Cisco 200-901 DevNet Associate (DEVASC) Exam Practice Test
DevNet Associate (DEVASC) Questions and Answers
What is a tenet of test-driven development?
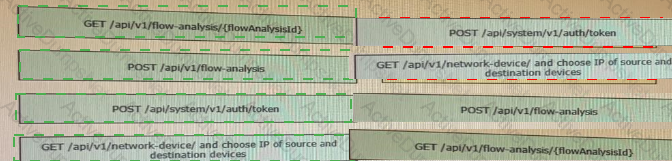
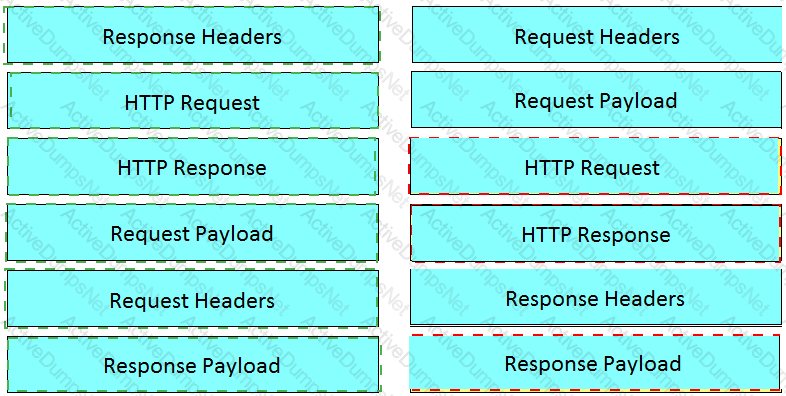
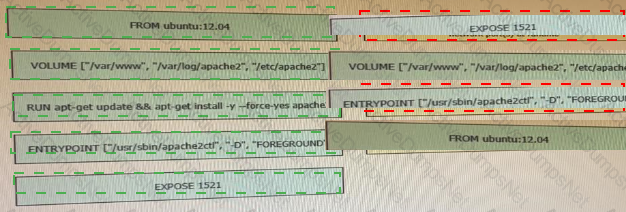
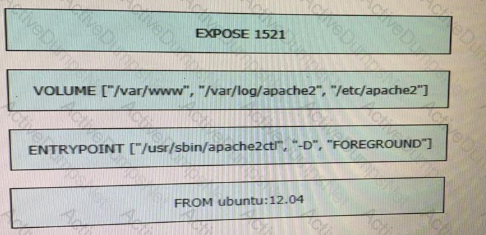
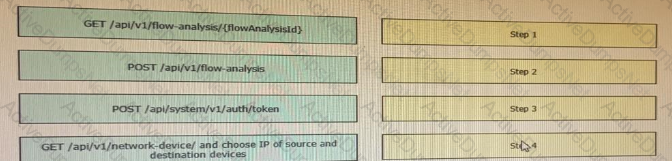
Drag and drop the requests from the left into the correct order on the right to create and check the path trace between two devices using Cisco DNA center API.
A developer is reviewing a code that was written by a colleague. It runs fine, but there are many lines of code to do a seemingly simple task repeatedly. Which action organizes the code?
Which principle is a value from the manifesto for Agile software development?
Which two concepts describe test-driven development? (Choose two.)
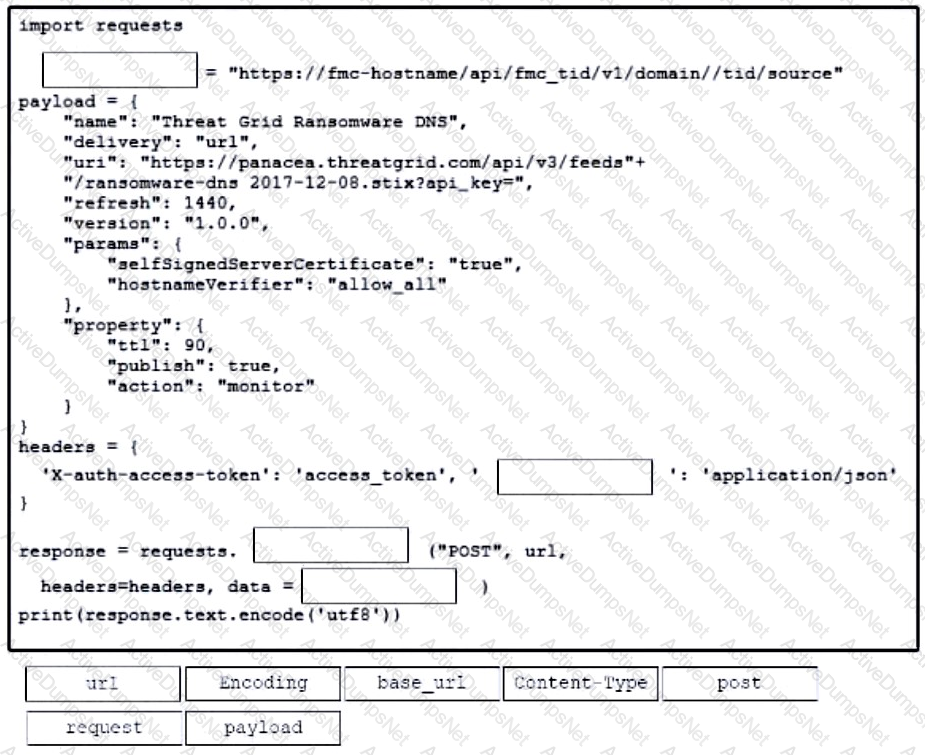
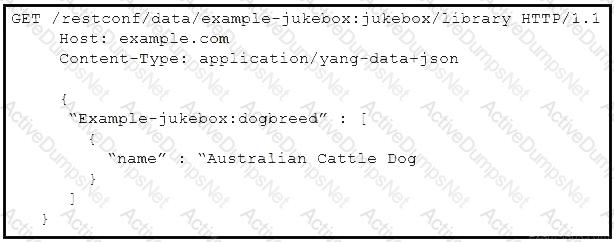
Refer to the exhibit.
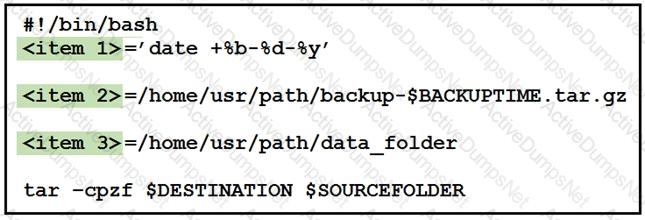
Drag and drop the variables from the left onto the item numbers on the right that match the missing assignments in the exhibit.
Which two protocols are used to apply a configuration change on a Cisco IOS XE device? (Choose two)
Which two statement describe the role of an artifact repository in a CI/CD pipeline? (Choose two.)
Which network device monitors incoming and outgoing traffic and decides whether to allow or block specific traffic based on a defined set of rules?
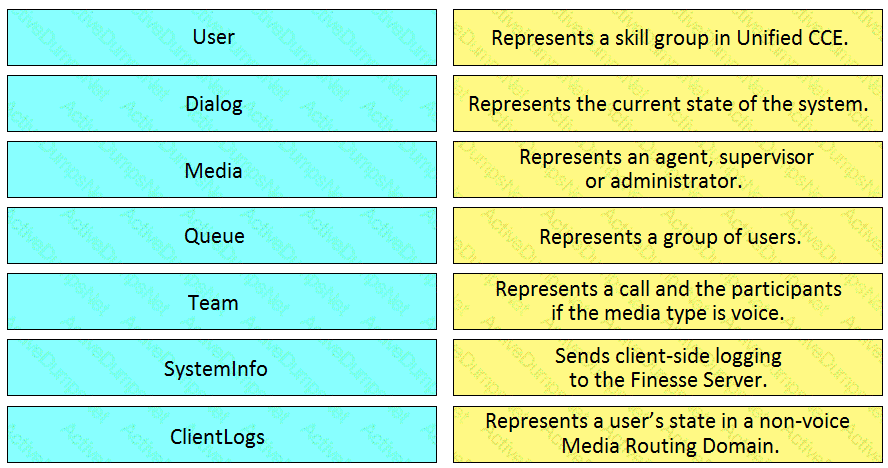
Drag and drop the element of the Finesse API on the left onto the description of its functionally on the right.
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
Which response status code is used by a RESTful interface to indicate successful execution of a request?
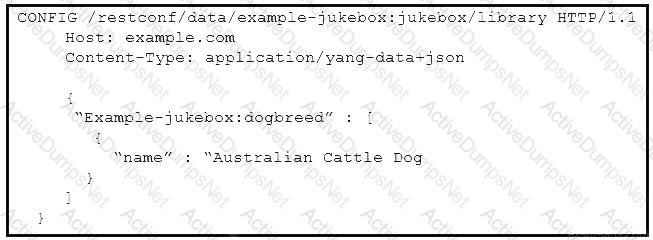
Refer to the exhibit.
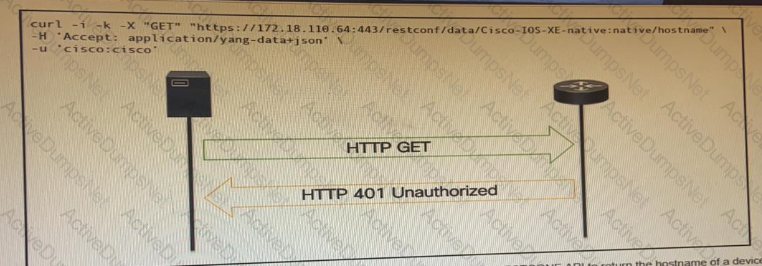
OR
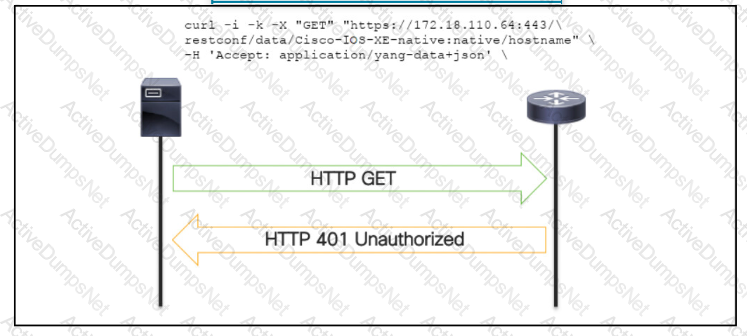
An administrator attempts to perform a GET using the Cisco IOS XE RESTOCNF API to return the hostname of a device. The sequence diagram illustrated the HTTP message observed. Which change to the API request resolves the issue?
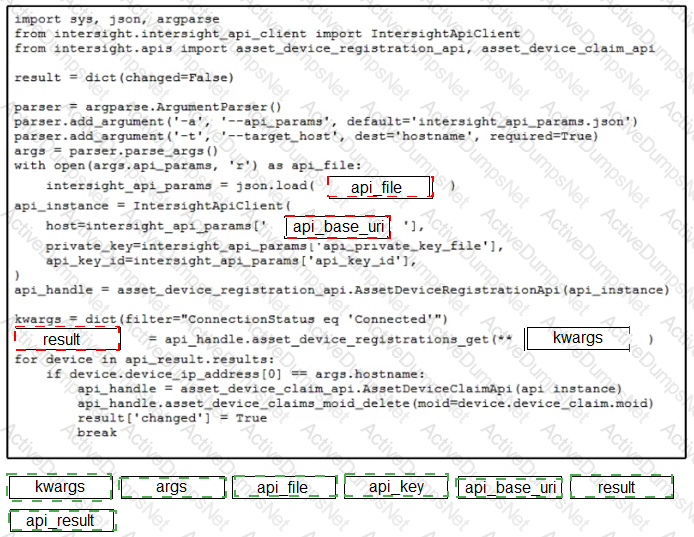
Which two statements are true about Cisco UCS manager, Cisco Intersight APIs? (Choose two.)
When a Cisco IOS XE networking device is configured using RESTCONF, what is the default data-encoding method?
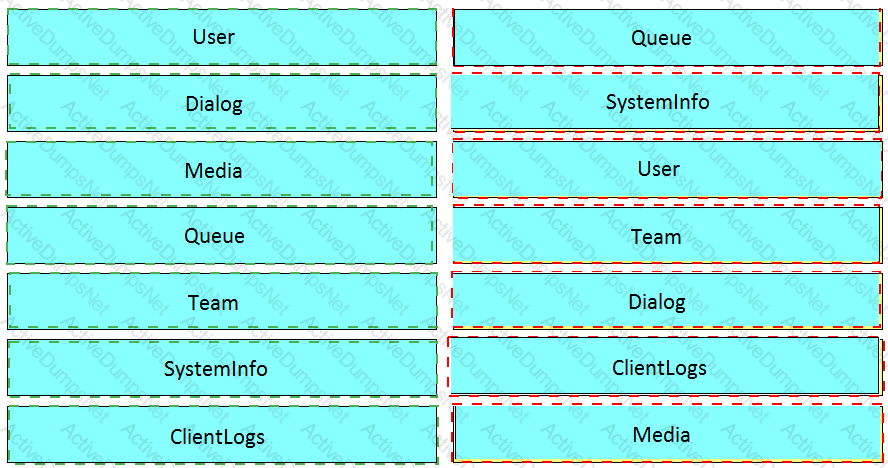
Drag and drop the network component names from the left onto the correct descriptions on the right. Not all options are used.
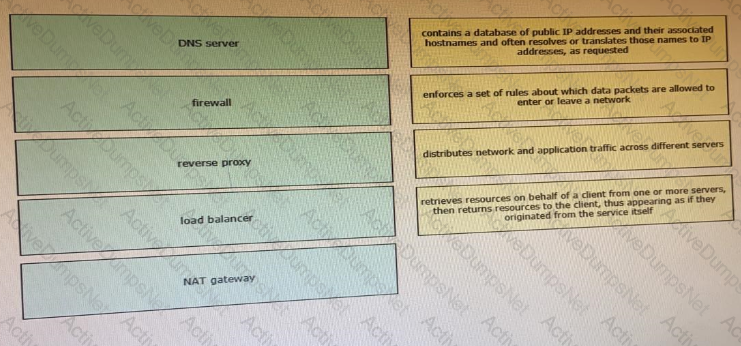
Which device is a system that monitors and controls incoming and outgoing network traffic based on predetermined security rules?
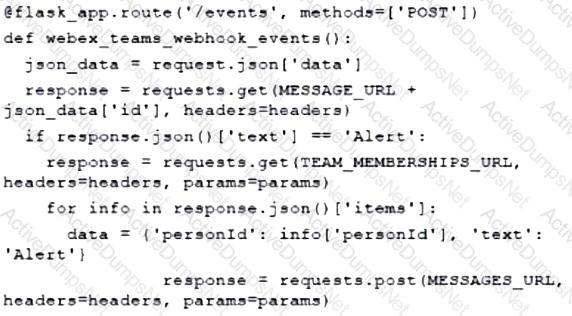
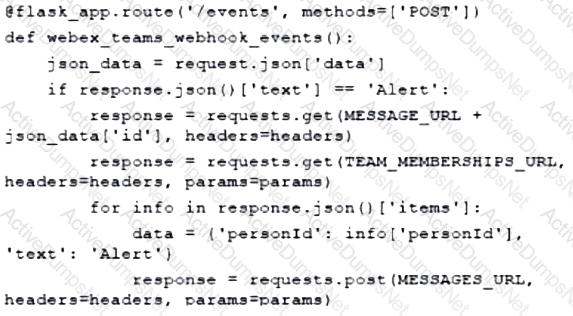
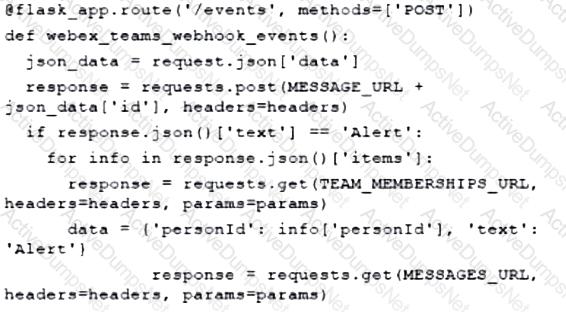
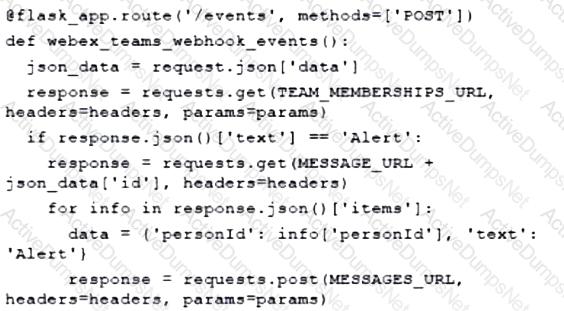
Which type of HTTP method is used by the Meraki nad webex teams APIs to send webhook notifications?
what is an advantage of a version control system?
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
Which task is performed because the test-driven development approach is being used?
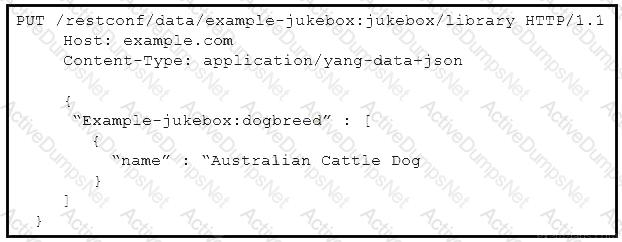
Refer to the exhibit.
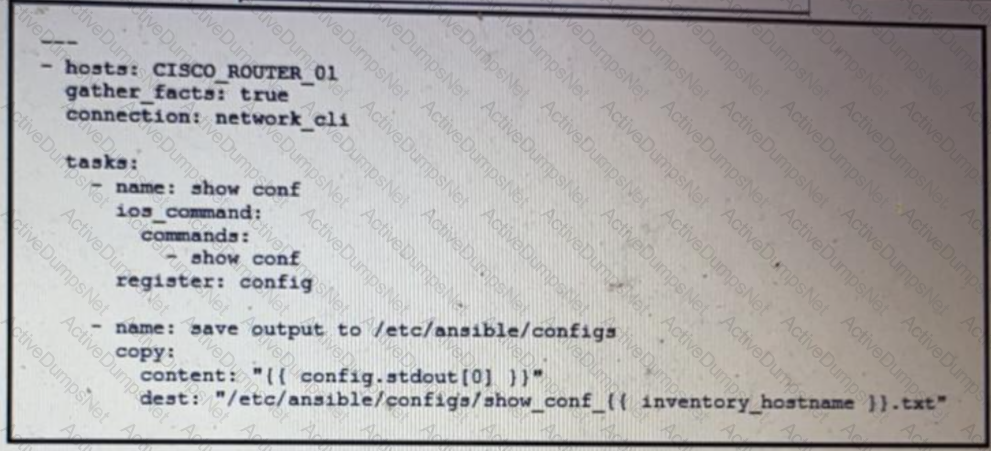
What is the result of executing this Ansible playbook?
Which action resolves a 401 error in response to an HTTP GET that is issued to retrieve statement using RESTCONF on a CSR 1000V?
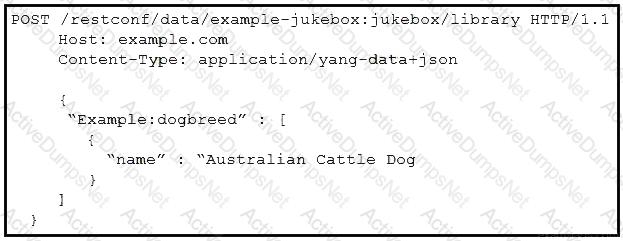
Refer to the exhibit.
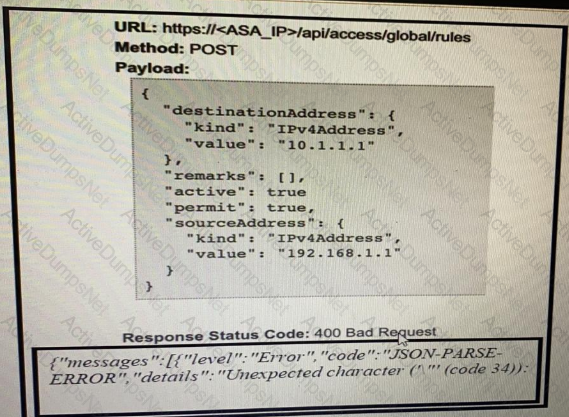
What caused the error in this API request?
Refer to the exhibit.
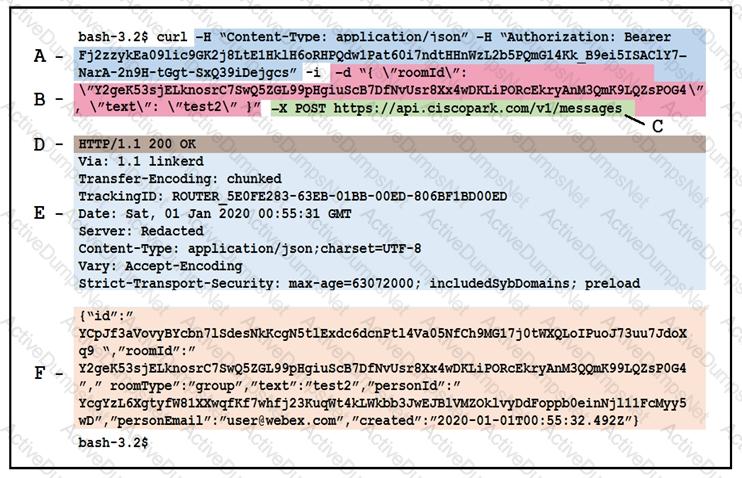
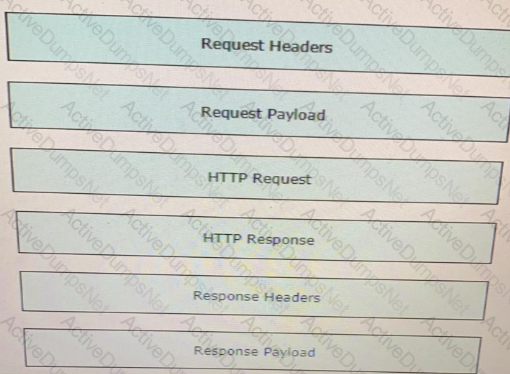
Drag and drop the descriptors from the left onto the correct parts of the API request and response on the right.
Refer to the exhibit.
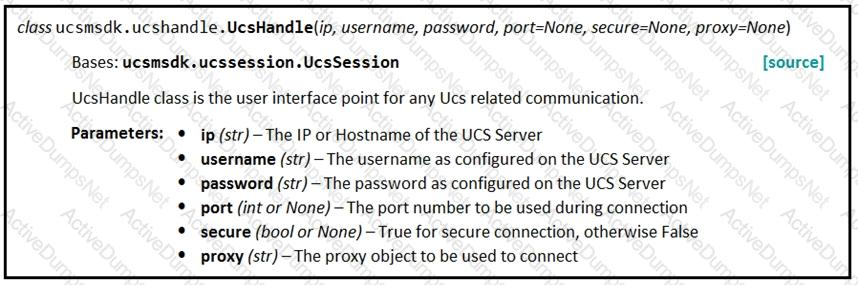
Given the API documentation for the UCS SDK python class, UcsHandle, which code snippet creates a handle instance?
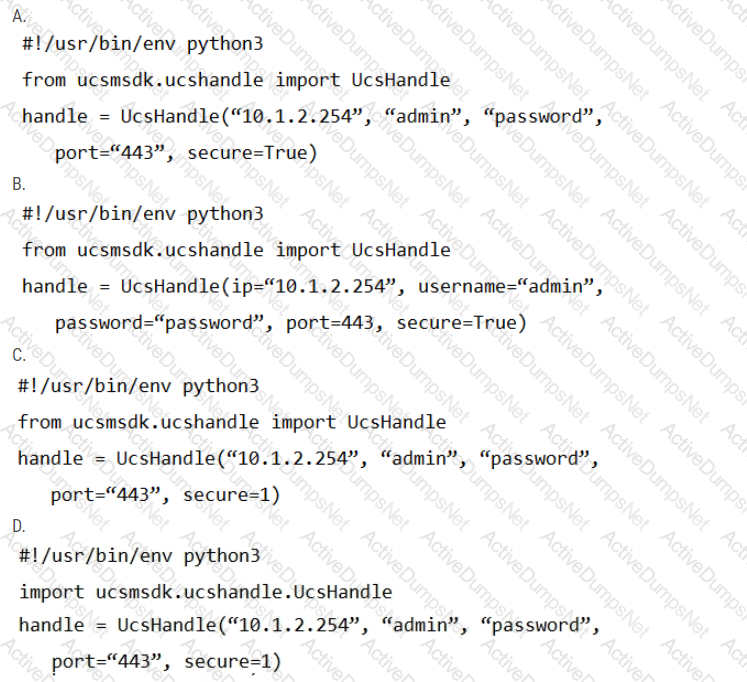
Refer to the exhibit.
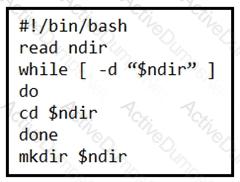
What is the action of the Bash script that is shown?
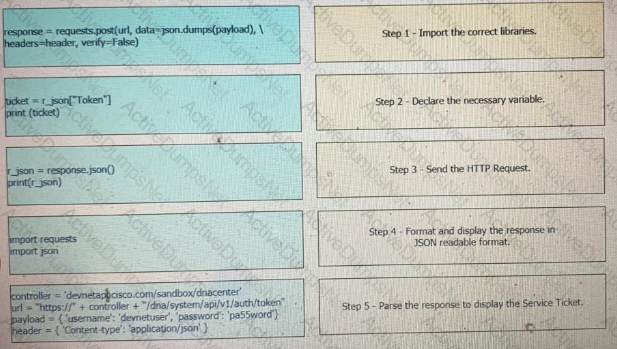
Drag and drop the Python code from the left onto the correct step on the right to call a REST API.
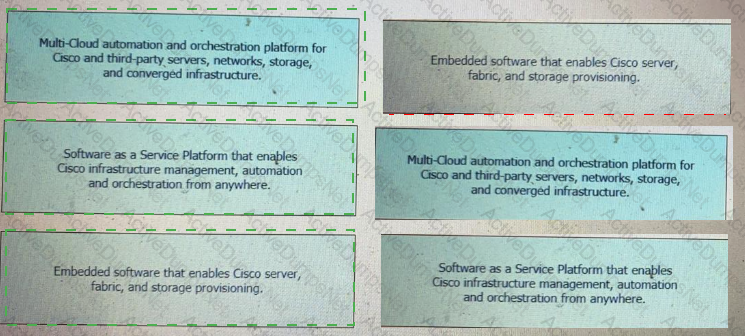
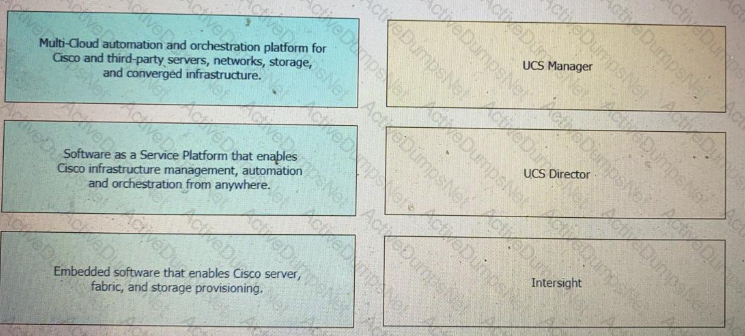
Drag and drop the capability on the left onto the Cisco compute management platform that supports the capability on the right.
Refer to the exhibit.
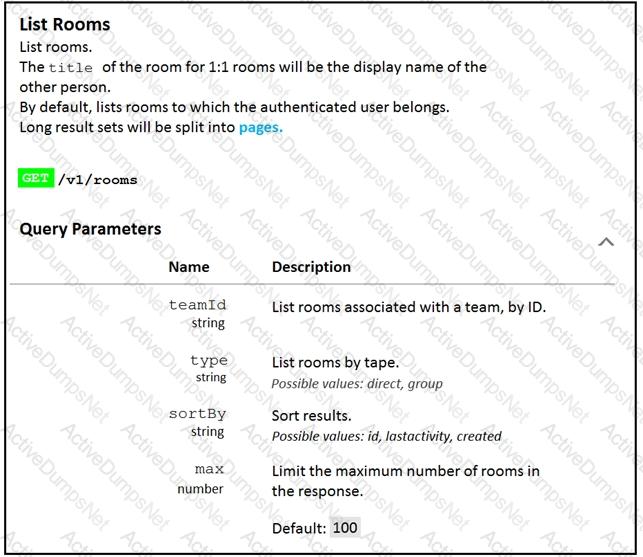
Fill in the blank to complete the query parameter and value so that the result set is returned in reverse chronological order (most recent first) based on when message were entered.

Which REST architectural constraint indicates that no client context should be stored on the server between requests?
Refer to the exhibit.
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
Which platform has an API that be used to obtain a list of vulnerable software on user devices?
Refer to the exhibit.
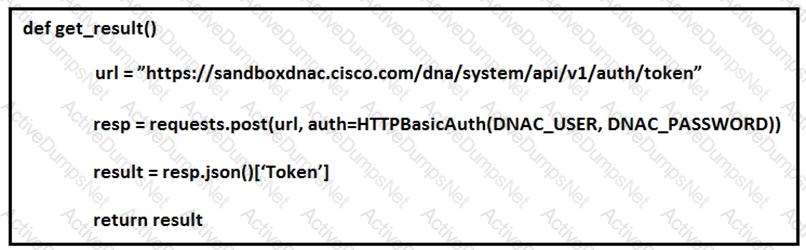
What does the python function do?
Users cannot access a webserver and after the traffic is captured. the capture tool shows an ICMP packet that reports "time exceeded in-transit". What is the cause of this webserver access issue?
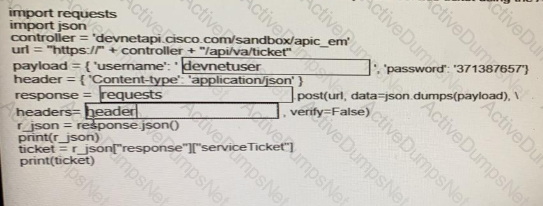
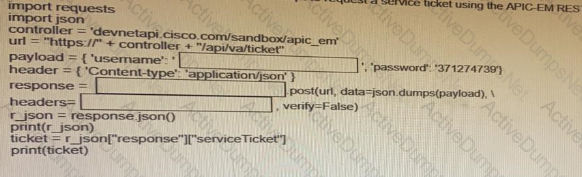
Fill in the blanks to complete the python script to request a service ticket using the APIC-EM rest API for the user “devnetuser”.
An application calls a REST API and expects a result set of more than 550 records, but each time the call is made, only 25 are returned. Which feature limits the amount of data that is returned by the API?
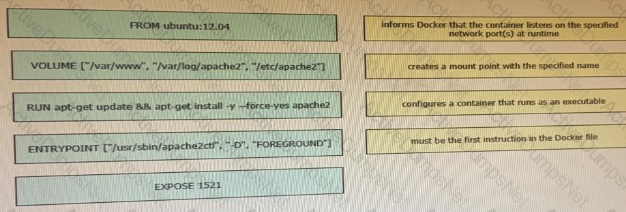
Drag and drop the Docker file instructions from the onto correct descriptions on the right. Not all options are used.
Which description of a default gateway if true?
Refer to the exhibit.
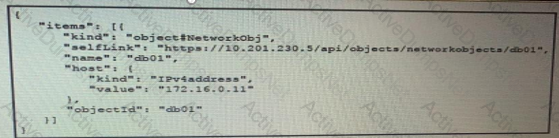
The JSON data in the exhibit has been parsed and stored in a variable, “data”. What returns the value “172.16.0.11” ?
What is a function of the default gateway in a network?
Which is an advantage of using network programmability?
Which model-driven programmability protocol does Cisco IOS XE Software support?
Refer to the exhibit.
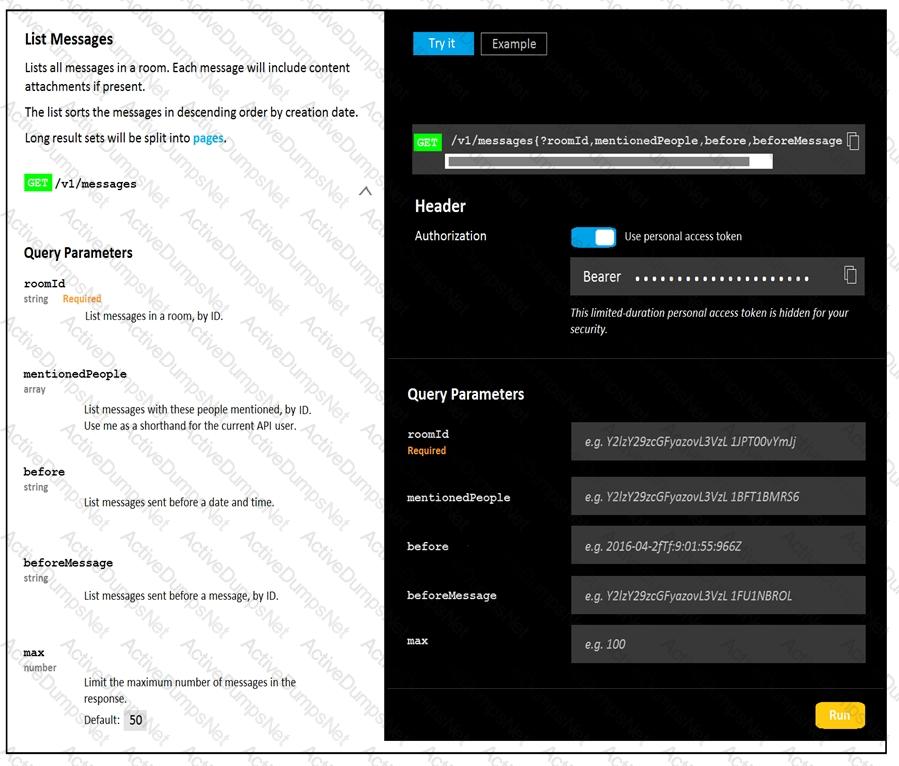
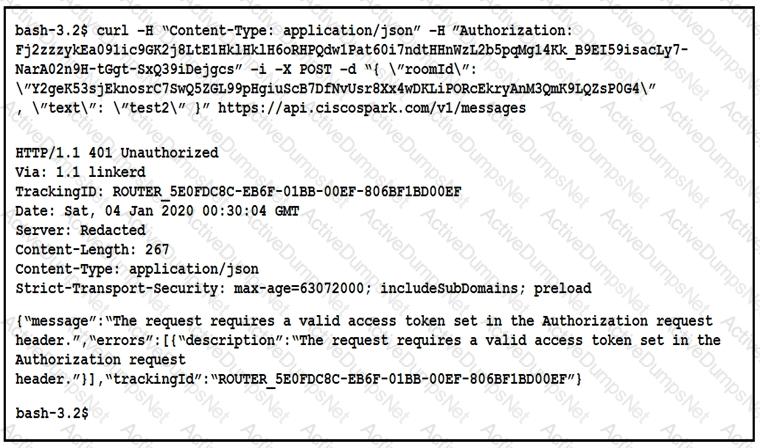
A developer is troubleshooting an API with the given API with the given API documentation and cURL command. What is the cause of this problem?
Which two items are Cisco DevNet resources? (Choose two.)
Refer to the exhibit.
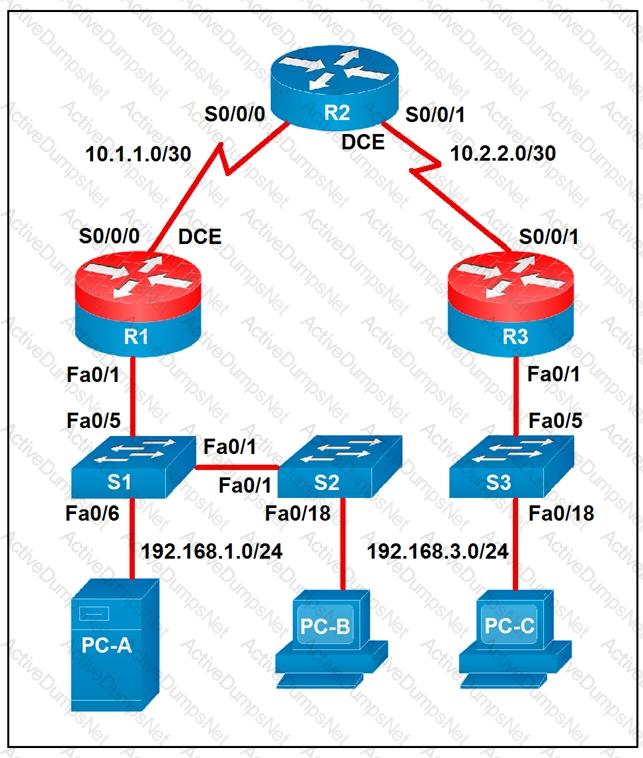
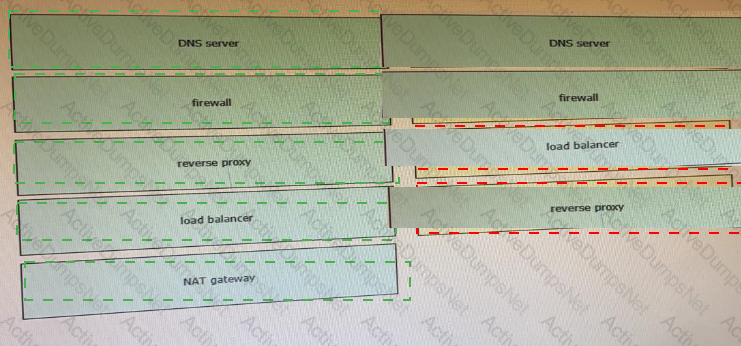
Which two statements about the network diagram are true? (Choose two.)
What is the purpose of a MAC address?
What is a capability of an agentless configuration management system?
Refer to the exhibit.

A developer must integrate a bot with an internal communication app. The developer wants to replace the webexbot package with the teamsbot package by using Ansible and prepares a playbook In the first two tasks, the playbook stops the webexbot and verifies that the teamsbot is installed. What is accomplished in the last task of the workflow when the developer runs the Ansible playbook?
A developer creates a script that configured multiple Cisco IOS XE devices in a corporate infrastructure. The internal test environment is unavailable, and no maintenance window is available to test on a low-priority production environment. Which resource is used to test the code before it is applied to the production environment?
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario?
How do XML and JSON compare regarding functionality?
Refer to the exhibit.

A network engineer must change the configuration on devices daily. The Python script must collect CLI arguments from the user, organize data according to the Cisco-IOS-XE-native YANG model, and utilize Cisco REST APIs to make the configuration. Which workflow is being automated by the Python script?
Refer to the exhibit.

The script returns an output of 401. To use the supplied URL. an HTTP GET request must Be sent with an Authorization header. The header value is a BaseG4 encoded concatenation of the username and password. Which action must be taken to return an output of 200?
What are two benefits of using VLANs? (Choose two.)
Refer to the exhibit.

An engineer writes a Python script that uses two different API calls to query Cisco DNA Center for the number of interfaces on a device. The engineer notices that the two API calls produce different results. Why are fewer interfaces returned for the same device when the 'get_all_interfaces' API call is used?
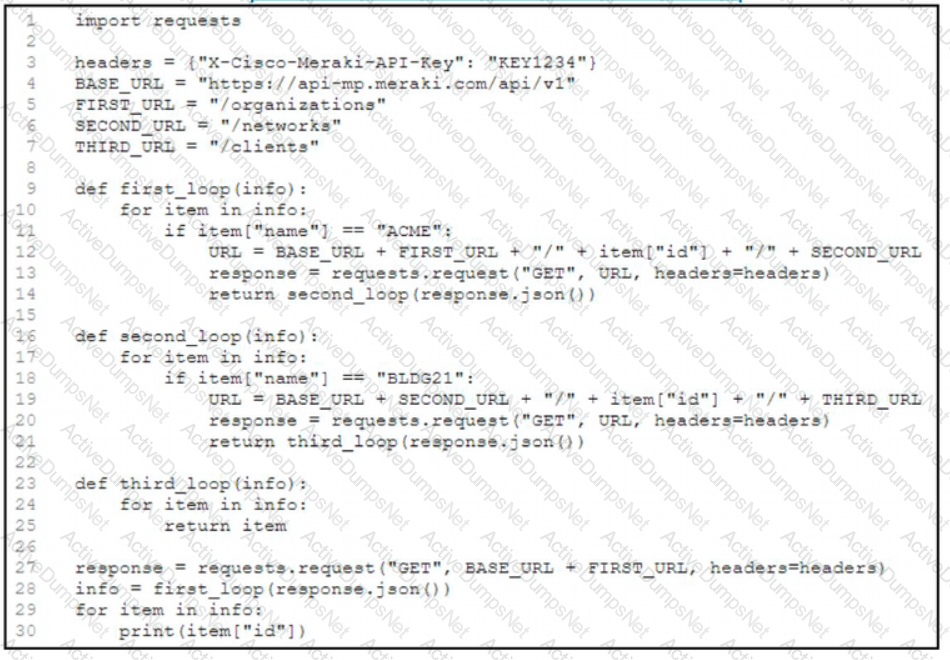
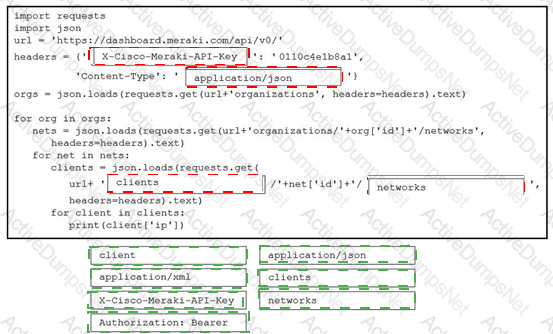
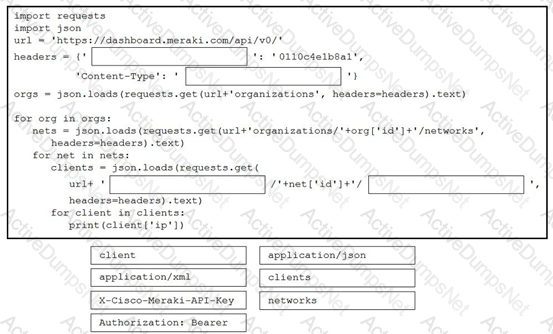
Refer to the exhibit. A network engineer must collect information from the network. The engineer prepares a script to automate workflow by using Cisco Meraki API. The script must run over nested loops to collect organization and network information and uses the collected data for final collection. Which process is being automated by using the Python script?
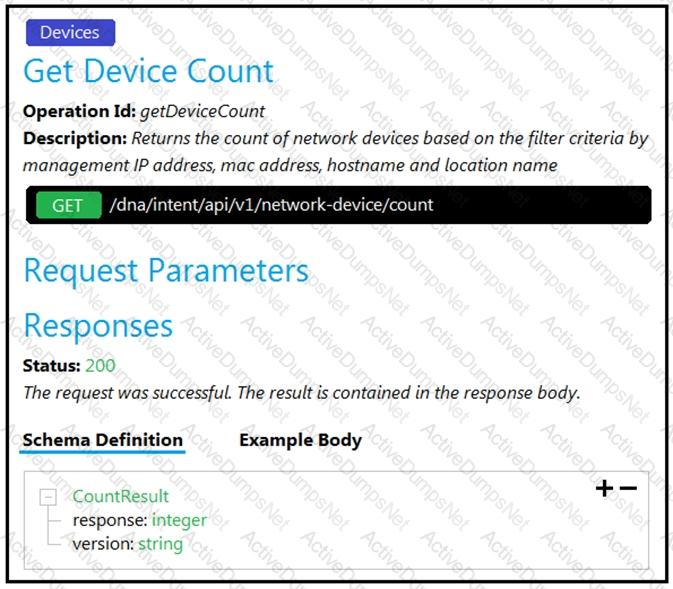
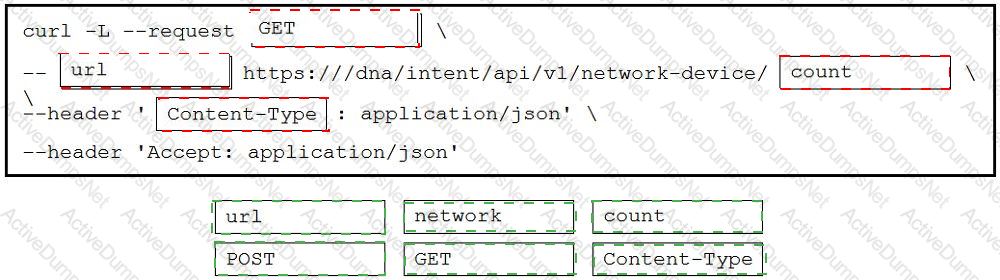
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to construct a request to find the Cisco DNA Center switch count. Not all options are used.
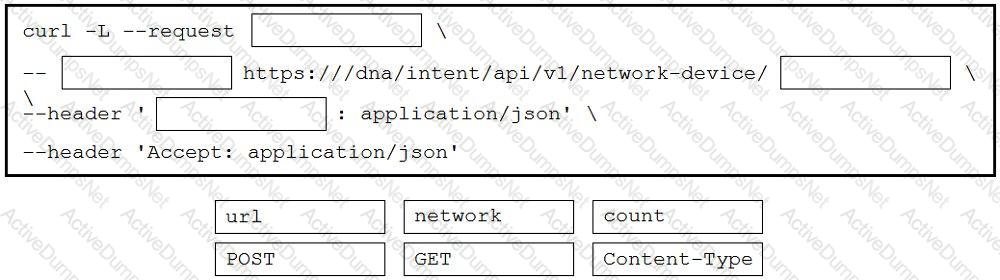
Which HTTP response status code means “Forbidden”?
Which application should be used to externally access all applications deployed in the same host machine with a single public IP address and port, when each application listens on different local ports?
Why is refactoring done during test-driven development?
What are two benefits of model-driven programmability?
A developer created a new secure API and is testing the functionality locally. The API was added to a container for further testing, and other team members and applications need to connect to the API. Which command exposes the API in the container as port 8443 and allows connections external to the host?
Refer to the exhibit.
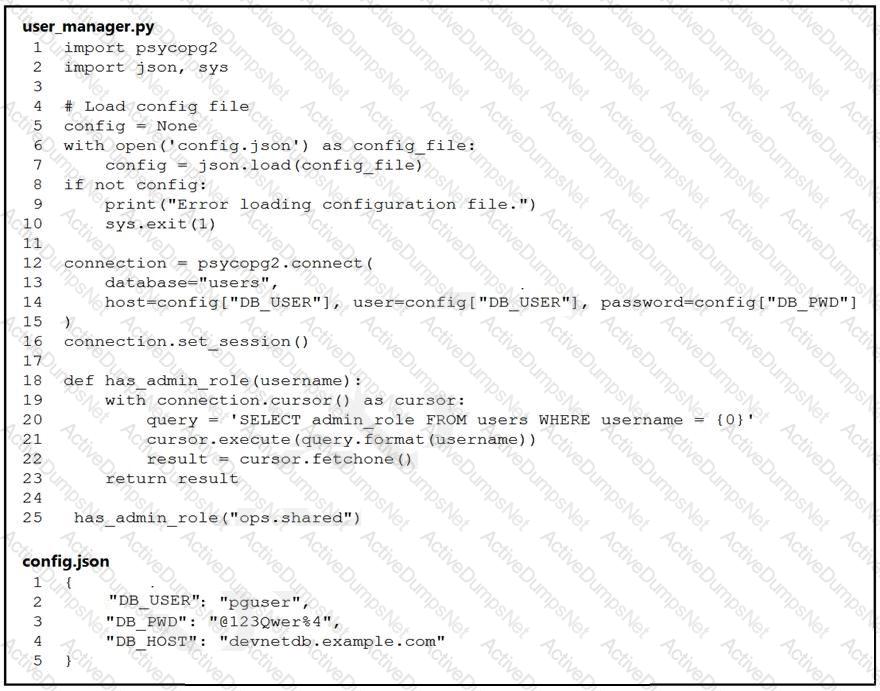
An engineer must check the admin rights of users on a database regularly and prepares
the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection?
What is a benefit of organizing code into modules?
Which Cisco platform provides organization-wide automation, security, policy enforcement, any agility across wired and wireless networks?
What is a benefit of organizing into modules?
Refer to the exhibit.

A Python code has been written to query a device. The executed code results in the error shown. Which action resolves the problem?
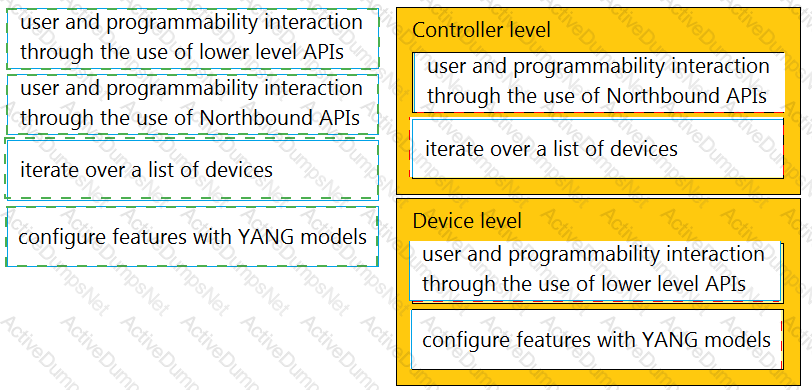
Drag and drop the types of management from the left onto the levels at which they are performed on the right.
Before which process is code review performed when version control is used?
Several teams at a company are developing a new CRM solution to track customer interactions with a goal of improving customer satisfaction and driving higher revenue. The proposed solution contains these components:
• MySQL database that stores data about customers
• HTML5 and JavaScript UI that runs on Apache
• REST API written in Python
What are two advantages of applying the MVC design pattern to the development of the solution? (Choose two.)
Refer to the exhibit.
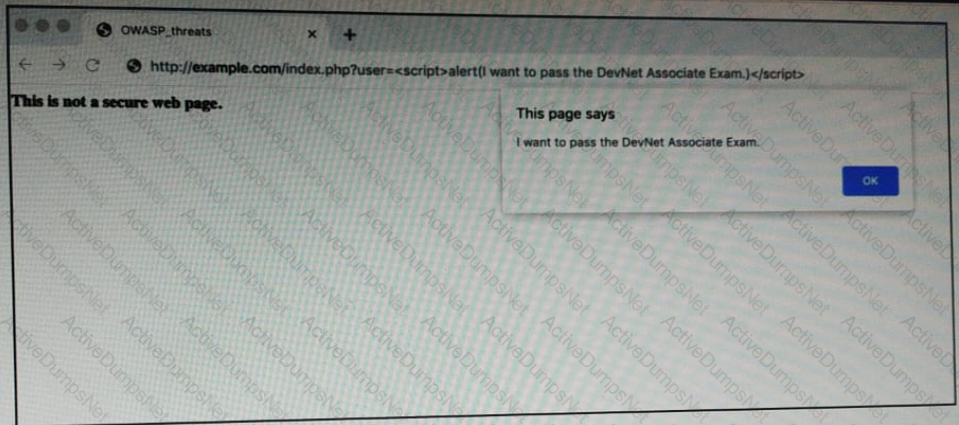
OWASP threat does this example demonstrate?
Which platform is used to programmatically create a space and invite users for collaboration?
Refer to the exhibit.
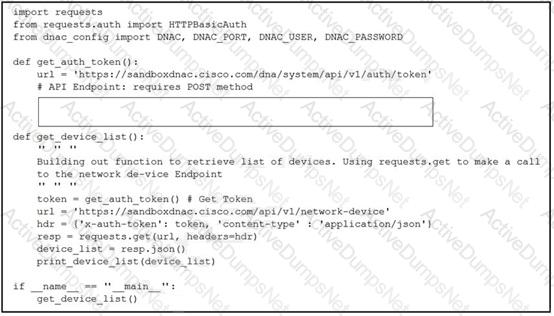
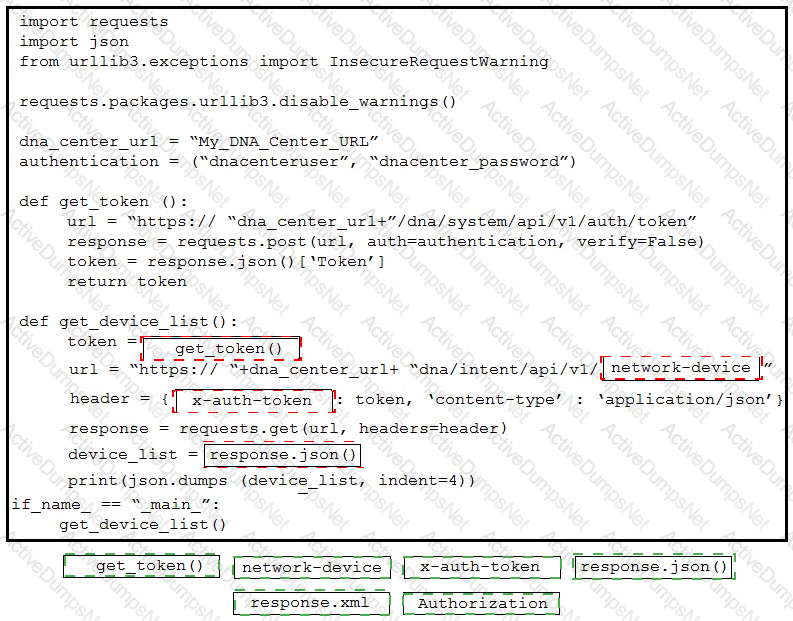
A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function?
A developer needs a list of clients connected to a specific device in a Meraki network. After making a REST API call, the developer receives an unfamiliar response code. Which Cisco DevNet resource should be used to identify the meaning of the response code?
Refer to the exhibit.
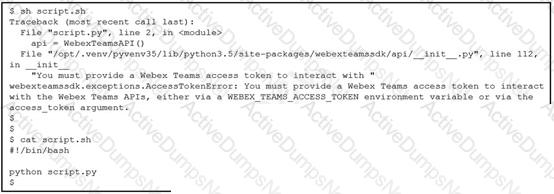
Which line must be included in the Bash script for the Python code to succeed?
Which HTTP code group is issued when a request is received successfully, understood, and processed?
A file that already exists in a local repository is updated. Which command must be executed to ensure that the changes in the file are included in the next Git commit?
Refer to the exhibit.
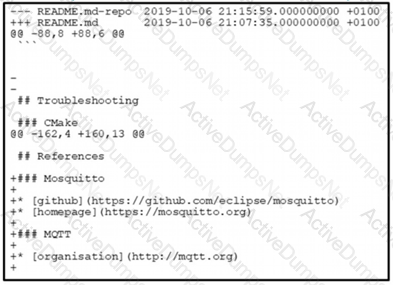
The output of the diff-u README.md-repo README.md command is shown. The original file was 165 lines long How many lines are in the edited copy of the file?
Where is an IP packet routed if the packet does not match any routes in the routing table?
Refer to the exhibit.

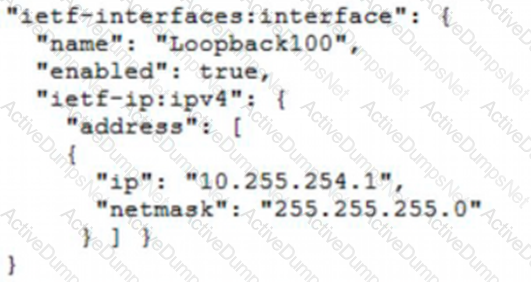
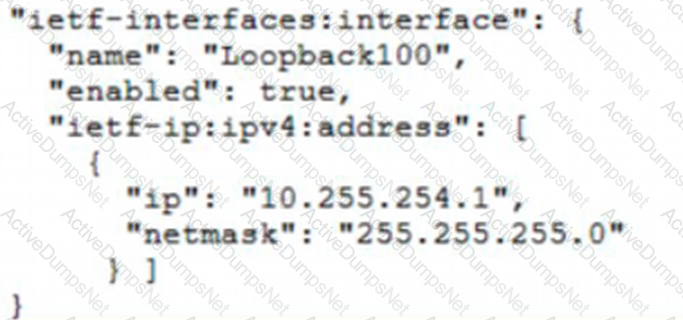
Which JSON snippet configures a new interface according to YANG model?
A)
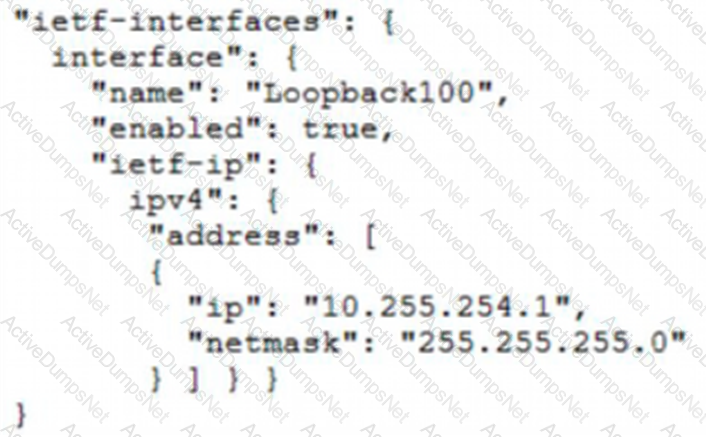
B)
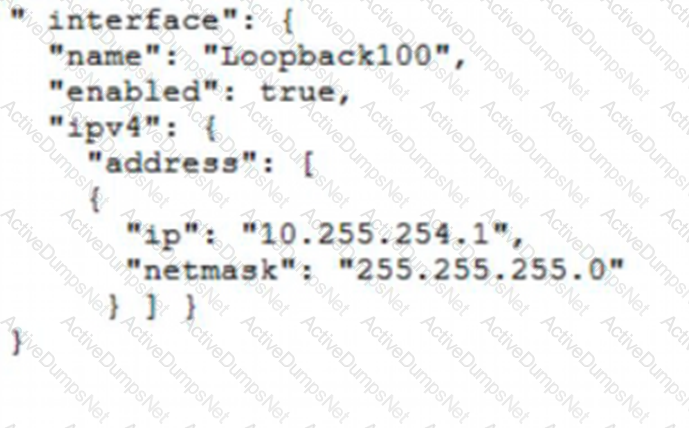
C)
D)
While developing a real-Time VoIP application on a Cisco Webex platform, users report that their voice gets chopped or parts of the conversation drop out. Which network constraint is impacting the application?
Drag and drop the code from the bottom onto the box where the code is missing in the Python script to complete a function to return all the clients on a network by using the Cisco Meraki Dashboard API. Not all options are used.
How does a synchronous API request differ from an asynchronous API request?
Which implementation creates a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire?
Which HTTP response code should be returned when the request is completed, but there is no content to send for the request?
Which tool allows changes to the configuration management toolset to be tested?
Refer to the exhibit.
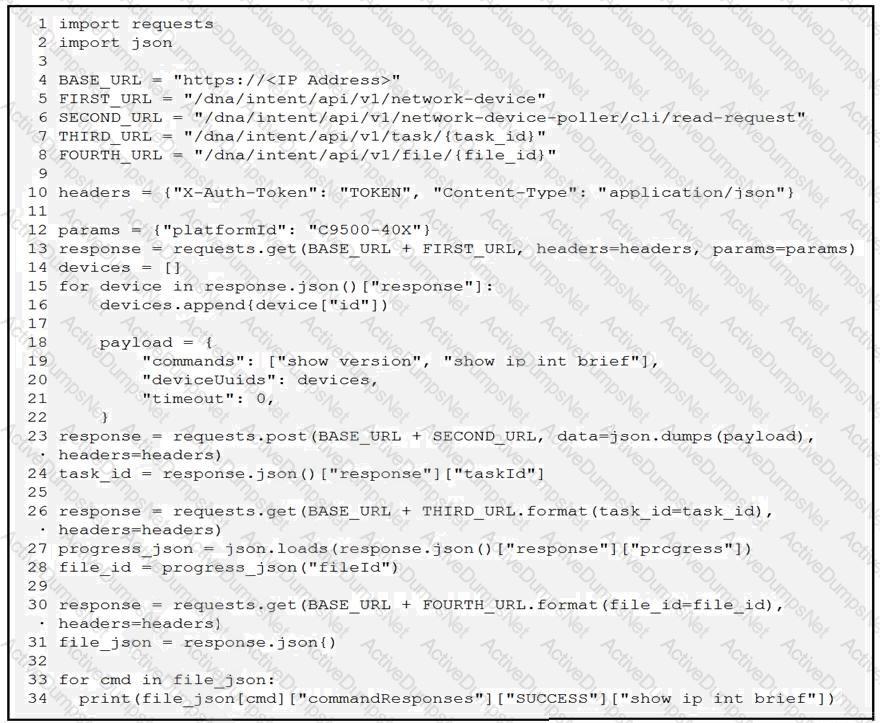
A network engineer must collect information from the network using Cisco DNA Center APIs. The script must query for the devices with 'platformId' 'C9540-x' and then send commands to be executed. Which process is automated by the Python script?
Refer to the exhibit.
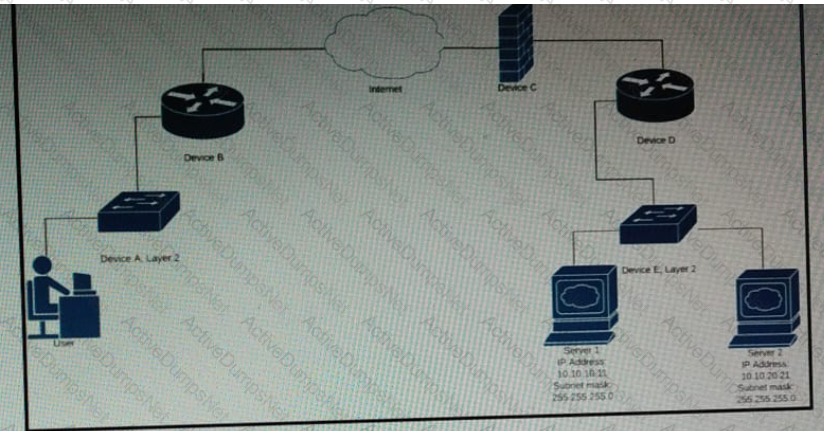
Which device limits traffic between server 1 and server 2?
What are two considerations when selecting the "best route" for a network device to reach its destination? (Choose two.)
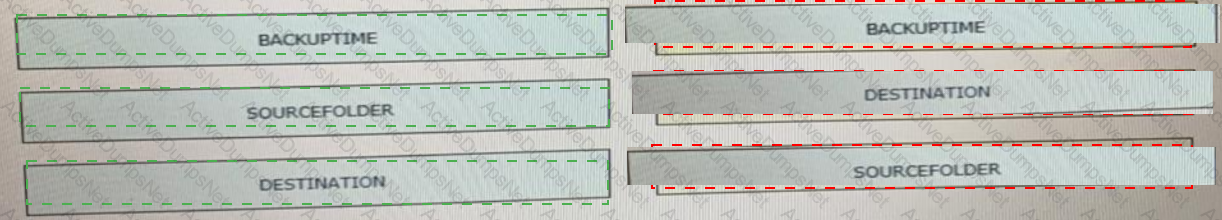
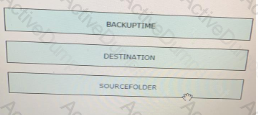
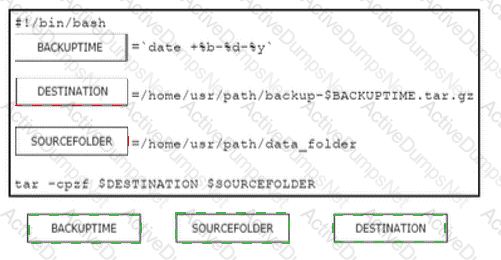
Drag and drop the code from the bottom onto the box where the code is missing in the Bash script to complete the missing assignment.
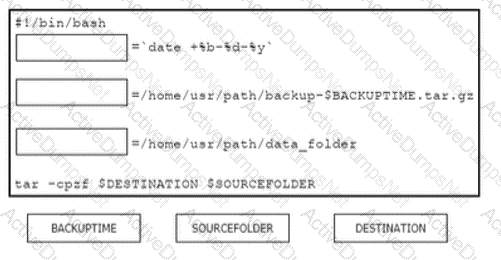
A developer is working on a feature for a new application. The changes in the existing branch named 'feat00304' must be integrated into a single commit with the current working primary branch named 'prodapp411926287'. Which git command must be used?
What is the difference between YAML and JSON data structure?
Refer to the exhibit.
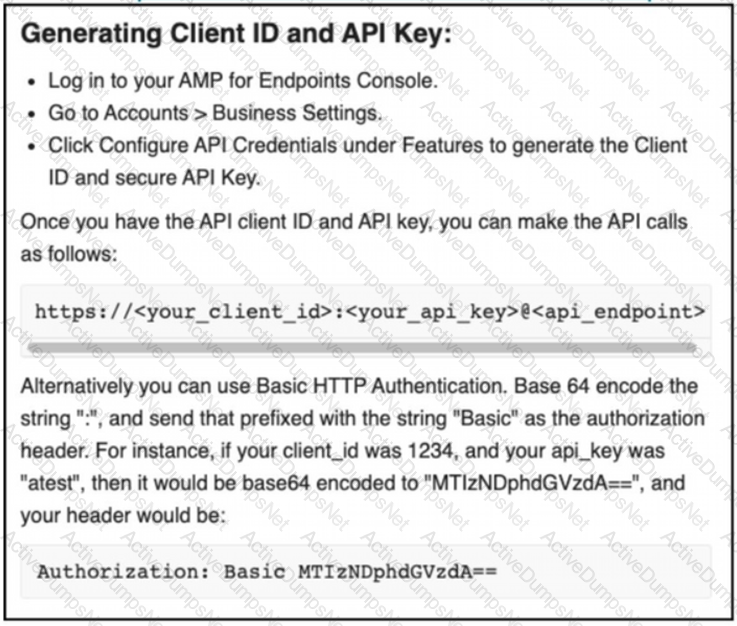
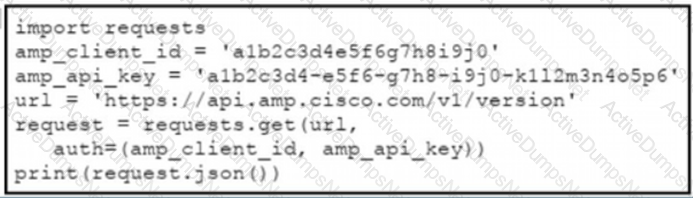
The documentation outlines how to use credentials for the AMP API Which script successfully performs an API call using basic authentication?
A)
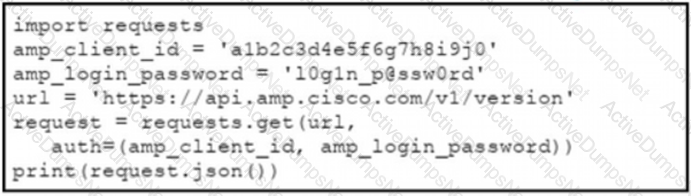
B)
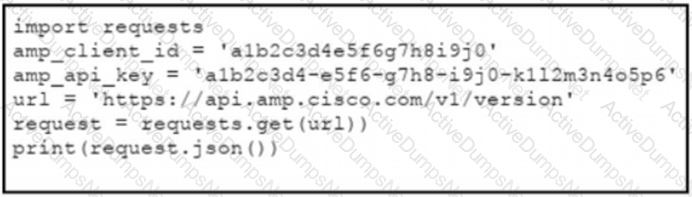
C)
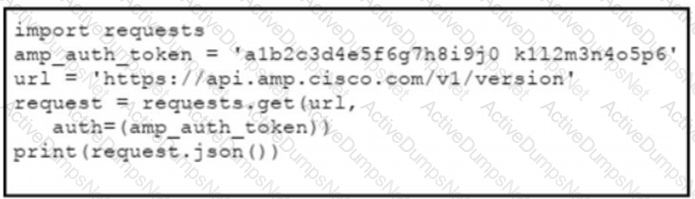
D)
Which technology is responsible for resolving a host name to an IP address?
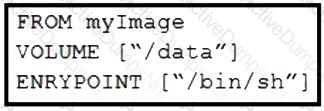
Refer to the exhibit. Drag and drop the actions from the left that the contents of this Dockerfile accomplish onto the right. Not all options are used.
Which protocol is used for clock synchronization between network devices?
What is a characteristic of Waterfall compared to Agile software development method?
An engineer deploys a Cisco CSR 1000 V instance to a virtual machine. The engineer must output the device configuration in JSON format. Which protocol is used for this task?
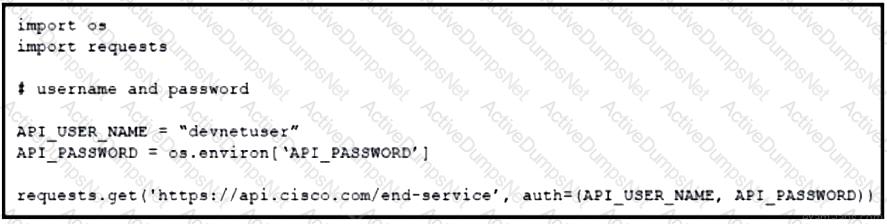
Refer to the exhibit. An engineer must authorize a REST API call. The API password is "Cisco123!". Which Bash command must be placed in the code to authorize the call?
Which action do webhooks enable an application to perform?
A developer is developing a web application that uses username and password to authenticate to the next service. The user credentials must be available at any time in the application. The developer must choose and implement a secure method of storing the authentication credentials that are used in the automation code. Which password handling method must be used to minimize the security risk?
What is a benefit of using a code review process in application development?

Refer to the exhibit. A network engineer must copy the “config.txt” file from directory TEST to directory PROD. The copied file must also be renamed into “current.txt”. Which command must be used to accomplish these tasks?
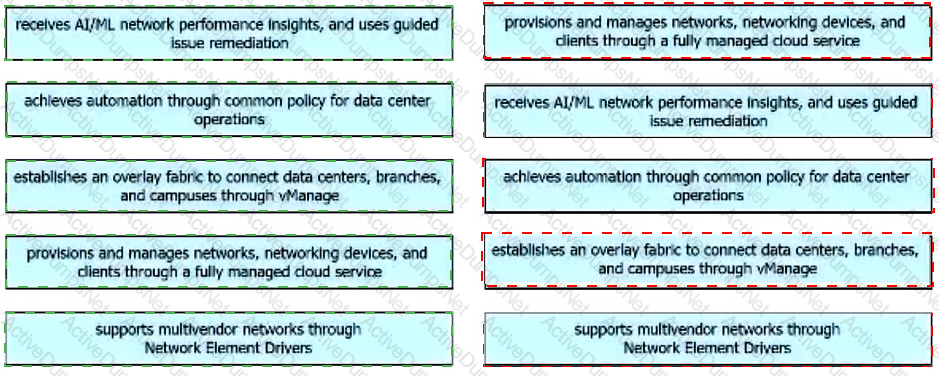
Drag and drop the capabilities from the left onto the Cisco Network Management Platforms that support the capabilities on the right.
A developer is attempting to retrieve all the messages from a Cisco Webex space. The server responds by sending the first 1,000 messages. The developer must make additional requests to retrieve the rest of the messages. Which API constraint is described in this scenario?
What is the impact on an application from having a large distance between a client device and a host server?
A network engineer makes several API calls lo Cisco Prime to retrieve a list of all devices. Each time a response is received, only a subset of the devices is returned. The engineer :ices that HTTP code 429 is returned instead of 200 for some API calls. Why did the response exclude some of the devices?
Which Cisco compute management platform controls server, network, storage, and virtual resources with policy-driven management for up to 10000 physical Cisco servers?
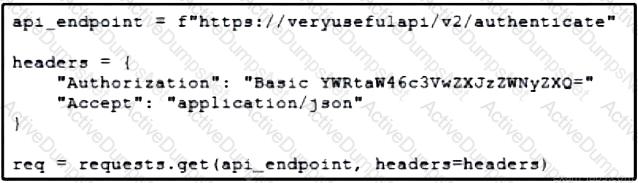
Refer to the exhibit. A developer is part of a team that is working on an open-source project in which source code is hosted in a public GitHub repository. While the application was built, security concerns were addressed by encrypting the credentials on the server. After a few months, the developer realized that a hacker managed to gain access to the account. The exhibit contains part of the source code for the login process. Why was the attacker able to access the developer's account?
Refer to the exhibit.
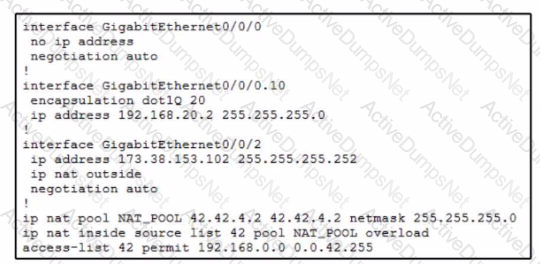
A company recently acquired new IP-based security cameras. After discussion with the engineering team, they decide to segment the security camera traffic m the rest…The engineer assigns the new VLAN 10 for the security camera traffic. After all the devices are configured, it seems as if the cameras cannot access the Internet, .. a few minutes of debugging, the engineer restricts the problem to the router configuration. What is the cause of the issue?
Which RFC 1918 address space includes a subnet of 172.16.0.0 that uses a mask of 255.255.0.0?
A developer is working on a new feature in a branch named 'newfeat123456789' and the current working primary branch is named 'prim987654321'. The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must be used?
What is a benefit of using Python classes?
Which port does HTTPS use by default?
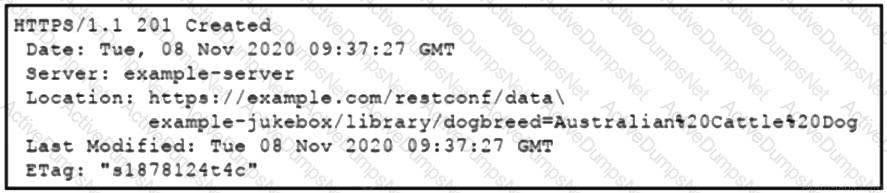
Refer to the exhibit. Which RESTCONF request results in this response?
Which two HTTP code series relate to errors? (Choose two.
A developer has addressed a bug that was found in the production code of an application. A separate file named ‘bug427896191v_fix” has been created with the changes to the code. Which Git command must be used to incorporate the bug fix into the production code?
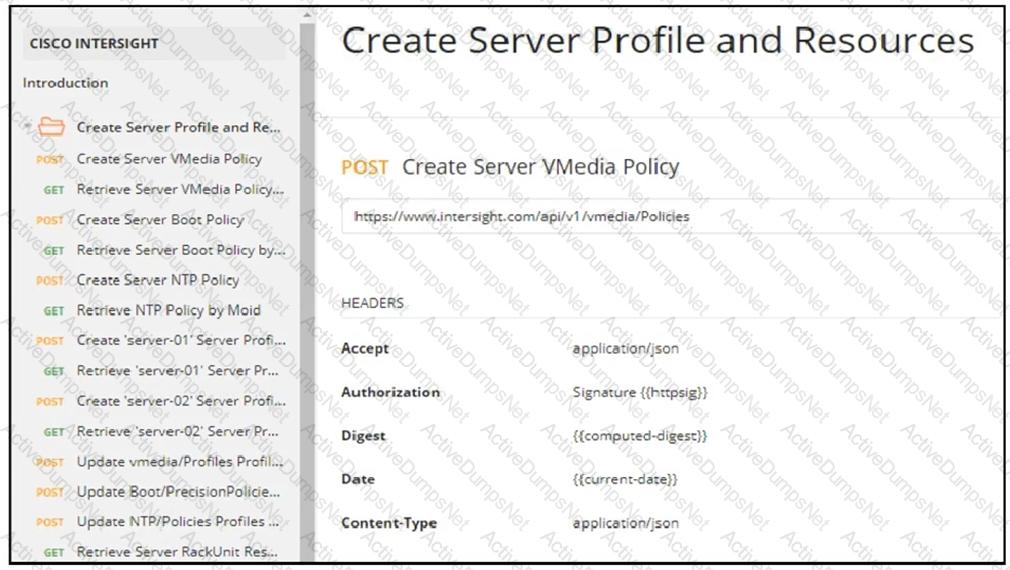
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script by using the Cisco SDK. Not all options are used.
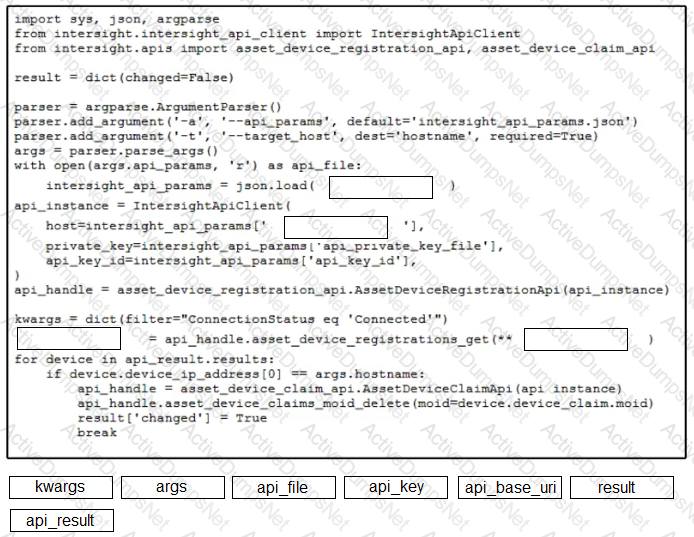
Refer to the exhibit.
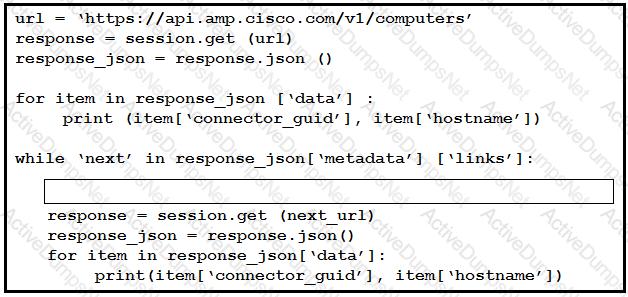
An engineer sends the request to collect data over Cisco AMP for Endpoints API. The Engineer must list guide and hostname data for all computers, but the first request returns only 500 items out of 2,000. Then, the engineer adds the loop to collect all the data. What must be added to the script where the code is missing to complete the requests?
An engineer prepares a set of Python scripts to interact with network devices. To avoid network performance issues, the engineer wants to run them in a test environment. Which resource must be used to monitor the
live execution of code in an always-available environment?
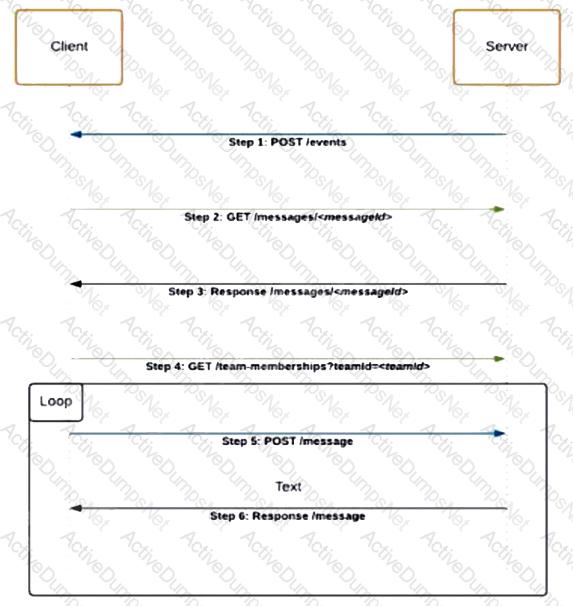
Refer to the exhibit. Which code snippet represents the sequence.
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of network devices from Cisco DNA Center. Not all options are used.
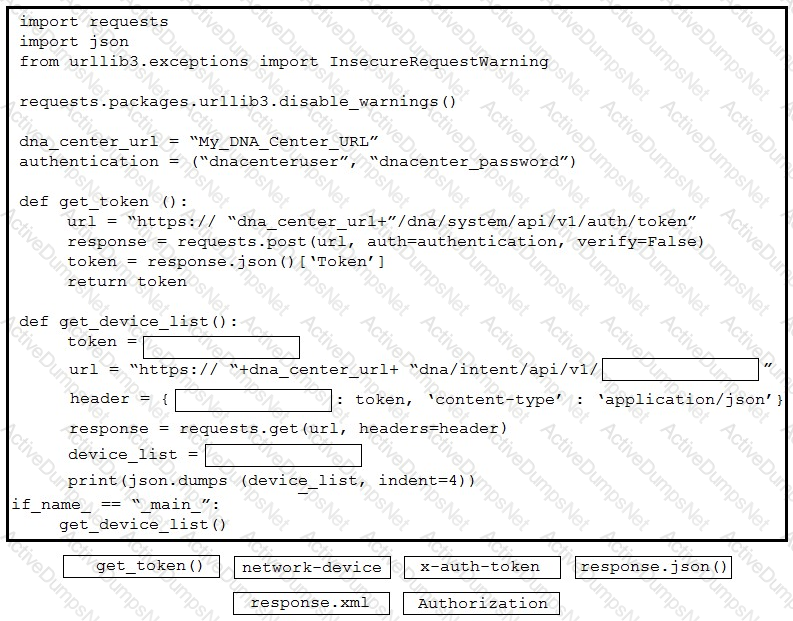
What is a capability of the AXL API?
What does a developer import in a script to parse a file from XML to Python?
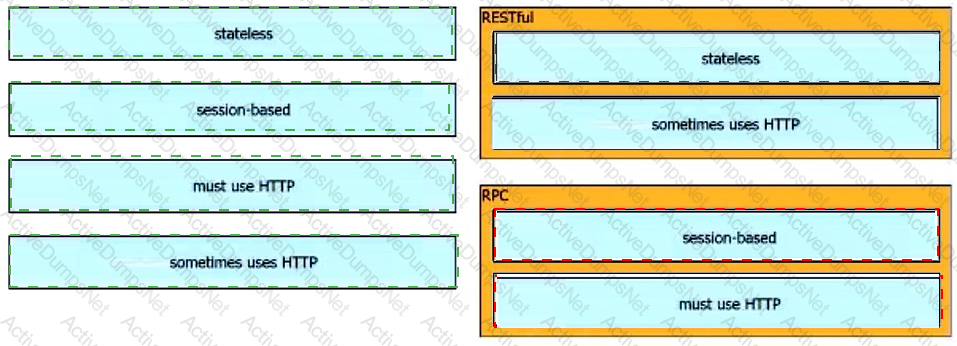
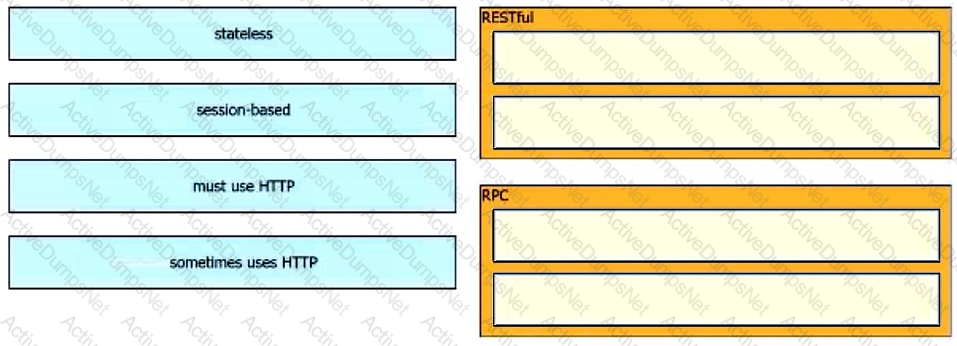
Drag and drop the characteristics from the left onto the corresponding categories on the right to compare RESTful and RPC APIs.
How does edge computing analyze sensitive data in the context of privacy control?
Refer to the exhibit.
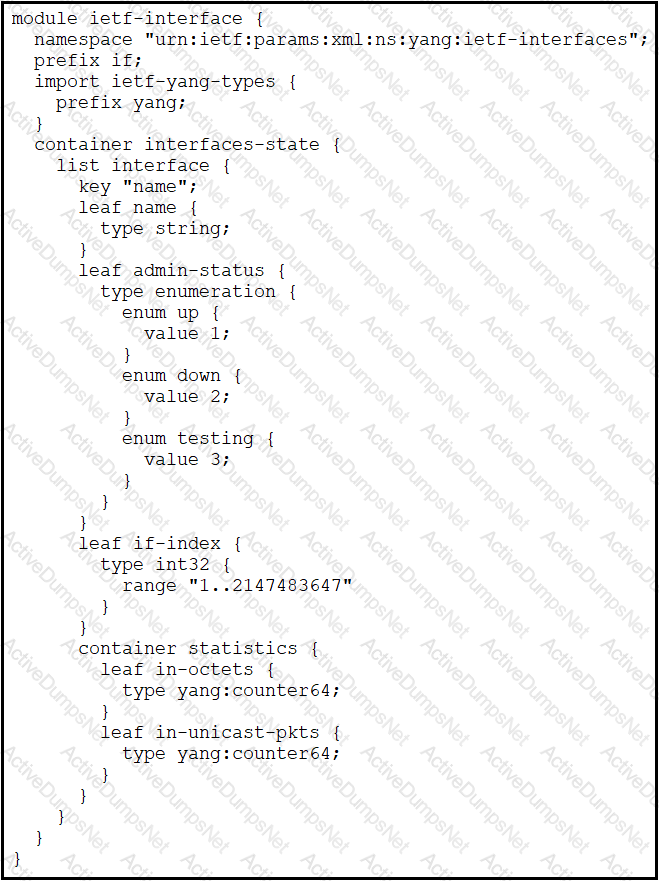
Which XML snippet has interface information that conforms to the YANG model?
A)
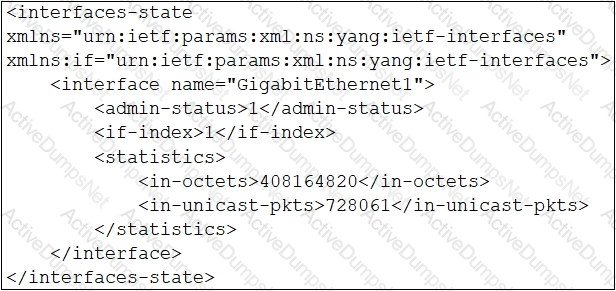
B)
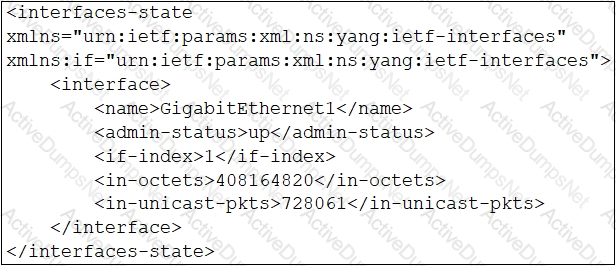
C)
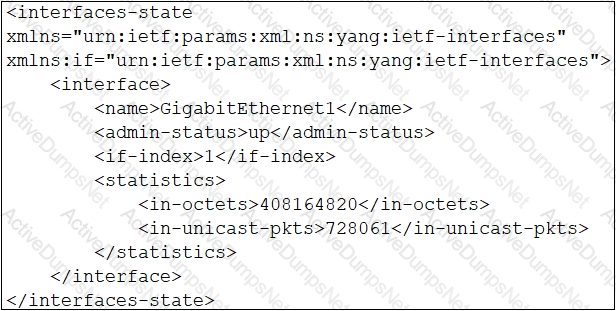
D)
Which solution reduces costs from MPLS, improves application performance, and simplifies operations?
What is a capability of Cisco Webex?
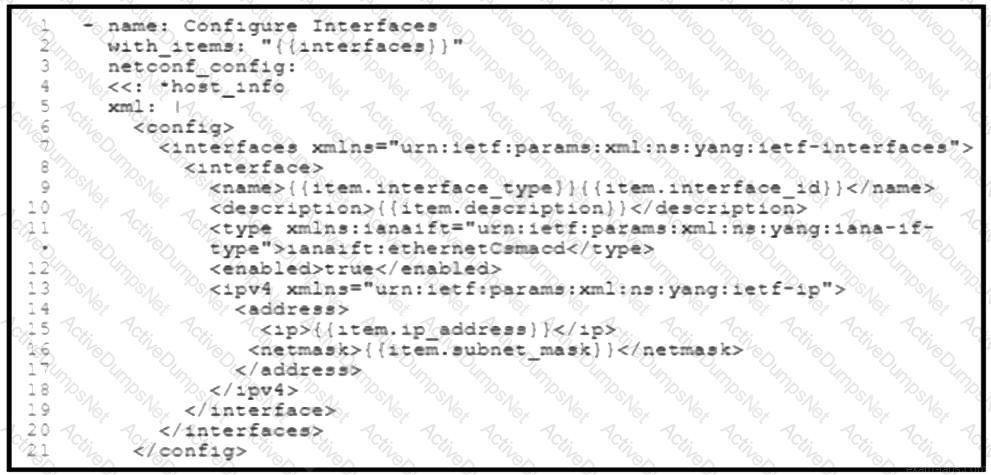
Refer to the exhibit. A network engineer must configure new interfaces on a set of devices and is planning to use an Ansible playbook for the task. All devices support SSH and NETCONF protocol, and the interface variables are unique per device. In which directory are the YAML files including variables hosted to automate the task with the netconf_config module?
A developer starts to learn about building applications that use Cisco APIs. The developer needs access to Cisco security products in a development lab to test the first new Dlication that has been built. Which DevNet resource must be used?
What is a function of the default gateway in a network?
Refer to the exhibit.
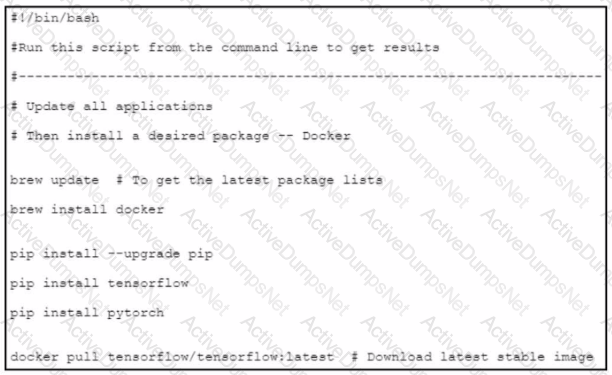
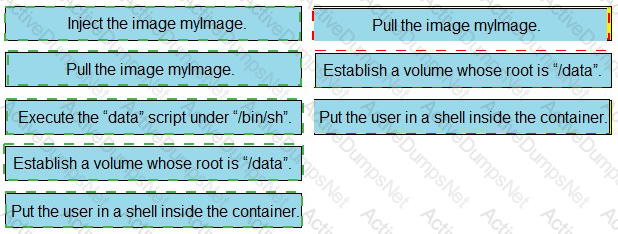
An engineer wants to create a Bash script to automate a workflow that is related to a machine learning-based application. The engineer wants to use the application as a container and use an image from the open-source public repository. What is accomplished by the script?
What is a benefit of version control?
What is the function of an Ethernet switch in a networking environment?
Which TCP port is used to connect to a network device by using Telnet?
A resource named /item is protected by oAuth2 authentication. An endpoint named /login must request authentication. Which method must be used to access the resource by using the REST API?
A developer must test the performance and reliability of an application. After functional and load tests are run, the application crashes due to traffic spikes from users. Which type of API constraint must be implemented to maintain reliability?
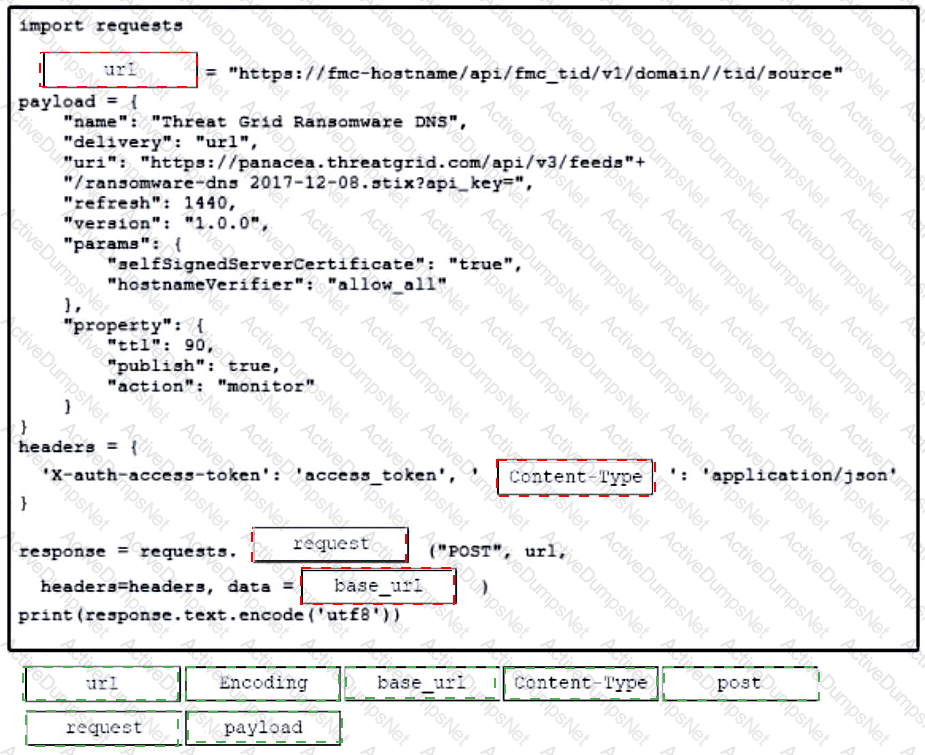
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.