Cisco 300-720 Securing Email with Cisco Email Security Appliance (300-720 SESA) Exam Practice Test
Securing Email with Cisco Email Security Appliance (300-720 SESA) Questions and Answers
Which two features of Cisco Email Security are added to a Sender Group to protect an organization against email threats? (Choose two.)
An engineer is configuring an SMTP authentication profile on a Cisco ESA which requires certificate verification.
Which section must be configured to accomplish this goal?
An administrator identifies that, over the past week, the Cisco ESA is receiving many emails from certain senders and domains which are being consistently quarantined. The administrator wants to ensure that these senders and domain are unable to send anymore emails.
Which feature on Cisco ESA should be used to achieve this?
Which two features are applied to either incoming or outgoing mail policies? (Choose two.)
Which suboption must be selected when LDAP is configured for Spam Quarantine End-User Authentication?
An administrator notices that incoming emails with certain attachments do not get delivered to all recipients when the emails have multiple recipients in different domains like cisco.com and test.com. The same emails when sent only to recipients in cisco.com are delivered properly. How must the Cisco Secure Email Gateway be configured to avoid this behavior?
Which components are required when encrypting SMTP with TLS on a Cisco Secure Email Gateway appliance when the sender requires TLS verification?
An organization wants to use DMARC to improve its brand reputation by leveraging DNS records.
Which two email authentication mechanisms are utilized during this process? (Choose two.)
How does the graymail safe unsubscribe feature function?
Which SMTP extension does Cisco ESA support for email security?
A Cisco Secure Email Gateway administrator is creating a Mail Flow Policy to receive outbound email from Microsoft Exchange. Which Connection Behavior must be selected to properly process the messages?
Spreadsheets containing credit card numbers are being allowed to bypass the Cisco ESA.
Which outgoing mail policy feature should be configured to catch this content before it leaves the network?
A Cisco Secure Email Gateway administrator recently enabled the Outbreak Filters Global Service Setting to detect Viral as well as Non-Viral threat detection, with no detection of Non-viral threats after 24 hours of monitoring Outbreak Filters What is the reason that Non-Viral threat detection is not detecting any positive verdicts?
An administrator is managing multiple Cisco ESA devices and wants to view the quarantine emails from all devices in a central location.
How is this accomplished?
What are the two different phases in the process of Cisco Secure Email Gateway performing S/MIME encryption? (Choose two.)
What is the maximum message size that can be configured for encryption on the Cisco ESA?
An organization wants to designate help desk personnel to assist with tickets that request the release of messages from the spam quarantine because company policy does not permit direct end-user access to the quarantine. Which two roles must be used to allow help desk personnel to release messages while restricting their access to make configuration changes in the Cisco Secure Email Gateway? (Choose two.)
When URL logging is configured on a Cisco ESA, which feature must be enabled first?
Refer to the exhibit.
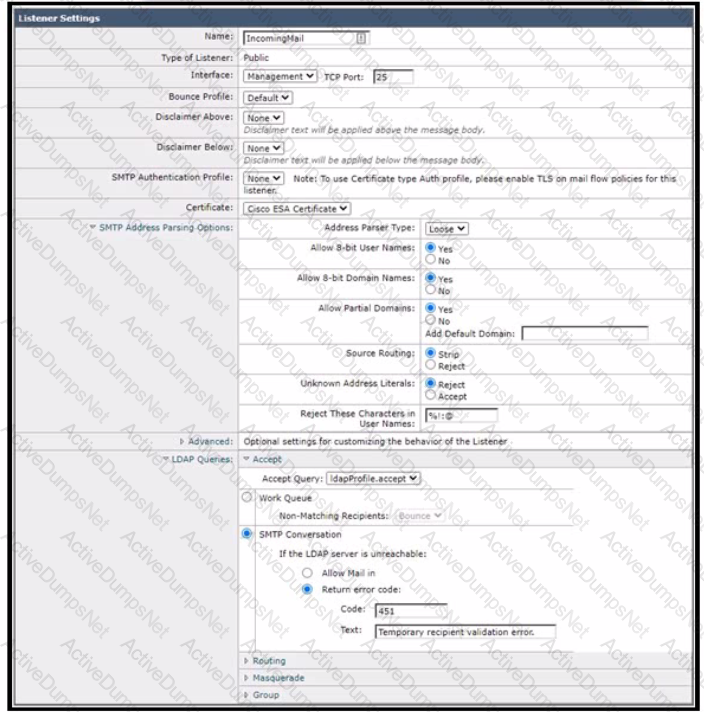
Which additional configuration action must be taken to protect against Directory Harvest Attacks?
A network administrator is modifying an outgoing mail policy to enable domain protection for the organization. A DNS entry is created that has the public key.
Which two headers will be used as matching criteria in the outgoing mail policy? (Choose two.)
Which component must be added to the content filter to trigger on failed SPF Verification or DKIM Authentication verdicts?
Which two factors must be considered when message filter processing is configured? (Choose two.)
An administrator has created a content filter to quarantine all messages that result in an SPF hardfail to review the messages and determine whether a trusted partner has accidentally misconfigured the DNS settings. The administrator sets the policy quarantine to release the messages after 24 hours, allowing time to review while not interrupting business.
Which additional option should be used to help the end users be aware of the elevated risk of interacting with these messages?
Which type of query must be configured when setting up the Spam Quarantine while merging notifications?
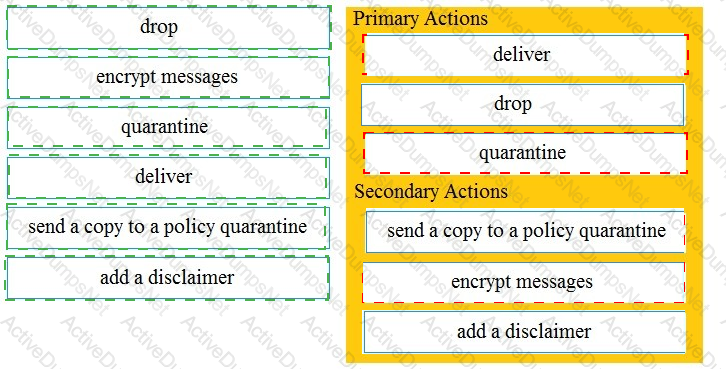
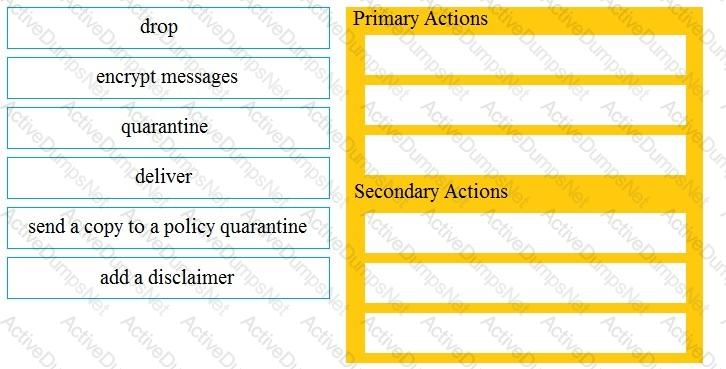
Drag and drop the Cisco ESA reactions to a possible DLP from the left onto the correct action types on the right.
Which two query types are available when an LDAP profile is configured? (Choose two.)
An administrator manipulated the subnet mask but was still unable to access the user interface. How must the administrator access the Cisco Secure Email Gateway appliance to perform the initial configuration?
An analyst creates a new content dictionary to use with Forged Email Detection.
Which entry will be added into the dictionary?
Which feature utilizes sensor information obtained from Talos intelligence to filter email servers connecting into the Cisco ESA?
Refer to the exhibit.
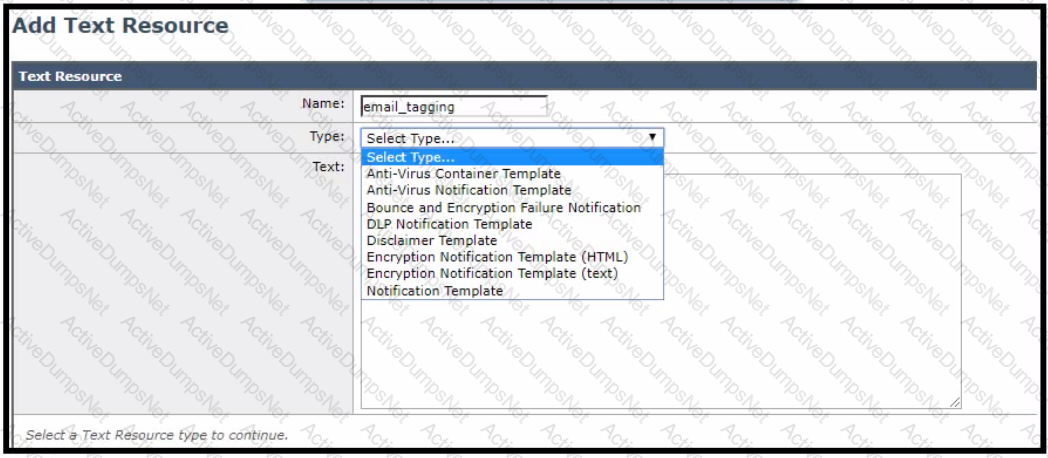
For improved security, an administrator wants to warn users about opening any links or attachments within an email How must the administrator configure an HTML-coded message at the top of an email body to create this warning?
A Cisco Secure Email Gateway administrator must provide outbound email authenticity and configures a DKIM signing profile to handle this task. What is the next step to allow this organization to use DKIM for their outbound email?
A trusted partner of an organization recently experienced a new campaign that was leveraging JavaScript attachments to trick users into executing malware. As a result, they created a local policy to deny messages with JavaScript attachments. Which action should the administrator of the organization take to ensure encrypted communications are delivered to the intended partner recipient?
A company has deployed a new mandate that requires all emails sent externally from the Sales Department to be scanned by DLP for PCI-DSS compliance. A new DLP policy has been created on the Cisco ESA and needs to be assigned to a mail policy named ‘Sales’ that has yet to be created.
Which mail policy should be created to accomplish this task?
A Cisco Secure Email Gateway appliance is processing many messages that are sent to invalid recipients verification. Which two steps are required to accomplish this task? (Choose two.)
What is the default HTTPS port when configuring spam quarantine on Cisco ESA?
A Cisco ESA administrator was notified that a user was not receiving emails from a specific domain. After reviewing the mail logs, the sender had a negative sender-based reputation score.
What should the administrator do to allow inbound email from that specific domain?
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
A content dictionary was created for use with Forged Email Detection. Proper data that pertains to the CEO Example CEO:
Which two components must be configured to perform DLP scanning? (Choose two.)
Which feature must be activated on a Cisco Secure Email Gateway to combat backscatter?
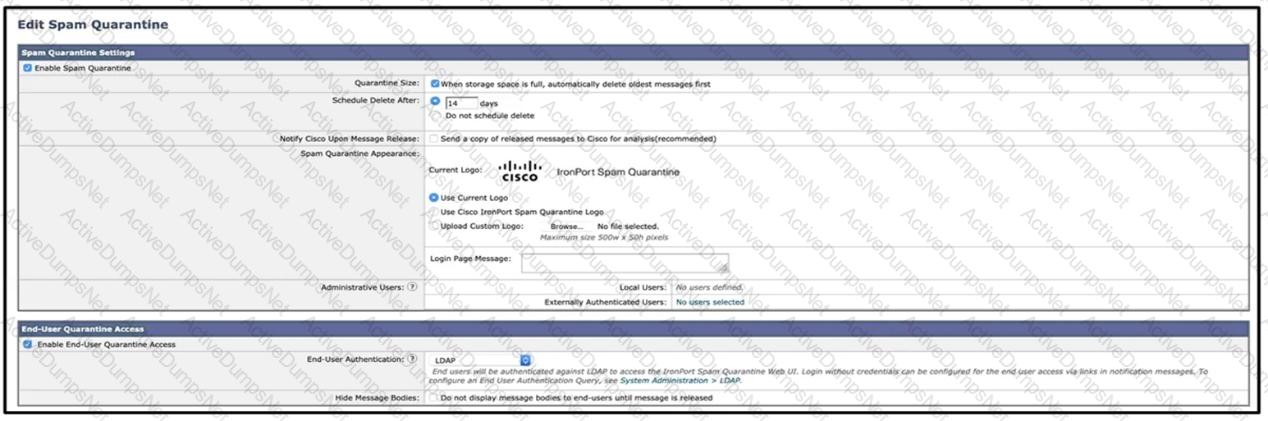

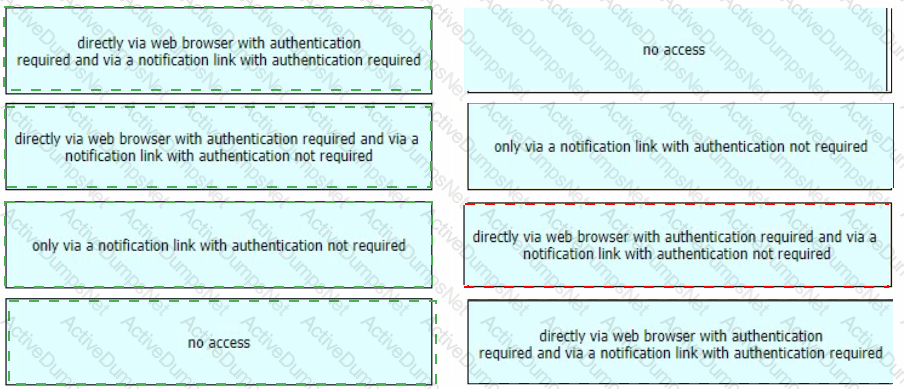
Refer to the exhibits. What must be done to enforce end user authentication before accessing quarantine?
Drag and drop authentication options for End-User Quarantine Access from the left onto the corresponding configuration steps on the right.
Which of the following two statements are correct about the large file attachments (greater than 25MB) feature in Cisco Secure Email Encryption Service? (Choose two.)
Which content filter condition checks to see if the "From: header" in the message is similar to any of the users in the content dictionary?