Cisco 300-715 Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) Exam Practice Test
Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) Questions and Answers
An engineer is configuring web authentication using non-standard ports and needs the switch to redirect traffic to the correct port. Which command should be used to accomplish this task?
An administrator needs to add a new third party network device to be used with Cisco ISE for Guest and BYOD authorizations. Which two features must be configured under Network Device Profile to achieve this? (Choose two.)
An engineer is enabling a newly configured wireless SSID for tablets and needs visibility into which other types of devices are connecting to it. What must be done on the Cisco WLC to provide this information to Cisco ISE9
Which two features must be used on Cisco ISE to enable the TACACS. feature? (Choose two)
Which two features should be used on Cisco ISE to enable the TACACS+ feature? (Choose two )
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network Which CoA configuration meets this requirement?
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose two)
An engineer is assigned to enhance security across the campus network. The task is to enable MAB across all access switches in the network. Which command must be entered on the switch to enable MAB?
A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task''
Which two VMware features are supported on a Cisco ISE virtual appliance? (Choose two.)
How is policy services node redundancy achieved in a deployment?
The IT manager wants to provide different levels of access to network devices when users authenticate using TACACS+. The company needs specific commands to be allowed based on the Active Directory group membership of the different roles within the IT department. The solution must minimize the number of objects created in Cisco ISE. What must be created to accomplish this task?
The security engineer for a company has recently deployed Cisco ISE to perform centralized authentication of all network device logins using TACACS+ against the local AD domain. Some of the other network engineers are having a hard time remembering to enter their AD account password instead of the local admin password that they have used for years. The security engineer wants to change the password prompt to "Use Local AD Password:" as a way of providing a hint to the network engineers when logging in. Under which page in Cisco ISE would this change be made?
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
An administrator is configuring new probes to use with Cisco ISE and wants to use metadata to help profile the endpoints. The metadata must contain traffic information relating to the endpoints instead of industry-standard protocol information Which probe should be enabled to meet these requirements?
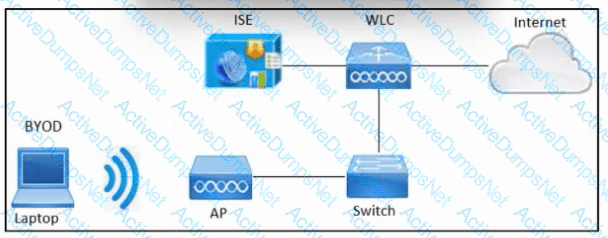
Refer to the exhibit. An engineer must configure BYOD in Cisco ISE. A single SSID must be used to allow BYOD devices to connect to the network. These configurations have been performed on Wireless LAN Controller already:
RADIUS server
BYOD-Dot1x SSID
Which two configurations must be done in Cisco ISE to meet the requirement? (Choose two.)
A network engineer is configuring a Cisco Wireless LAN Controller in order to find out more information about the devices that are connecting. This information must be sent to Cisco ISE to be used in authorization policies. Which profiling mechanism must be configured in the Cisco Wireless LAN Controller to accomplish this task?
An administrator is configuring the Native Supplicant Profile to be used with the Cisco ISE posture agents and needs to test the connection using wired devices to determine which profile settings are available. Which two configuration settings should be used to accomplish this task? (Choose two.)
Refer to the exhibit.
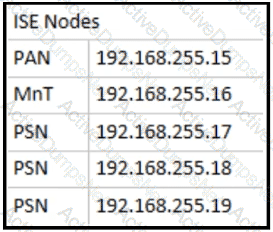
Which two configurations are needed on a catalyst switch for it to be added as a network access device in a Cisco ISE that is being used for 802 1X authentications? (Choose two )
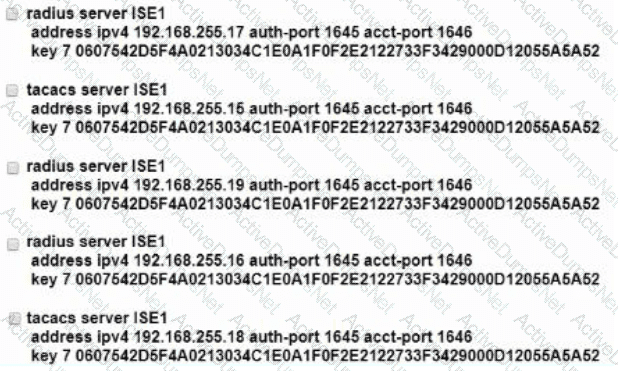
Which two ports do network devices typically use for CoA? (Choose two)
Users in an organization report issues about having to remember multiple usernames and passwords. The network administrator wants the existing Cisco ISE deployment to utilize an external identity source to alleviate this issue. Which two requirements must be met to implement this change? (Choose two.)
An administrator is troubleshooting an endpoint that is supposed to bypass 802 1X and use MAB. The endpoint is bypassing 802.1X and successfully getting network access using MAB. however the endpoint cannot communicate because it cannot obtain an IP address. What is the problem?
The security team identified a rogue endpoint with MAC address 00:46:91:02:28:4A attached to the network. Which action must security engineer take within Cisco ISE to effectively
restrict network access for this endpoint?
What is the default port used by Cisco ISE for NetFlow version 9 probe?
An engineer wants to use certificate authentication for endpoints that connect to a wired network integrated with Cisco ISE. The engineer needs to define the certificate field used as the principal username. Which component would be needed to complete the configuration?
On which port does Cisco ISE present the Admin certificate for posture and client provisioning?
An administrator is configuring a Cisco WLC for web authentication Which two client profiling methods are enabled by default if the Apply Cisco ISE Default Settings check box has been selected'? (Choose two.)
What occurs when a Cisco ISE distributed deployment has two nodes and the secondary node is deregistered?
While configuring Cisco TrustSec on Cisco IOS devices the engineer must set the CTS device ID and password in order for the devices to authenticate with each other. However after this is complete the devices are not able to property authenticate What issue would cause this to happen even if the device ID and passwords are correct?
An administrator must deploy the Cisco Secure Client posture agent to employee endpoints that access a wireless network by using URL redirection in Cisco ISE. The compliance module must be downloaded from Cisco and uploaded to the Cisco ISE client provisioning resource. What must be used to upload the compliance module?
NO: 37
In which two ways can users and endpoints be classified for TrustSec?
(Choose Two.)
An engineer is configuring posture assessment for their network access control and needs to use an agent that supports using service conditions as conditions for the assessment. The agent should be run as a background process to avoid user interruption but when it is run. the user can see it. What is the problem?
An organization is adding new profiling probes to the system to improve profiling on Oseo ISE The probes must support a common network management protocol to receive information about the endpoints and the ports to which they are connected What must be configured on the network device to accomplish this goal?
What is a difference between TACACS+ and RADIUS in regards to encryption?
An engineer is configuring Cisco ISE policies to support MAB for devices that do not have 802.1X capabilities. The engineer is configuring new endpoint identity groups as conditions to be used in the AuthZ policies, but noticed that the endpoints are not hitting the correct policies. What must be done in order to get the devices into the right policies?
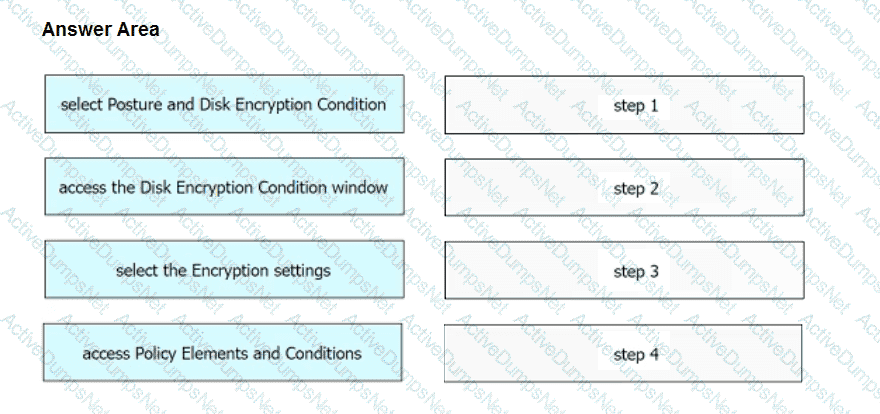
An engineer needs to configure a compliance policy on Cisco ISE to ensure that the latest encryption software is running on the C drive of all endpoints. Drag and drop the configuration steps from the left into the sequence on the right to accomplish this task.
What is the purpose of the ip http server command on a switch?
An administrator is configuring TACACS+ on a Cisco switch but cannot authenticate users with Cisco ISE. The configuration contains the correct key of Cisc039712287. but the switch is not receiving a response from the Cisco ISE instance What must be done to validate the AAA configuration and identify the problem with the TACACS+ servers?
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)
A network security administrator wants to integrate Cisco ISE with Active Directory. Which configuration action must the security administrator take to accomplish the task?
An engineer must configure Cisco ISE to provide internet access for guests in which guests are required to enter a code to gain network access. Which action accomplishes the goal?
What is a restriction of a standalone Cisco ISE node deployment?
A network administrator is currently using Cisco ISE to authenticate devices and users via 802 1X There is now a need to also authorize devices and users using EAP-TLS. Which two additional components must be configured in Cisco ISE to accomplish this'? (Choose two.)
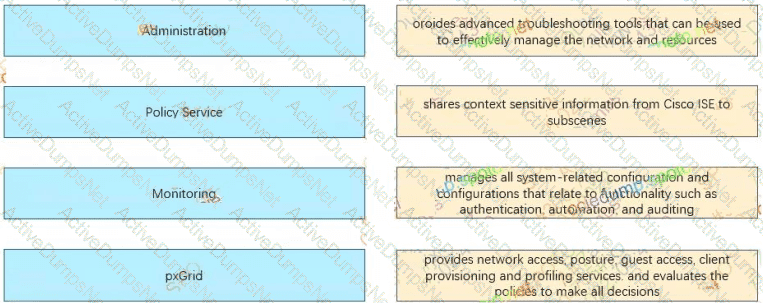
Which personas can a Cisco ISE node assume'?
A Cisco device has a port configured in multi-authentication mode and is accepting connections only from hosts assigned the SGT of SGT_0422048549 The VLAN trunk link supports a maximum of 8 VLANS What is the reason for these restrictions?
An engineer has been tasked with standing up a new guest portal for customers that are waiting in the lobby. There is a requirement to allow guests to use their social media logins to access the guest network to appeal to more customers What must be done to accomplish this task?
A Cisco ISE engineer is creating a certificate authentication profile to be used with machine authentication for the network. The engineer wants to be able to compare the user-presented certificate with a certificate stored in Active Directory. What must be done to accomplish this?
An engineer is working on a switch and must tag packets with SGT values such that it learns via SXP. Which command must be entered to meet this requirement?
Which two actions occur when a Cisco ISE server device administrator logs in to a device? (Choose two)
There is a need within an organization for a new policy to be created in Cisco ISE. It must validate that a specific anti-virus application is not only installed, but running on a machine before it is allowed access to the network. Which posture condition should the administrator configure in order for this policy to work?
An engineer is configuring 802.1X and wants it to be transparent from the users' point of view. The implementation should provide open authentication on the switch ports while providing strong levels of security for non-authenticated devices. Which deployment mode should be used to achieve this?
A Cisco ISE server sends a CoA to a NAD after a user logs in successfully using CWA Which action does the CoA perform?
An administrator needs to give the same level of access to the network devices when users are logging into them using TACACS+ However, the administrator must restrict certain commands based on one of three user roles that require different commands How is this accomplished without creating too many objects using Cisco ISE?
What are two differences of TACACS+ compared to RADIUS? (Choose two.)
TION NO: 33
Which portal is used to customize the settings for a user to log in and download the compliance module?
Select and Place
An engineer is using Cisco ISE and configuring guest services to allow wireless devices to access the network. Which action should accomplish this task?
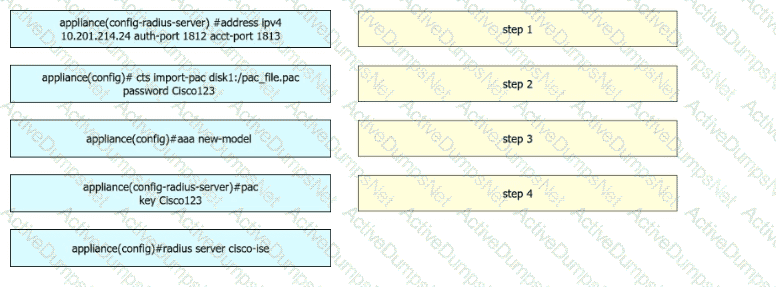
A security engineer configures a Cisco Catalyst switch to use Cisco TrustSec. The engineer must define the PAC key to authenticate the switch to Cisco IISE. Drag and drop the commands from the left into sequence on the right. Not all options are used.
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
An administrator replaced a PSN in the distributed Cisco ISE environment. When endpoints authenticate to it, the devices are not getting the right profiles or attributes and as a result, are not hitting the correct policies. This was working correctly on the previous PSN. Which action must be taken to ensure the endpoints get identified?
A network engineer must create a guest portal for wireless guests on Cisco ISE. The guest users must not be able to create accounts; however, the portal should require a username and password to connect. Which portal type must be created in Cisco ISE to meet the requirements?
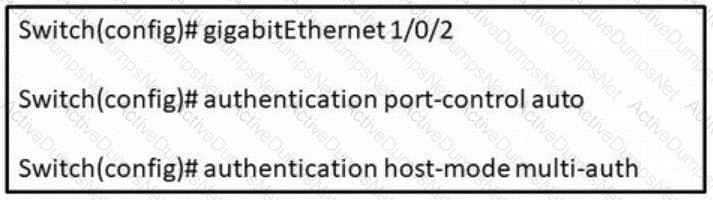
Refer to the exhibit. In which scenario does this switch configuration apply?
There are several devices on a network that are considered critical and need to be placed into the ISE database and a policy used for them. The organization does not want to use profiling. What must be done to accomplish this goal?
An engineer is implementing network access control using Cisco ISE and needs to separate the traffic based on the network device ID and use the IOS device sensor capability. Which probe must be used to accomplish this task?
What is a valid guest portal type?
Using the SAK Active Directory Federation Services server. The configurations were performed:
• created a new SAML Identity provider profile in Cisco ISE
• exported the service provider Information
• configured all the required Active Directory Federation Services configurations
• Imported the Active Directory Federation Services metadata
• configured groups in the new SAML identity
• added attributes to the new SAML identity provider profile
• configured Advanced Settings in the new SAML identity provider profile
Which two actions must be taken to complete the configuration? (Choose two.)
A network engineer is configuring Cisco TrustSec and needs to ensure that the Security Group Tag is being transmitted between two devices Where in the Layer 2 frame should this be verified?
An organization is migrating its current guest network to Cisco ISE and has 1000 guest users in the current database There are no resources to enter this information into the Cisco ISE database manually. What must be done to accomplish this task effciently?
Which default "guest type" is included with Cisco ISE?
An engineer is configuring Central Web Authentication in Cisco ISE to provide guest access. When an authentication rule is configured in the Default Policy Set for the Wired_MAB or Wireless_MAB conditions, what must be selected for the "if user not found" setting?
What is a requirement for Feed Service to work?
An administrator connects an HP printer to a dot1x enable port, but the printer in not accessible Which feature must the administrator enable to access the printer?
What happens when an internal user is configured with an external identity store for authentication, but an engineer uses the Cisco ISE admin portal to select an internal identity store as the identity source?
A network engineer must configure BYOD using Cisco ISE. In the deployment, the users must be able to submit CSR through the end devices. Which two features must be enabled to meet the requirement?
(Choose two.)
What is the minimum certainty factor when creating a profiler policy?
An administrator is configuring a Cisco ISE posture agent in the client provisioning policy and needs to ensure that the posture policies that interact with clients are monitored, and end users are required to comply with network usage rules Which two resources must be added in Cisco ISE to accomplish this goal? (Choose two)
NO: 184
An engineer builds a five-node distributed Cisco ISE deployment The first two deployed nodes are responsible for the primary and secondary administration and monitoring personas Which persona configuration is necessary to have the remaining three Cisco ISE nodes serve as dedicated nodes in the Cisco ISE cube that is responsible only for handling the RADIUS and TACACS+ authentication requests, identity lookups, and policy evaluation?
A)
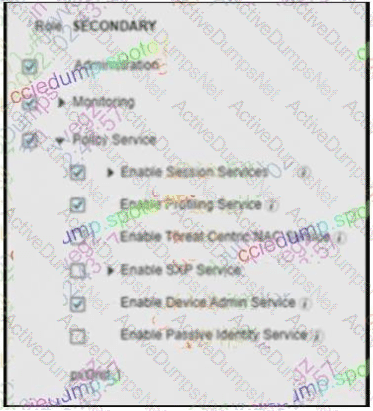
B)
C)
D)
Which two responses from the RADIUS server to NAS are valid during the authentication process? (Choose two)
Refer to the exhibit.

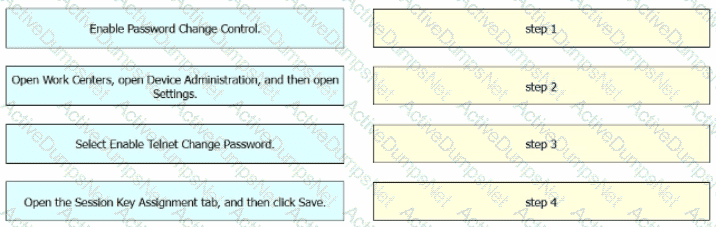
An engineer must configure Cisco ISE to be used as the TACACS+ server for any administrator that signs into the router. Users must be able to change their Telnet password through the TACACS+ server. Drag and drop the configuration steps from the left into the sequence on the right.
Refer to the exhibit:
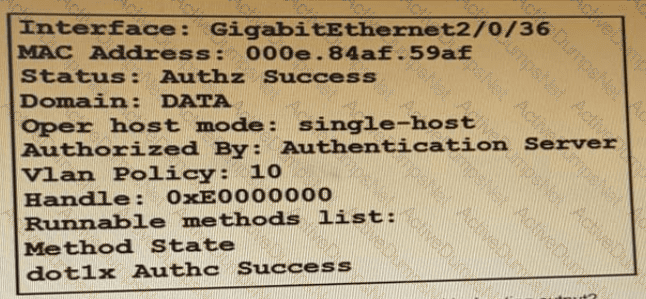
Which command is typed within the CU of a switch to view the troubleshooting output?
What is the deployment mode when two Cisco ISE nodes are configured in an environment?
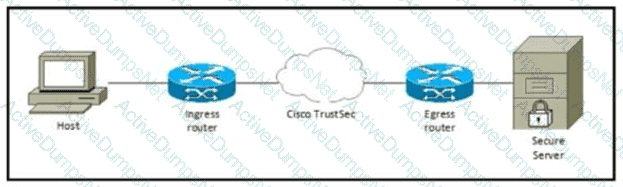
Refer to the exhibit Which component must be configured to apply the SGACL?
What is an advantage of using EAP-TLS over EAP-MS-CHAPv2 for client authentication?
An administrator needs to connect ISE to Active Directory as an external authentication source and allow the proper ports through the firewall. Which two ports should be opened to accomplish this task? (Choose two)
What is the difference between how RADIUS and TACACS+ handle encryption?
A user is attempting to register a BYOD device to the Cisco ISE deployment, but needs to use the onboarding policy to request a digital certificate and provision the endpoint. What must be configured to accomplish this task?
An administrator made changes in Cisco ISE and needs to apply new permissions for endpoints that have already been authenticated by sending a CoA packet to the network devices. Which IOS command must be configured on the devices to accomplish this goal?
Refer to the exhibit.

Which switch configuration change will allow only one voice and one data endpoint on each port?
An ISE administrator must change the inactivity timer for MAB endpoints to terminate the authentication session whenever a switch port that is connected to an IP phone does not detect packets from the device for 30 minutes. Which action must be taken to accomplish this task?




