Cisco 400-007 Cisco Certified Design Expert (CCDE v3.1) Exam Practice Test
Cisco Certified Design Expert (CCDE v3.1) Questions and Answers
When a company network architect is working on a new network design, they are expected to ensure that business requirements and technical aspects are factored in, but often there are other factors that come into play as well. Which non-business constraint must also be considered throughout the design phase?
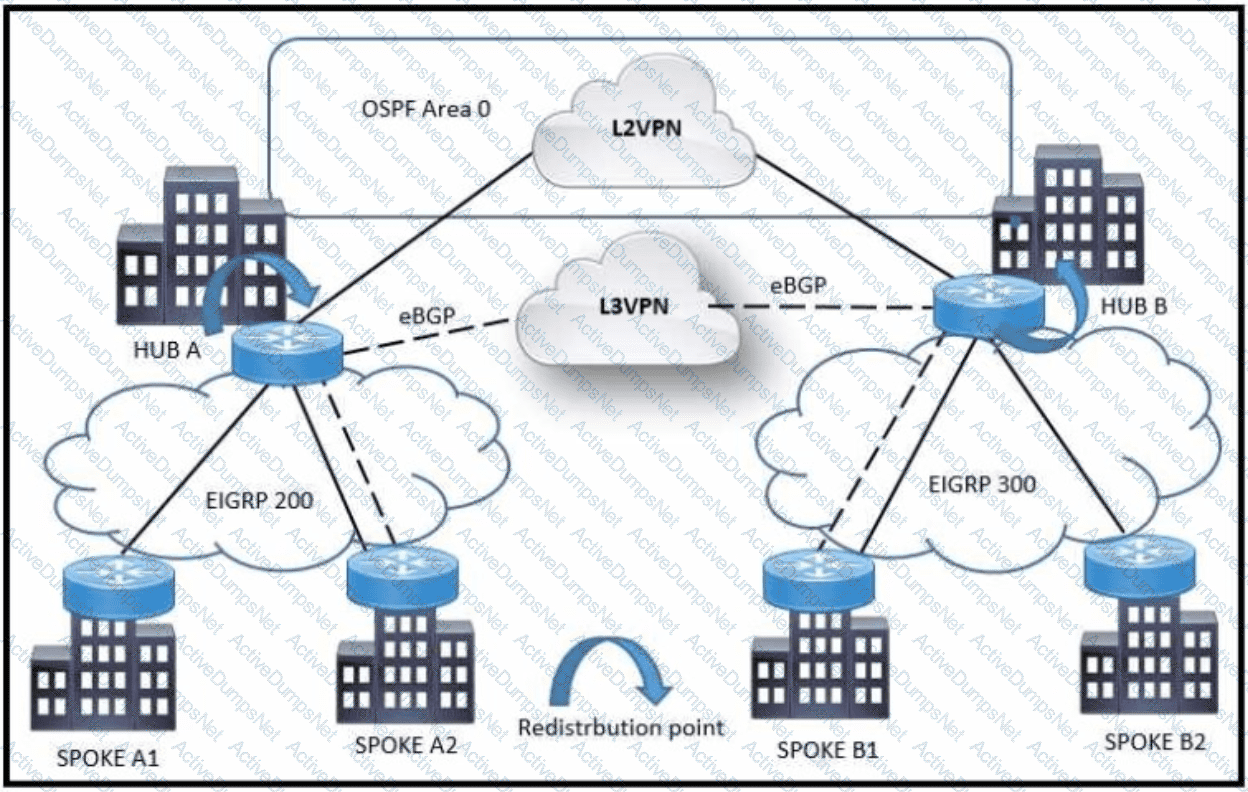
Refer to the exhibit: A customer is migrating from a TDM-based Layer 2 VPN (L2VPN) to an MPLS Layer 3 VPN (L3VPN) in phases. The backbone OSPF connection between HUB A and HUB B will be replaced by eBGP. During the migration, some spokes (A2 and B1) are already moved to the L3VPN. The goal is to avoid routing loops during this hybrid transition.
Which design choice helps prevent routing loops during the backbone link migration?
The goal for any network designer is to strive to build a resilient network that adapts to changing conditions rapidly with minimal impact on the services running over the network. A resilient network can adapt to failures, but which soft failure can be harder to define and detect?
Company XYZ wants to deploy OSPF. The design plan requires that two OSPF networks be mutually redistributed at multiple locations and ensure end-to-end connectivity to all of the company's networks. Which technology can be used to fulfill the requirements while avoiding the creation of routing loops?
A product manufacturing organization is integrating cloud services into their IT solution. The IT team is working on the preparation phase of the implementation approach, which includes the Define Strategy step. This step defines the scope of IT, the application, and the service. What is one topic that should be considered in the Define Strategy step?
Sometimes SDN leverages various overlay networking technologies to create layer(s) of network abstraction. What describes an overlay network?
You are designing a new Ethernet-based metro-area network for an enterprise customer to connect 50 sites within the same city. OSPF will be the routing protocol used. The customer is primarily concerned with IPv4 address conservation and convergence time. Which two combined actions do you recommend? (Choose two)
Company XYZ wants to use the FCAPS ISO standard for network management design. The focus of the design should be to monitor and keep track of any performance issues by continuously collecting and analyzing statistical information to monitor, correct, and optimize any reduced responsiveness across the network. Which layer accomplishes this design requirement?
Company XYZ was not satisfied with the reconvergence time OSPF is taking. BFD was implemented to try to reduce the reconvergence time, but the network is still experiencing delays when having to reconverge. Which technology will improve the design?
How can EIGRP topologies be designed to converge as fast as possible in the event of a point-to-point link failure?
Which three Cisco products are used in conjunction with Red Hat to provide an NFVi solution? (Choose three.)
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two.)
The administrator of a small branch office wants to implement the Layer 2 network without running STP. The office has some redundant paths. Which mechanism can the administrator use to allow redundancy without creating Layer 2 loops?
Refer to the exhibit.
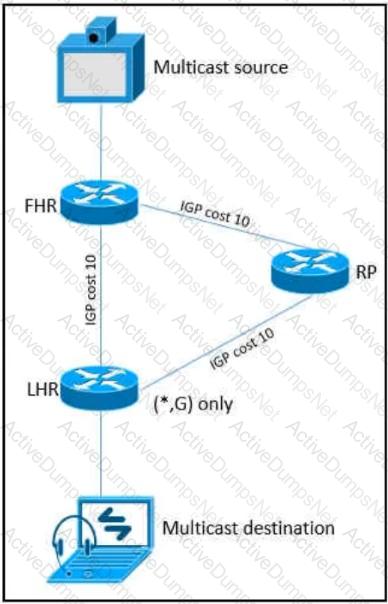
As part of a redesign project, you must predict multicast behavior. What happens to the multicast traffic received on the shared tree (*,G), if it is received on the LHR interface indicated?
Network changes due to mergers, acquisitions, and divestitures can be highly disruptive if not carefully planned. When an organization sells part of its business, it must detach those parts of the network with minimal risk and downtime.
Which network design approach is appropriate to minimize the impact and risks as the divested parts of the network are detached?
A consultant needs to evaluate project management methodologies for a new service deployment on the existing network of a customer. The customer wants to be involved in the end-to-end project progress and be provided with frequent updates. The customer also wants the ability to change the requirements if needed, as the project progresses. Which project management methodology should be used?
An IT service provider is upgrading network infrastructure to comply with PCI security standards. The network team finds that 802.1X and VPN authentication based on locally-significant certificates are not available on some legacy phones. Which workaround solution meets the requirement?
The Company XYZ network requires OSPF dead neighbor detection in a subsecond manner. However, the company network does not support BFD. Which other feature can be used to fulfill the design requirement?
What statement describes the application layer as defined in the software-defined networking architecture?
Which two foundational aspects of IoT are still evolving and being worked on by the industry at large? (Choose two)
Refer to the exhibit.
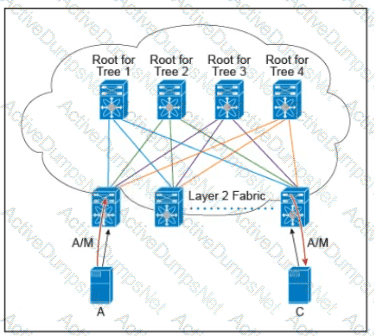
There are multiple trees in the Cisco FabricPath. All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two.)
Which methodology is the leading lifecycle approach to network design and implementation?
What is a web-based model in which a third-party provider hosts applications that are available to customers over the Internet?
A network engineering team is in the process of designing a lab network for a customer demonstration. The design engineer wants to show that the resiliency of the MPLS Traffic Engineering Fast Reroute solution has the same failover/failback times as a traditional SONET/SDH network (around 50 msec). In order to address both link failure and node failure within the lab topology network, which type of the MPLS TE tunnels must be considered for this demonstration?
The network designer needs to use GLOP IP addresses in order to make them unique within their ASN. Which multicast address range should be used?
An engineer is designing a DMVPN network where OSPF has been chosen as the routing protocol. A spoke-to-spoke data propagation model must be set up. Which two design considerations must be taken into account? (Choose two)
What advantage of placing the IS-IS Layer 2 flooding domain boundary at the core layer in a three-layer hierarchical network is true?
A company requires an RPO of less than 10 seconds to ensure business continuity. Which technology should be deployed?
Which two actions ensure voice quality in a branch location with a low-speed, high-latency WAN connection? (Choose two.)
A software-defined networking (SDN) controller learns network topology information by using BGP link-state sessions with the route reflectors of an MPLS-enabled network. The controller then uses the topology information to apply on-demand traffic policies to the network through a protocol that is supported from all Layer 3 routers. Each policy is represented as a RIB entry in the control plane of the router. Which SDN model has been implemented?
You have been tasked with designing a data center interconnect as part of business continuity. You want to use FCoE over this DCI to support synchronous replication. Which two technologies allow for FCoE via lossless Ethernet or data center bridging? (Choose two.)
As a network designer, you need to support an enterprise with hundreds of remote sites connected over a single WAN network that carries different types of traffic, including VoIP, video, and data applications. Which of the following design considerations will not impact design decision?
Which main IoT migration aspect should be reviewed for a manufacturing plant?
In outsourced IT services, the RTO is defined within the SLA. Which two support terms are often included in the SLA by IT and other service providers? (Choose two.)
In a redundant hub-and-spoke design with inter-spoke links, load oscillation and routing instability occur due to overload conditions. Which two design changes improve resiliency? (Choose two)
An enterprise campus is adopting a network virtualization design solution with these requirements:
• It must include the ability to virtualize the data plane and control plane by using VLANs and VRFs
• It must maintain end-to-end logical path transport separation across the network
• Resources available grouped at the access edge
Which two primary models can this network virtualization design be categorized? (Choose two)
Which two actions must be taken when assessing an existing wireless network implementation for its readiness to support voice traffic? (Choose two.)
In an OSPF network with routers connected together with Ethernet cabling, which topology typically takes the longest to converge?
Over the years, many solutions have been developed to limit control plane state which reduces the scope or the speed of control plane information propagation. Which solution removes more specific information about a particular destination as topological distance is covered in the network?
Software-defined networking architecture is used for cost-effective, adaptable, and easily manageable applications. In which two software-defined networks is SDN commonly used? (Choose two.)
A network architect is designing a policy where database applications access the internet directly, while other traffic routes through the data center, with dynamic path switching based on performance. Which solution meets these requirements?
Which two advantages of using DWDM over traditional optical networks are true? (Choose two.)
A business invests in SDN and develops its own SDN controller that, due to budget constraints, runs on a single controller. The controller actively places an exclusive lock on the configuration of the devices to ensure it is the only source of changes to the environment. What is the result if the controller fails?
Which design benefit of PortFast is true?
Company XYZ is in the process of identifying which transport mechanism(s) to use as their WAN technology. Their main two requirements are:
A technology that could offer DPI, SLA, secure tunnels, privacy, QoS, scalability, reliability, and ease of management.
A technology that is cost-effective.
Which WAN technology(ies) should be included in the design of company XYZ?
Company XYZ wants to prevent switch loops caused by unidirectional point-to-point link conditions on Rapid PVST+ and MST. Which technology can be used in the design to meet this requirement?
What is a disadvantage of the traditional three-tier architecture model when east-west traffic between different pods must go through the distribution and core layers?
The controller has a global view of the network, and it can easily ensure that the network is in a consistent and optimal configuration. Which two statements describe a centralized SDN control path? (Choose two.)
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?
An architect prepares a network design for a startup company. The design must meet business requirements while the business grows and divests due to rapidly changing markets. What is the highest priority in this design?
Which DCI technology utilizes a “flood and learn” technique to populate the Layer 2 forwarding table?
Which feature must be part of the network design to wait a predetermined amount of time before notifying the routing protocol of a change in the path in the network?
Company XYZ, a global content provider, owns data centers on different continents. Their data center design involves a standard three-layer design with a Layer 3-only core. VRRP is used as the FHRP. They require VLAN extension across access switches in all data centers and plan to purchase a Layer 2 interconnection between two of their data centers in Europe. In the absence of other business or technical constraints, which termination point is optimal for the Layer 2 interconnection?
What is a disadvantage of the traditional three-tier architecture model when east-west traffic between different pods must go through the distribution and core layers?
Refer to the exhibit.
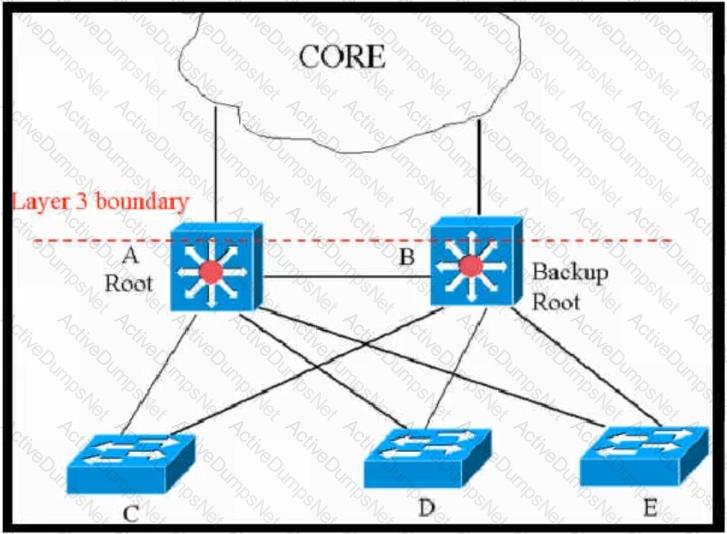
This network is running legacy STP 802.1d. Assuming "hello_timer" is fixed to 2 seconds, which parameters can be modified to speed up convergence times after single link/node failure?
Company XYZ has implemented policy-based routing in their network. Which potential problem must be kept in mind about network reconvergence and PBR?
Which two impacts of adding the IP event dampening feature to a network design are true? (Choose two.)
Which two data plane hardening techniques are true? (Choose two)
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)
Refer to the diagram.
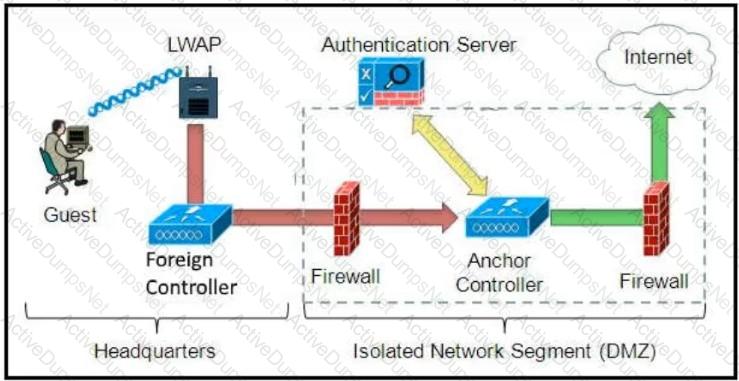
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
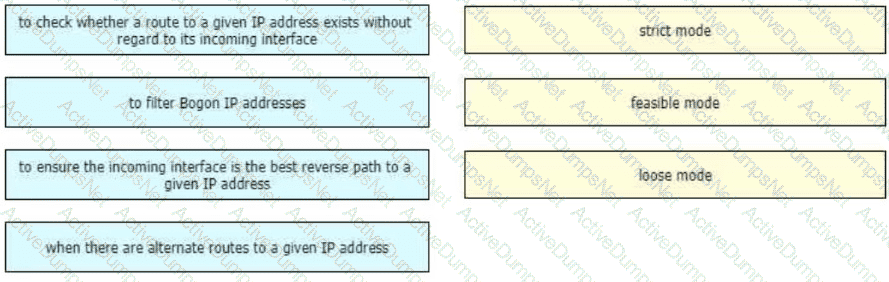
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks Not all options are used.
Which two statements describe the usage of the IS-IS overload bit technique? (Choose two.)
A network design includes a long signaling delay in notifying the Layer 3 control plane that an interface has failed. Which two of these actions would reduce that delay? (Choose two.)
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two.)
You are designing a network running both IPv4 and IPv6 to deploy QoS. Which consideration is correct about the QoS for IPv4 and IPv6?
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. Which activity should be completed each time a legacy network is migrated?
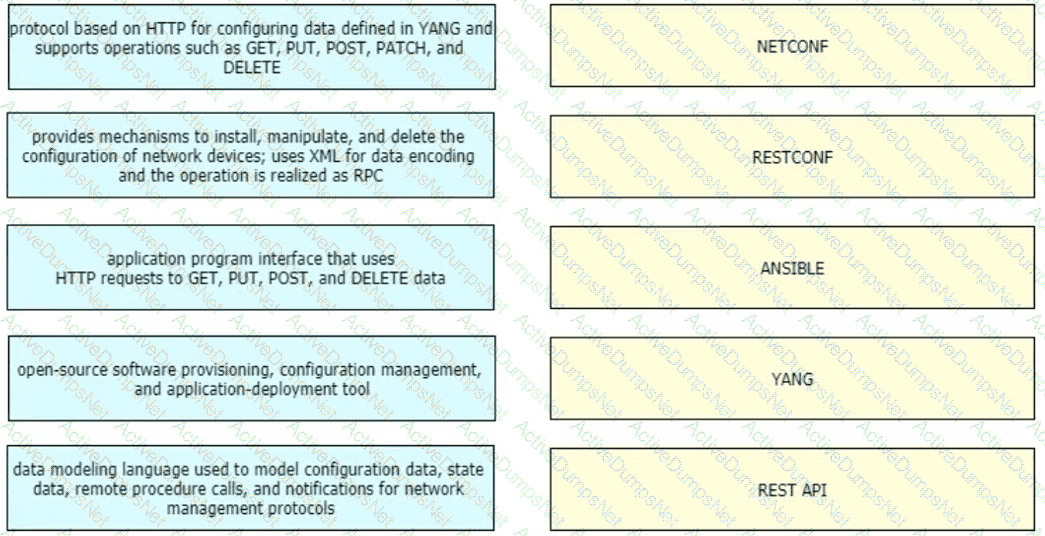
Drag and drop the characteristics from the left onto the corresponding network management options on the right.
Which Interconnectivity method offers the fastest convergence in the event of a unidirectional issue between three Layer 3 switches connected together with routed links in the same rack in a data center?
Which issue poses a challenge for security architects who want end-to-end visibility of their networks?
Refer to the table.
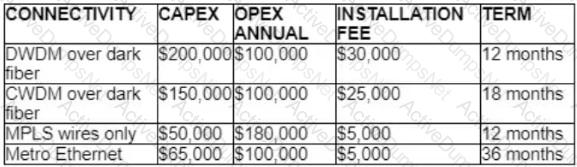
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads. Which transport technology provides the best ROI based on cost and flexibility?
What is a description of a control plane action?
The SD-WAN architecture is composed of separate orchestration, management, control, and data planes. Which activity happens at the orchestration plane?
An international media provider faces challenges managing deployed services with a homegrown orchestration system. Which platform is well-suited as a state-aware orchestration system?
An MPLS service provider is offering a standard EoMPLS-based VPLS service to Customer A, providing Layer 2 connectivity between a central site and approximately 100 remote sites. Customer A wants to use the VPLS network to carry its internal multicast video feeds which are sourced at the central site and consist of 20 groups at Mbps each. Which service provider recommendation offers the most scalability?
Which two features are advantages of SD-WAN compared to MPLS-based connectivity? (Choose two.)
A multinational enterprise integrates a cloud solution with these objectives:
• Achieve seamless connectivity across different countries and regions
• Extend data center and private clouds into public clouds and provider-hosted clouds
What are two outcomes of deploying data centers and fabrics that interconnect different cloud networks? (Choose two.)
What are two advantages of controller-based networks versus traditional networks? (Choose two.)
Refer to the exhibit.
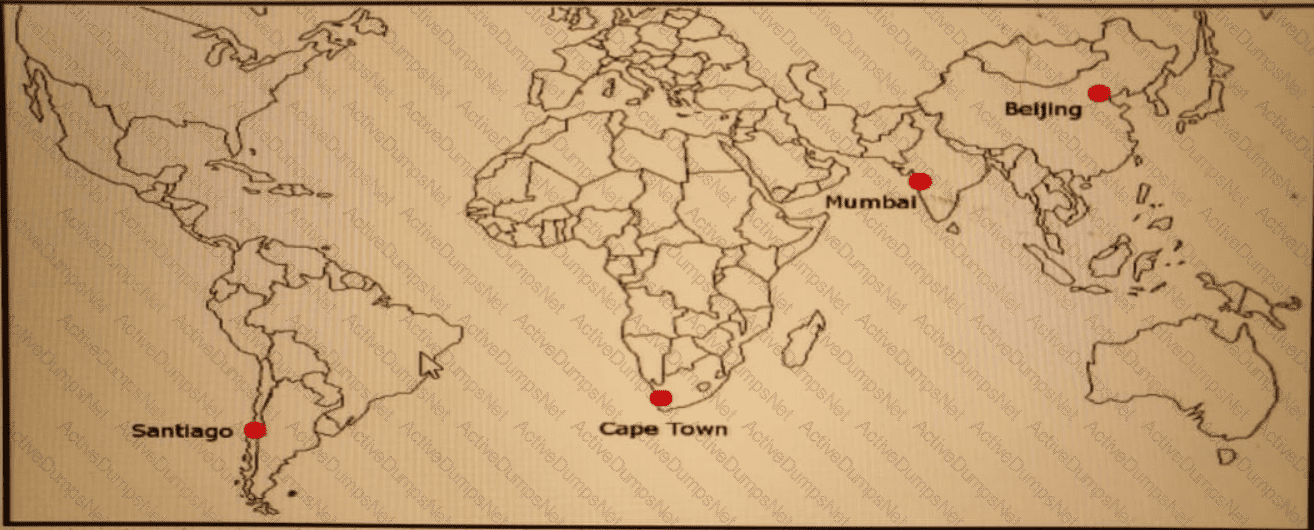
ACME Mining has four data centers in Santiago. Cape Town. Mumbai, and Beijing, full-mesh connected via a 400 Mb/s EVP-LAN They want to deploy a new mission-critical application with these
requirements:
clusterheartbeat2Mb/s continuous (250 KB/s)
cluster heartbeat one-way maximum latency 100 ms
These are the current ping tests results between the four data centers:
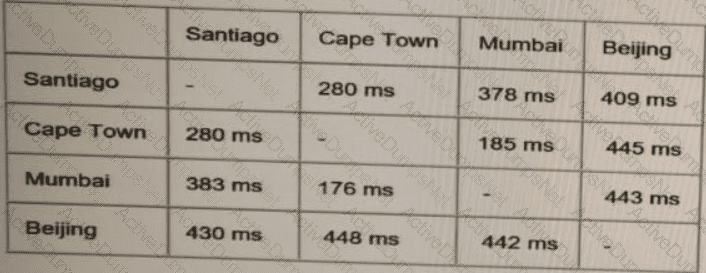
Which hosting data center pair can host the new application?
Company XYZ has 30 sites running a legacy private WAN architecture that connects to the Internet via multiple high-speed connections. The company is now redesigning their network and must comply with these design requirements:
Use a private WAN strategy that allows the sites to connect to each other directly and caters for future expansion.
Use the Internet as the underlay for the private WAN.
Securely transfer the corporate data over the private WAN.
Which two technologies should be incorporated into the design of this network? (Choose two.)
Router R1 is a BGP speaker with one peering neighbor over link "A". When link "A" fails, routing announcements are terminated, which results in the tearing down of the state for all BGP routes at each end of the link. What is this a good example of?
Which three tools are used for ongoing monitoring and maintenance of a voice and video environment? (Choose three.)
Refer to the exhibit.
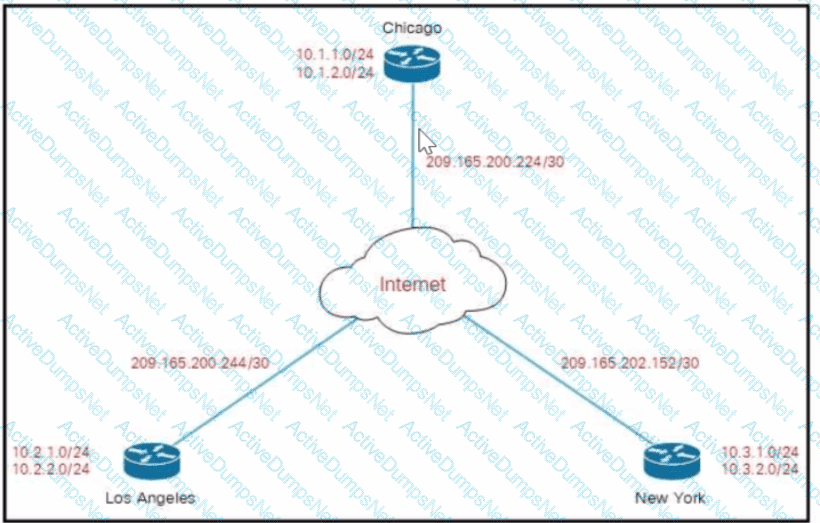
Company XYZ must design a DMVPN tunnel between the three sites. Chicago is going to act as the NHS, and the company wants DMVPN to detect peer endpoint failures. Which technology should be used in the design?
How many fully established neighbour relationships exist on an Ethernet with five routers running OSPF as network type broadcast?
A key to maintaining a highly available network is building in the appropriate redundancy to protect against failure. This redundancy is carefully balanced with the inherent complexity of redundant systems. Which design consideration is relevant for enterprise WAN use cases when it comes to resiliency?
Which two benefits can software defined networks provide to businesses? (Choose two.)
You are designing a network for a branch office. In order to improve convergence time, you are required to use the BFD feature. Which four routing protocols can you use to facilitate this? (Choose four.)
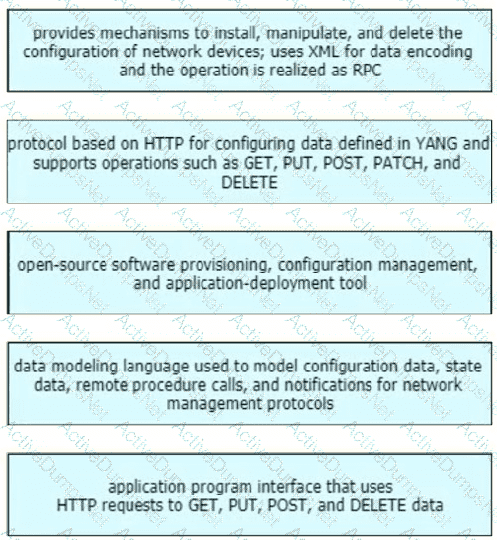
What best describes the difference between Automation and Orchestration?
Refer to the exhibit.
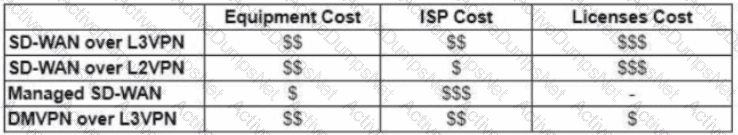
The WAN network of the General Bank of Greece has experienced several outages. It takes too long to activate a new branch site. The networking department of the bank plans to upgrade the legacy end-of-life WAN network with a new flexible, manageable, and scalable in-house solution. The number of branches will increase exponentially in the next fiscal year. The CTO states that the bank’s main goal is OPEX reduction. The network engineering team prepares a table to evaluate the available options. Which WAN technology can be used for the solution?
An enterprise solution team is analyzing multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface. Which requirement addresses this ability on a multicontroller platform?
When consumers that leverage IaaS reach 100% resource capacity, what can be used to redirect the overflow of traffic to the public cloud so there is no disruption to service?
What is a country-specific requirement that data is subject to the laws of the country in which it is collected or processed and must remain within its borders?
IPFIX data collection via standalone IPFIX probes is an alternative to flow collection from routers and switches. Which use case is suitable for using IPFIX probes?
Which two statements describe network automation and network orchestration? (Choose two.)
Company XYZ asks for design recommendations for Layer 2 redundancy. The company wants to prioritize fast convergence and resiliency elements. In the design, which two technologies are recommended? (Choose two.)
You were tasked to enhance the security of a network with these characteristics:
A pool of servers is accessed by numerous data centers and remote sites
The servers are accessed via a cluster of firewalls
The firewalls are configured properly and are not dropping traffic
The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
Identity and access management between multiple users and multiple applications has become a mandatory requirement for Company XYZ to fight against ever-increasing cybersecurity threats. To achieve this, federated identity services have been deployed to provide Single Sign-On and Multi-Factor Authentication. Which protocol can be used by Company XYZ to provide authentication and authorization services?
Company XYZ has a new network based on IPv6. Some of the subnets that they are planning to use will be confidential and need an addressing scheme that confines them to the local campus network. Which type of IPv6 addresses can be used for these networks in the IPv6 addressing design?
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
You have been asked to design a remote access VPN solution to support up to 2000 devices. You must ensure that only corporate assets are allowed to connect to the VPN, and users must authenticate to gain access based on their user role. Users must use a password that they are already using to access existing applications. A user may not always use the same device to access the VPN. Which two options combined meet the requirements? (Choose two)
An enterprise plans to evolve from a traditional WAN network to a software-defined WAN network. The existing devices have limited capability when it comes to virtualization. As the migration is carried out, enterprise applications and services must not experience any traffic impact. Which implementation plan can be used to accommodate this during the migration phase?
Company XYZ is running SNMPv1 in their network and understands that it has some flaws. They want to change the security design to implement SNMPv3 in the network. Which network threat is SNMPv3 effective against?
Company XYZ has two routing domains (EIGRP and OSPF). They want full reachability and need OSPF to see link costs added to external routes. How must redistribution be designed?
Company XYZ is running a redundant private WAN network using OSPF as the underlay protocol. The current design accommodates for redundancy in the network, but it is taking over 30 seconds for the network to reconverge upon failure. Which technique can be implemented in the design to detect such a failure in a subsecond?
Which two statements about MLD snooping are true? (Choose two)




 Text
Description automatically generated
Text
Description automatically generated