Cisco 300-515 Implementing Cisco Service Provider VPN Services (300-515 SPVI) Exam Practice Test
Implementing Cisco Service Provider VPN Services (300-515 SPVI) Questions and Answers
How do Ethernet virtual circuits provide a way for service providers to maximize the use of VLAN tags'-1
Refer to the exhibit.
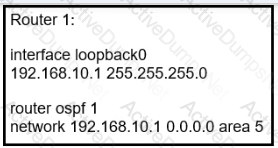
Refer to the exhibit Router 1 is a P router in the ISP MPLS core A connected P router cannot generate an MPLS label for the router 1 loopback0 interface Which action resolves this issue?
How do PE routers exchange CE routes between remote sites?
An engineer is troubleshooting AToM on an IOS XE router and receives an error when creating the xconnect. Which command does he need to complete to create the xconnect in AToM?
While troubleshooting an AToM L2VPN service, a network consultant notices that the AC Layer 2 encapsulations are different. Which action should the consultant take in order to make the MPLS L2VPN work?
A network architect is troubleshooting the L2TPv3 tunneling security due to the untrusted nature of the underlaying network. Which two L2TPv3 features does the architect deploy to address the ongoing issues? (Choose two.)
In an Ethernet Virtual Circuit environment, which restriction do bridge domains have when STP is running?
Which two statements describe primary differences between MPLS Layer 2 and Layer 3 VPNs? (Choose two.)
Which two are characteristics of using a non-MPLS peer-to-peer model over a traditional overlay model? (Choose two.)
Which condition must be met before an environment can support CSC?
