two)
A company plans to implement a research facility with Intellectual property data that should be protected The following is the security diagram proposed by the security architect
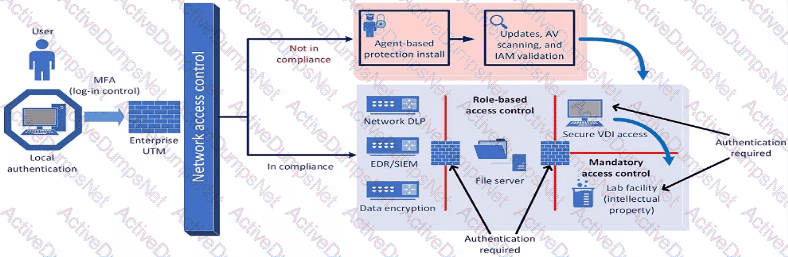
Which of the following security architect models is illustrated by the diagram?
A company’s internal network is experiencing a security breach, and the threat actor is still active. Due to business requirements, users in this environment are allowed to utilize multiple machines at the same time. Given the following log snippet:
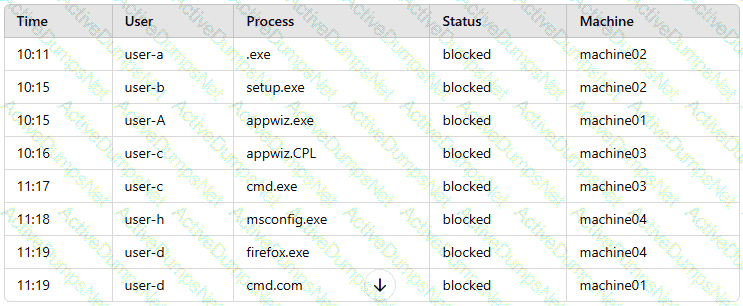
Which of the following accounts should a security analyst disable to best contain the incident without impacting valid users?
A company detects suspicious activity associated with external connections Security detection tools are unable tocategorize this activity. Which of the following is the best solution to help the company overcome this challenge?
Recent repents indicate that a software tool is being exploited Attackers were able to bypass user access controls and load a database. A security analyst needs to find the vulnerability and recommend a mitigation. The analyst generates the following output:
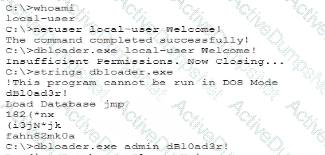
Which of the following would the analyst most likely recommend?
A security engineer must ensure that sensitive corporate information is not exposed if a company laptop is stolen. Which of the following actions best addresses this requirement?
A security analyst is troubleshooting the reason a specific user is having difficulty accessing company resources The analyst reviews the following information:
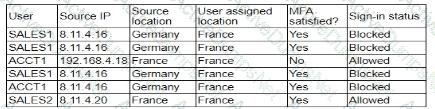
Which of the following is most likely the cause of the issue?
A user submits a help desk ticket stating then account does not authenticatesometimes. An analyst reviews the following logs for the user:
Which of the following best explains the reason the user's access is being denied?
An organization is required to
* Respond to internal andexternal inquiries in a timely manner
* Provide transparency.
* Comply with regulatory requirements
The organization has not experienced any reportable breaches but wants to be prepared if a breach occurs in the future. Which of the following is the best way for the organization to prepare?
While reviewing recent modem reports, a security officer discovers that several employees were contacted by the same individual who impersonated a recruiter. Which of the following best describes this type of correlation?
A company isolated its OT systems from other areas of the corporate network These systems are required to report usage information over the internet to the vendor Which oi the following b*st reduces the risk of compromise or sabotage' (Select two).
During a recentsecurity event, access from thenon-production environment to the production environmentenabledunauthorized usersto:
Installunapproved software
Makeunplanned configuration changes
During theinvestigation, the following findings were identified:
Several new users were added in bulkby theIAM team
Additionalfirewalls and routerswere recently added
Vulnerability assessmentshave been disabled formore than 30 days
Theapplication allow listhas not been modified intwo weeks
Logs were unavailablefor various types of traffic
Endpoints have not been patchedinover ten days
Which of the following actions would most likely need to be taken toensure proper monitoring?(Select two)
A company receives reports about misconfigurations and vulnerabilities in a third-party hardware device that is part of its released products. Which of the following solutions is the best way for the company to identify possible issues at an earlier stage?
A senior security engineer flags the following log file snippet as having likely facilitated an attacker’s lateral movement in a recent breach:
qry_source: 19.27.214.22 TCP/53
qry_dest: 199.105.22.13 TCP/53
qry_type: AXFR
| in comptia.org
------------ directoryserver1 A 10.80.8.10
------------directoryserver2 A 10.80.8.11
------------ directoryserver3 A 10.80.8.12
------------ internal-dns A 10.80.9.1
----------- www-int A 10.80.9.3
------------ fshare A 10.80.9.4
------------ sip A 10.80.9.5
------------ msn-crit-apcs A 10.81.22.33
Which of the following solutions, if implemented, would mitigate the risk of this issue reoccurring?
A security architect must make sure that the least number of services as possible is exposed in order to limit an adversary's ability to access the systems. Which of the following should the architect do first?
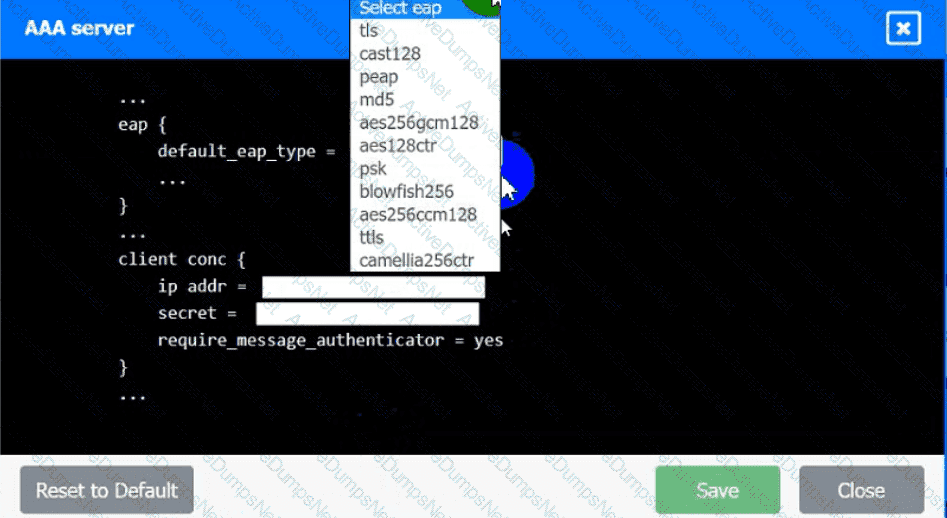
An IPSec solution is being deployed. The configuration files for both the VPN
concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
• The EAP method must use mutual certificate-based authentication (With
issued client certificates).
• The IKEv2 Cipher suite must be configured to the MOST secure
authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase
character, one numeric character, and one special character, and it must
meet a minimumlength requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration.
Fill in the appropriate fields and make selections from the drop-down menus.
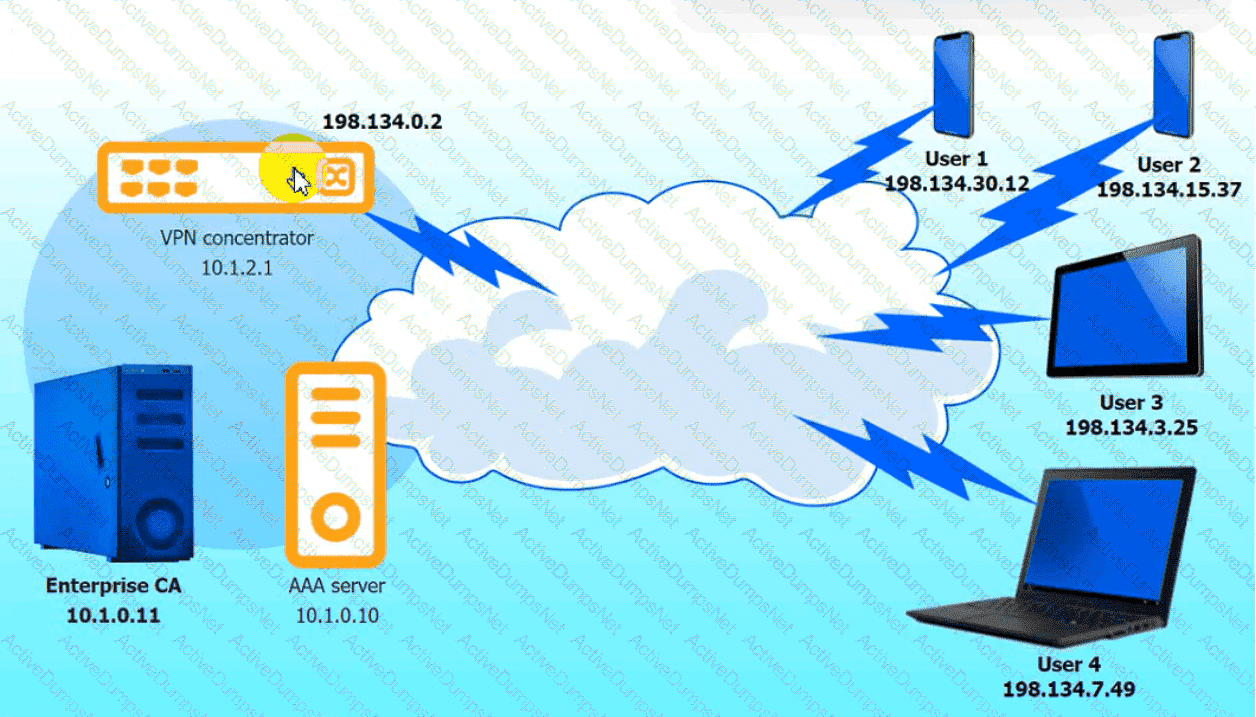
VPN Concentrator:
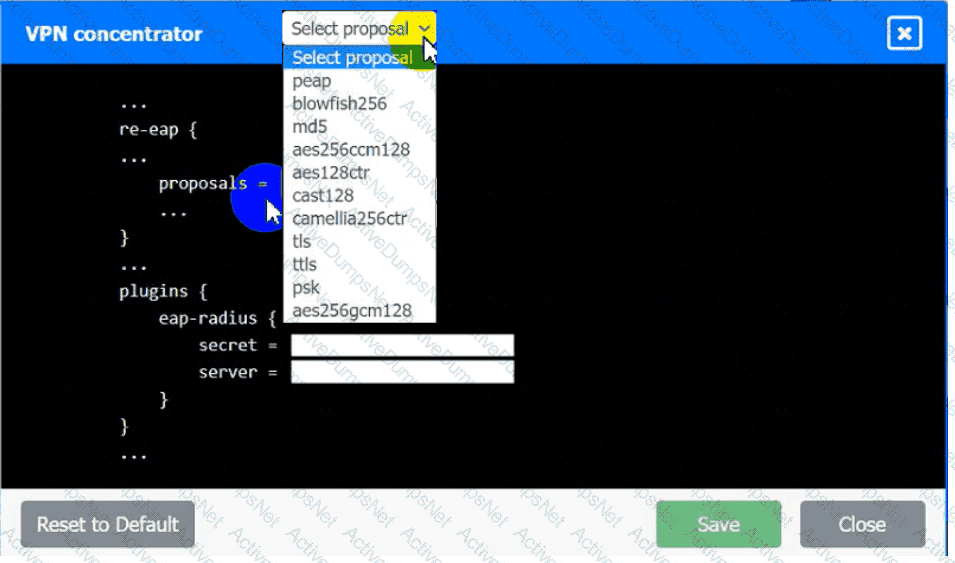
AAA Server:
A security engineer is assisting a DevOps team that has the following requirements for container images:
Ensure container images are hashed and use version controls.
Ensure container images are up to date and scanned for vulnerabilities.
Which of the following should the security engineer do to meet these requirements?
Audit findings indicate several user endpoints are not utilizing full disk encryption During me remediation process, a compliance analyst reviews the testing details for the endpoints and notes the endpoint device configuration does not support full disk encryption Which of the following is the most likely reason me device must be replaced'
Asoftware company deployed a new application based on its internal code repository Several customers are reporting anti-malware alerts on workstations used to test the application Which of the following is the most likely cause of the alerts?
Which of the following best describes the reason PQC preparation is important?
After some employees were caught uploading data to online personal storage accounts, a company becomes concerned about data leaks related to sensitive, internal documentation. Which of the following would the company most likely do to decrease this type of risk?
A security engineer is implementing a code signing requirement for all code developed by the organization. Currently, the PKI only generates website certificates. Which of the following steps should the engineer perform first?
A security engineer performed a code scan that resulted in many false positives. The security engineer must find asolution that improves the quality of scanning results before application deployment. Which of the following is the best solution?
A financial technology firm works collaboratively with business partners in the industry to share threat intelligence within a central platform This collaboration gives partner organizations the ability to obtain and share data associated with emerging threats from a variety of adversaries Which of the following should the organization most likely leverage to facilitate this activity? (Select two).
During a recent audit, a company's systems were assessed- Given the following information:
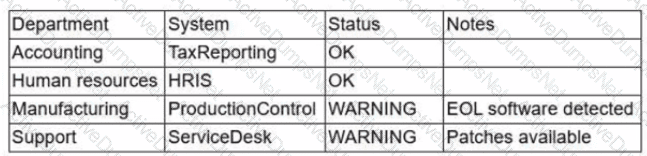
Which of the following is the best way to reduce the attack surface?
A systems administrator is working with clients to verify email-based services are performing properly. The administrator wants to have the email server digitally sign outbound emails using the organization's private key. Which of the following should the systems administrator configure?
An organization is developing a disaster recovery plan that requires data to be backed up and available at a moment's notice. Which of the following should the organization consider first to address this requirement?
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
After remote desktop capabilities were deployed in the environment, various vulnerabilities were noticed.
• Exfiltration of intellectual property
• Unencrypted files
• Weak user passwords
Which of the following is the best way to mitigate these vulnerabilities? (Select two).
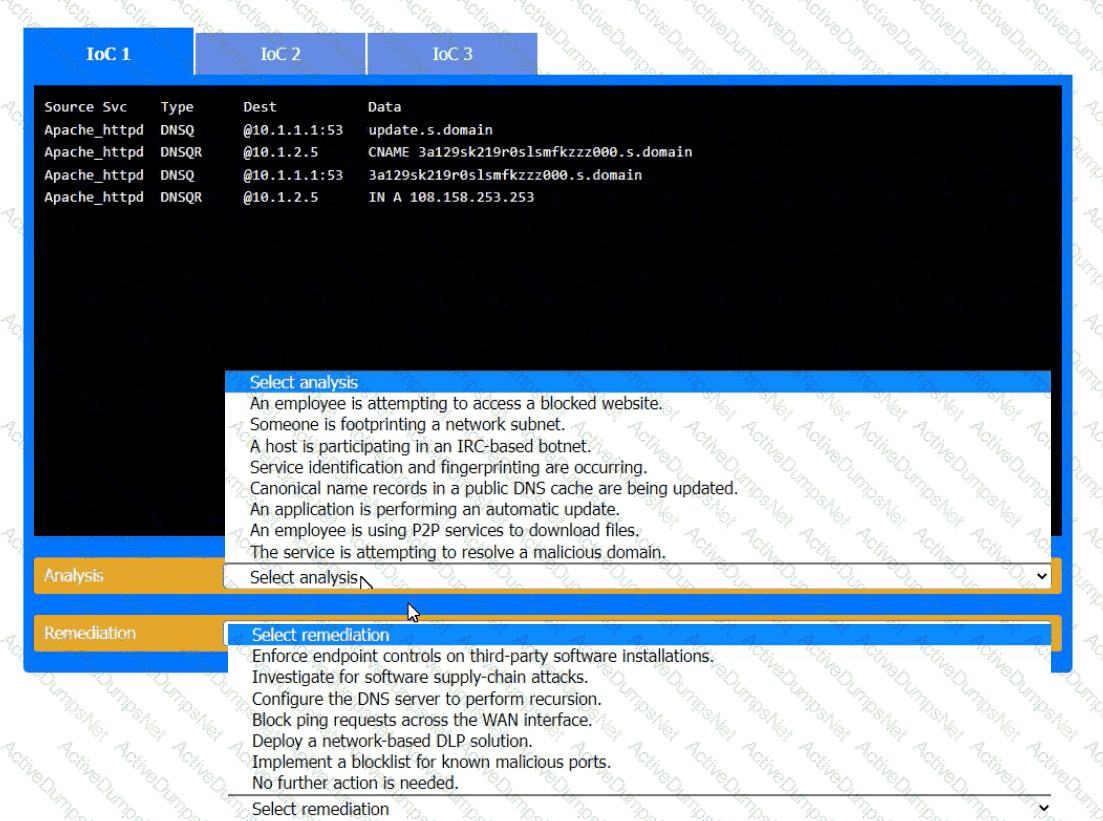
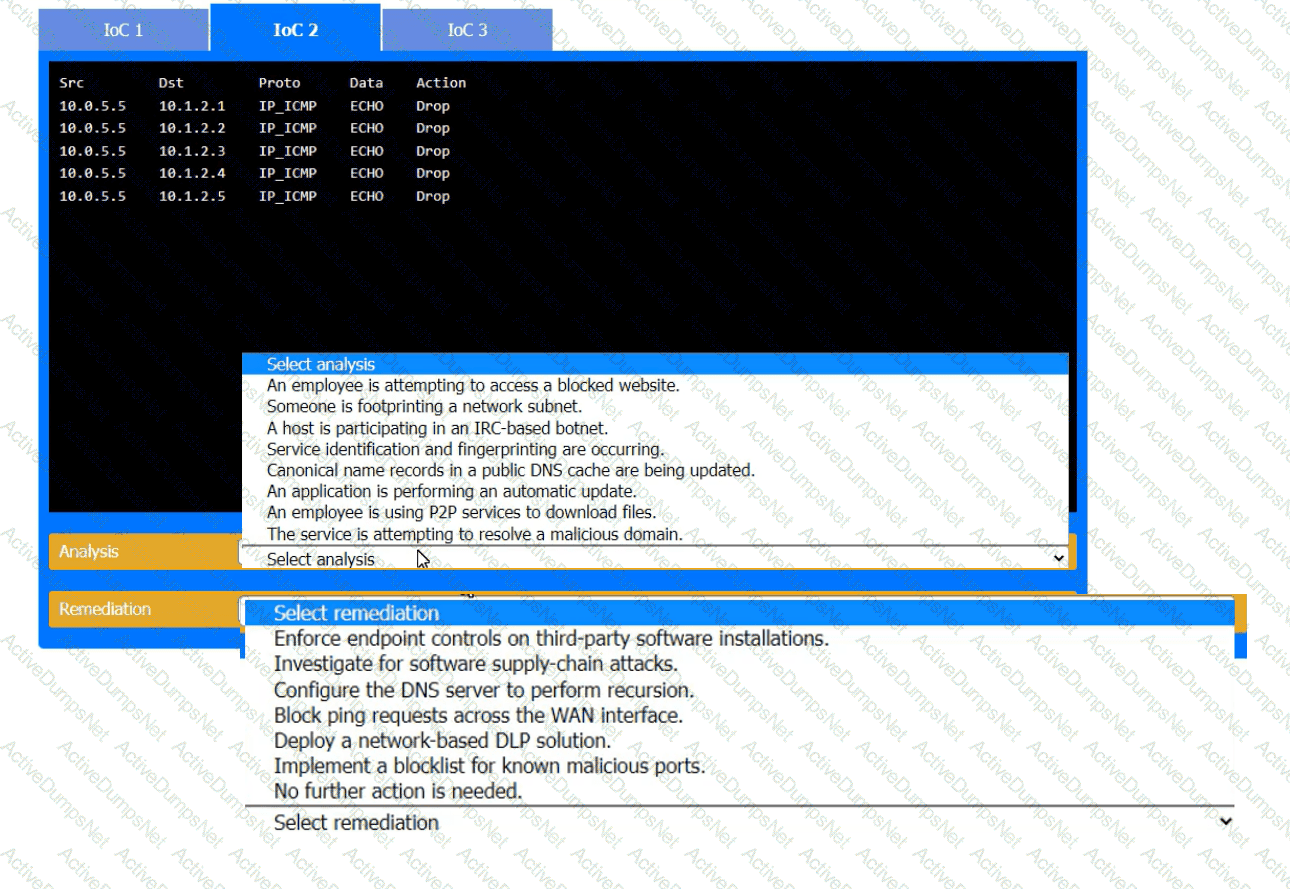
During the course of normal SOC operations, three anomalous events occurred and were flagged as potential IoCs. Evidence for each of these potential IoCs is provided.
INSTRUCTIONS
Review each of the events and select the appropriate analysis and remediation options for each IoC.
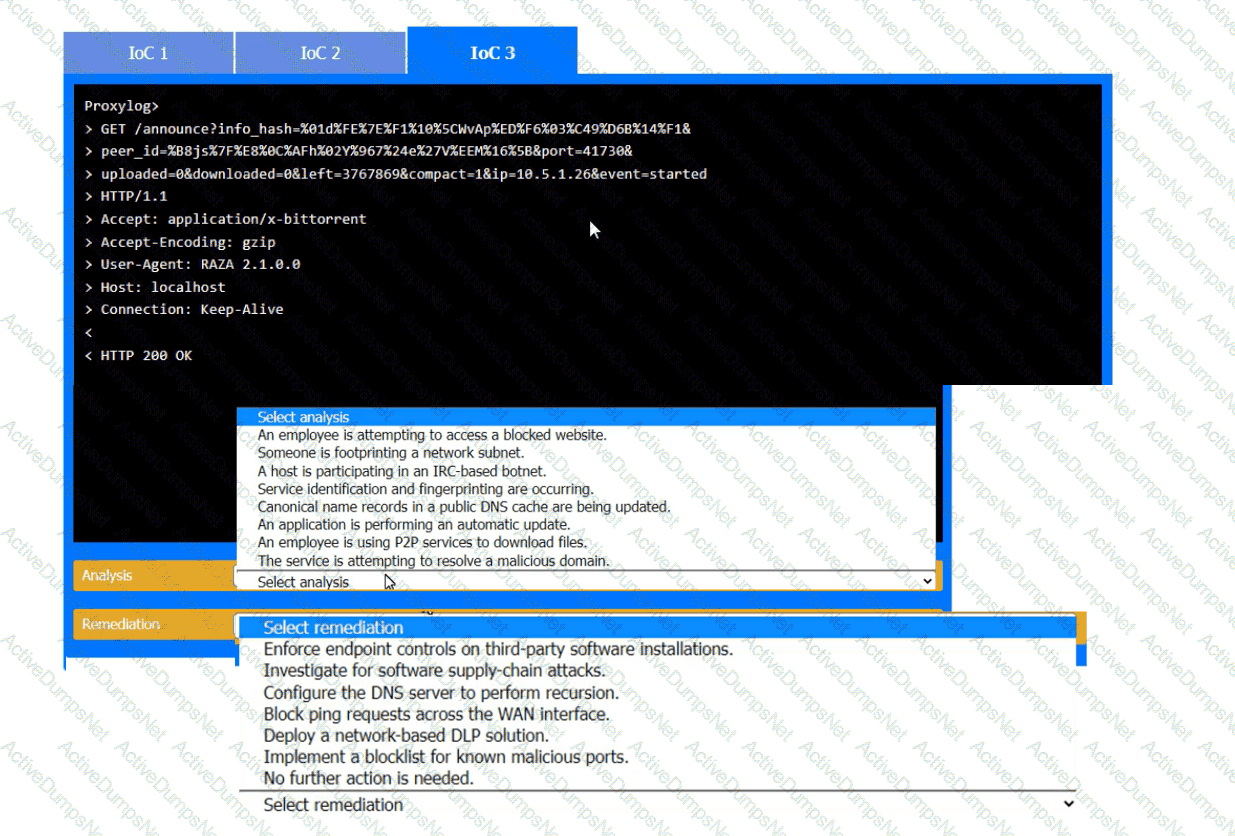
An analyst has prepared several possible solutions to a successful attack on the company. The solutions need to be implemented with the least amount of downtime. Which of the following should the analyst perform?
A systems administrator wants to reduce the number of failed patch deployments in an organization. The administrator discovers that system owners modify systems or applications in an ad hoc manner. Which of the following is the best way to reduce the number of failed patch deployments?
A large organization deployed a generative AI platform for its global user population to use. Based on feedback received during beta testing, engineers have identified issues with user interface latency and page-loading performance for international users. The infrastructure is currently maintained within two separate data centers, which are connected using high-availability networking and load balancers. Which of the following is the best way to address the performance issues?
A security analyst is reviewing the following authentication logs:
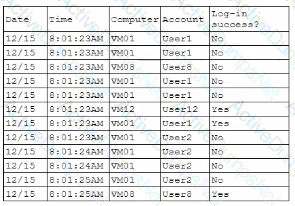
Which of the following should the analyst do first?
A security engineer is reviewing the following vulnerability scan report:
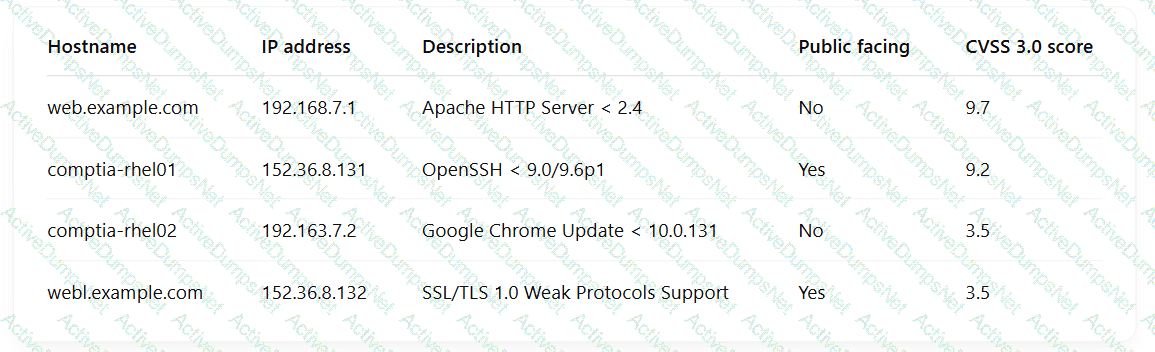
Which of the following should the engineer prioritize for remediation?
A security analyst Detected unusual network traffic related to program updating processes The analyst collected artifacts from compromised user workstations. The discovered artifacts were binary files with the same name as existing, valid binaries but. with different hashes which of the following solutions would most likely prevent this situation from reoccurring?
During a gap assessment, an organization notes that OYOD usage is asignificant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
A pharmaceutical lab hired a consultant to identify potential risks associated with Building 2, a new facility that is under construction. The consultant received the IT project plan, which includes the following VLAN design:
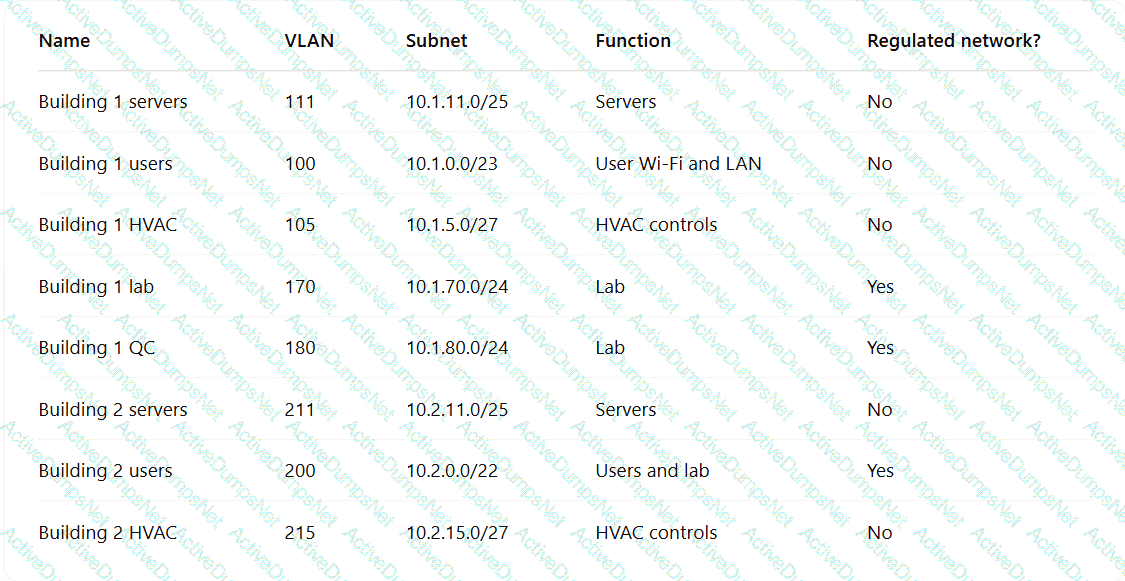
Which of the following TTPs should the consultant recommend be addressed first?
While investigating a security event an analyst finds evidence that a user opened an email attachment from an unknown source. Shortly after the user opened the attachment, a group of servers experienced a large amount of network and resource activity. Upon investigating the servers, the analyst discovers the servers were encrypted by ransomware that is demanding payment within 48 hours or all data will be destroyed. The company has no response plans for ransomware. Which of the following is the next step the analyst should take after reporting the incident to the management team?
An analyst reviews a SIEM and generates the following report:
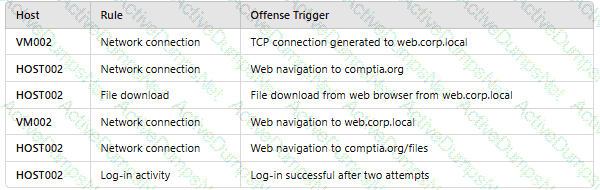
OnlyHOST002is authorized for internet traffic. Which of the following statements is accurate?
A security analyst is reviewing the following code in the public repository for potential risk concerns:
typescript
CopyEdit
include bouncycastle-1.4.jar;
include jquery-2.0.2.jar;
public static void main() {...}
public static void territory() { ... }
public static void state() { ... }
public static String code = "init";
public static String access_token = "spat-hfeiw-sogur-werdb-werib";
Which of the following should the security analyst recommend first to remediate the vulnerability?
Within a SCADA a business needs access to the historian server in order together metric about the functionality of the environment. Which of the following actions should be taken to address this requirement?
A systems engineer is configuring SSO for a business that will be using SaaS applications for its remote-only workforce. Privileged actions in SaaS applications must be allowed only from corporate mobile devices that meet minimum security requirements, but BYOD must also be permitted for other activity. Which of the following would best meet this objective?
A security analyst is reviewing the following vulnerability assessment report:
192.168.1.5, Host = Server1, CVSS 7.5, Web Server, Remotely Executable = Yes, Exploit = Yes
205.1.3.5, Host = Server2, CVSS 6.5, Bind Server, Remotely Executable = Yes, Exploit = POC
207.1.5.7, Host = Server3, CVSS 5.5, Email Server, Remotely Executable = Yes, Exploit = Yes
192.168.1.6, Host = Server4, CVSS 9.8, Domain Controller, Remotely Executable = Yes, Exploit = Yes
Which of the following should be patched first to minimize attacks against internet-facing hosts?
A network engineer must ensure that always-on VPN access is enabled Curt restricted to company assets Which of the following best describes what the engineer needs to do''
A company’sSIEMis designed to associate the company’sasset inventorywith user events. Given the following report:
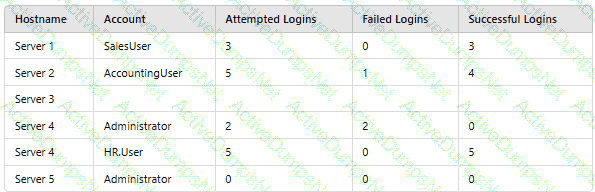
Which of thefollowing should asecurity engineer investigate firstas part of alog audit?
A company migrating to aremote work model requires that company-owned devices connect to a VPN before logging in to the device itself. The VPN gateway requires that a specific key extension is deployed to the machine certificates in the internal PKI. Which of the following best explains this requirement?
A recent security audit identified multiple endpoints have the following vulnerabilities:
• Various unsecured open ports
• Active accounts for terminated personnel
• Endpoint protection software with legacy versions
• Overly permissive access rules
Which of the following would best mitigate these risks? (Select three).
A company implemented a NIDS and a NIPS on the most critical environments. Since this implementation, the company has been experiencing network connectivity issues. Which of the following should the security architect recommend for a new NIDS/NIPS implementation?
An organization recently implemented a new email DLP solution. Emails sent from company email addresses to matching personal email addresses generated a large number of alerts, but the content of the emails did not include company data. The security team needs to reduce the number of emails sent without blocking all emails to common personal email services. Which of the following should the security team implement first?
A security analyst received a report that an internal web page is down after a company-wide update to the web browser Given the following error message:

Which of the following is the b«« way to fix this issue?
Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?
A security engineer is developing a solution to meet the following requirements?
• All endpoints should be able to establish telemetry with a SIEM.
• All endpoints should be able to be integrated into the XDR platform.
• SOC services should be able to monitor the XDR platform
Which of the following should the security engineer implement to meet the requirements?
Operational technology often relies upon aging command, control, and telemetry subsystems that were created with the design assumption of:
After an organization met with its ISAC, the organization decided to test the resiliency of its security controls against a small number of advanced threat actors. Which of the following will enable the security administrator to accomplish this task?