Cisco 500-220 Engineering Cisco Meraki Solutions (ECMS) v2.2 Exam Practice Test
Engineering Cisco Meraki Solutions (ECMS) v2.2 Questions and Answers
There will be 100 concurrent users streaming video to their laptops. A 30/70 split between 2.4 Ghz and 5 Ghz will be used. Roughly how many APs (rounded to the nearest whole number) are needed based on client count?
Which Cisco Meraki best practice method preserves complete historical network event logs?
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
Refer to the exhibit.
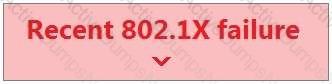
For an AP that displays this alert, which network access control method must be in use?
Refer to the exhibit.
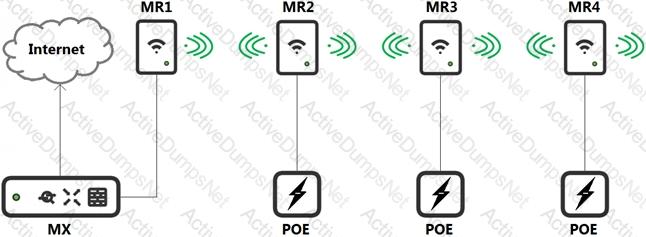
Which design recommendation should be considered?
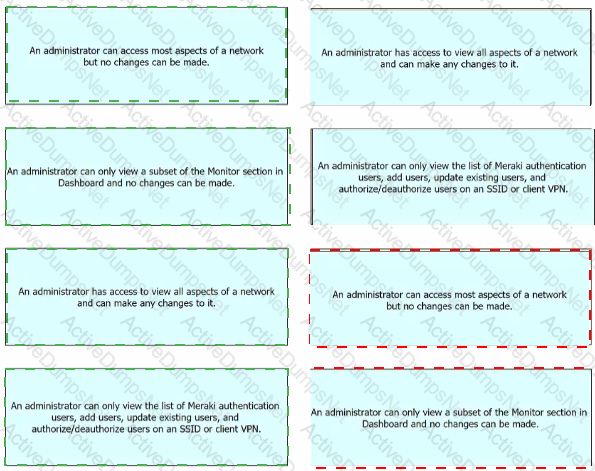
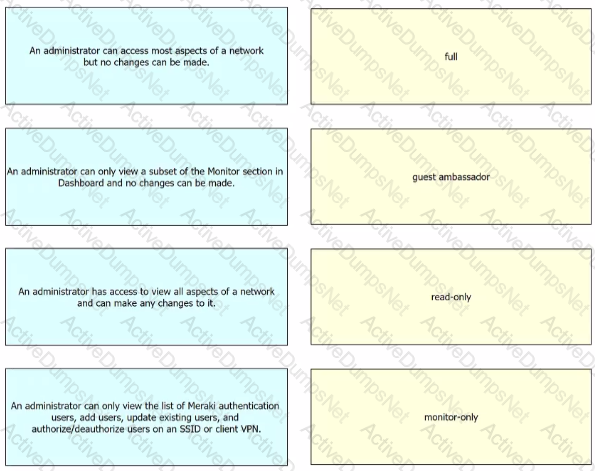
What are two organization permission types? (Choose two.)
One thousand concurrent users stream video to their laptops. A 30/70 split between 2.4 GHz and 5 GHz is used.
Based on client count, how many APs (rounded to the nearest whole number) are needed?
What is a feature of distributed Layer 3 roaming?
Refer to the exhibit.
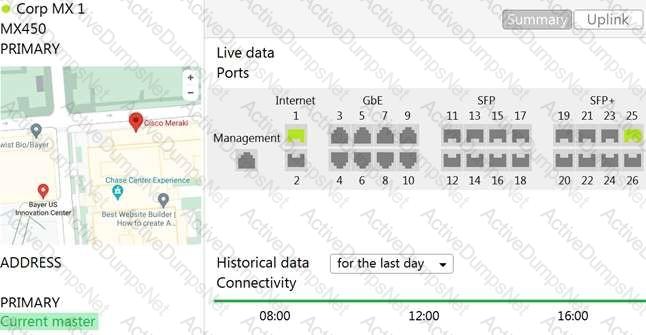
The VPN concentrator is experiencing issues. Which action should be taken to ensure a stable environment?
Drag and drop the descriptions from the left onto the permission types on the right.
Refer to the exhibit.
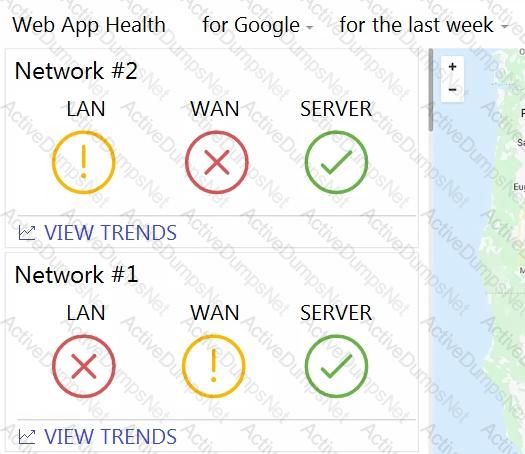
What are two outcomes reflected in the Web App Health application? (Choose two.)
Refer to the exhibit.
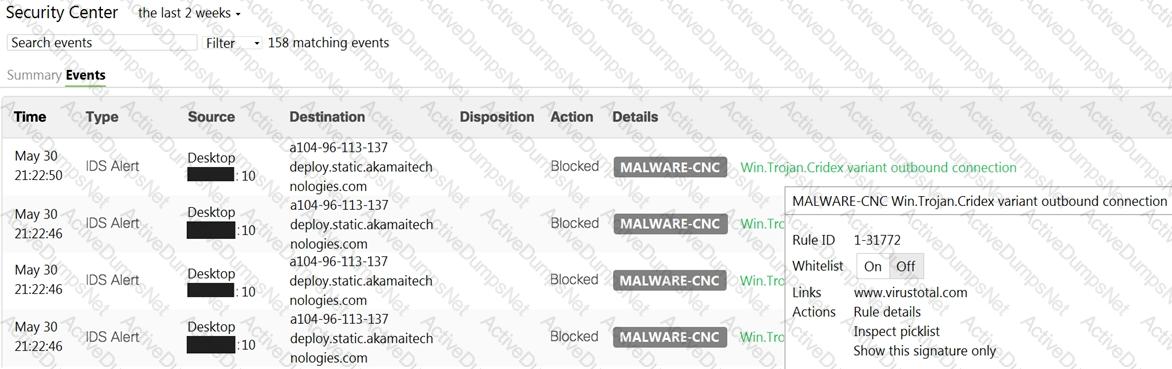
Which IDS/IPS mode is the MX Security Appliance configured for?
Refer to the exhibit.
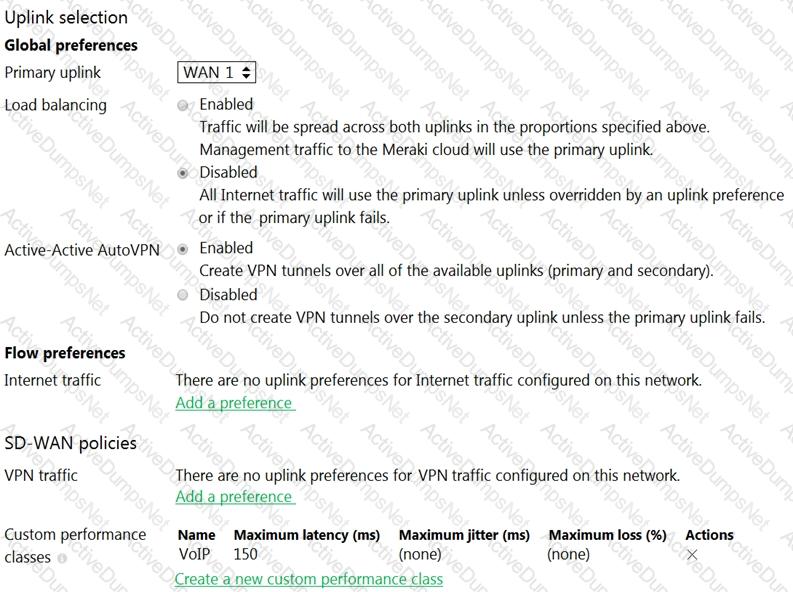
What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?
What happens to an unsupervised iOS device when the “Meraki management” profile is removed?
An organization requires that BYOD devices be enrolled in Systems Manager before they gain access to the network. Part of the enrollment includes pushing out the corporate SSID preshared key, corporate email settings, and some business-sensitive PDFs. When a user leaves the organization, which Systems Manager feature allows the removal of only the MDM-delivered content from the user's device?
What is the default frequency of SD-WAN probes sent between VPN peers in a Cisco Meraki MX SD-WAN deployment?
Which order is accurate for a firmware upgrade on MX appliances in a high-availability configuration?
When wireless SSIDs are configured in Dashboard, which setting on the Access Control page affects the ability of a 2.4 GHz only client device from associating to the WLAN for the first time?
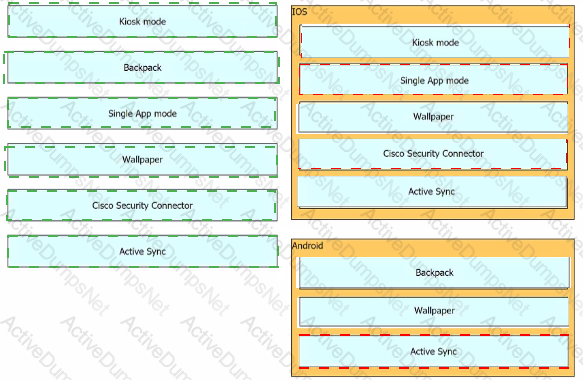
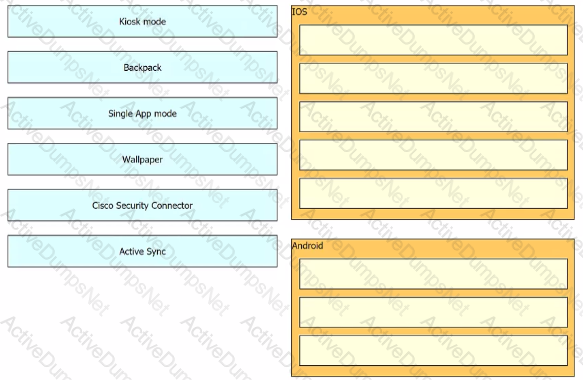
Drag and drop the settings from the left onto the OS system or systems that support it on the right Settings can be used more than once.
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
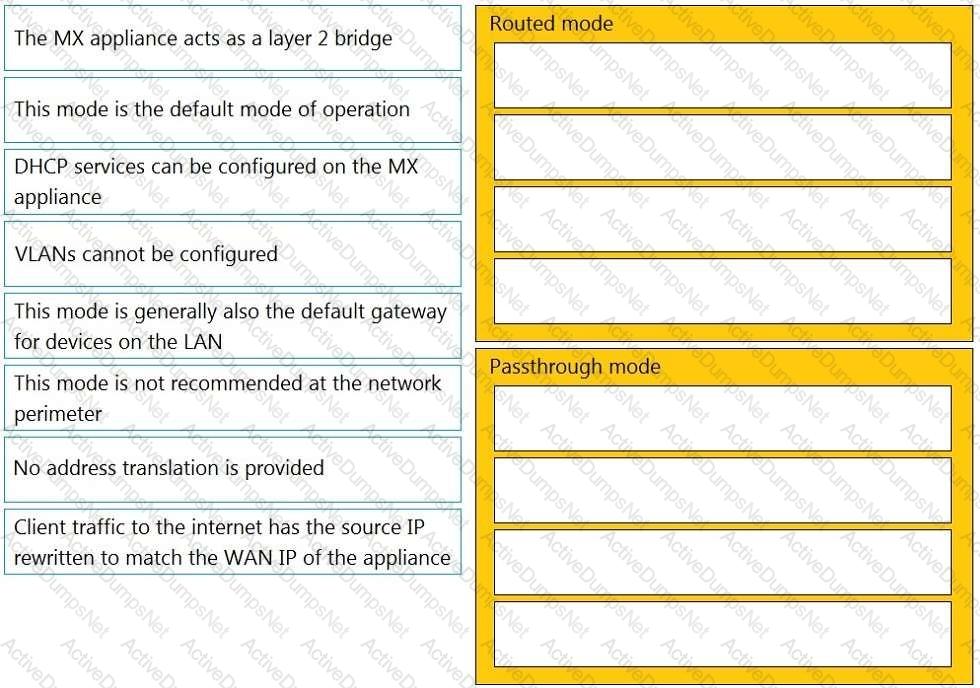
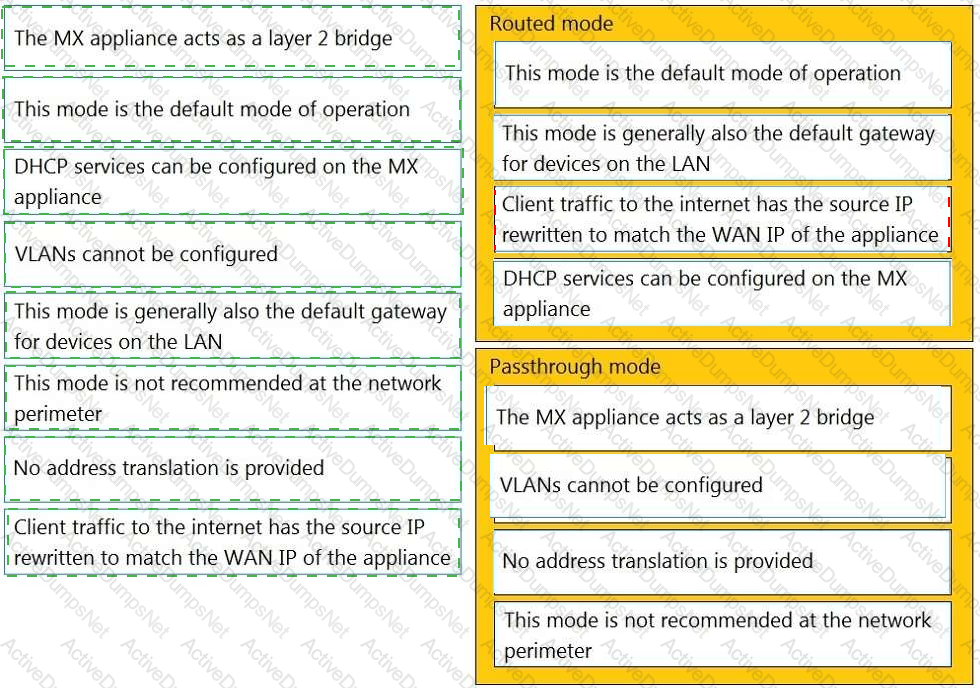
Drag and drop the descriptions from the left onto the corresponding MX operation mode on the right.