Cisco 350-401 Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) Exam Practice Test
Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) Questions and Answers
OR
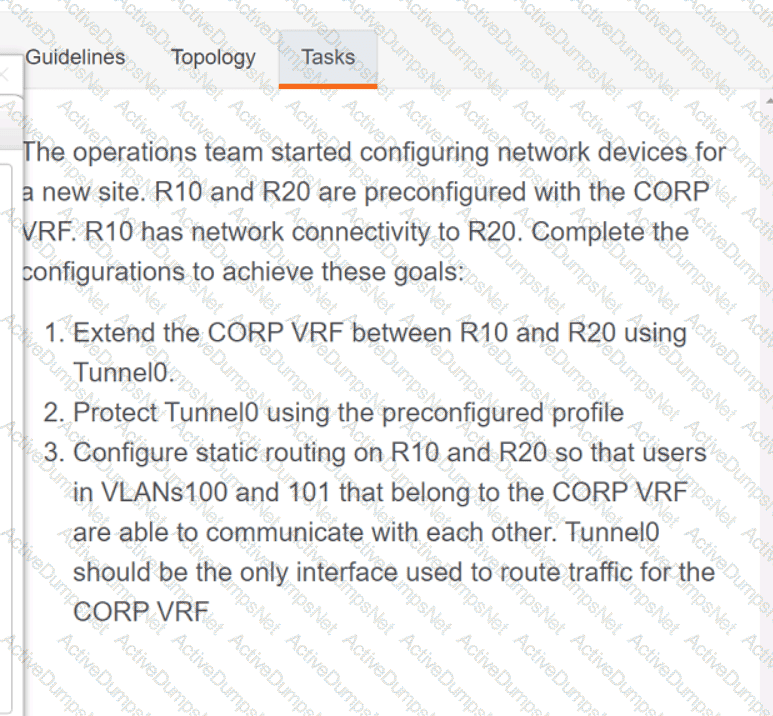
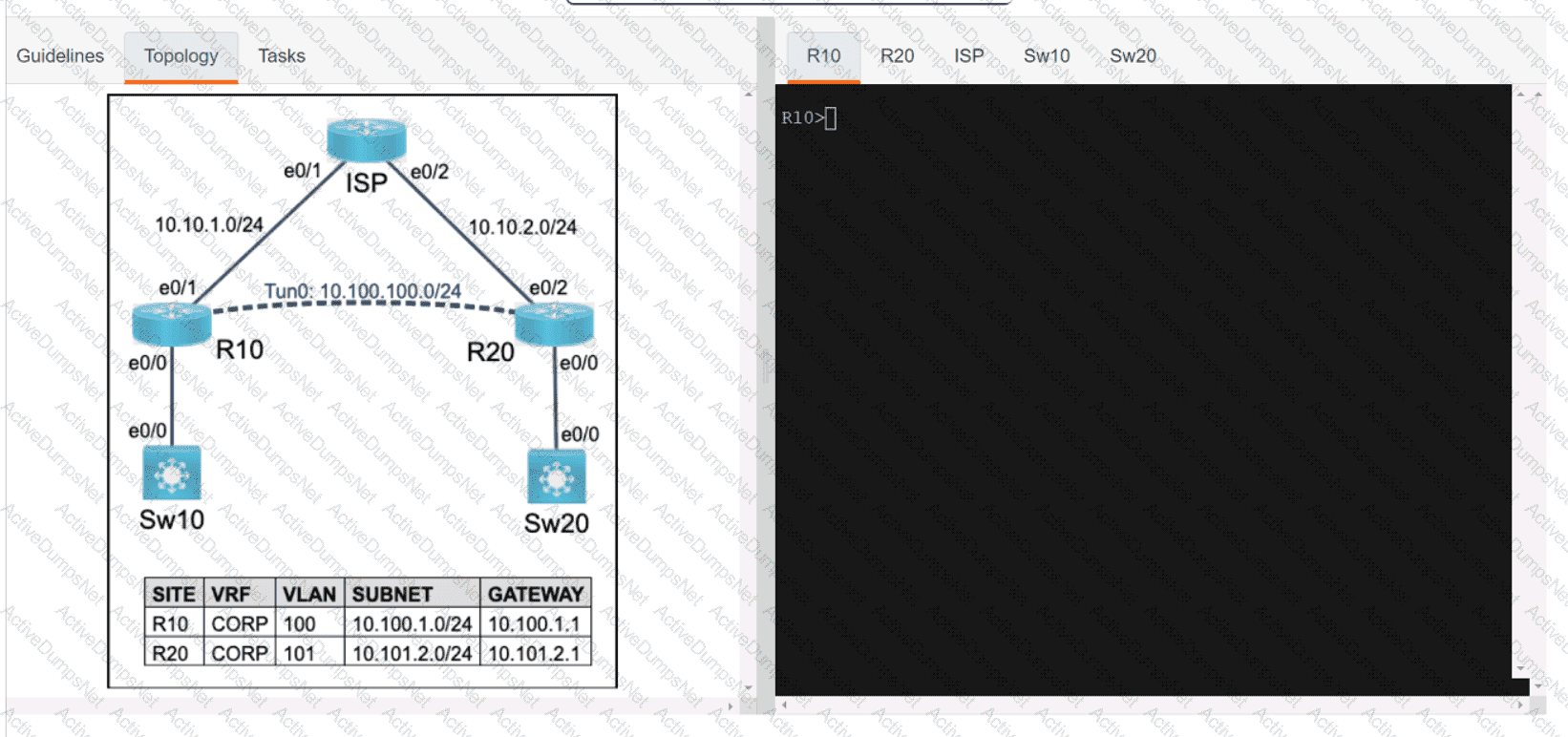
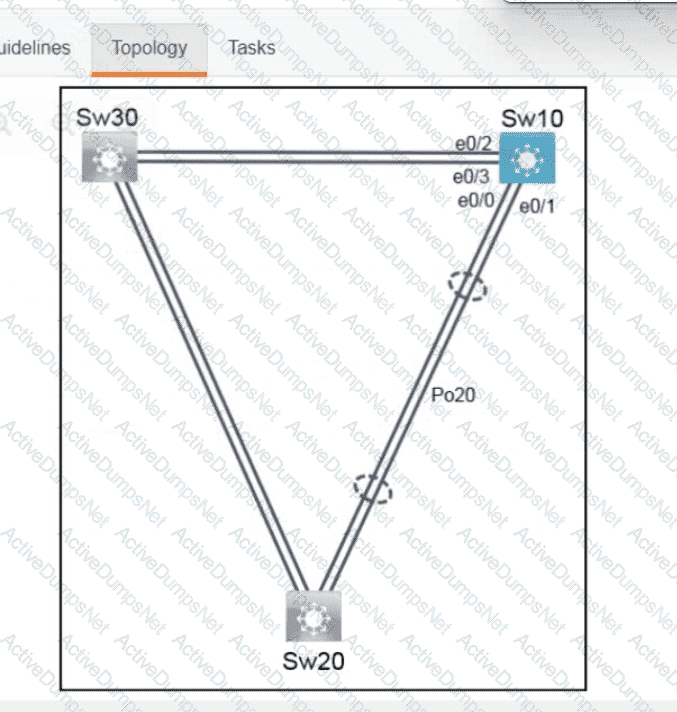

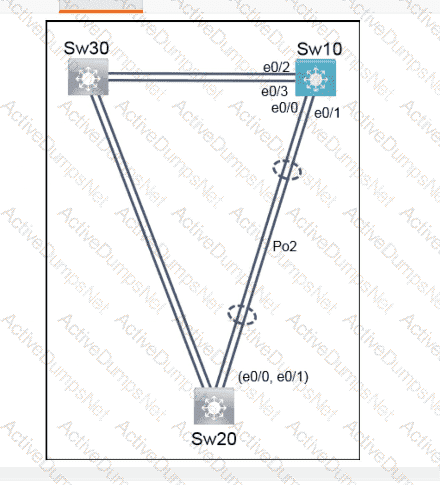

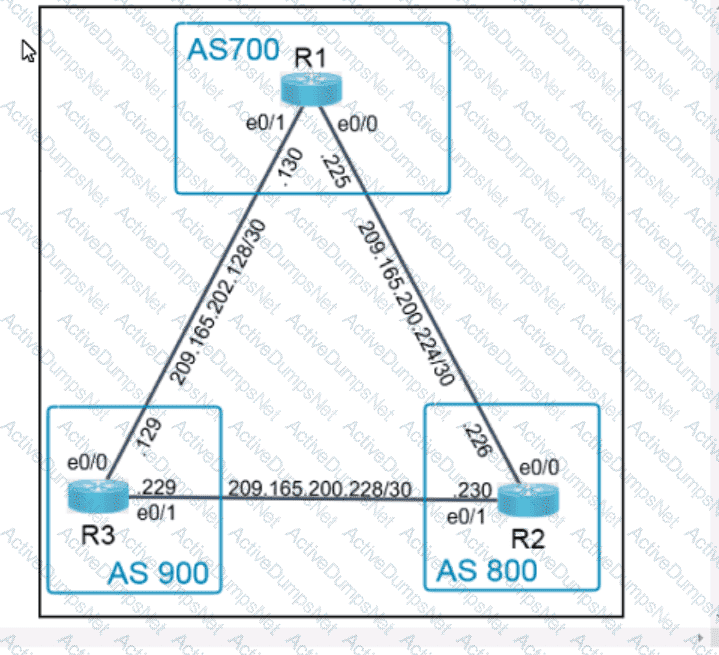
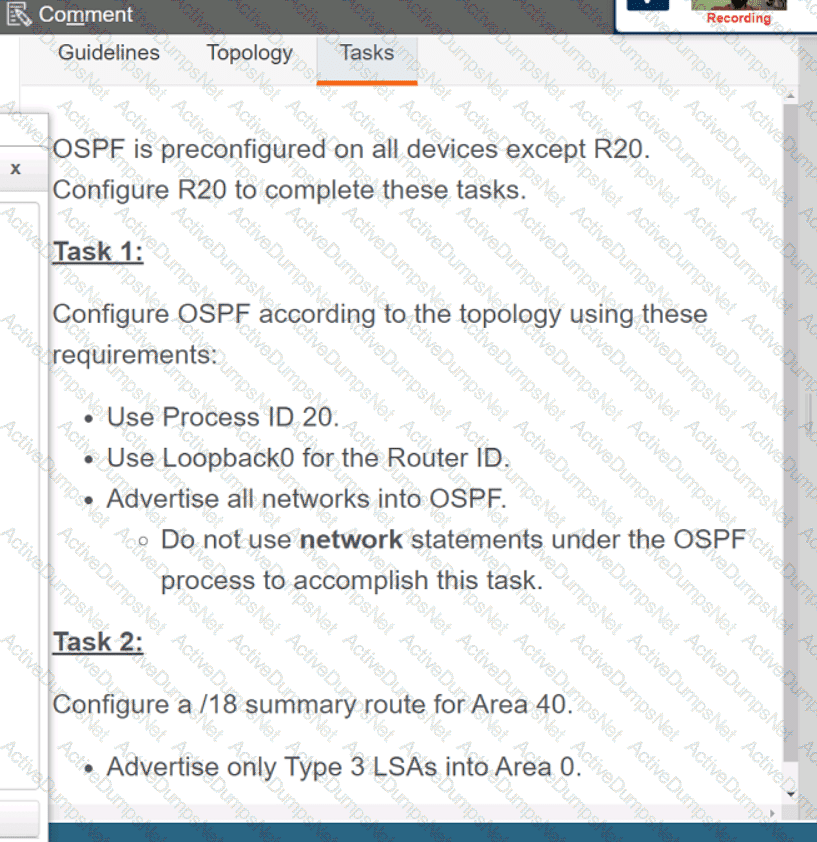
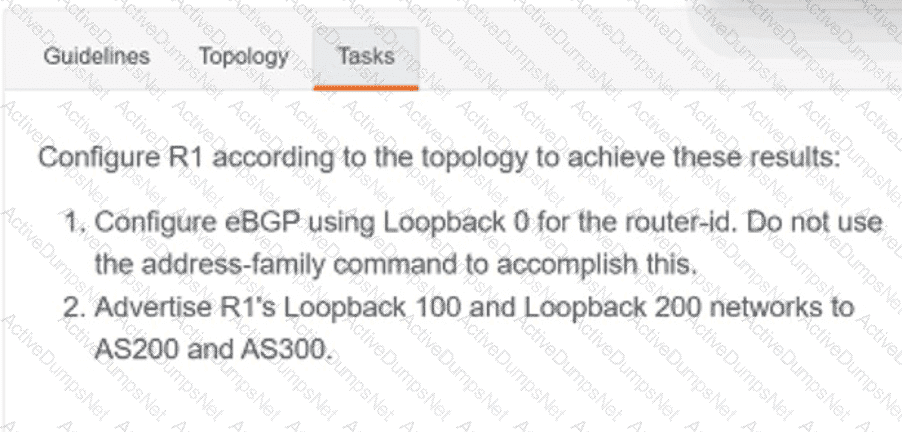
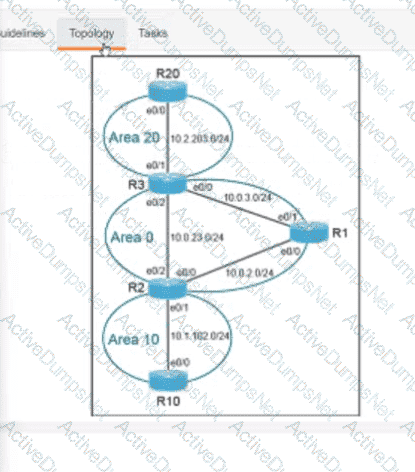

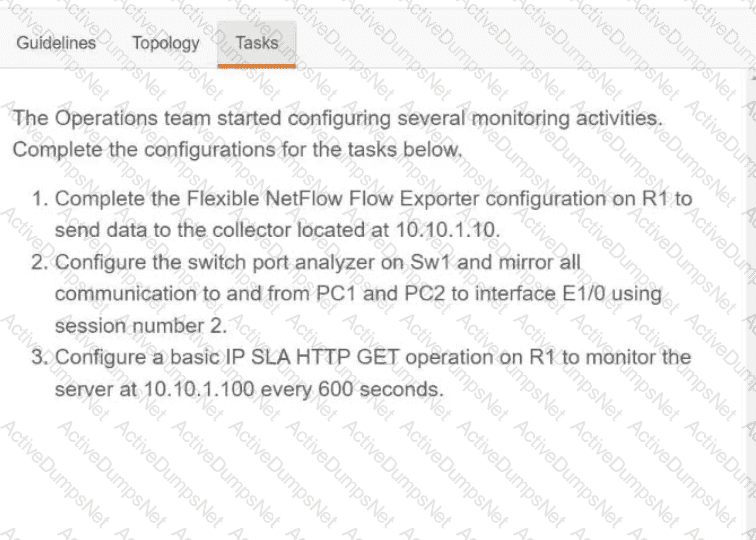
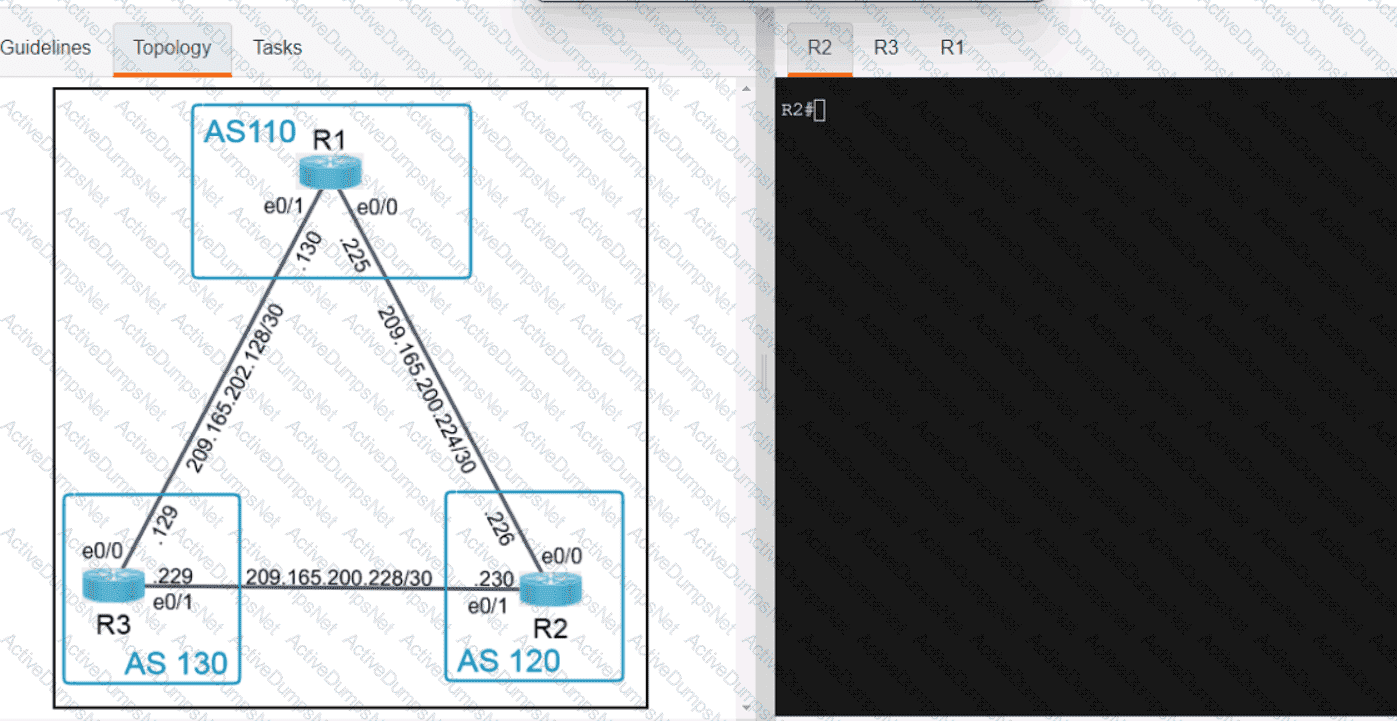


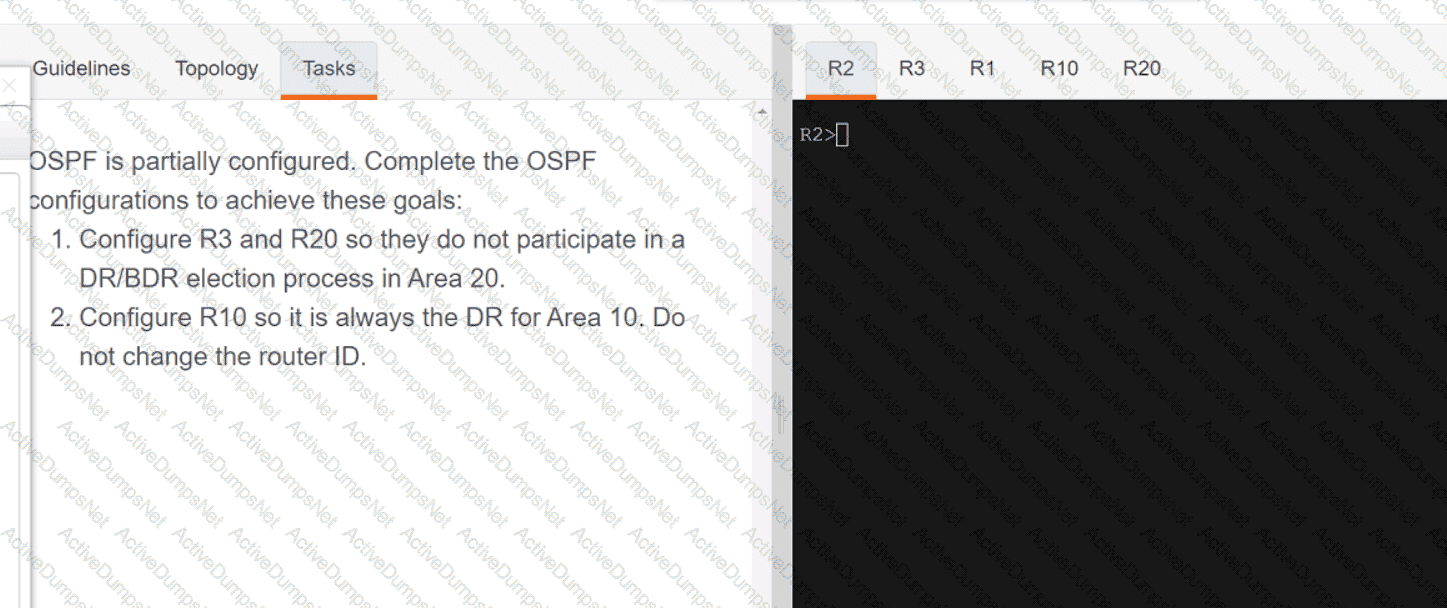
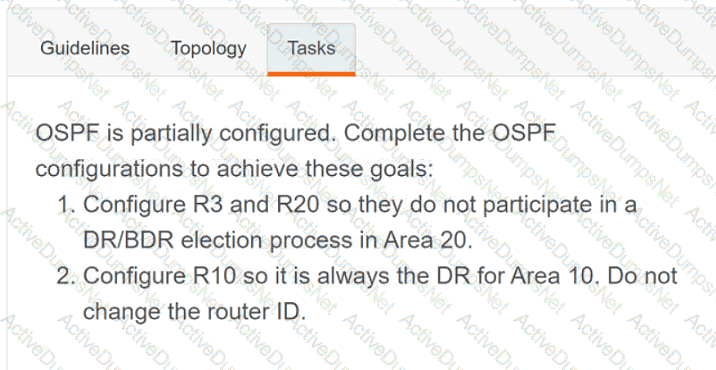
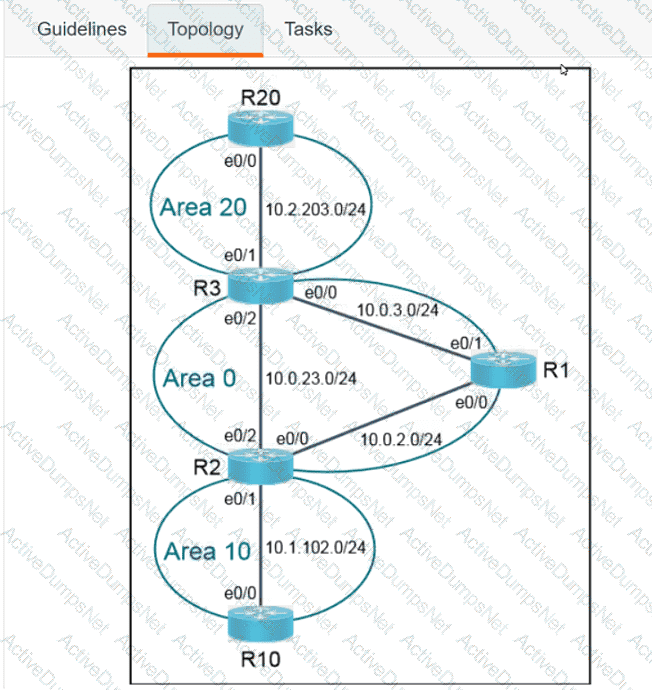
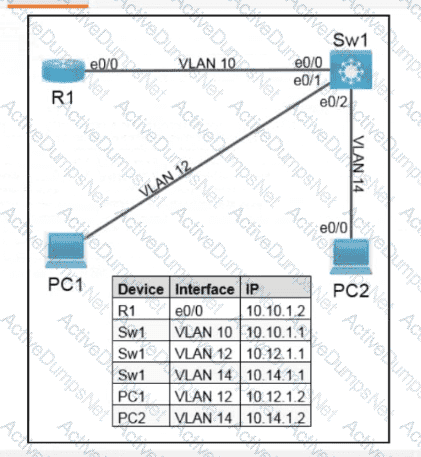

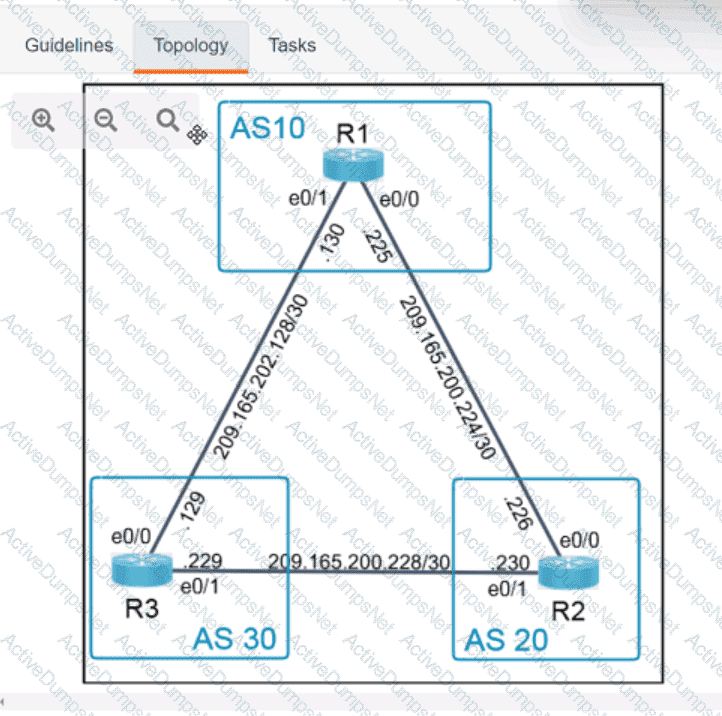
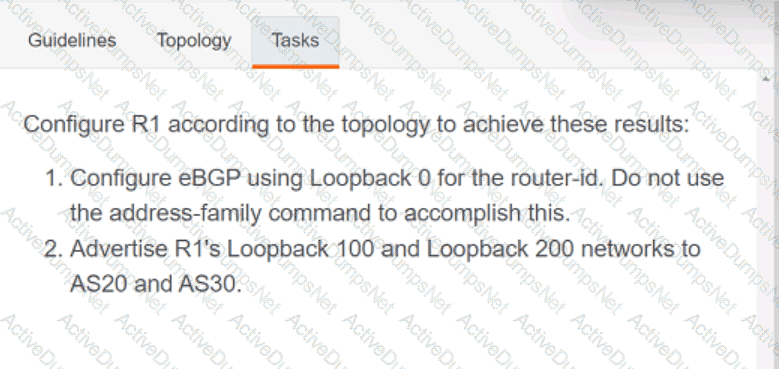
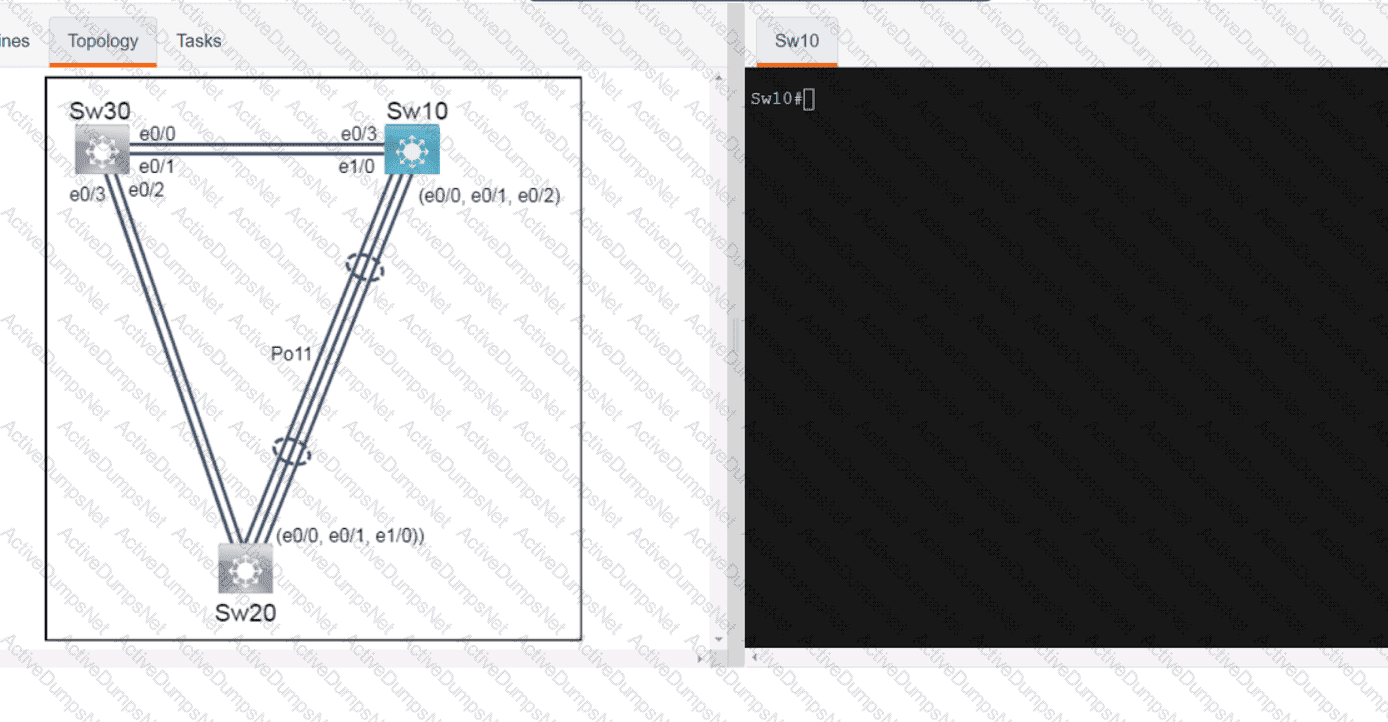
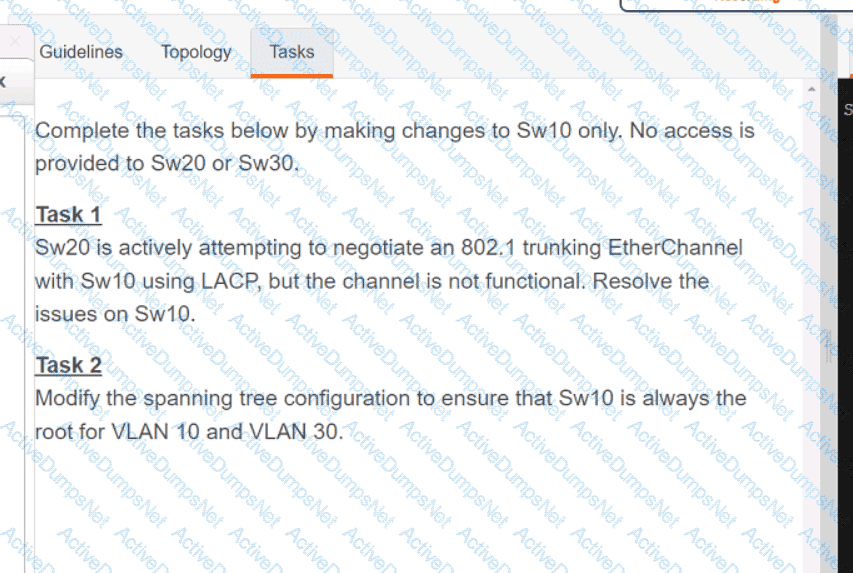


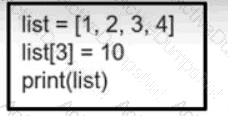
Refer to the exhibit. What is the value of the variable list after the code is run?
A response code of 404 is received while using the REST API on Cisco UNA Center to POST to this URI.
/dna/intent/api/v1 /template-programmer/project
What does the code mean?
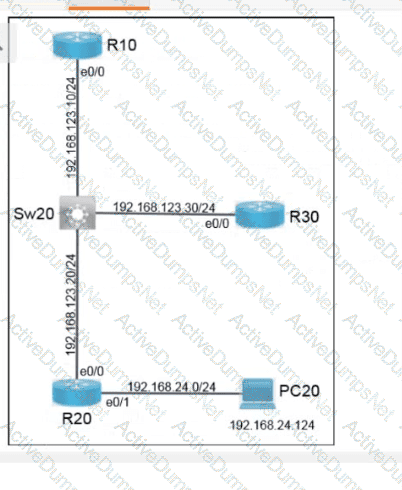
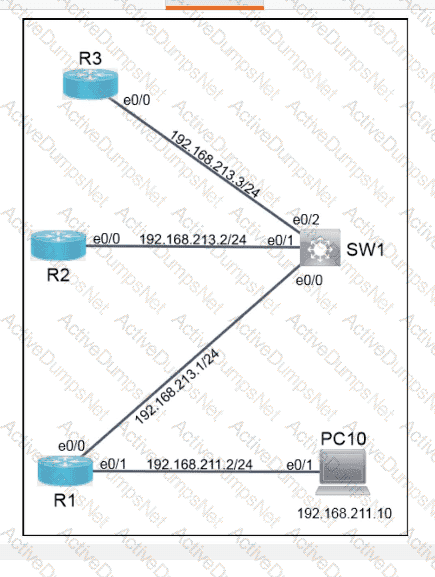
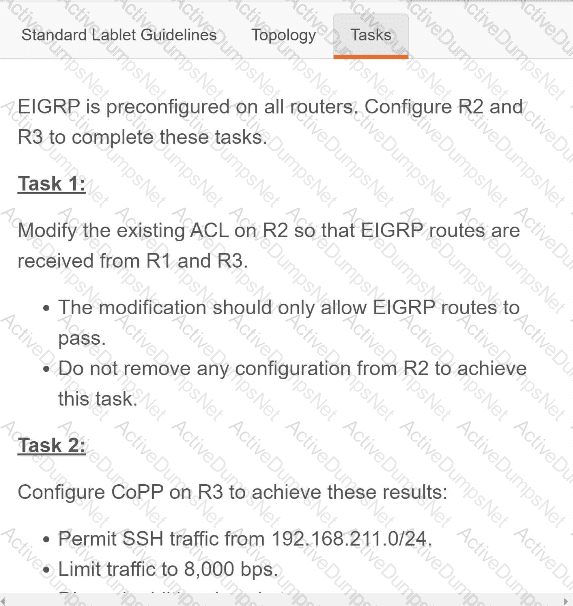
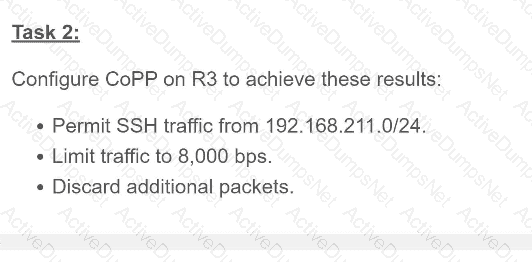
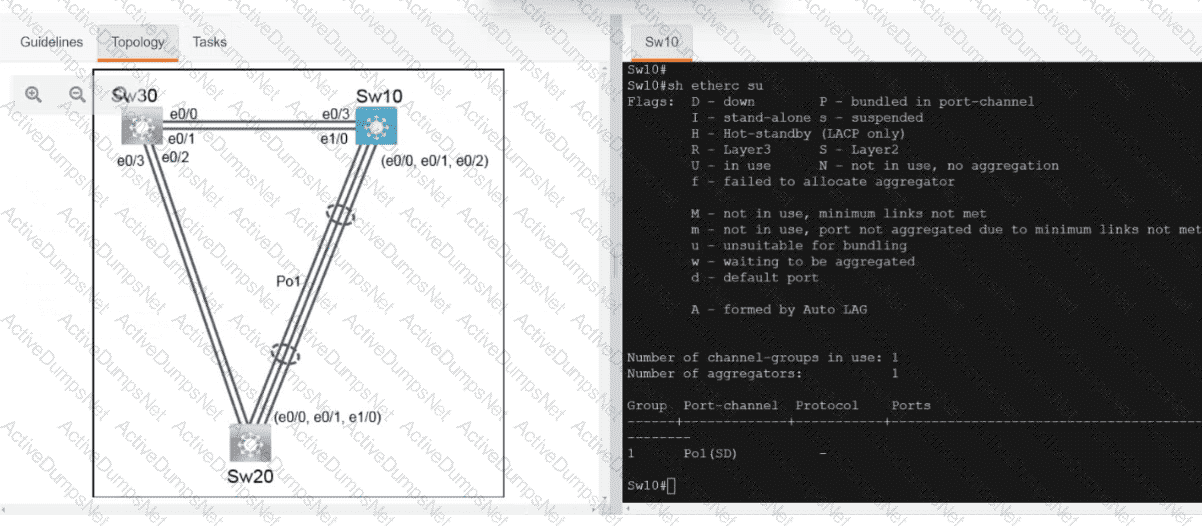
An engineer is reviewing a PCAP file that contains a packet capture of a four-way handshake exchange between a dient and AP using WPA2 Enterprise Which EAPOL message validates and confirms that the client device has successfully Installed the GTK?
Which tag defines the properties to be applied to each specific WLAN?

Refer to the exhibit. Based on this JSON response:
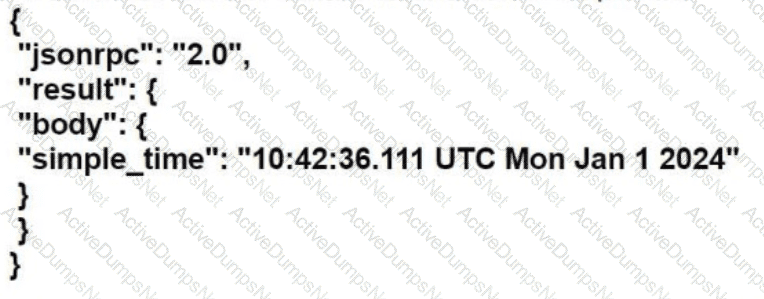
Which Python statement parses the response and prints "10:42:36.111 UTC Mon Jan 1 2024"?
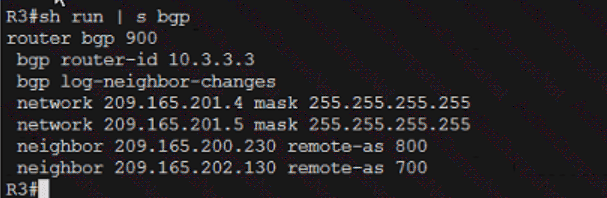
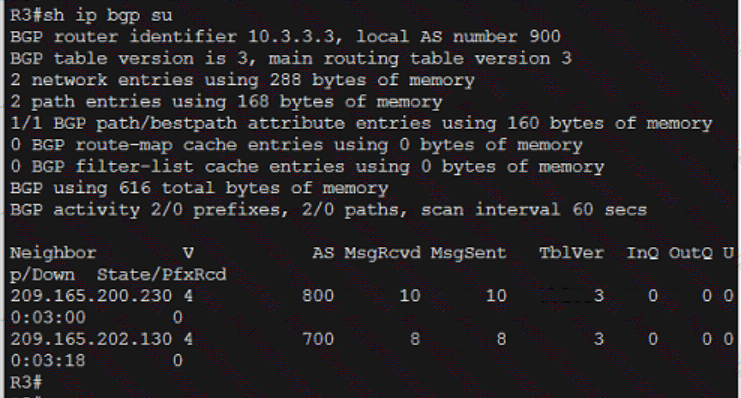
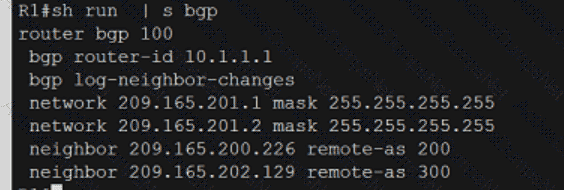
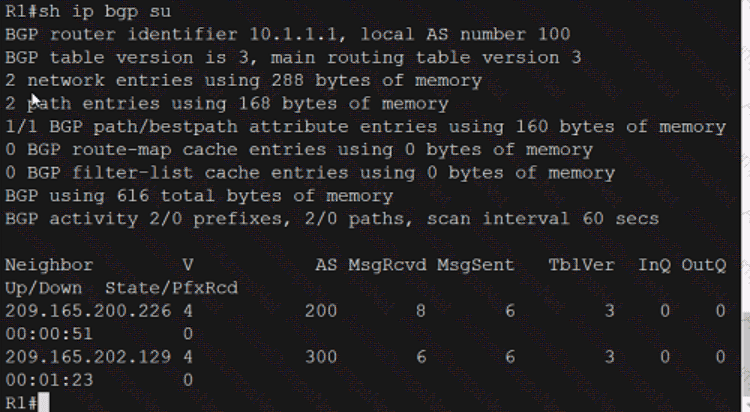
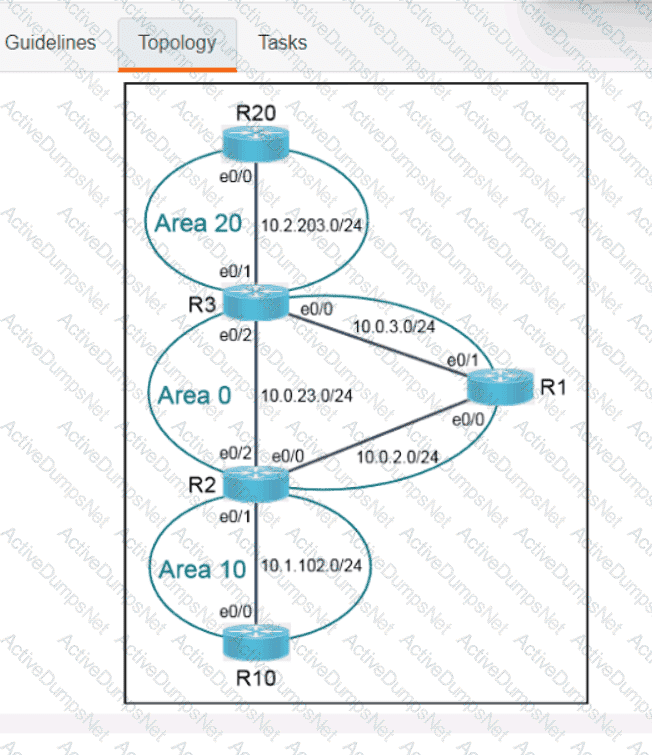
Which technology is the Cisco SD-Access control plane based on?
Which language can be used to model configuration and state data?
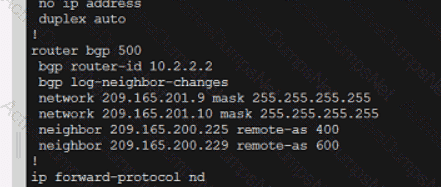
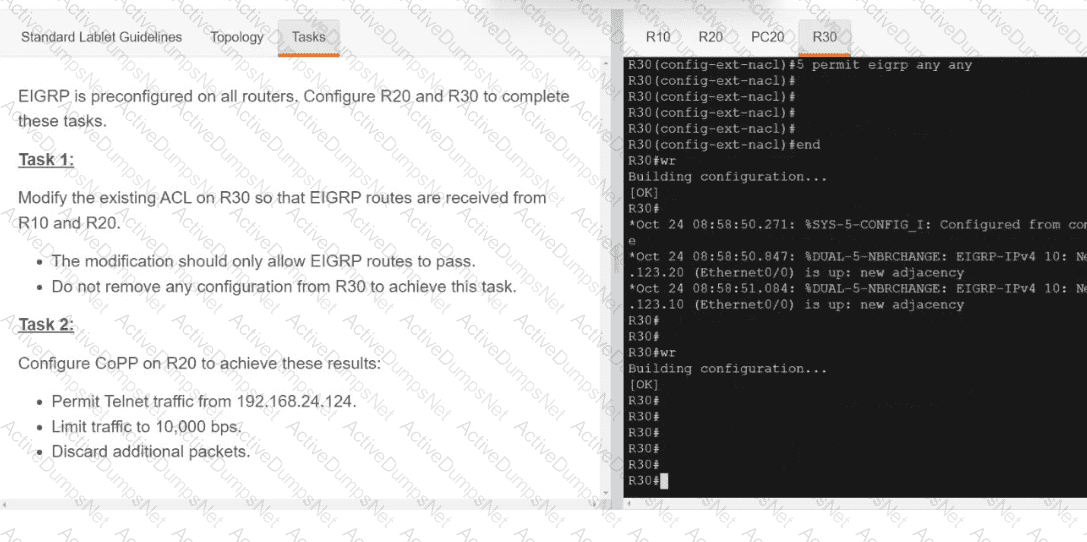
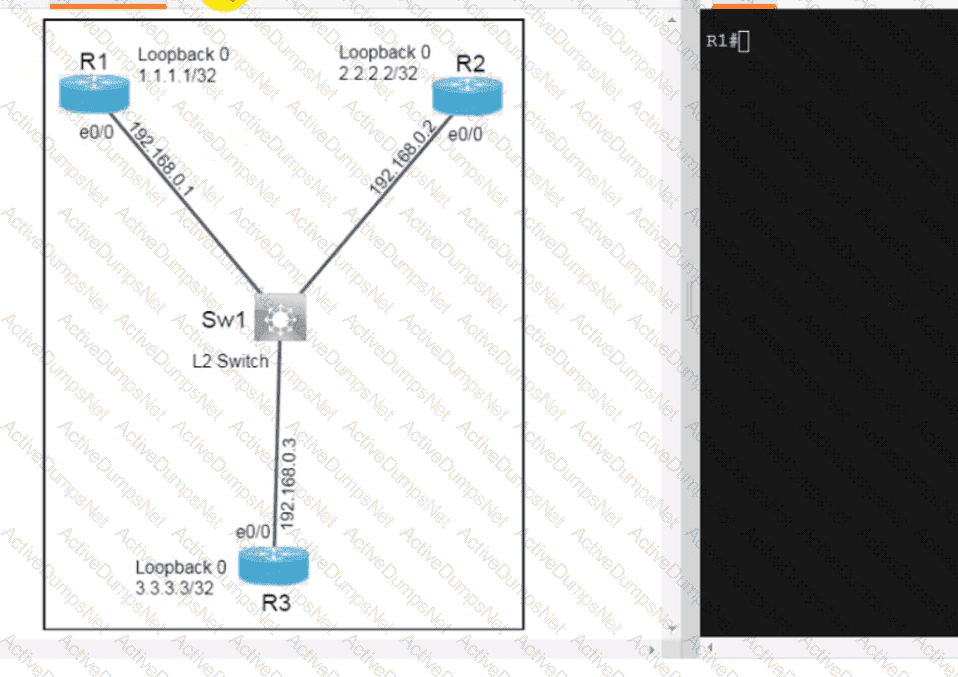
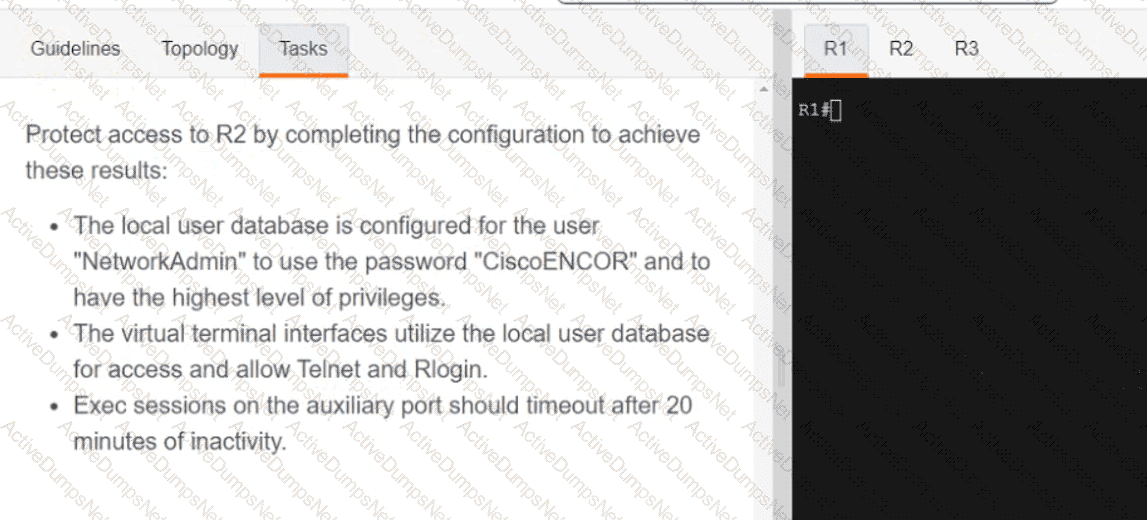
Which configuration enables a Cisco router lo send information to a TACACS+ server for individual EXEC commands associated with privilege level 15?
Which two new security capabilities are introduced by using a next-generation firewall at the Internet edge? (Choose two.)
What is a benefit of YANG modules?
Which two operational modes enable an AP to scan one or more wireless channels for rogue access points and at the same time provide wireless services to clients? (Choose two.)

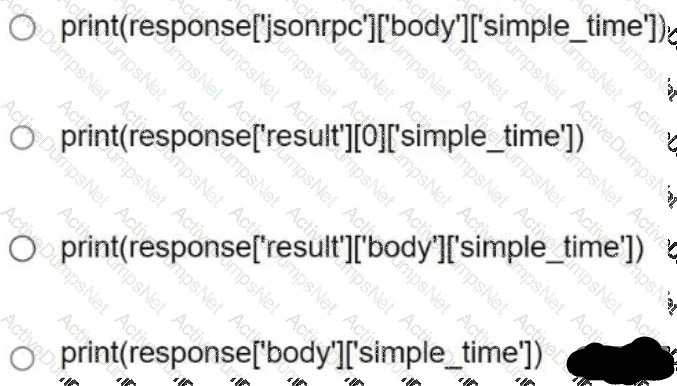
Refer to the exhibit. Drag and drop the snippets into the RESTCONF request to form the request that returns this response. Not all options are used.
Which technology is the Cisco SD-Access control plane based on?

What is the JSON syntax that is formed from the data?
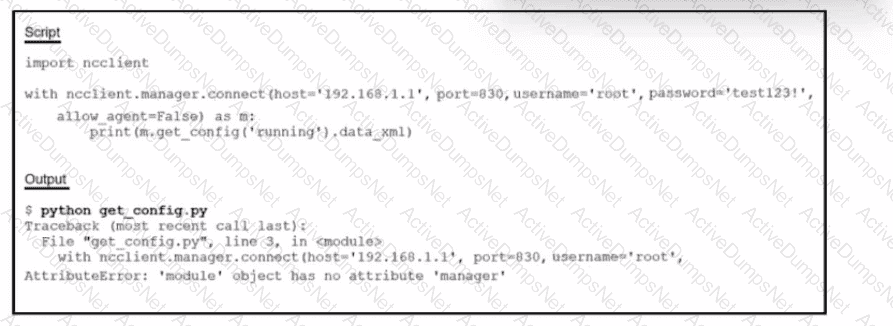
Refer to the exhibit. Running the script causes the output in the exhibit. What should be the first line of the script?
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
•LocationA -72dBm
• Location B:-75 dBm
• Location C; -65 dBm
• Location D -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two.)
Which two actions are recommended as security best practices to protect REST API? (Choose two.)
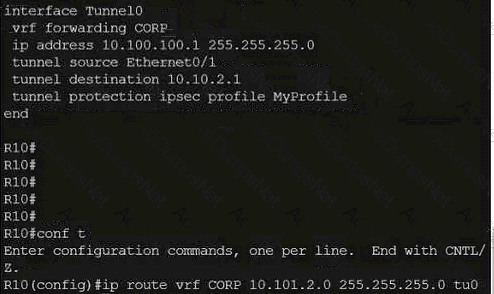
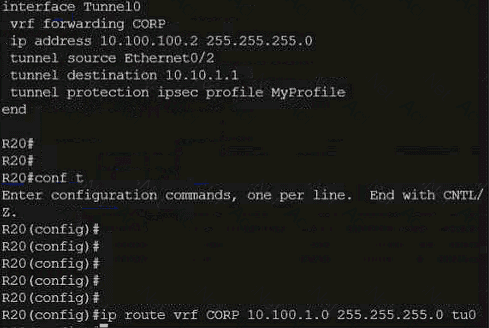
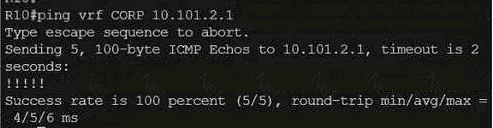
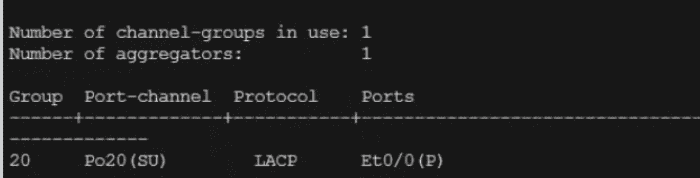
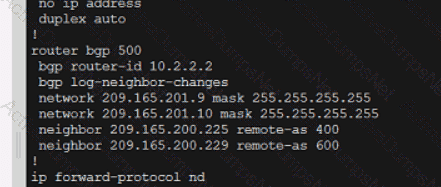
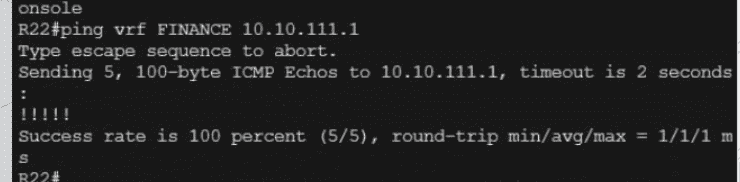
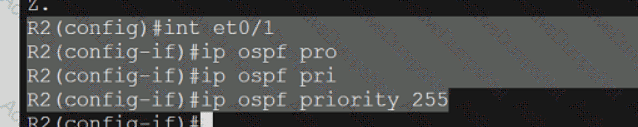
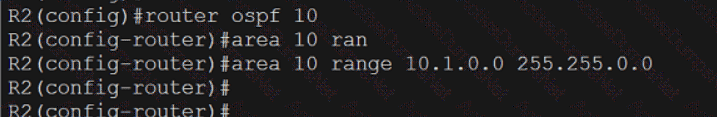
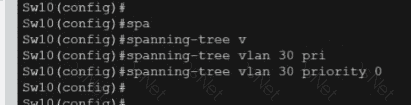
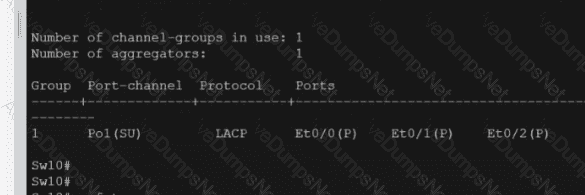
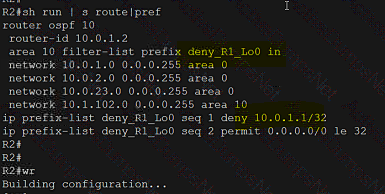
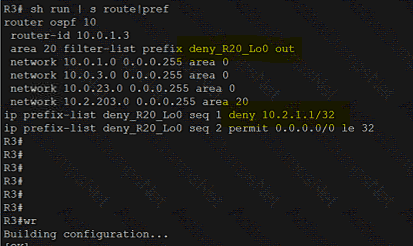
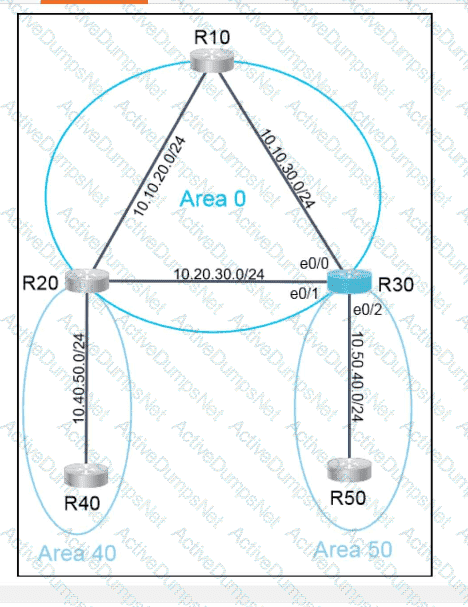
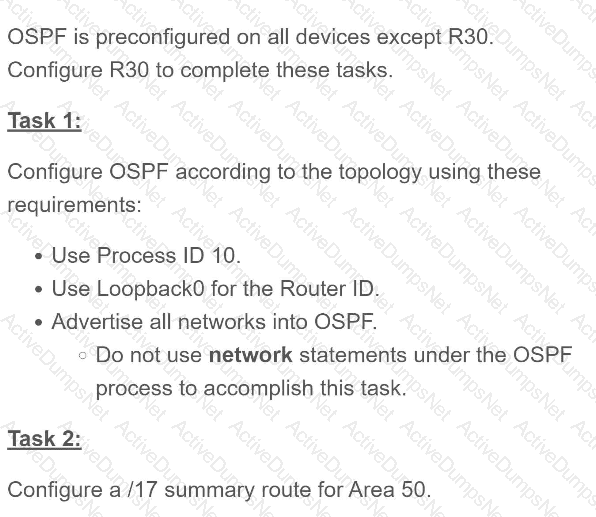
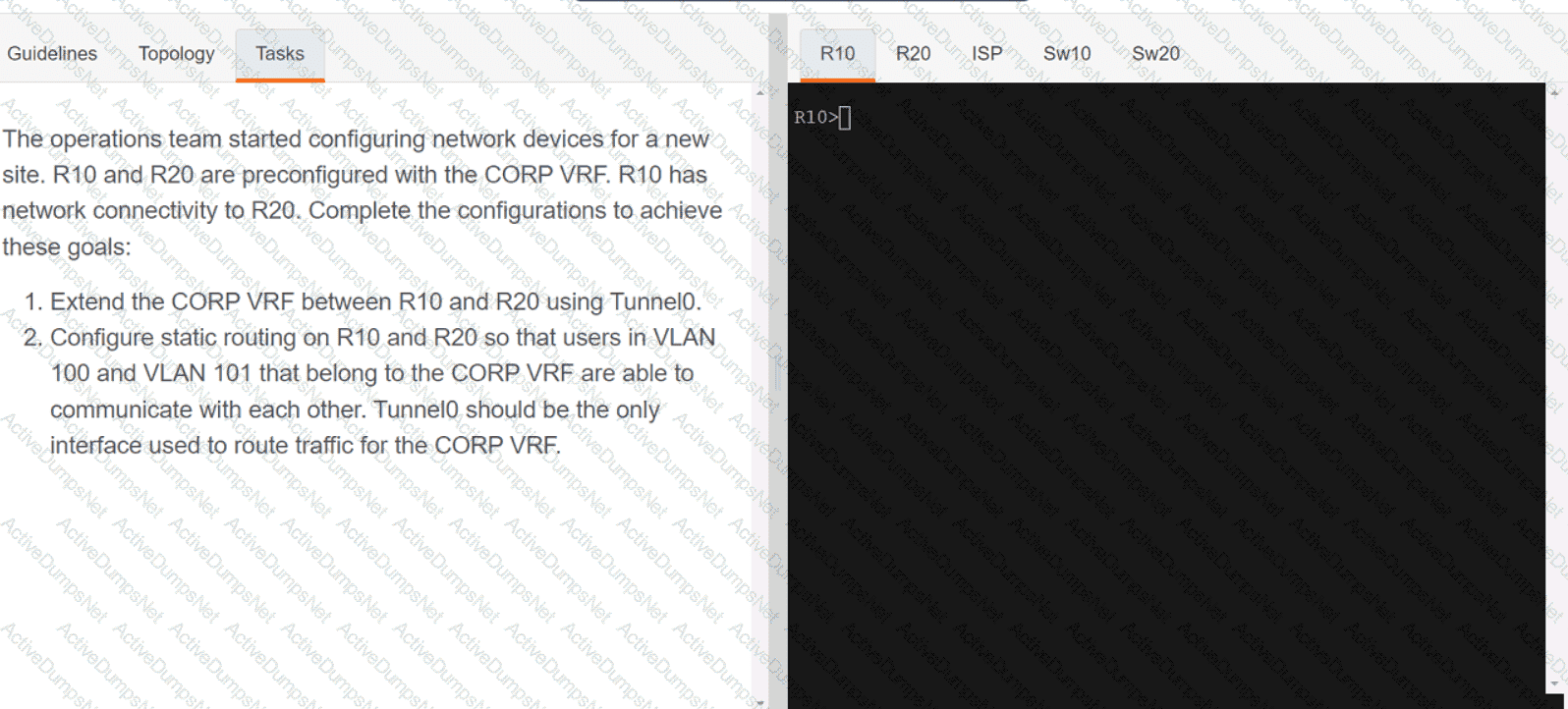
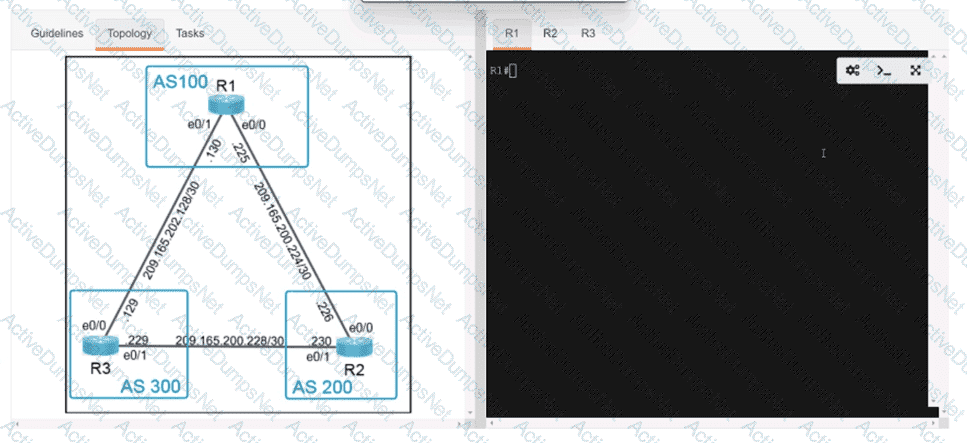
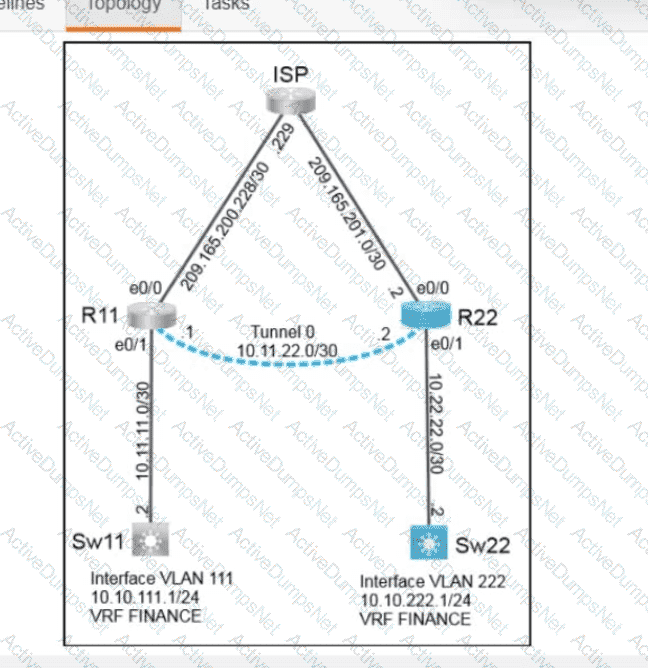
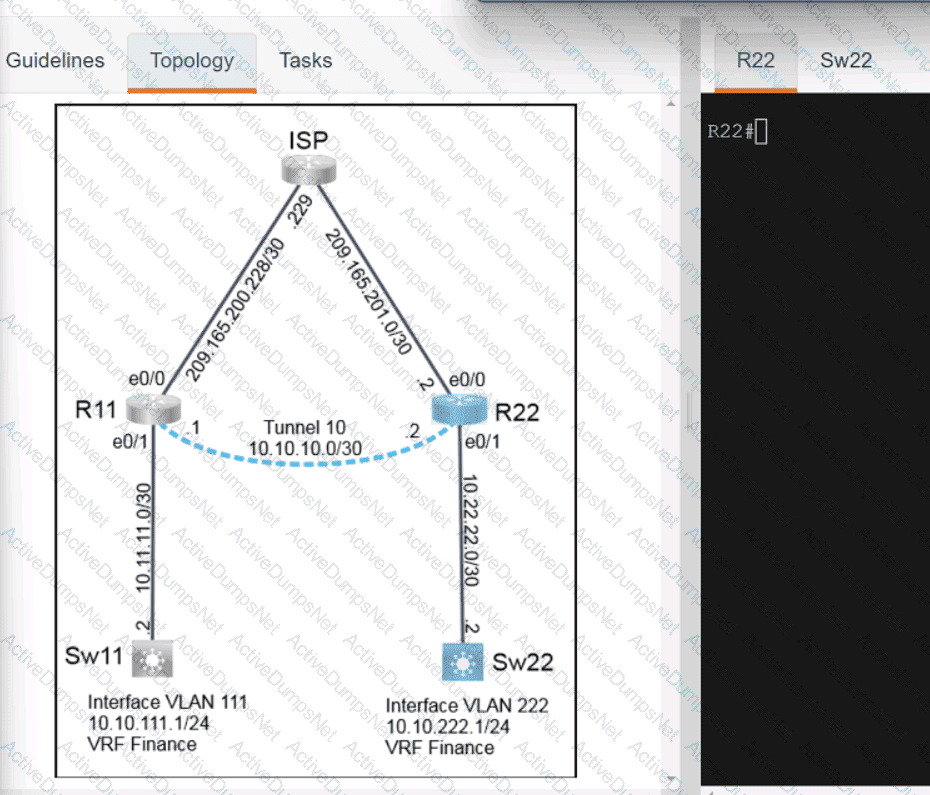
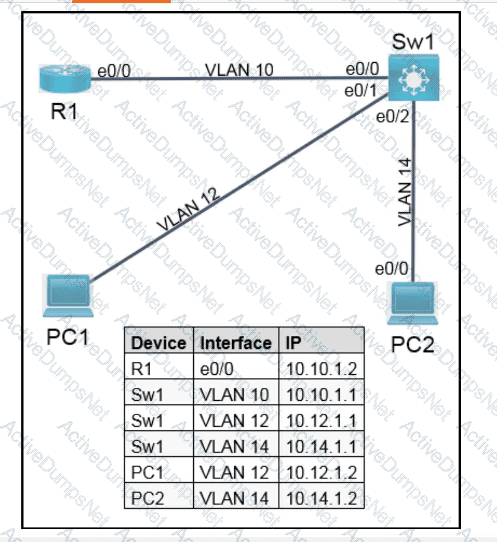
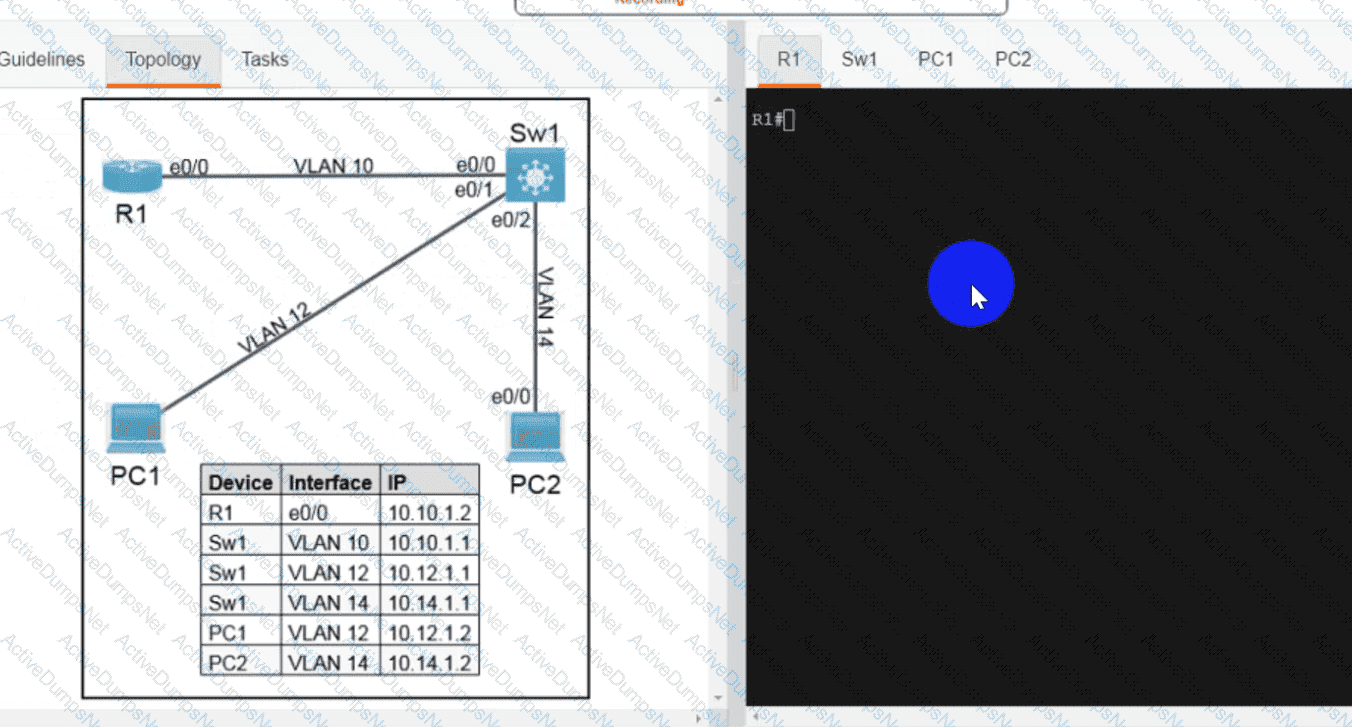
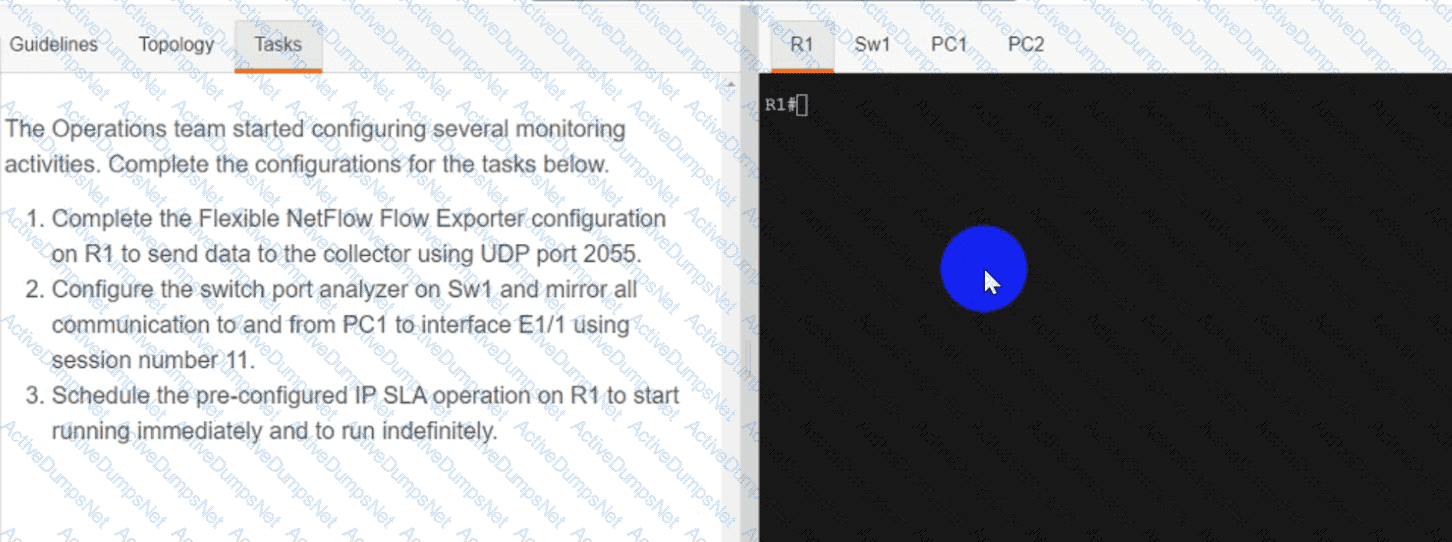
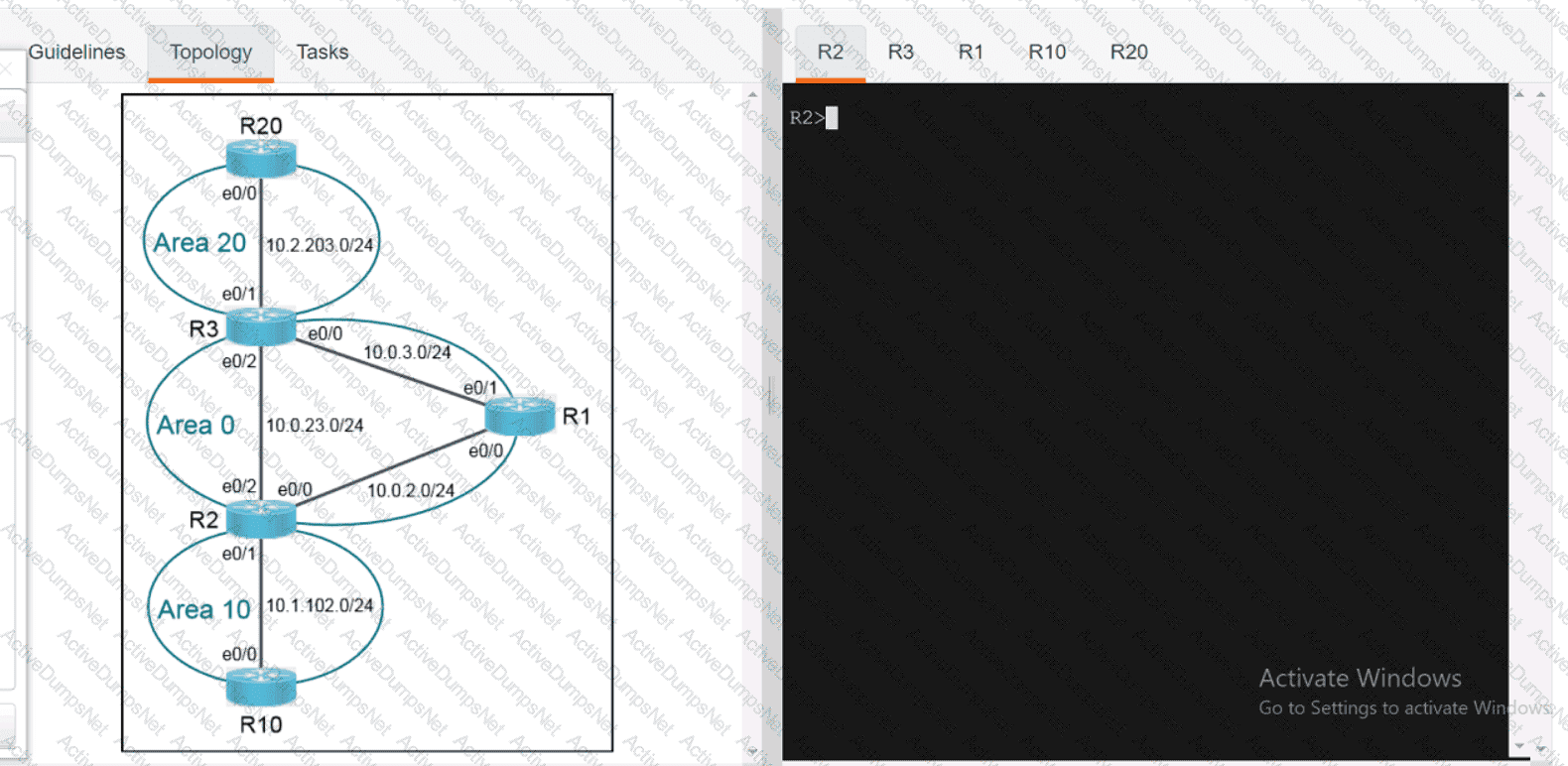
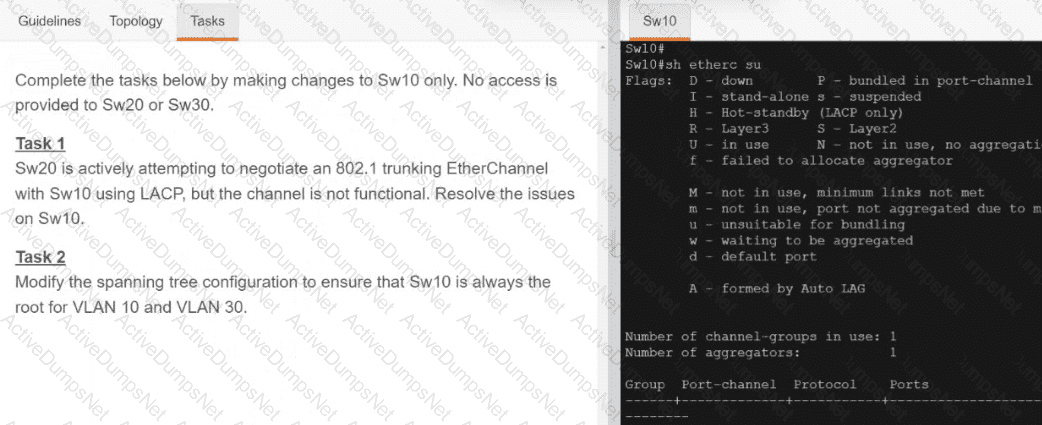
Refer to the exhibit.
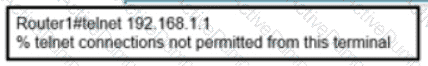
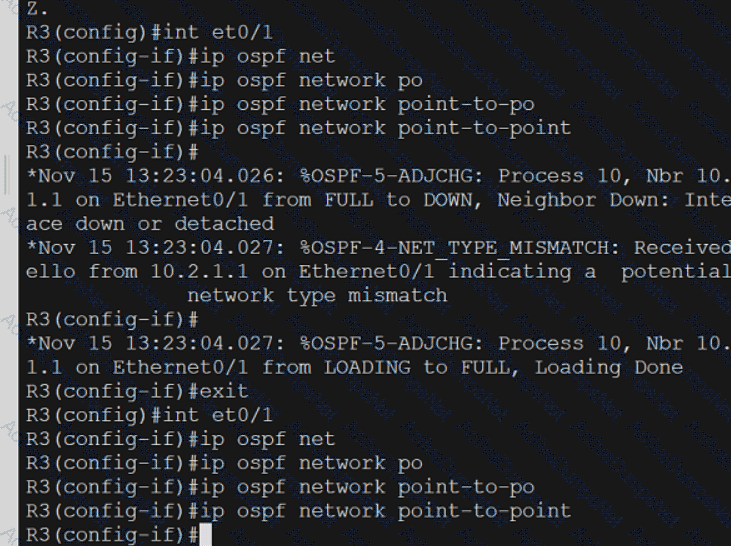
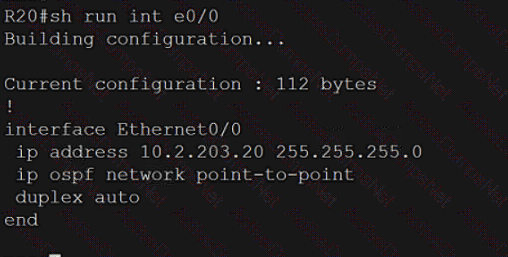
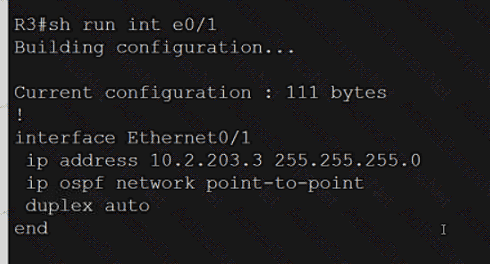
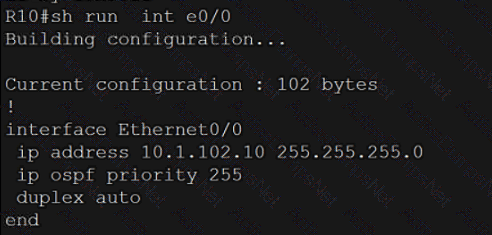
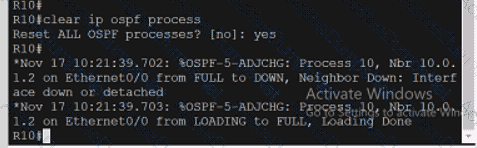
An engineer attempts to connect to another device from Route1’s console port. Which configuration is needed to allow telnet connections?
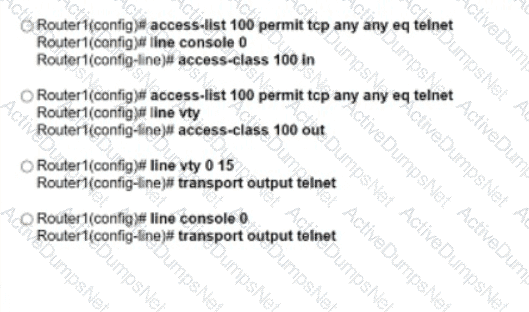
Drag and drop the snippets onto the blanks within the code to create an EEM script that adds an entry to a locally stored text file with a timestamp when a configuration change is made. Not all options are used.
What is the measure of the difference between the received signal and the noise floor in a wireless environment?
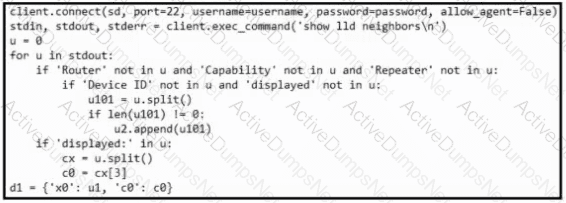
Refer to the exhibit. What is achieved by this Python script?
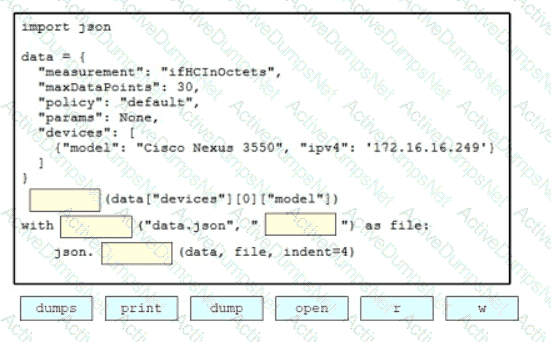
Drag and drop the code snippets from the bottom onto the blanks in the Python script to print the device model to the screen and write JSON data to a file. Not all options are used
A customer requires their wireless data traffic to egress at the switch port of the access point. Which access point mode supports this?
Which feature works with SSO to continue forwarding packets after a route processor failure until the control plane recovers?
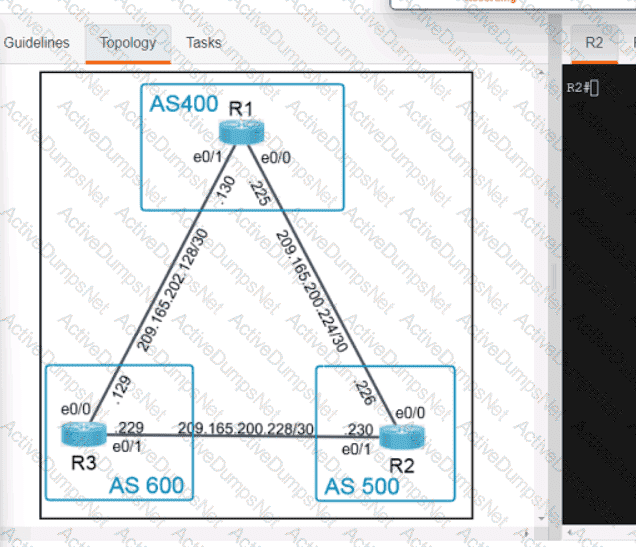
Which Cisco Catalyst SD-WAN component is responsible for distributing data plane traffic policies?
What happens when a FlexConnect AP changes to standalone mode?
A company recently decided to use RESTCONF instead of NETCONF. and many of their NETCONF scripts contain the operation
What is used by vManage to interact withCiscoSD-WAN devices in the fabric?
Which three methods does Cisco Catalyst Center (formerly DNA Center) use to discover devices? (Choose three.)
A corporate policy mandates that a certificate-based authentication system must be implemented on the wireless infrastructure. All corporate clients will contain a certificate that will be used in conjunction with ISE and user credentials to perform authentication before the clients are allowed to connect to the corporate Wi-Fi. Which authentication key option must be selected to ensure that this authentication can take place?