Cisco 300-740 Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) Exam Practice Test
Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) Questions and Answers
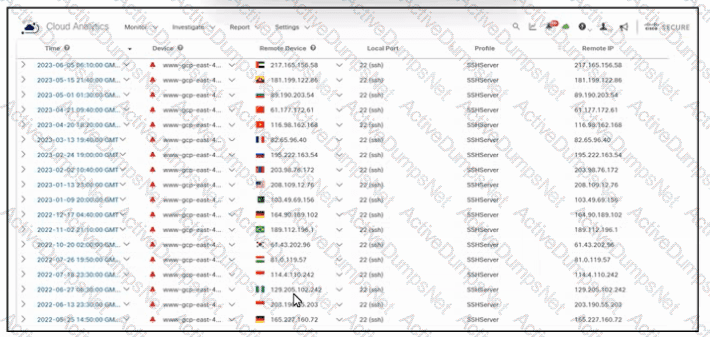
Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is occurring?
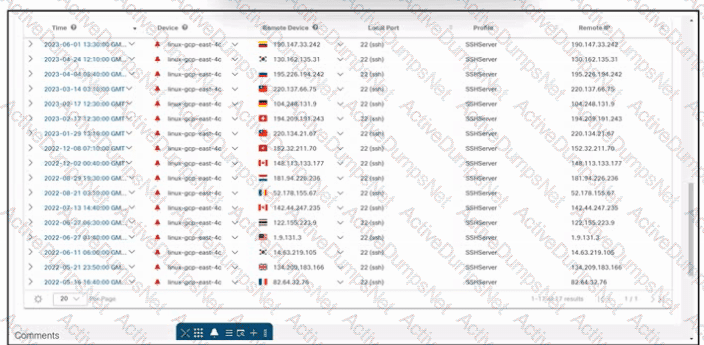
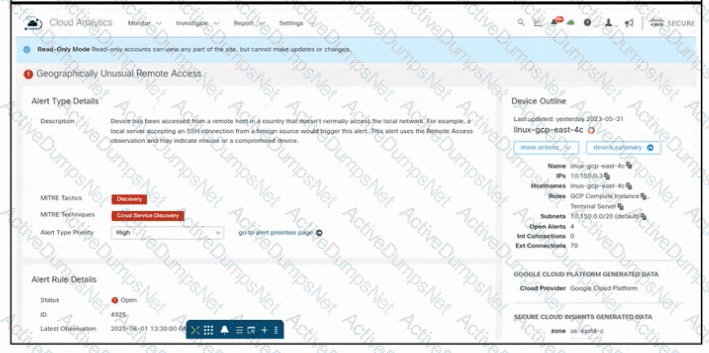
Refer to the exhibit. An engineer is investigating an issue by using Cisco Secure Cloud Analytics. The engineer confirms that the connections are unauthorized and informs the incident management team. Which two actions must be taken next? (Choose two.)
Which common strategy should be used to mitigate directory traversal attacks in a cloud environment?
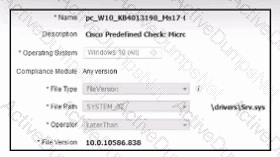
Refer to the exhibit. A security engineer must configure a posture policy in Cisco ISE to ensure that employee laptops have a critical patch for WannaCry installed before they can access the network. Which posture condition must the engineer configure?
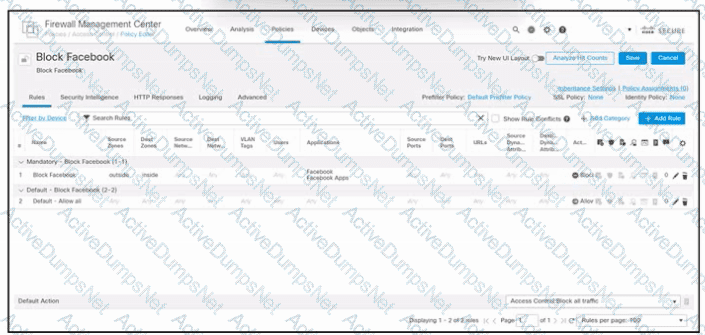
Refer to the exhibit. An engineer must block internal users from accessing Facebook and Facebook Apps. All other access must be allowed. The indicated policy was created in Cisco Secure Firewall Management Center and deployed to the internet edge firewall; however, users still can access Facebook. Which two actions must be taken to meet the requirement? (Choose two.)
What is a crucial component in the MITRE ATT&CK framework?
Which method is used by a Cisco XDR solution to prioritize actions?
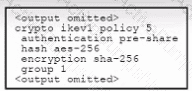
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv1 VPN that will use AES256 and SHA256 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which two IKEv1 policy commands must be run to meet the requirement? (Choose two.)
A network administrator uses Cisco Umbrella to protect internal users from malicious content. A customer is using an IPsec tunnel to connect to an Umbrella Organization. The administrator was informed about a zero-day vulnerability that infects user machines and uploads sensitive data through the RDP port. The administrator must ensure that no users are connected to the internet using the RDP protocol. Which Umbrella configuration must the administrator apply?
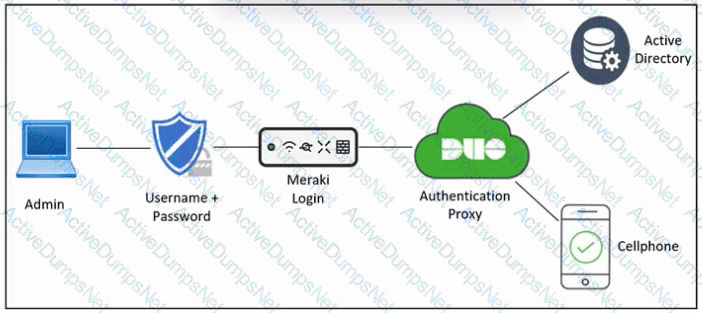
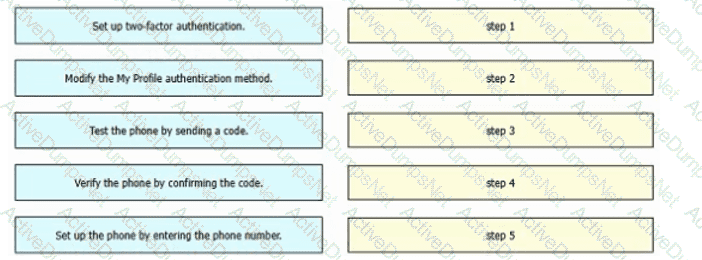
Refer to the exhibit. An engineer must configure multifactor authentication using the Duo Mobile app to provide admin access to a Cisco Meraki switch. The engineer already configured Duo Mobile and received an activation code. Drag and drop the steps from left to right to complete the configuration.
Which concept is used in the Cisco SAFE key reference model?
An engineer configures trusted endpoints with Active Directory with Device Health to determine if an endpoint complies with the policy posture. After a week, an alert is received by one user, reporting problems accessing an application. When the engineer verifies the authentication report, this error is found:
"Endpoint is not trusted because Cisco Secure Endpoint check failed, Check user's endpoint in Cisco Secure Endpoint."
Which action must the engineer take to permit access to the application again?
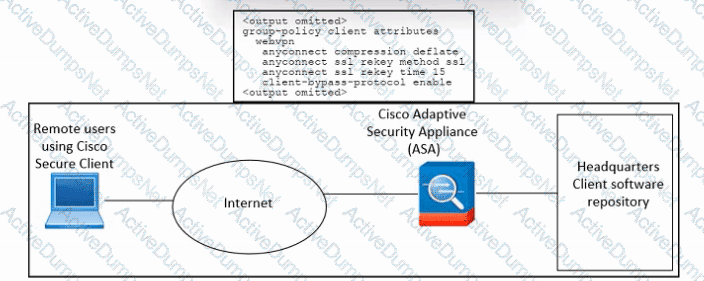
Refer to the exhibit. An engineer must configure Cisco ASA so that the Secure Client deployment is removed when the user laptop disconnects from the VPN. The indicated configuration was applied to the Cisco ASA firewall. Which command must be run to meet the requirement?

Refer to the exhibit. An engineer must create a segmentation policy in Cisco Secure Workload to block HTTP traffic. The indicated configuration was applied; however, HTTP traffic is still allowed. What should be done to meet the requirement?
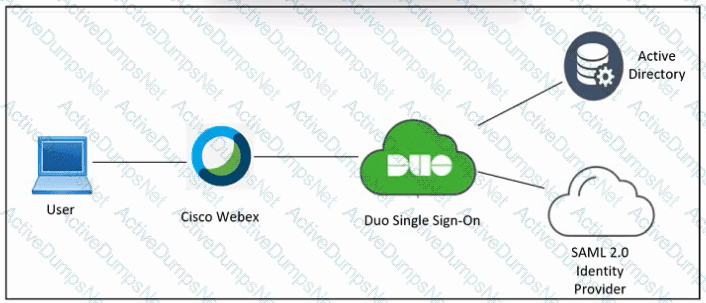
Refer to the exhibit. An engineer must configure Duo SSO for Cisco Webex and add the Webex application to the Duo Access Gateway. Which two actions must be taken in Duo? (Choose two.)
According to Cisco Security Reference Architecture, which solution provides threat intelligence and malware analytics?
In the zero-trust network access model, which criteria is used for continuous verification to modify trust levels?

Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)

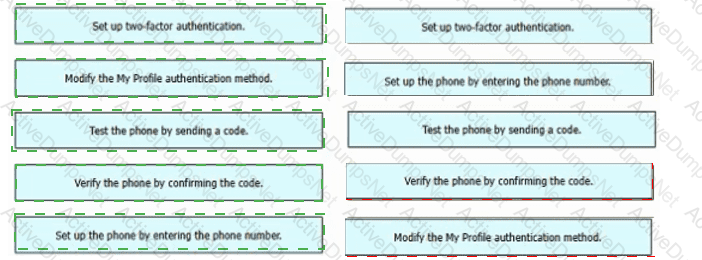
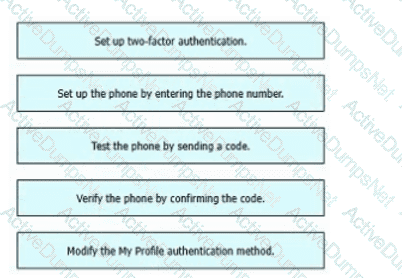 A screenshot of a phone number
AI-generated content may be incorrect.
A screenshot of a phone number
AI-generated content may be incorrect.