Cisco 300-215 Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Exam Practice Test
Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Questions and Answers
Refer to the exhibit.
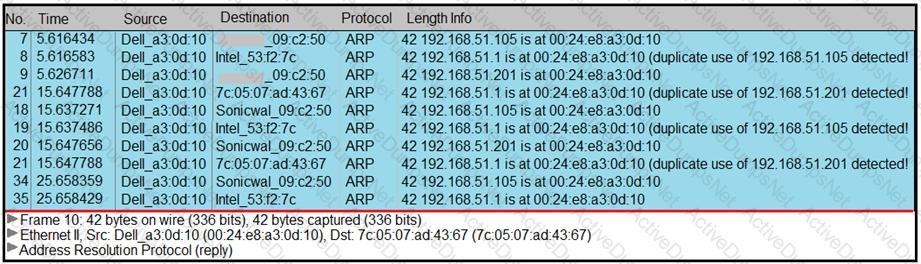
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A new zero-day vulnerability is discovered in the web application. Vulnerability does not require physical access and can be exploited remotely. Attackers are exploiting the new vulnerability by submitting a form with malicious content that grants them access to the server. After exploitation, attackers delete the log files to hide traces. Which two actions should the security engineer take next? (Choose two.)
A security team receives reports of multiple files causing suspicious activity on users’ workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
Refer to the exhibit.

An “unknown error code” is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
Refer to the exhibit.
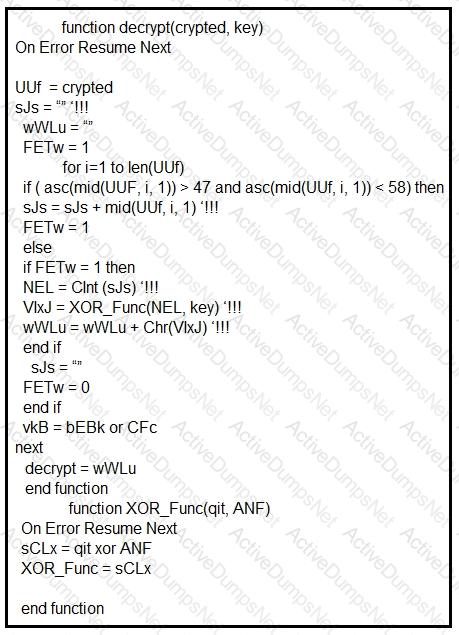
Which type of code created the snippet?
What describes the first step in performing a forensic analysis of infrastructure network devices?
A malware outbreak revealed that a firewall was misconfigured, allowing external access to the SharePoint server. What should the security team do next?
What is a use of TCPdump?
Refer to the exhibit.
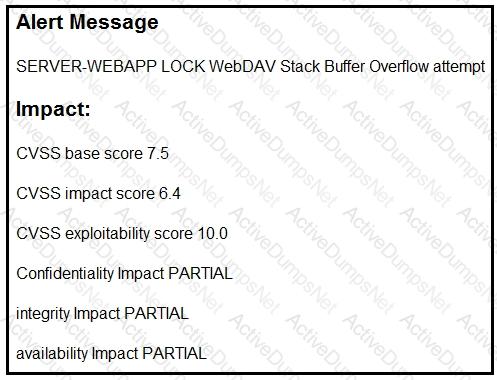
After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability. Which two mitigation techniques should the engineer recommend? (Choose two.)
A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
Refer to the exhibit.
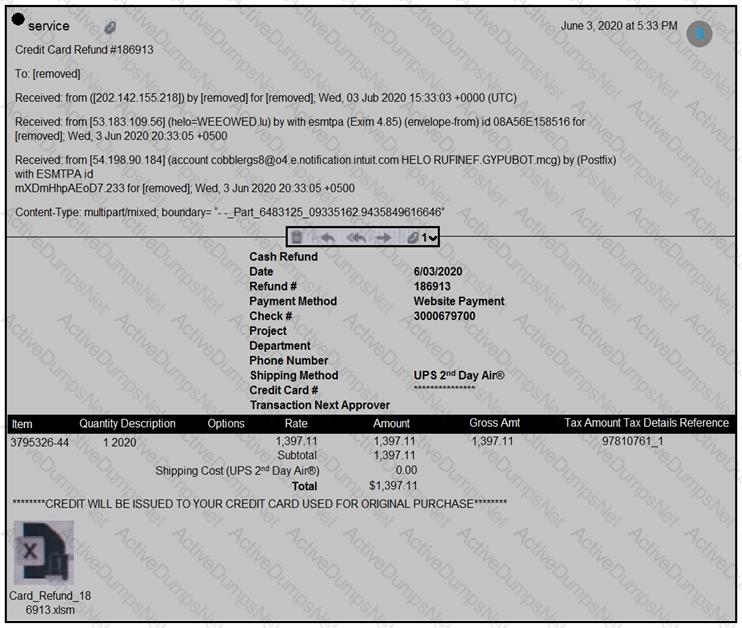
Which element in this email is an indicator of attack?
A cybersecurity analyst is examining a complex dataset of threat intelligence information from various sources. Among the data, they notice multiple instances of domain name resolution requests to suspicious domains known for hosting C2 servers. Simultaneously, the intrusion detection system logs indicate a series of network anomalies, including unusual port scans and attempts to exploit known vulnerabilities. The internal logs also reveal a sudden increase in outbound network traffic from a specific internal host to an external IP address located in a high-risk region. Which action should be prioritized by the organization?
Refer to the exhibit.
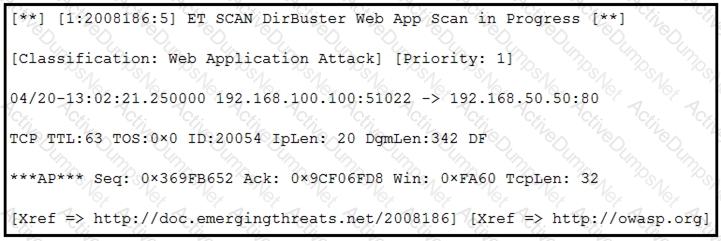
According to the SNORT alert, what is the attacker performing?
An engineer is analyzing a DoS attack and notices that the perpetrator used a different IP address to hide their system IP address and avoid detection. Which anti-forensics technique did the perpetrator use?
Refer to the exhibit.
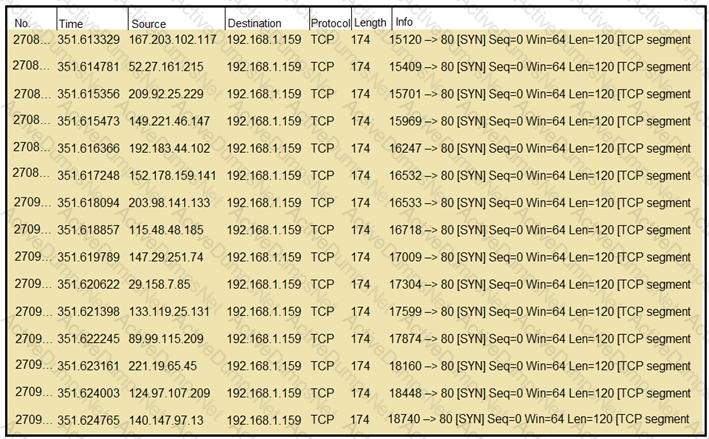
What should an engineer determine from this Wireshark capture of suspicious network traffic?
Refer to the exhibit.
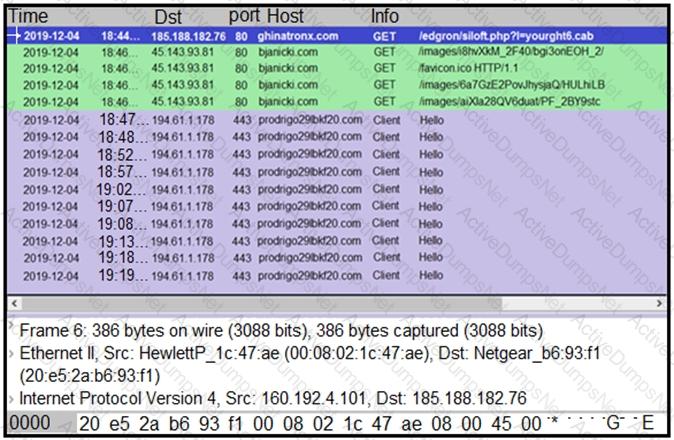
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?
What is the goal of an incident response plan?
Refer to the exhibit.
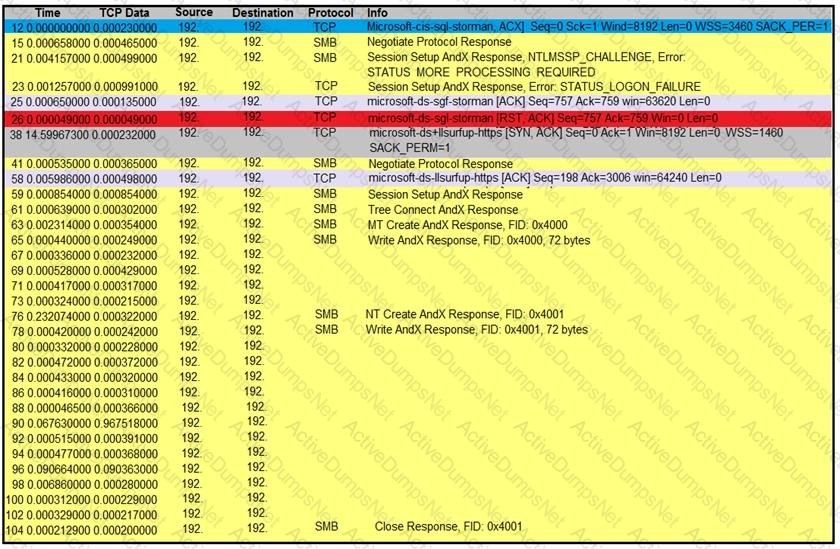
An engineer is analyzing a TCP stream in Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
An organization recovered from a recent ransomware outbreak that resulted in significant business damage. Leadership requested a report that identifies the problems that triggered the incident and the security team’s approach to address these problems to prevent a reoccurrence. Which components of the incident should an engineer analyze first for this report?
Snort detects traffic that is targeting vulnerabilities in files that belong to software in the Microsoft Office suite. On a SIEM tool, the SOC analyst sees an alert from Cisco FMC. Cisco FMC is implemented with Snort IDs. Which alert message is shown?
What is an issue with digital forensics in cloud environments, from a security point of view?
Refer to the exhibit.
What is occurring?
A scanner detected a malware-infected file on an endpoint that is attempting to beacon to an external site. An analyst has reviewed the IPS and SIEM logs but is unable to identify the file’s behavior. Which logs should be reviewed next to evaluate this file further?
A security team received an alert of suspicious activity on a user’s Internet browser. The user’s anti-virus software indicated that the file attempted to create a fake recycle bin folder and connect to an external IP address. Which two actions should be taken by the security analyst with the executable file for further analysis? (Choose two.)
Which tool is used for reverse engineering malware?
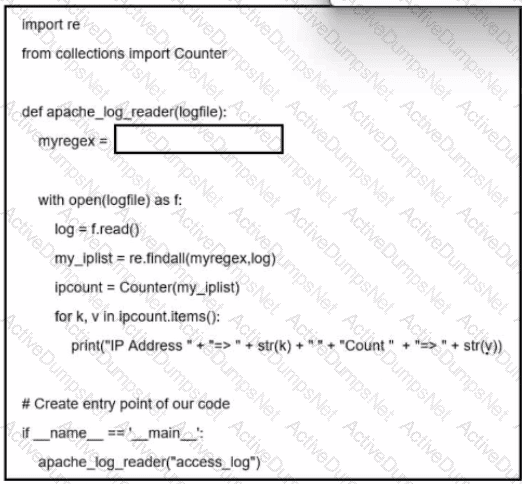
Refer to the exhibit. A network administrator creates an Apache log parser by using Python. What needs to be added in the box where the code is missing to accomplish the requirement?
Refer to the exhibit.

A security analyst is reviewing alerts from the SIEM system that was just implemented and notices a possible indication of an attack because the SSHD system just went live and there should be nobody using it. Which action should the analyst take to respond to the alert?
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
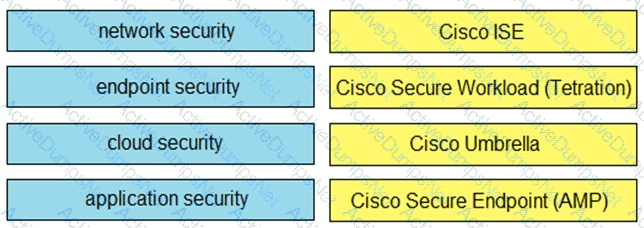
What are two features of Cisco Secure Endpoint? (Choose two.)
Refer to the exhibit.
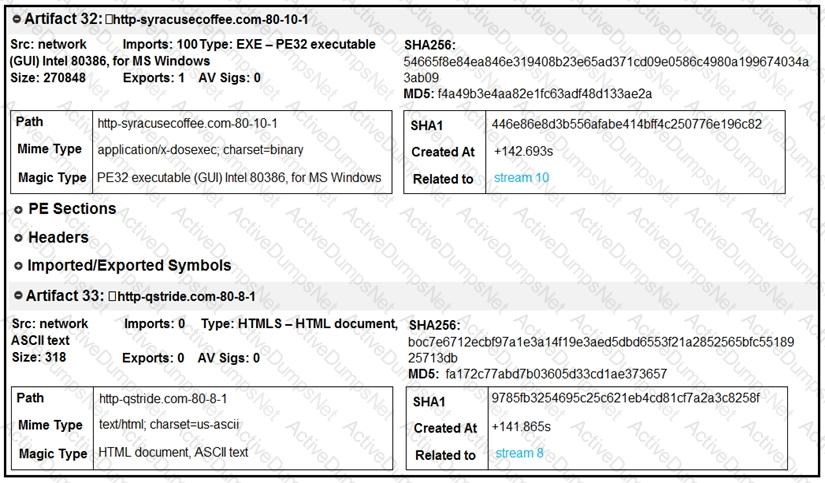
What do these artifacts indicate?
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?
An engineer must advise on how YARA rules can enhance detection capabilities. What can YARA rules be used to identify?

