Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Exam Practice Test
Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Questions and Answers
What is a risk to data privacy during the storage and transmission of data?
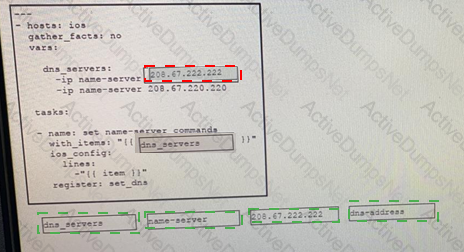
Drag and drop the code from the bottom onto the box where the code is missing the snippet to complete this Ansible Playbook. Not all options are used.

Which function does Fluentd fulfill for application logging in Kubernetes?
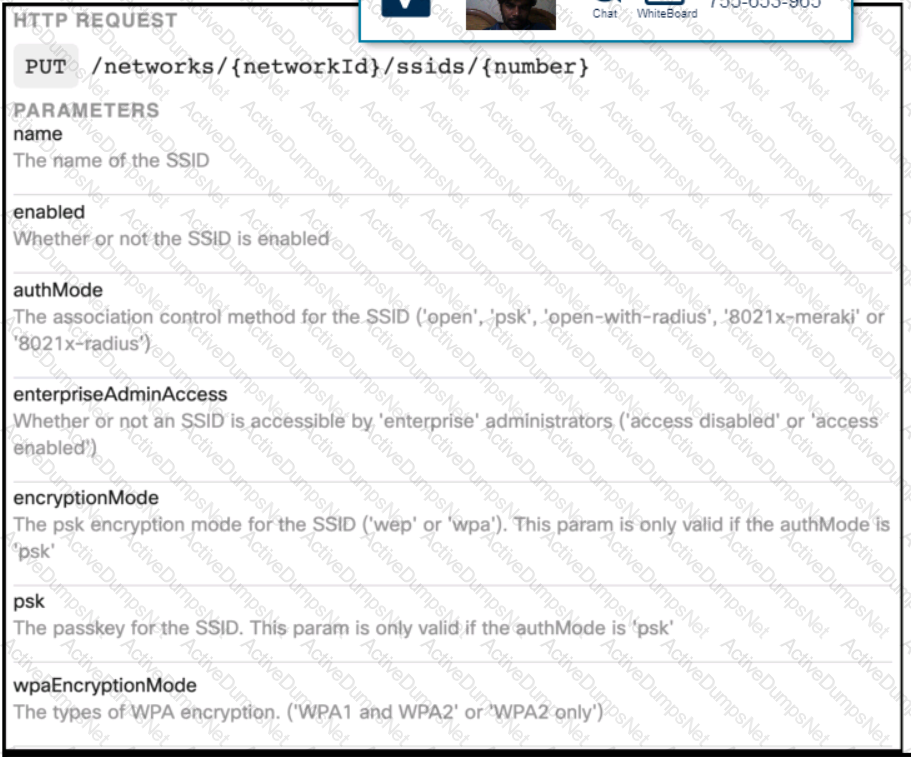
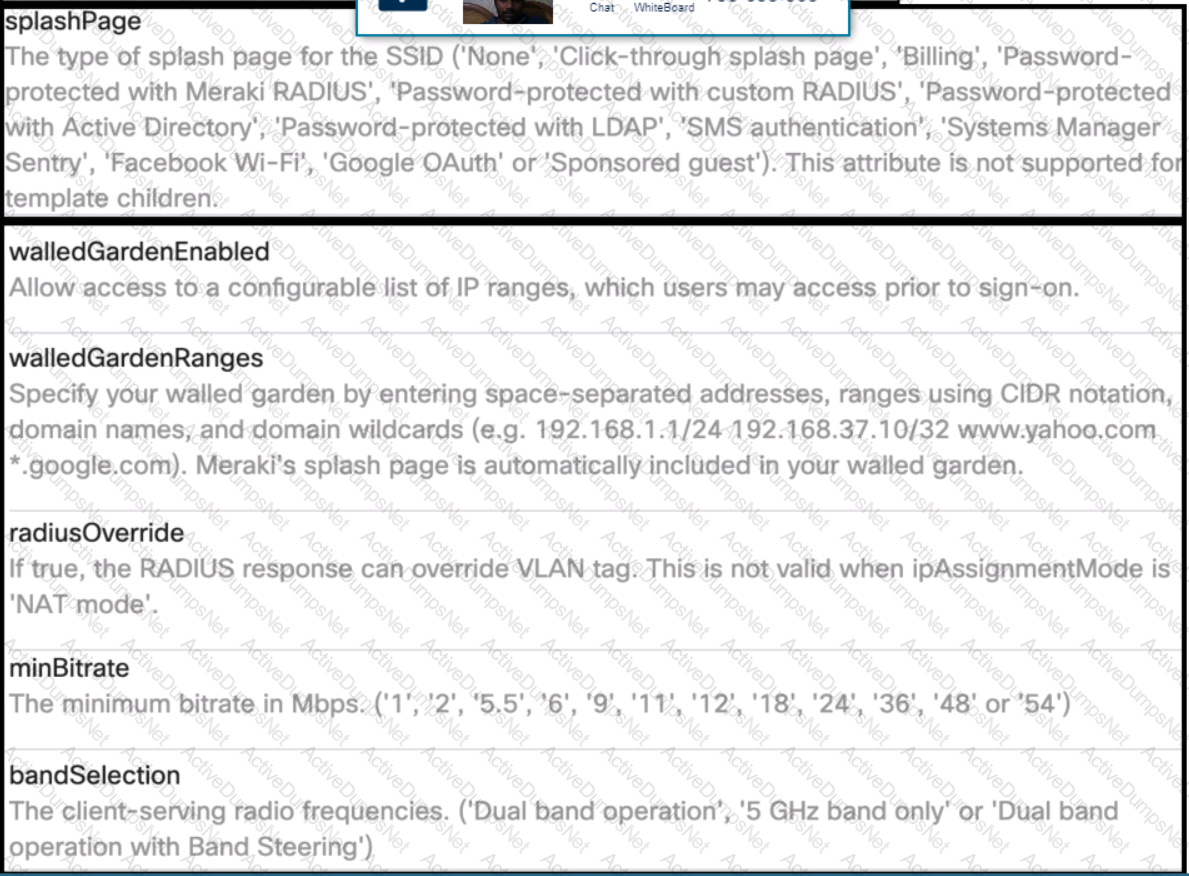
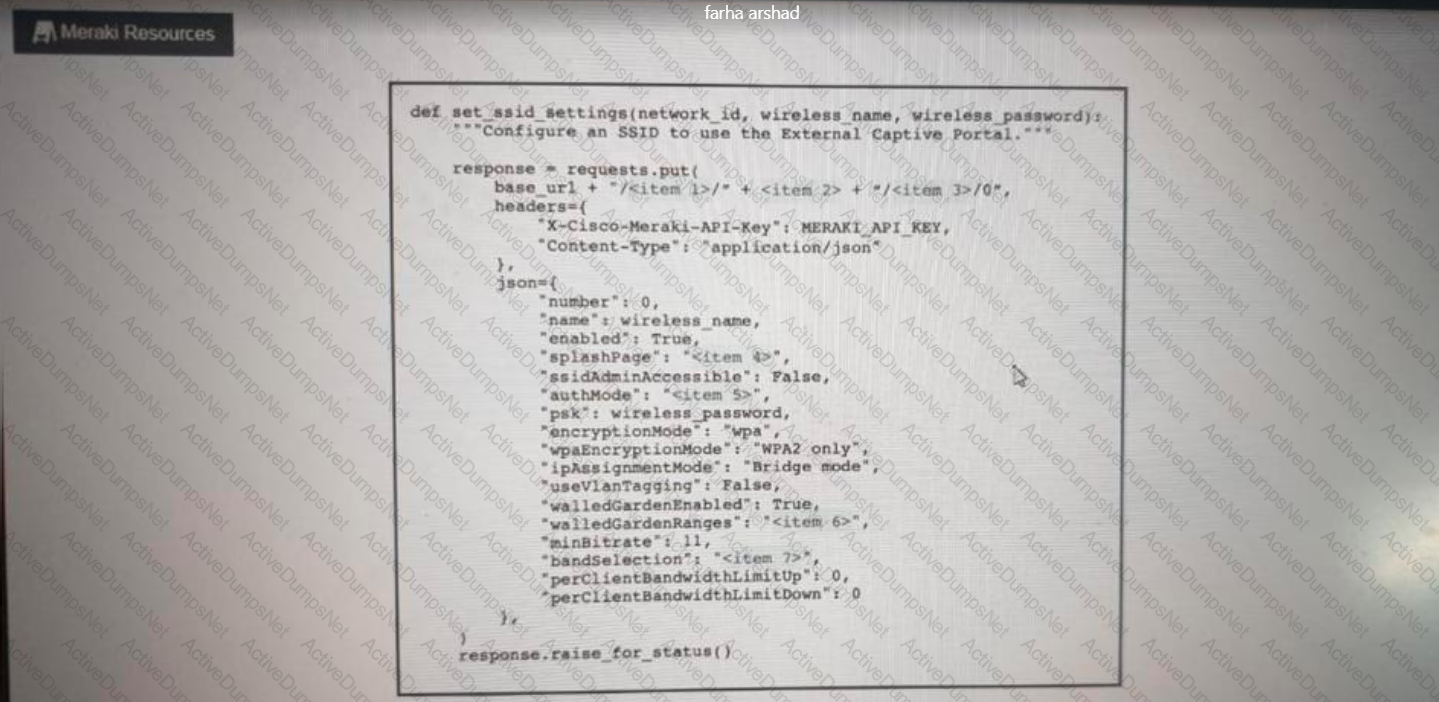
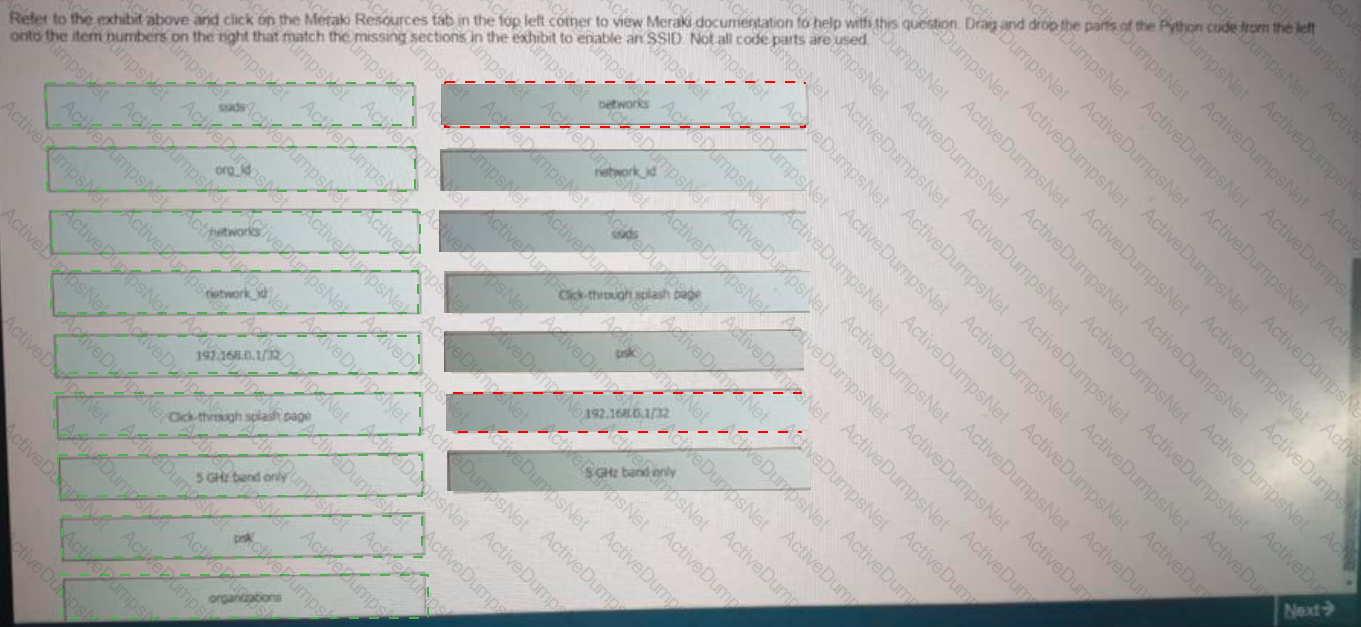
Click on the Meraki Resources tab in the left corner to view Meraki documentation to help with this question.Drag and drop the parts of the python code from the left onto the item numbers on the right that match the missing sections in the exhibit to enable an SSID. Not all code parts are used.

Refer to the exhibit.
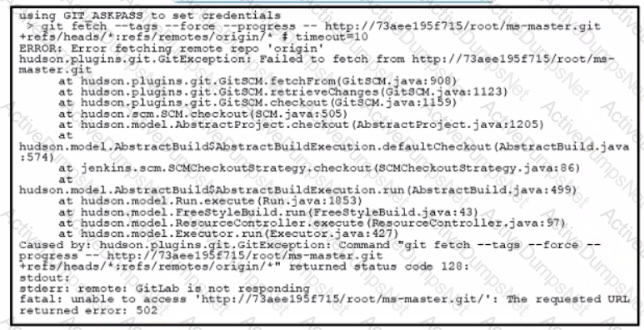
An attempt to execute a CI/CD pipeline results m the error shown What is the cause of the error?
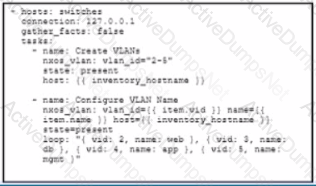
A developer must create VLANs 2-5 on a remote Cisco NX-OS switch by using an Ansible playbook The playbook must meet these requirements
• Configure the VLANs and a name for each VLAN
• Only run against the switches inventory group
• Execute from the local Ansible controller
• Prevent the collection of system information prior to execution
Which playbook must be used?
A)

B)

C)

D)
Refer to the exhibit.
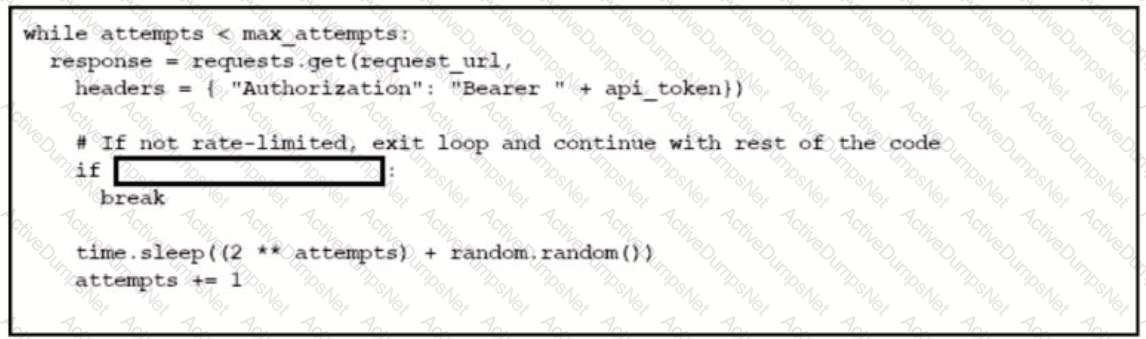
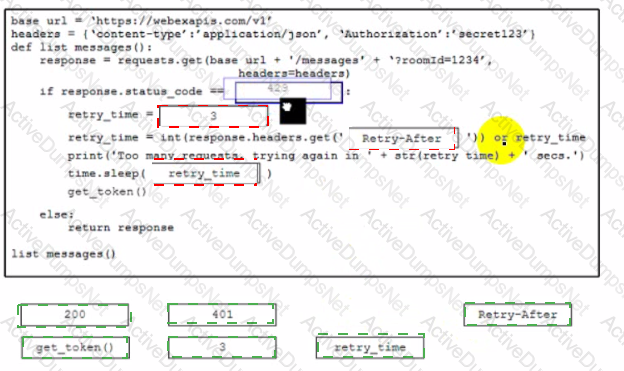
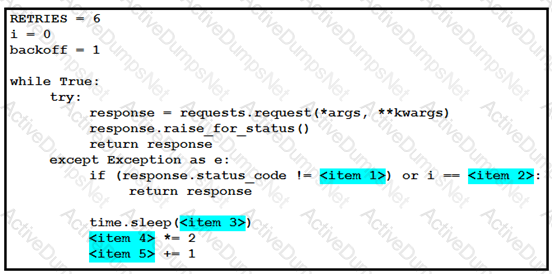
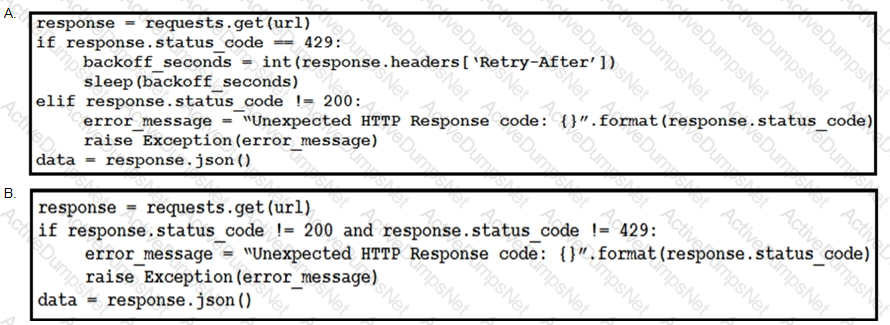
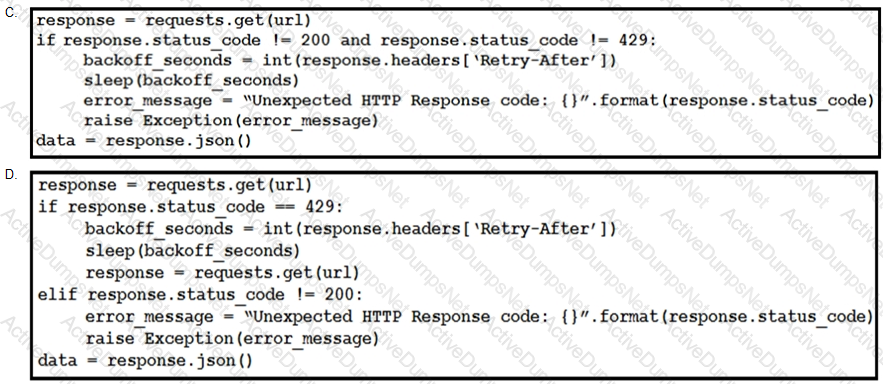
Which code snippet completes this code to handle API rate-limit?
A developer is working on a new feature in a branch named 'newfeay000222118' and the current working primary branch is named 'pnm409024967' The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must Be used?
A)

B)

C)

D)

What are two benefits of using distributed log collectors? (Choose two.)
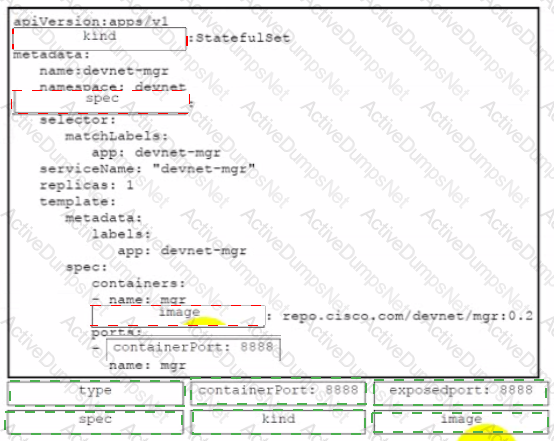
A developer must package an application for Kubernetes to integrate into a prebuilt CD environment. The application utilizes a Docker image from Cisco DevNet public repository and is accessible from a specific port of the container. Drag and drop the code from the bottom onto the box where the code is missing in the Kubernetes YAML configuration file. Not all options are used.

A new record-keeping application for employees to track customer orders must be deployed to a company's existing infrastructure. The host servers reside in a data center in a different country to where the majority of users work. The new network configuration for the database server is: •IP: 10.8.32.10
• Subnet Mask: 255.255.255.0
• Hostname: CustOrd423320458-Prod-010
• MAC: 18-46-AC-6F-F4-52.
The performance of the client-side application is a priority due to the high demand placed on it by employees. Which area should the team consider in terms of impact to application performance due to the planned deployment?
Which Git command enables the developer to revert back to f414f31 commit to discard changes in the current working tree?
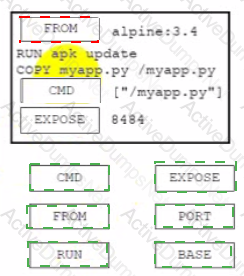
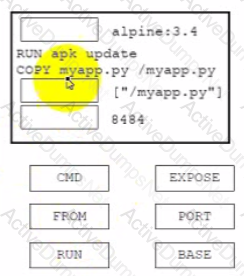
Drag and drop the code from the bottom onto the box where the code is missing on the Dockerfile to containerize an application that listens on the specified TCP network port at runtime. Not all options are used.
Drag and drop the code snippets from the bottom onto the boxes where the code is missing to complete the API call to implement error handling Not all options are used.
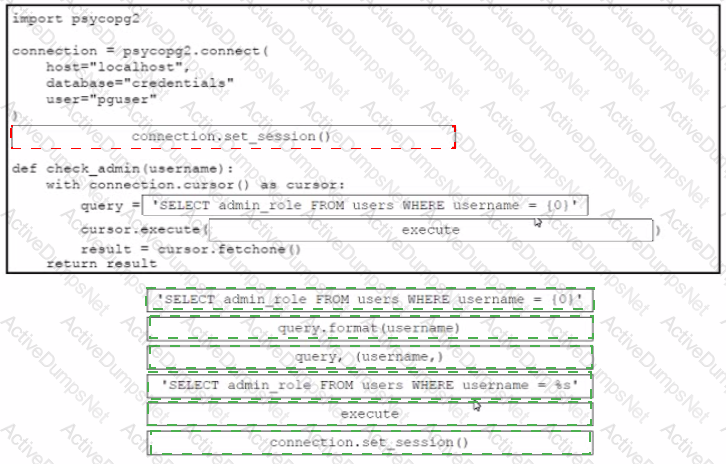
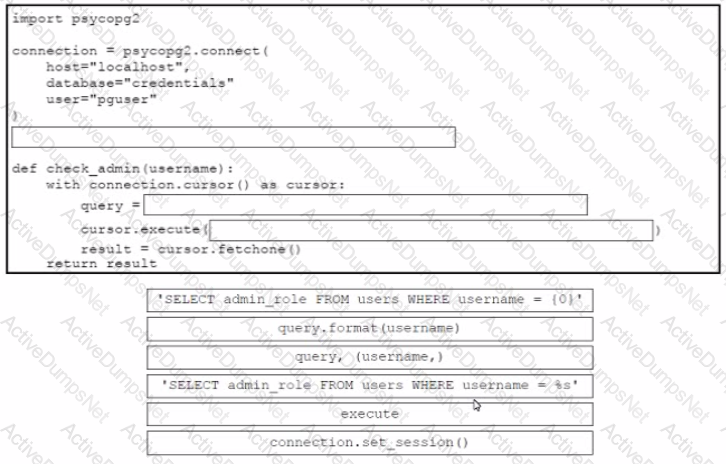
Drag and drop the code from the bottom onto the box where the code is missing in the Python code to query for user permissions while mitigating against SQL Injection Not all options are used.
Refer to the exhibit.
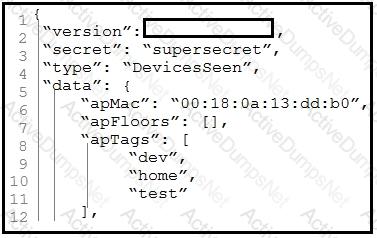
Which parameter is missing from the JSON response to confirm the API version that is
used?
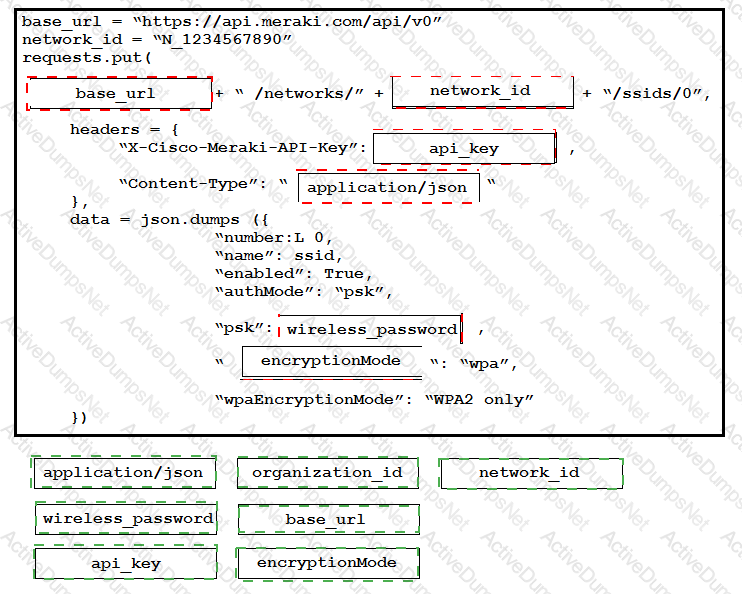
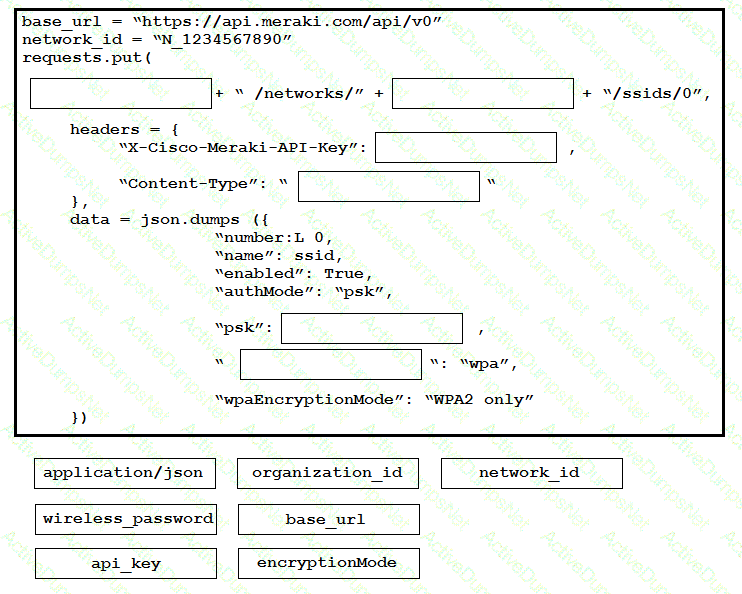
Drag and drop the code onto the snippet to update a SSID in Meraki using the Dashboard API. Not all options are used.
Refer to the exhibit.
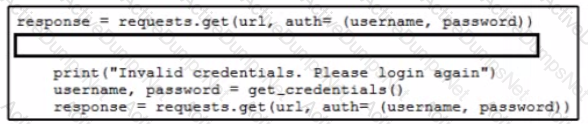
Which code snippet must be added to the blank in the code to automate the evaluation and handling of errors due to wrong credentials when Basic Authorization is used?
A)

B)

C)

D)

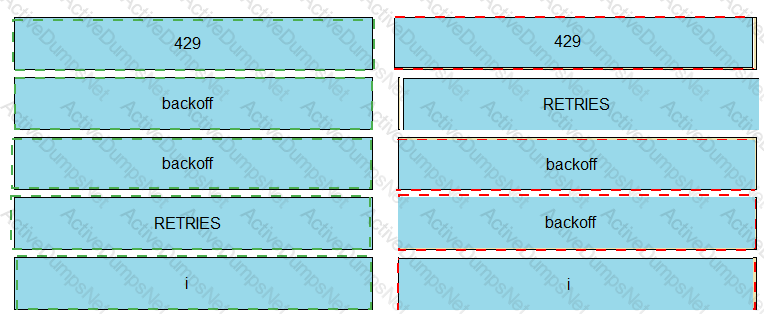
Refer to the exhibit. The self-service Webex Teams bot is failing when many users attempt to interact with it at the same time. Drag and drop the code snippets from the left onto the correct item numbers on the right that match the missing sections in the exhibit to complete this code to handle this high-load situation.
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances.
Which two actions can improve the design of the application to identify the faults? (Choose two.)
When end-to-end encryption is implemented, which area is most vulnerable to exploitation?
What is a benefit of using model-driven telemetry?
Refer to the exhibit.

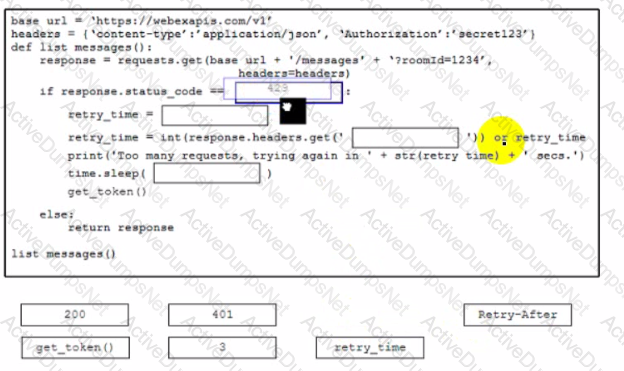
This snippet of a script has recently started exiting abnormally with an exception stating “Unexpected HTTP Response code: 429”.
Which solution handles rate limiting by the remote API?
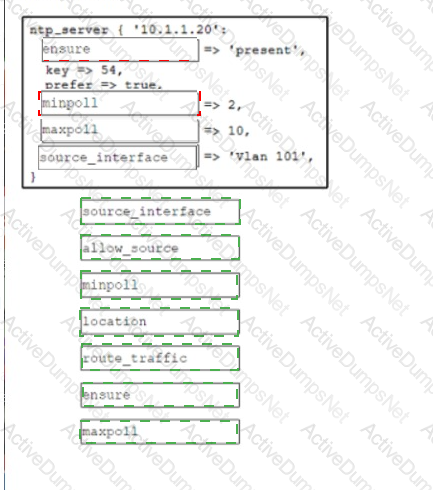
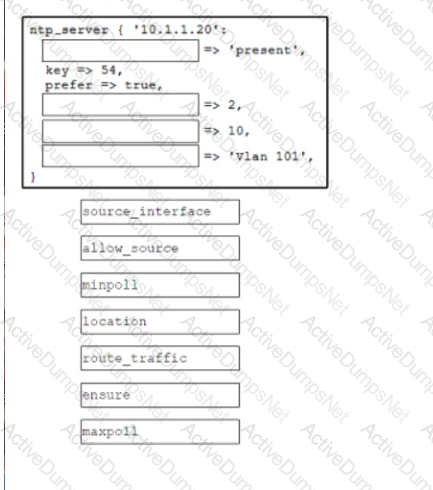
Drag and drop the code from the bottom onto the box where the code is missing to create a Puppet manifest that implements an NTP configuration when applied to a device in the master inventory. Not all options are used.
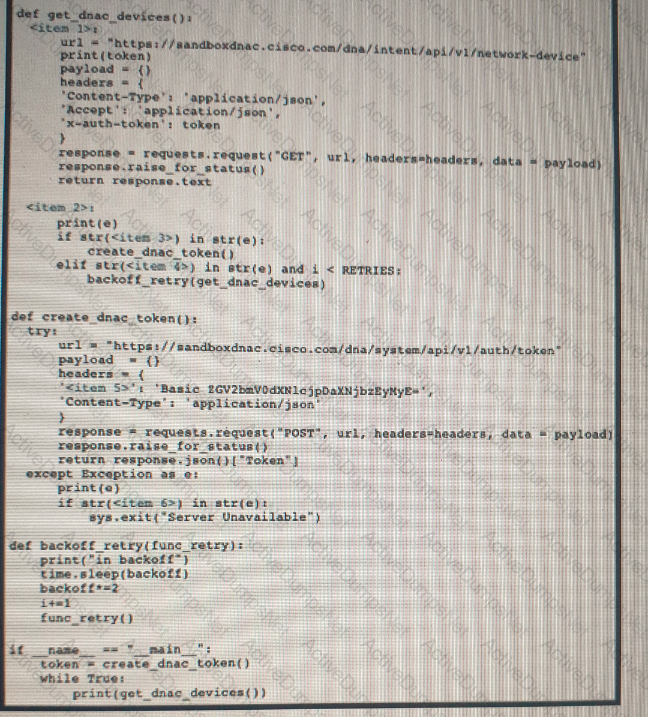
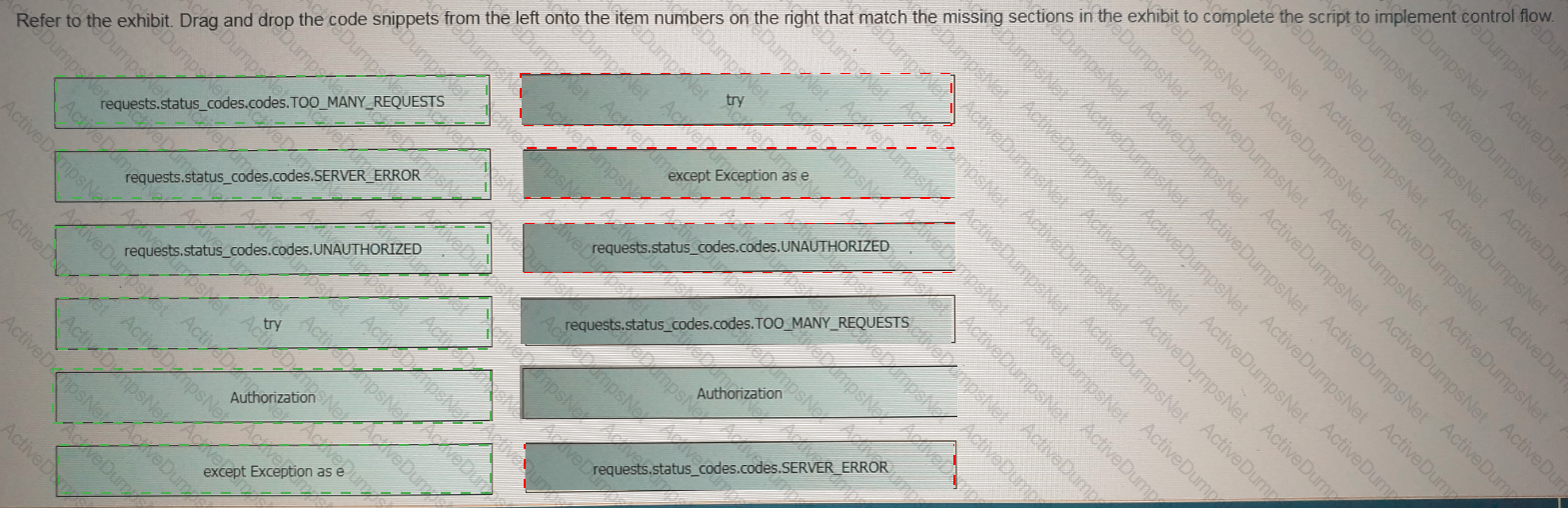
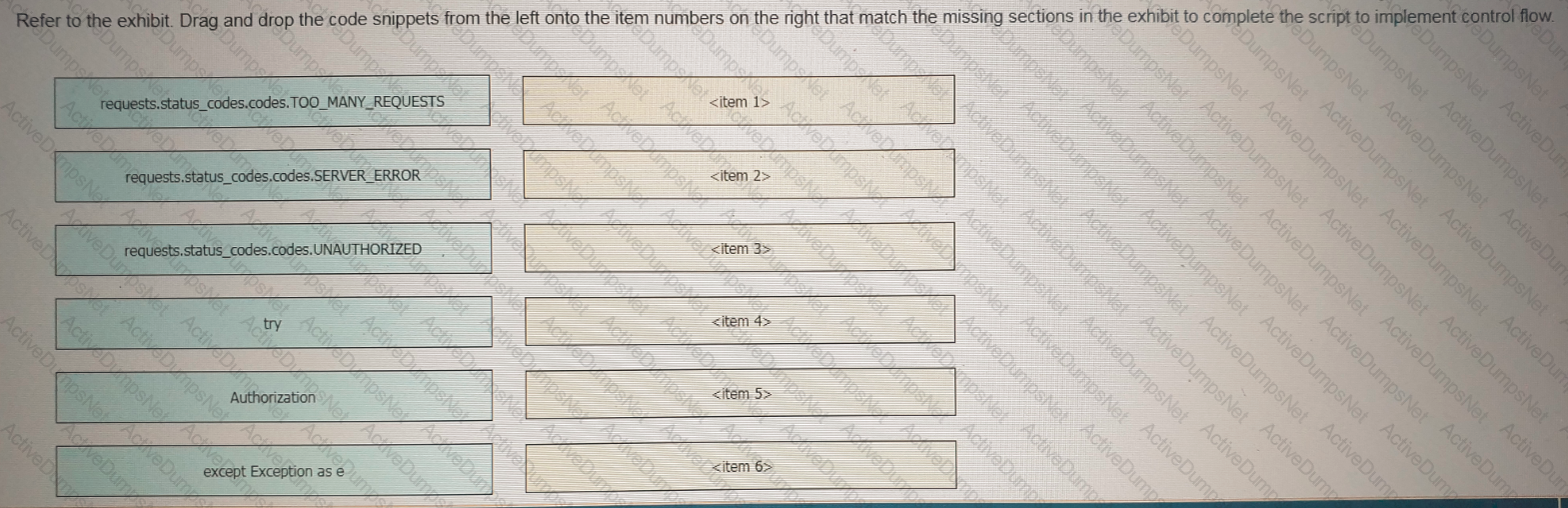
Refer to the exhibit Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
An application must be able to print the values of the variables in specific modules. Different message levels will be used for production and for development. Proof of access and activity must be documented. What must be included in the implementation to support these observability requirements?
A developer deploys a SQLite database in a Docker container. Single-use secret keys are generated each time
a user accesses the database. The keys expire after 24 hours. Where should the keys be stored?

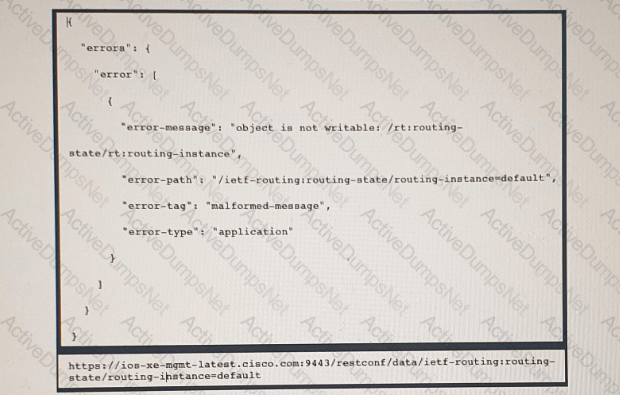
Refer to the exhibit above and click on the IETF Routing tab in the top left corner to help with this question. A developer is trying to update the routing instance by adding a new route to the routes list using the URL in the exhibit. What action must be taken to fix the error being received?
Refer to the exhibit.

A developer must review an intern's code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running-config to the server. When considering maintainability, which two changes must be made to the code? (Choose two.)
A timeframe custom dashboard must be developed to present data collected from Cisco Meraki. The dashboard must include a wireless health alert count. What needs to be built as a prerequisite?
A developer has issued git add file1 and file2 test.py command to add the three files for the next commit, but then decides to executed test.py from this command. Which command needs to be used to exclude test.py from this commit but keep the rest of the files?
A developer is working on an enhancement for an application feature and has made changes to a branch called ‘devcor-432436127a-enhance4‘. When merging the branch to production, conflicts occurred. Which Git command must the developer use to recreate the pre-merge state?
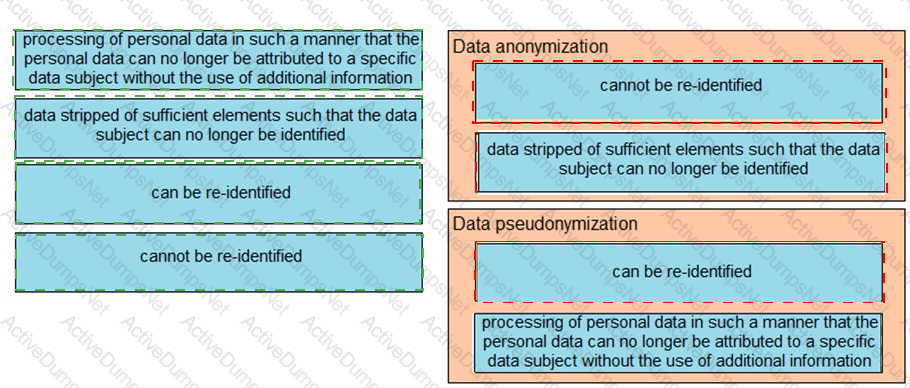
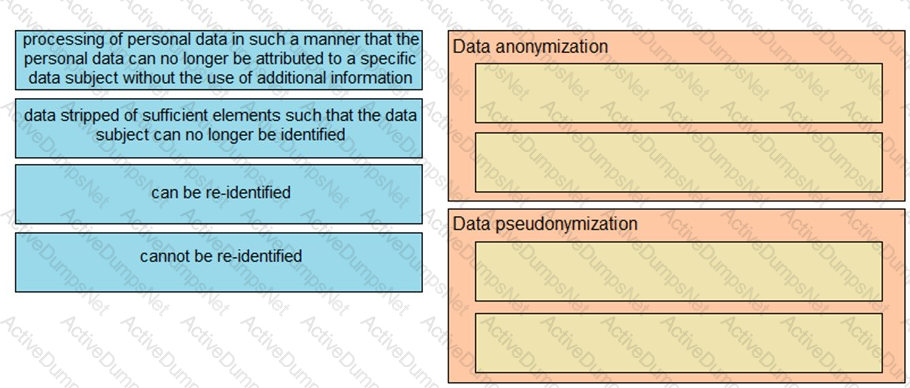
Drag and drop the characteristics from the left onto the correct data processing techniques on the right, in the context of GDPR.
The UCS Python SDK includes modules for Service Profile template creation. Which two UCS Service Profile template types are supported? (Choose two.)
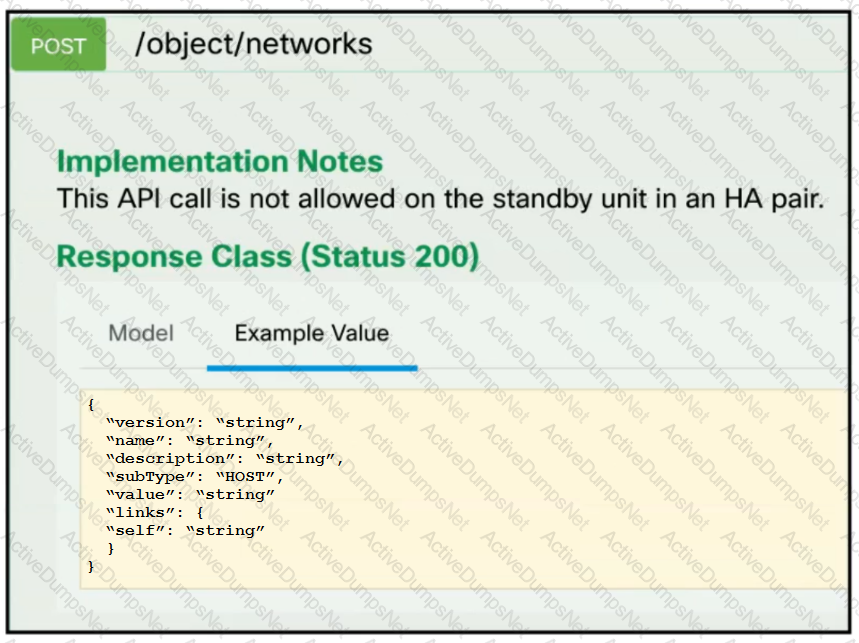
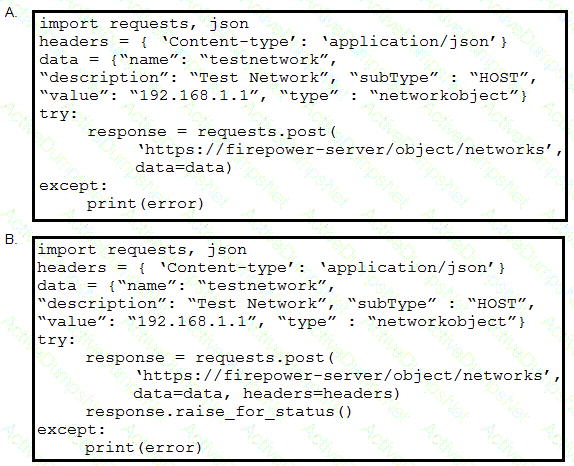
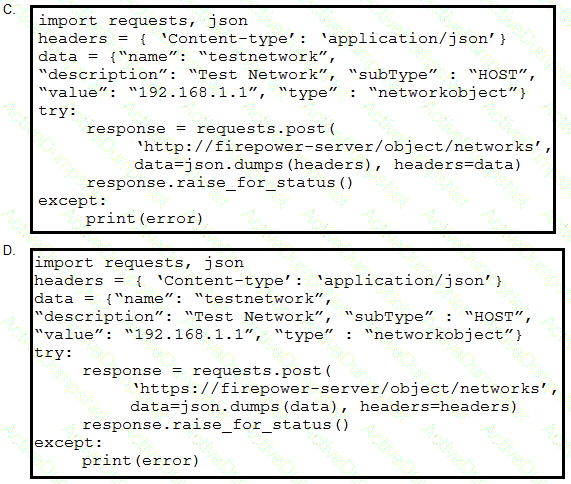
Refer to the exhibit. A developer must create a new network object named testnetwork by using the Cisco Firepower Device Management API. The script must also handle any exceptions that occur during the request and print out any resulting errors. Which script must be used?
Refer to the exhibit.
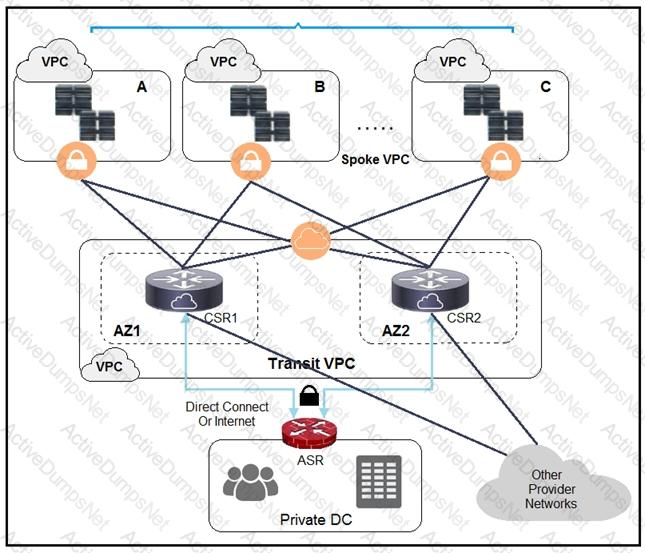
A company has extended networking from the data center to the cloud through Transit VPC.
Which two statements describe the benefits of this approach? (Choose two.)
A team is developing a cloud-native application for network monitoring and management of various devices. An increased growth rate of users is expected. The solution must be easily managed and meet these requirements:
•able to use dependencies
•easy disposability
•flexible configuration
Which application design approach must be used?
Which security approach should be used for developing a REST API?
Refer to the exhibit.
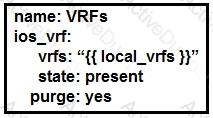
The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?
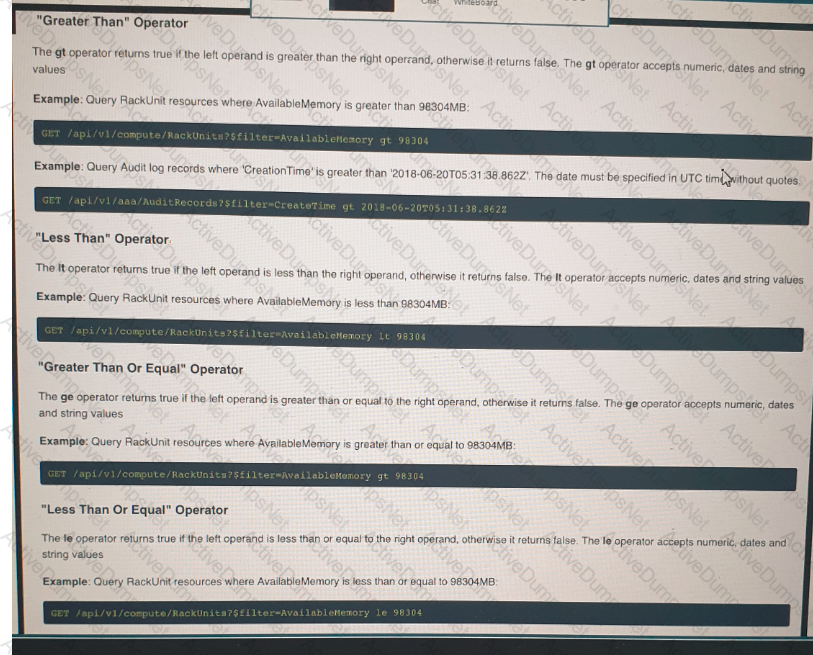
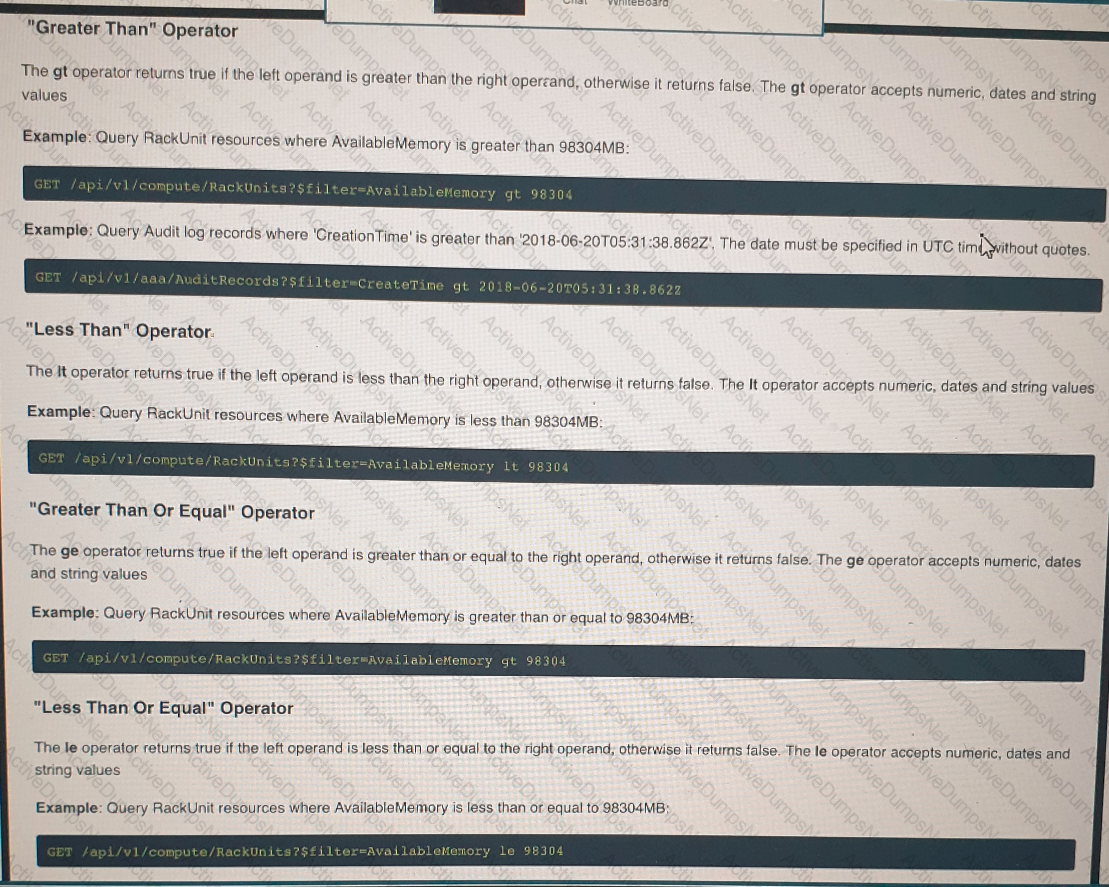
Click on the GET Resource button above to view resources that will help with this question. An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
Refer to the exhibit.
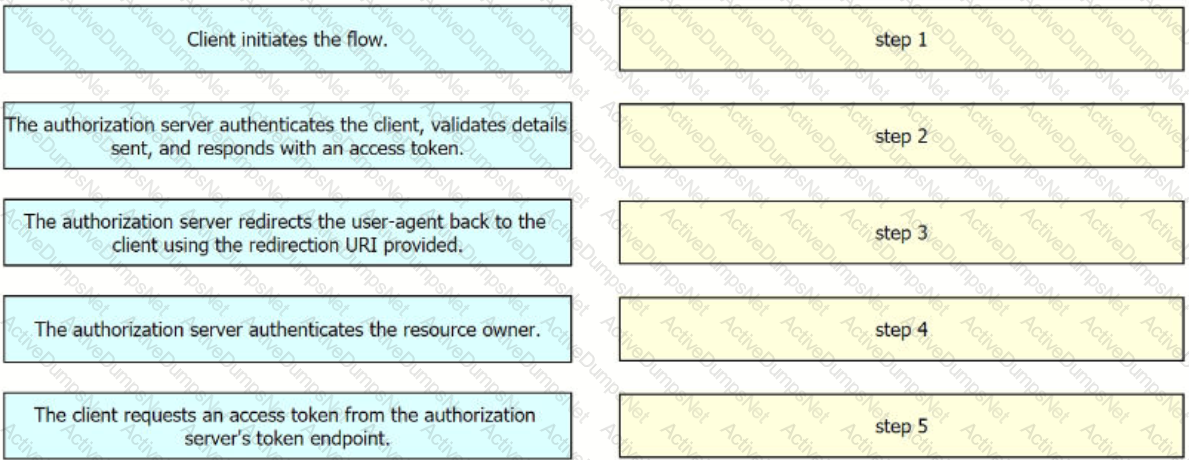
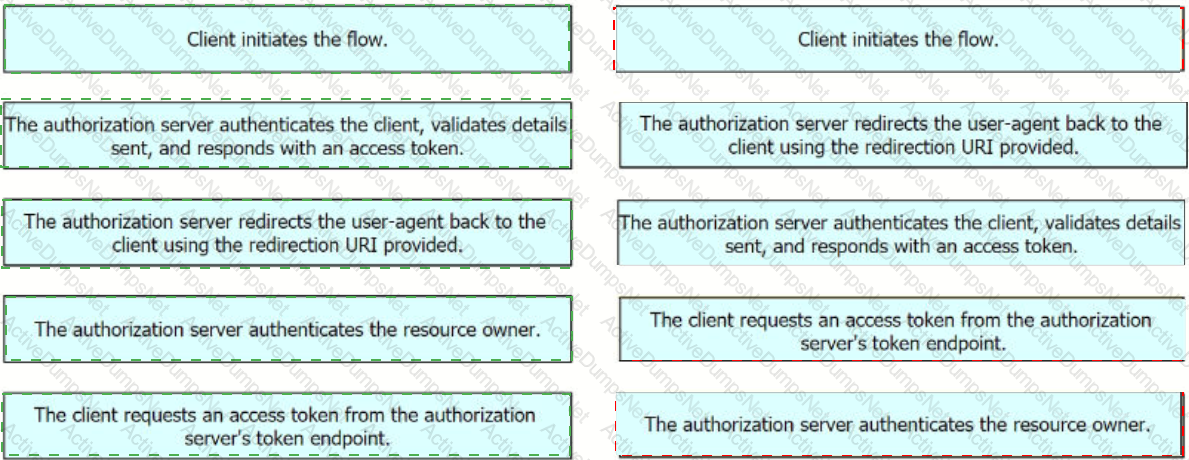
Drag and drop the steps from the left into the order of operation on the right for a successful OAuth2 three-legged authorization code grant flow,
Refer to the exhibit.
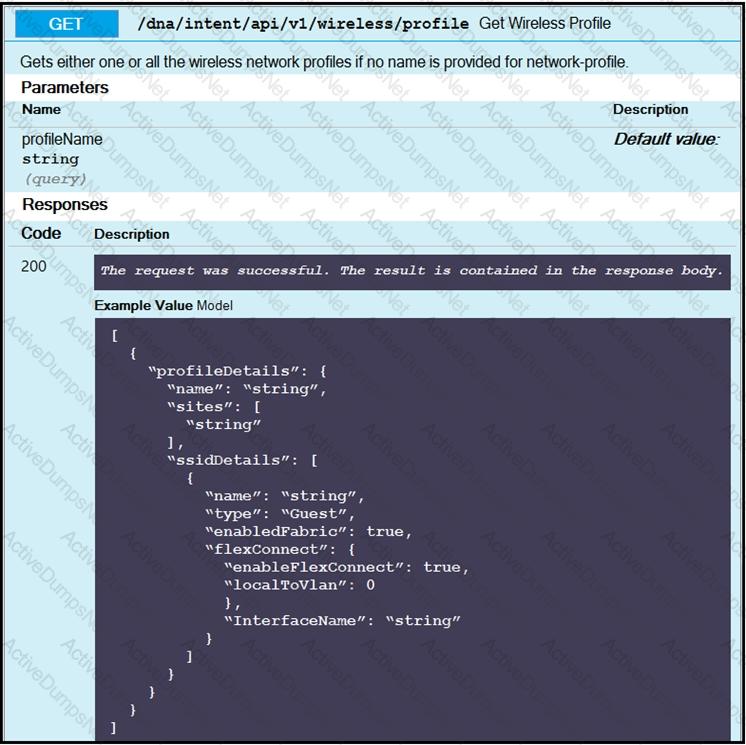
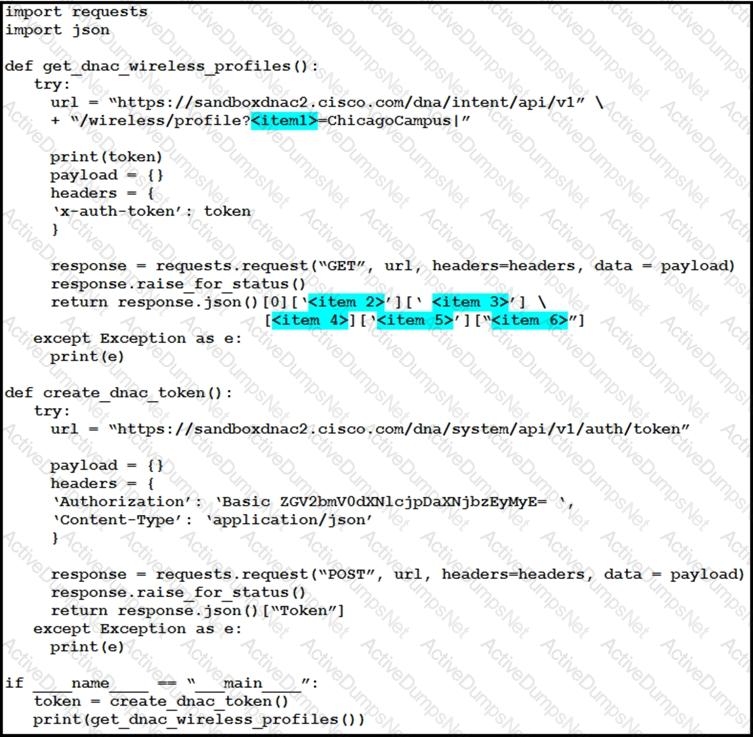
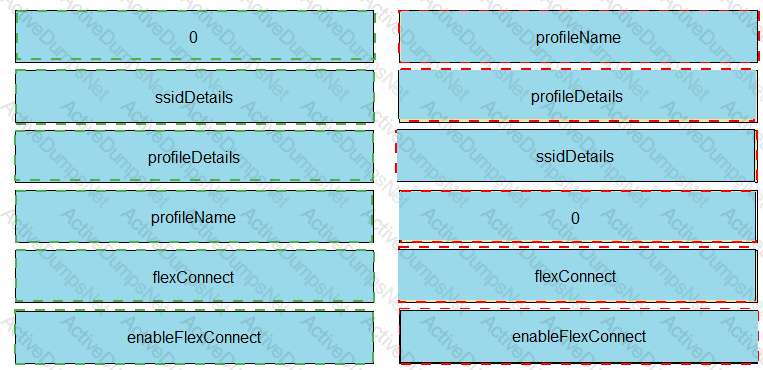
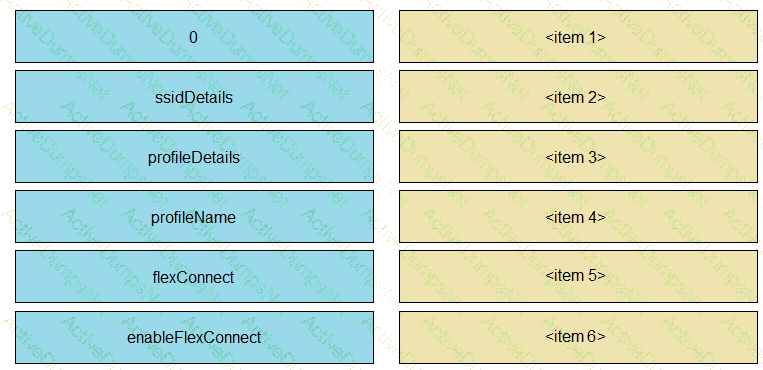
The Python script is supposed to make an API call to Cisco DNA Center querying a wireless profile for the “ChicagoCampus” and then parsing out its enable FlexConnect value. Drag and drop the parts of the Python code from the left onto the item numbers on the right that match the missing sections in the exhibit.
The Meraki API URL https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been stored in the environment variable meraki_url and the API key has been stored in meraki_api_key. Which snippet presents the API call to configure, secure and enable an SSID using the Meraki API?
A)
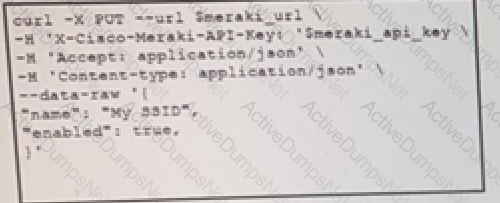
B)
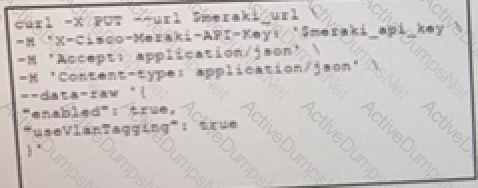
C)

D)
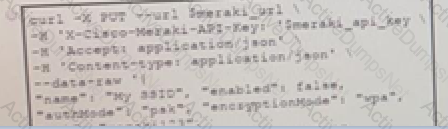
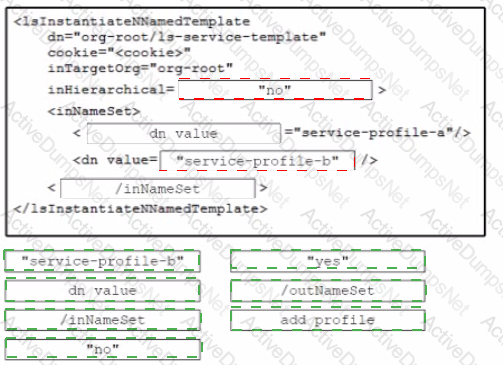
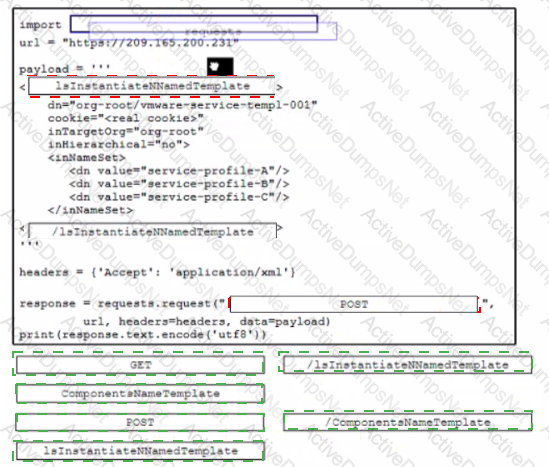
Drag and drop the code from the bottom onto the box where the code is missing to construct a UCS XML API request to generate two service profiles from the template org-root/is-service-template. Not at options are used

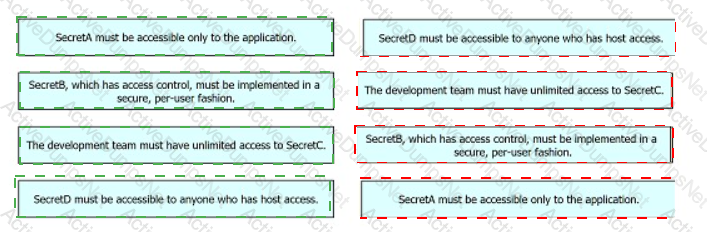
A developer is designing an application that uses confidential information for a company and its clients. The developer must implement different secret storage techniques for each handled secret to enforce security policy compliance within a project. Drag and drop the security policy requirements from the left onto the storage solutions on the right
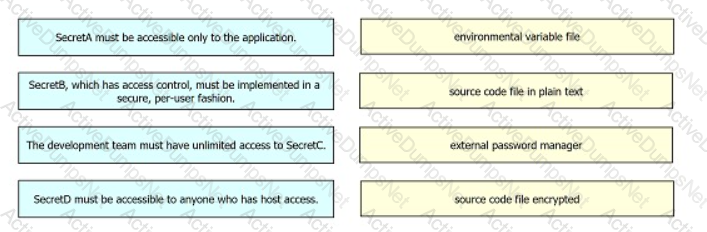
A heterogeneous network of vendors and device types needs automating for better efficiency and to enable future automated testing. The network consists of switches, routers, firewalls and load balancers from different vendors, however they all support the NETCONF/RESTCONF configuration standards and the YAML models with every feature the business requires. The business is looking for a buy versus build solution because they
cannot dedicate engineering resources, and they need configuration diff and rollback functionality from day 1.
Which configuration management for automation tooling is needed for this solution?
Drag and drop the code snippets from the bottom onto the boxes where the code is missing to deploy three Cisco UCS servers each from a different template Not all options ate used.
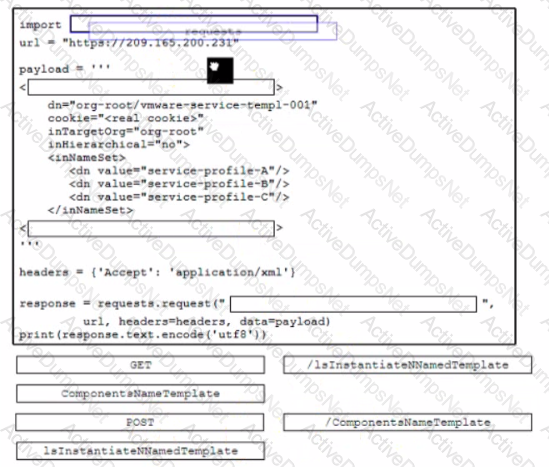
A developer releases a new application for network automation of Cisco devices deployed m a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability-driven development lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
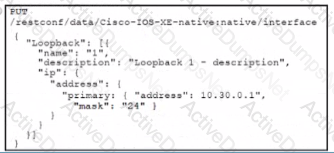
Refer to the exhibit.
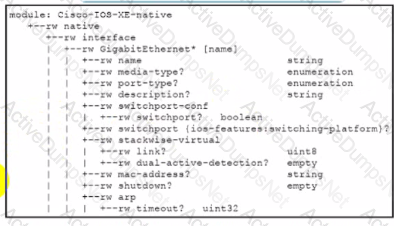
Interface Lookback 1 must be created with IP address 10.30.0.1/24 in a Cisco IOS XE device using RESTCONF. The schema that is defined by the exhibit must be used. Which body and URI should be used for this operation?
A)
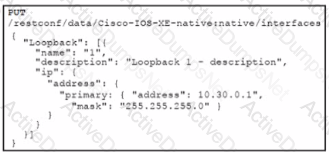
B)
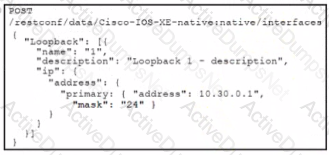
C)

D)
Click on the GET Resource button above to view resources that will help with this question.
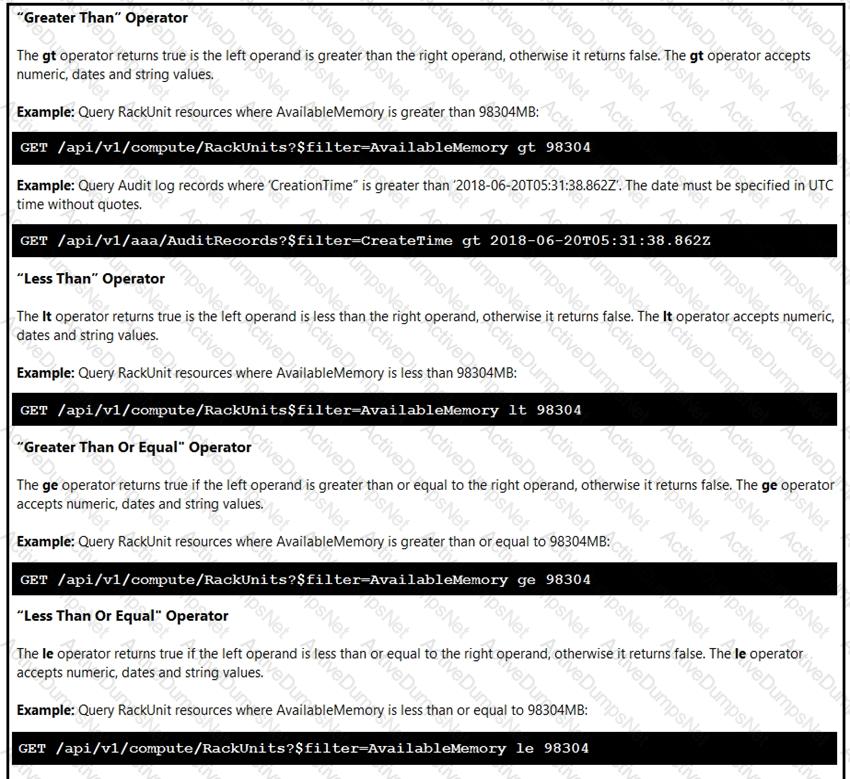
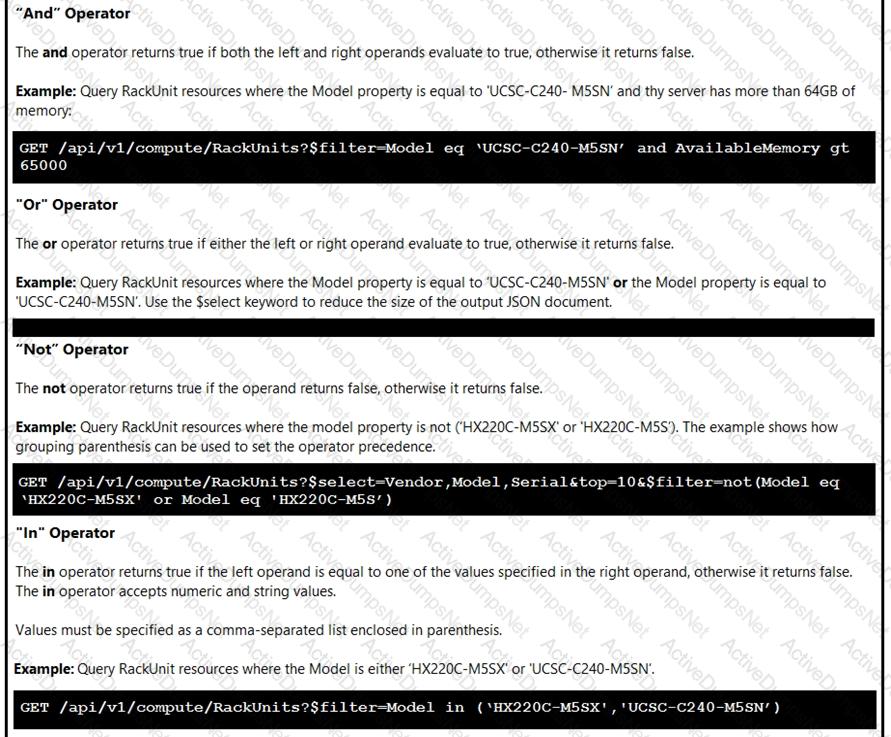
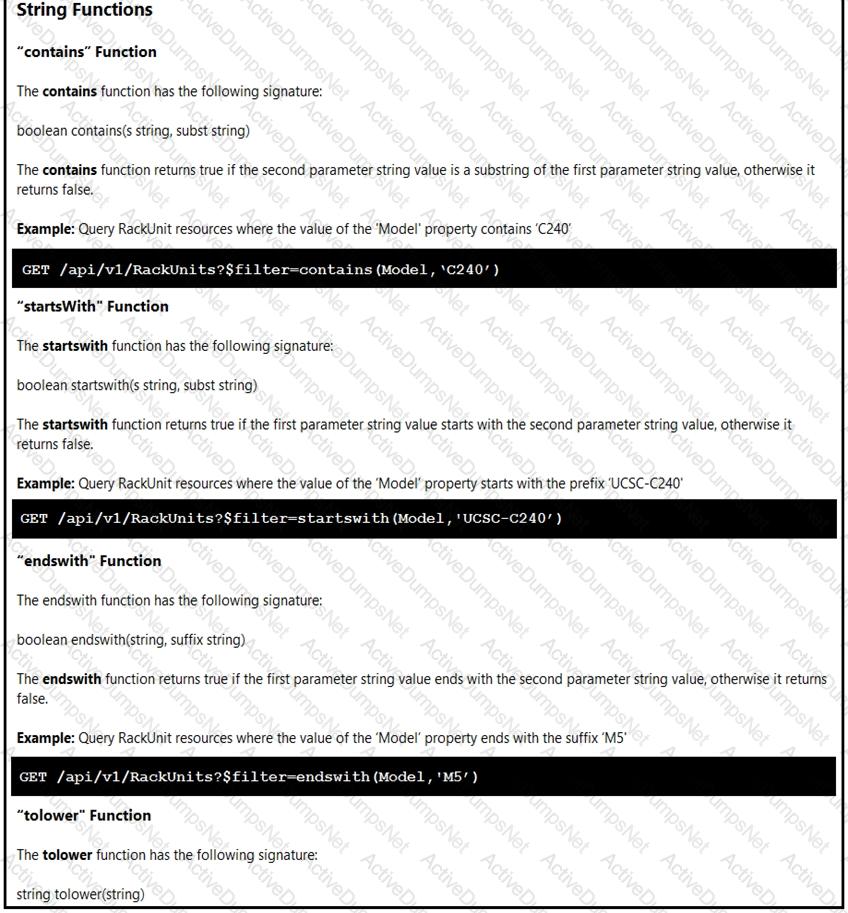
An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB.
Which REST API call accomplishes this task?
Refer to the exhibit Pipenv is used to manage dependencies The test funs successfully on a local environment. What is the reason for the error when running the test on a CI'CD pipeline?
Refer to the exhibit.
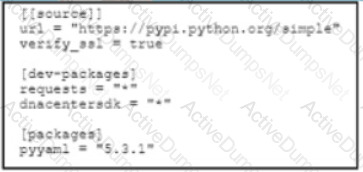
Which type of python dependency file is shown?
A developer is working on a bug fix. The existing branch named ‘bugfix05328’ needs to be merged with the current working primary branch named ‘prim404880077’. All changes must be integrated into a single commit instead of preserving them as individual commits. Which git command must be used?
Refer to the exhibit.
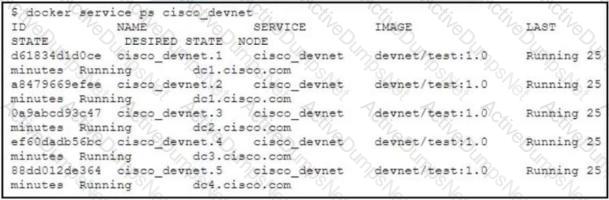
The cisco_devnet Docker swarm service runs across five replicas.The development team tags and imports a new image named devnet/ test:1.1 and requests that the image be upgraded on each container.There must be no service outages during the upgrade process. Which two design approaches must be used? (Choose two.)