Cisco 200-301 Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 Exam Practice Test
Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 Questions and Answers
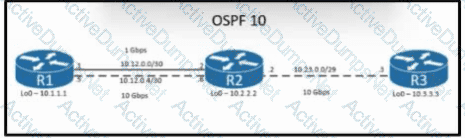
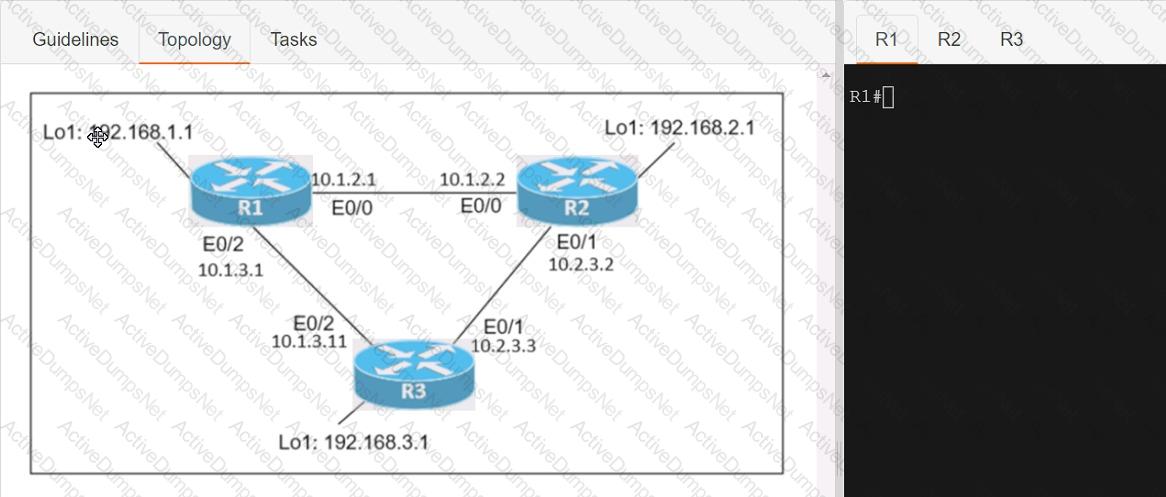
Refer to the exhibit. The loopback IP of R3 has been learned via the two interfaces on R1. R1 is configured with a reference bandwidth of 10 Gbps. Based on the metric calculations, which next hop IP would be used for outgoing routing?
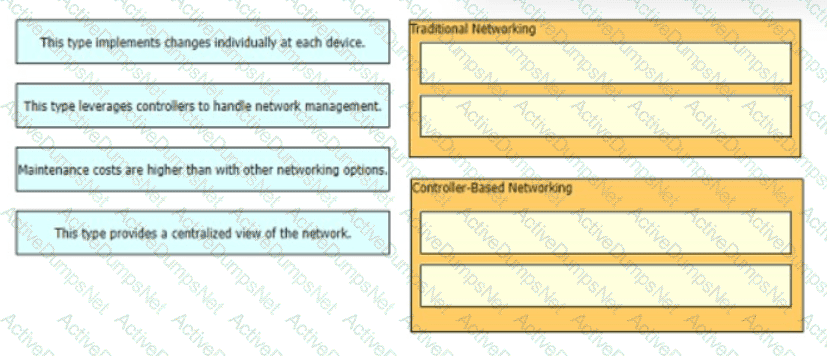
How does automation affect network management processes?
What is a characteristic of private IPv4 addressing?
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.
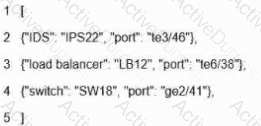
What is represented by the word "switch" within this JSON schema?
Which interface condition is occurring in this output?

Connectivity between three routers has been established, and IP services must be configured jn the order presented to complete the implementation Tasks assigned include configuration of NAT, NTP, DHCP, and SSH services.
1. All traffic sent from R3 to the R1 Loopback address must be configured for NAT on R2. All source addresses must be translated from R3 to the IP address of Ethernet0/0 on R2, while using only a standard access list named NAT To verify, a ping must be successful to the R1 Loopback address sourced from R3. Do not use NVI NAT configuration.
2. Configure R1 as an NTP server and R2 as a client, not as a peer, using the IP address of the R1 Ethernet0/2 interface. Set the clock on the NTP server for midnight on January 1, 2019.
3. Configure R1 as a DHCP server for the network 10.1.3.0/24 in a pool named TEST. Using a single command, exclude addresses 1-10 from the range. Interface Ethernet0/2 on R3 must be issued the IP address of 10.1.3.11 via DHCP.
4. Configure SSH connectivity from R1 to R3, while excluding access via other remote connection protocols. Access for user root and password Cisco must be set on router R3 using RSA and 1024 bits. Verify connectivity using an SSH session from router R1 using a destination address of 10.1.3.11. Do NOT modify console access or line numbers to accomplish this task.
What is a function of Layer 3 switches?
Which interface is used to send traffic to the destination network?
O 10.76.170 161/26 |110/102] via FO/17
O 10.76.170 161/26[110/27e31] via FO/20
R 10.76.170.161/261120/15] via FO/8
R 10.76.170.161/26 [120/10] via FO/12
What is a characteristic of private IPv4 addressing?
What is the main purpose of SSH management access?
Refer to the exhibit.
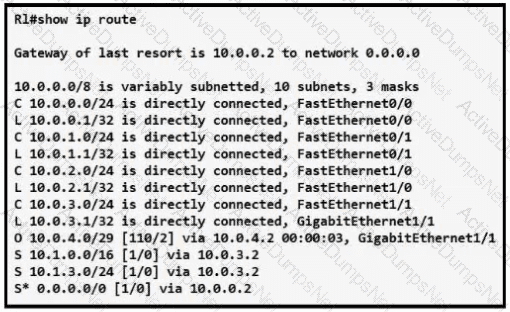
How does router R1 forward packets destined to 10.0.4.10?
How does automation leverage data models to reduce the operational complexity of a managed network?
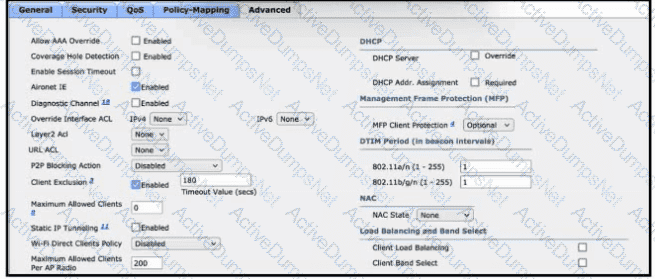
Refer to the exhibit. After a recent internal security audit, the network administrator decided to block all P2P-capable devices from the selected SSID. Which configuration setting must the administrator apply?
Which interface on the WLC is used exclusively as a DHCP relay?
Refer to the exhibit.
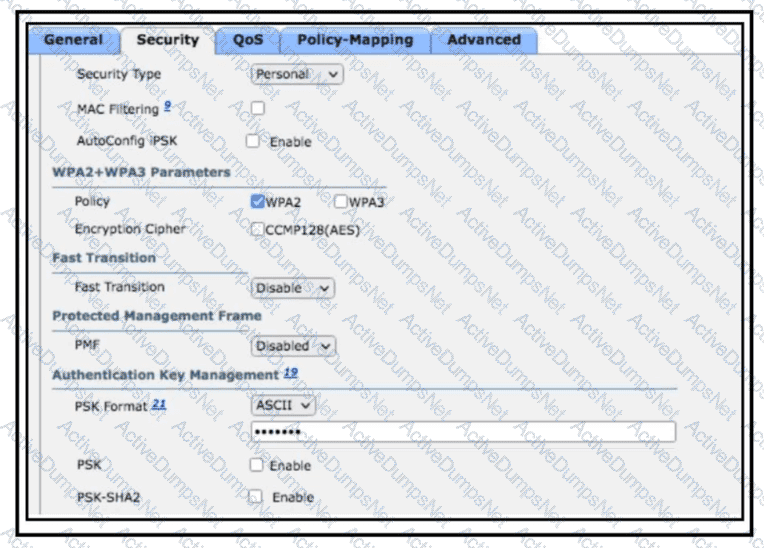
Users will be using a preconfigured secret key and SSID and must have a secured key hashing algorithm configured. The AAA server must not be used for the user authentication method. Which action completes the task?

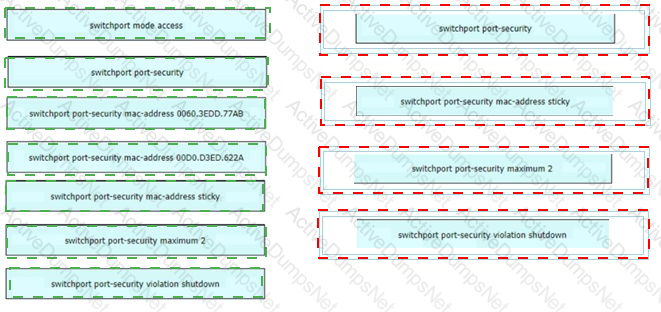
Refer to the exhibit. An administrator must connect SW_1 and the printer to the network. SW_2 requires DTP to be used for the connection to SW_1. The printer is configured as an access port with VLAN 5. Which set of commands completes the connectivity?
How is Al used to identify issues within network traffic?
Which technology allows for logical Layer 3 separation on physical network equipment?
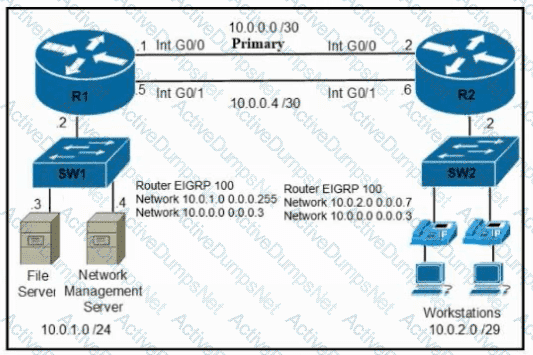
Refer to the exhibit. A secondary route is required on router R1 to pass traffic to the LAN network on R2 if the primary link fails. Which command must be entered to configure the router?
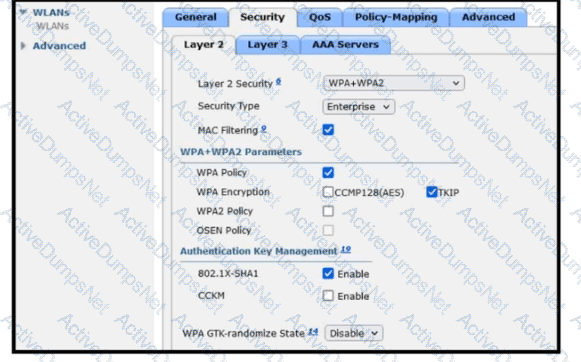
Refer to the exhibit. A guest WLAN must be created that prompts the client for a username and password on the local web page of the WLC. Which two actions must be performed on the Layer 2 tab before enabling the Authentication option on the Layer 3 tab? (Choose two.)
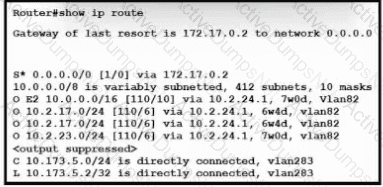
Refer to the exhibit. What is the value of the administrative distance for the default gateway?
Refer to the exhibit.
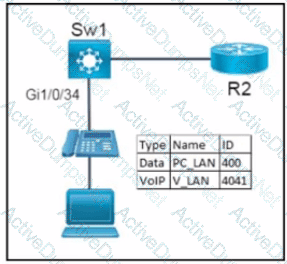
Network services must be enabled on interface Gil/0734. Which configuration meets the needs for this implementation?
A)
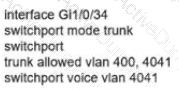
B)
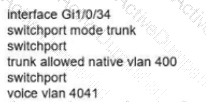
C)
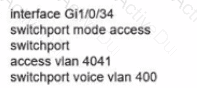
D)
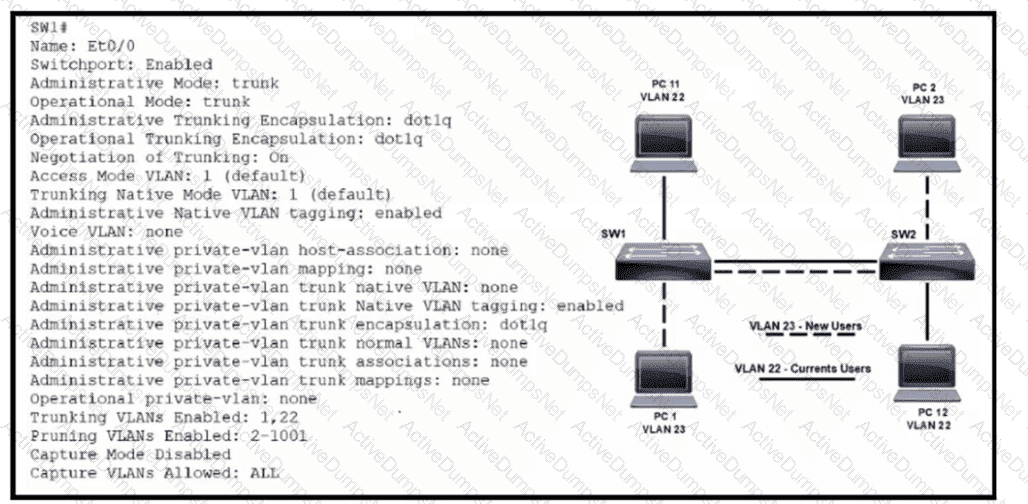
Refer to the exhibit. VLAN 23 is being implemented between SW1 and SW2. The command show interface ethernet0/0 switchport has been issued on SW1. Ethernet0/0 on SW1 is the uplink to SW2. Which command when entered on the uplink interface allows PC 1 and PC 2 to communicate without impact to the communication between PC 11 and PC 12?
Which default condition must be considered when an encrypted mobility tunnel is used between two Cisco WLCs?
Which action prevents debug messages from being sent via syslog while allowing other messages when an abnormally high number of syslog messages are generated by a device with the debug process turned on?
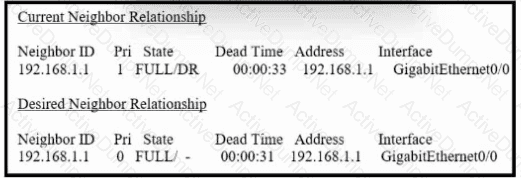
Refer to the exhibit. How must OSPF be configured on the GigabitEthernet0/0 interface of the neighbor device to achieve the desired neighbor relationship?
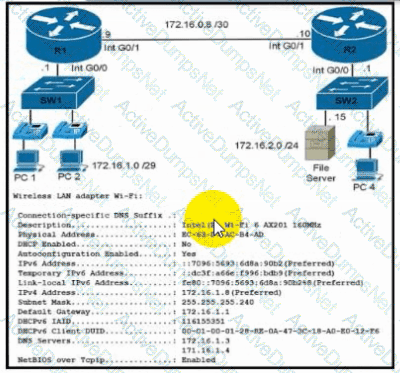
Refer to the exhibit. During initial configuration testing, the Windows workstation PC1 cannot connect with the 172.16.2.0/24 network.
Which set of actions corrects the configuration?
Why does an administrator choose to implement a remote access IPsec VPN?
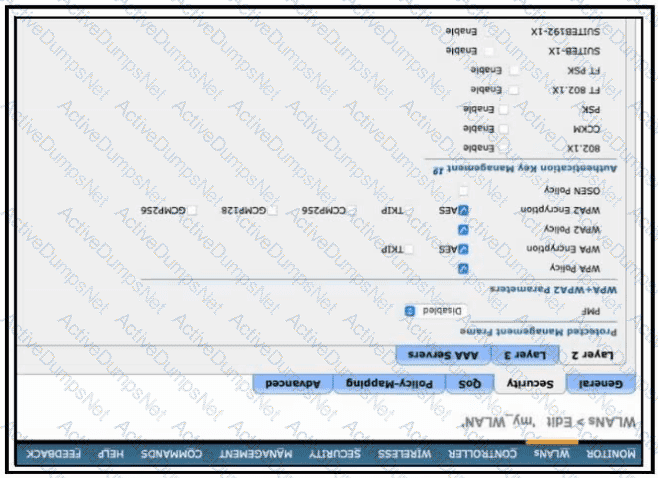
Refer to the exhibit.
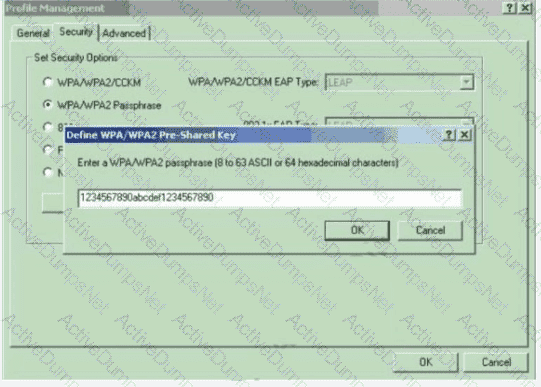
Which configuration is needed to configure a WLAN with WPA2 only and with a password that is 63 characters long?
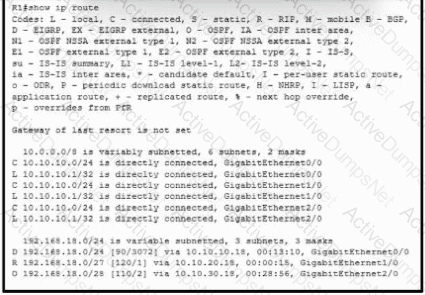
Refer to the exhibit. Which interface does a packet take to reach the host address of 192.168.18.16?
Which fact must the engineer consider when implementing syslog on a new network?
Which header must be included in a REST request from an application that requires JSON-formatted content?
What is a characteristic of private IPv4 addressing?
What is the purpose of the service-set identifier?
Which QoS feature drops traffic that exceeds the committed access rate?

Refer to the exhibit. Which next hop is used to route packets to the application server at 152.168.32.85?
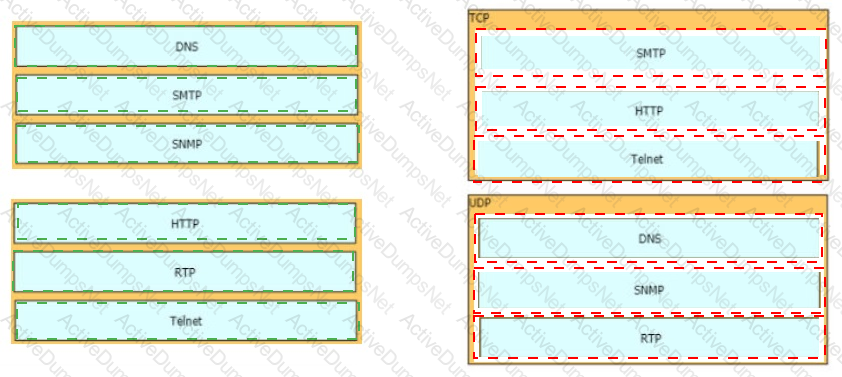
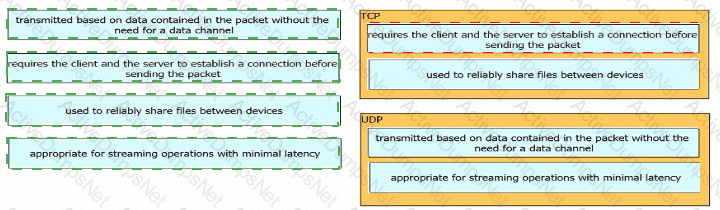
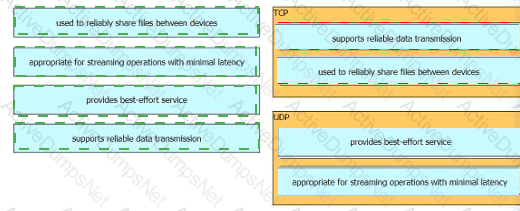
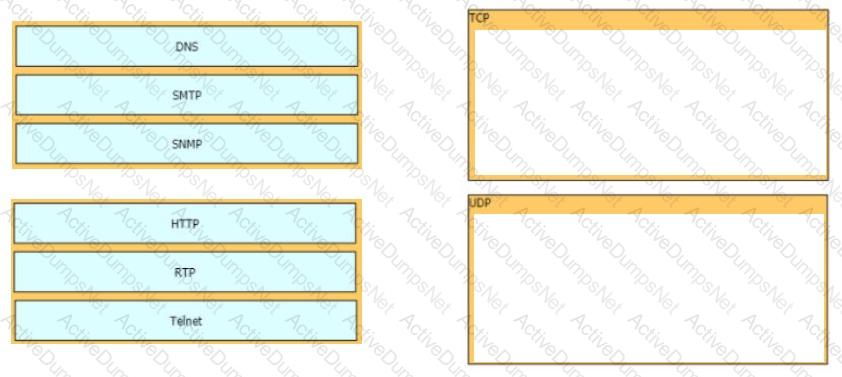
What is the difference between the TCP and UDP protocols?
What is a reason to implement HSRP on a network?
What are two behaviors of a point-to-point WAN topology? (Choose two.)
What is a characteristic of an SSID in wireless networks?
Aswitch receives a frame with the destination MAC address 3C:5D: 7E:9F: 1A:2B.
Switch# show ethernet-frame-and-mac-address-table
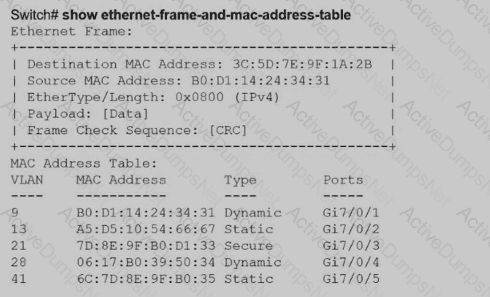
How does the switch handle the frame?
In which way does generative AI aid network simulations?
What is an advantage of using SDN versus traditional networking when it comes to security?
How does MAC learning function?
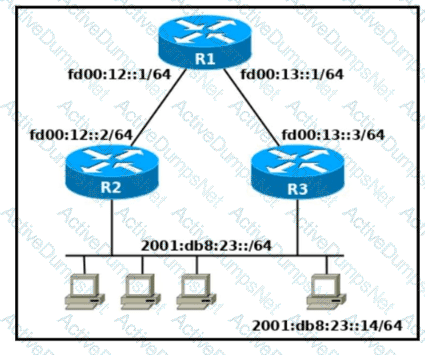
Refer to the exhibit. Which two commands, when configured on router R1. fulfill these requirements? (Choose two.) ' Packets toward the entire network 2001:db8:23: :/64 must be forwarded through router R2. ' Packets toward host 2001: db8:23::14 preferably must be forwarded through R3.
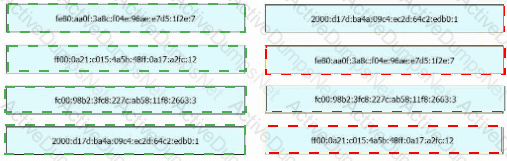
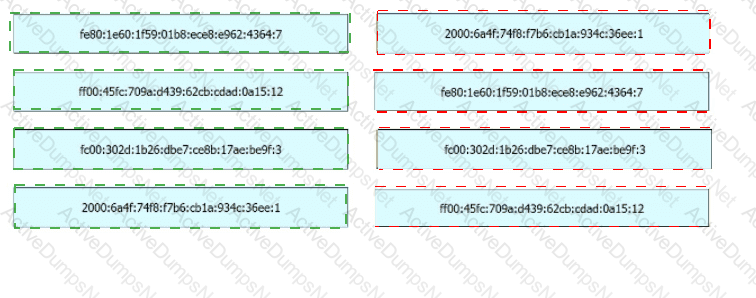
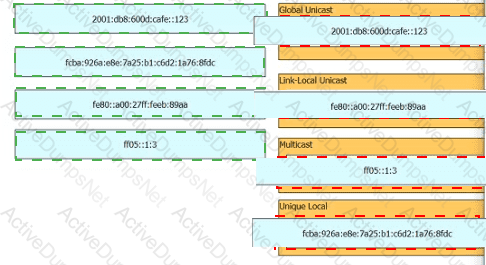
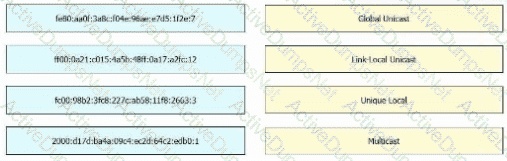
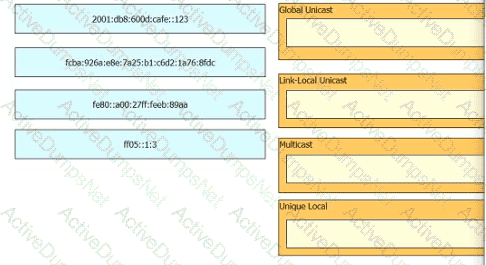
Drag and drop the IPv6 address from the left onto the type on the right.
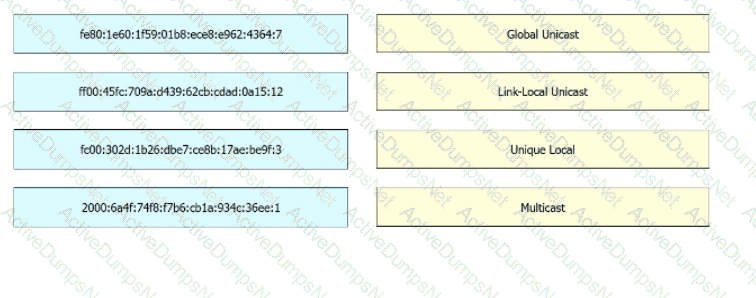
Drag and drop the IPv6 address from the left onto the type on the right.
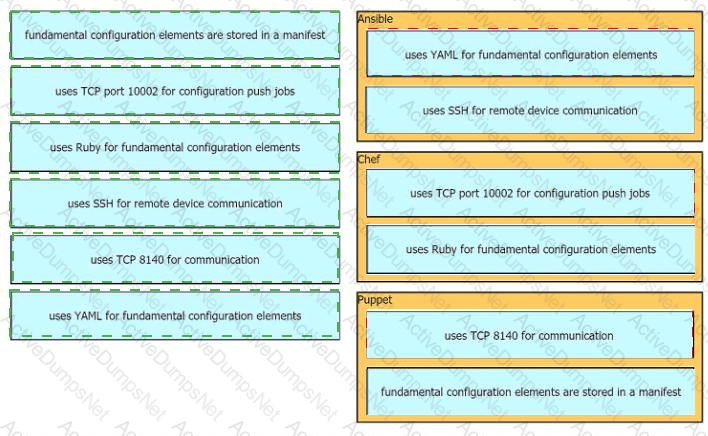
Which two features are provided by Ansible in network automation? (Choose two.)
An organization developed new security policies and decided to print the policies and distribute them to all personnel so that employees review and apply the policies. Which element of a security program is the organization implementing?
What is the function of generative AI in network operations?
Which AP feature provides a captive portal for users to authenticate, register, and accept terms before accessing the internet?
Which interface is used to send traffic to the destination network?
10.90.207.87/26 [110/1912] via F0/7
10.90.207.87/26 [110/28968] via F0/6
10.90.207.87/26 [120/14] via F0/4
10.90.207.87/26 [120/11] via F0/5
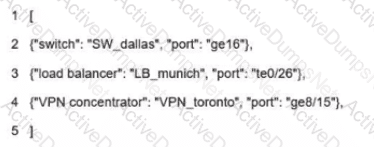
What is represented in line 3 within this JSON schema?
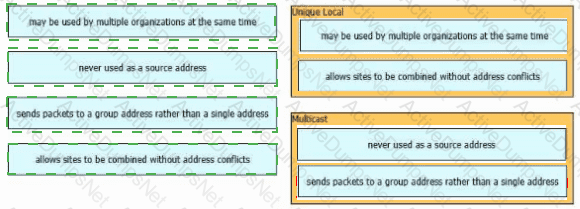
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
A new DHCP server has been deployed in a corporate environment with lease time set to eight hours. Which CMD command on a Windows-based device allows the engineer to verify the DHCP lease expiration?
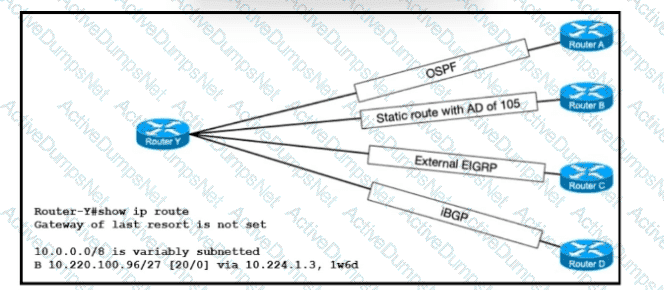
Refer to the exhibit. The route for 10.220.100.96/27 has been very unstable. The same route has four backups to routers A, B, C, and D via the respective methods. The routing protocol defaults for router Y have not been changed. When the current route for 10.220.100.96/27 becomes unavailable, which router will router Y use to route traffic to 10.220.100.96/27?
All physical cabling is in place. A company plans to deploy 32 new sites.
The sites will utilize both IPv4 and IPv6 networks.
1 . Subnet 172.25.0.0/16 to meet the subnet requirements and maximize
the number of hosts
Using the second subnet
• Assign the first usable IP address to e0/0 on Sw1O1
• Assign the last usable IP address to e0/0 on Sw102
2. Subnet to meet the subnet requirements and maximize
the number of hosts
c Using the second subnet
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on e0/0 on Sw101
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on eO/O on swi02
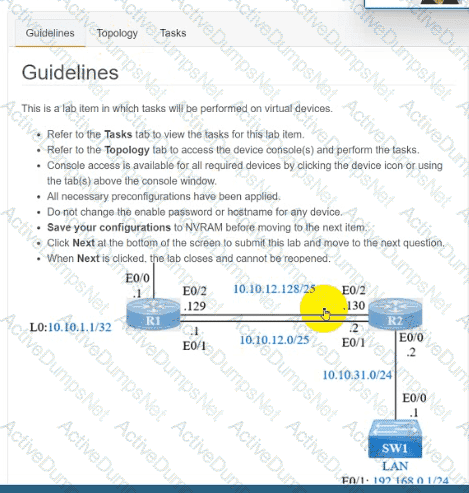
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.

An engineer requires a switch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
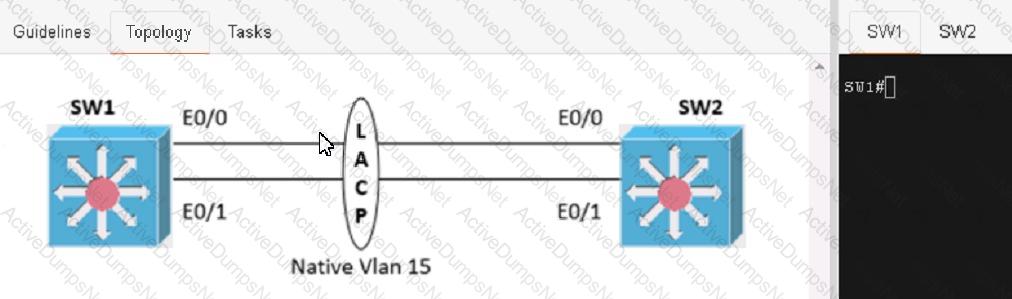
Physical connectivity is implemented between the two Layer 2 switches, and the network connectivity between them must be configured
1. Configure an LACP EtherChannel and number it as 1; configure it between switches SW1 and SVV2 using interfaces Ethernet0/0 and Ethernet0/1 on both sides. The LACP mode must match on both ends
2 Configure the EtherChannel as a trunk link.
3. Configure the trunk link with 802.1 q tags.
4. Configure the native VLAN of the EtherChannel as VLAN 15.
What is a characteristic of a Layer 2 switch?
Why would a network administrator choose to implement RFC 1918 address space?
What is the main capability of multifactor authentication?
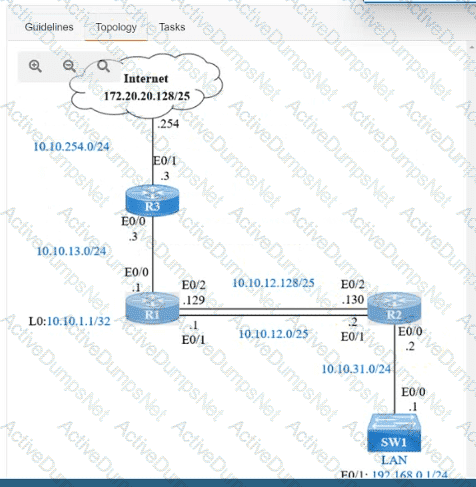
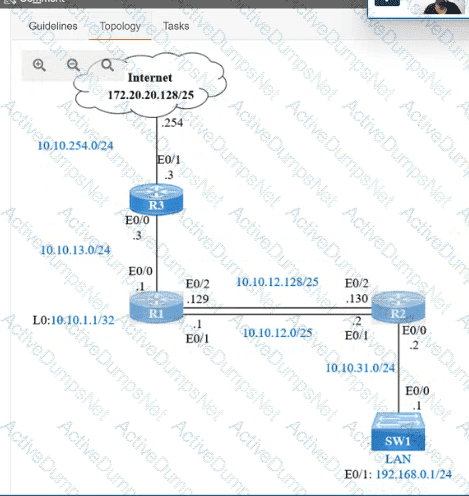
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
How does MAC learning function?
Which interface is used to send traffic to the destination network?
10.174.208.210/28 [110/2708] via G0/21
10.174.208.210/28 [110/25445] via G0/20
10.174.208.210/28 [120/1] via G0/12
10.174.208.210/28 [120/4] via G0/16
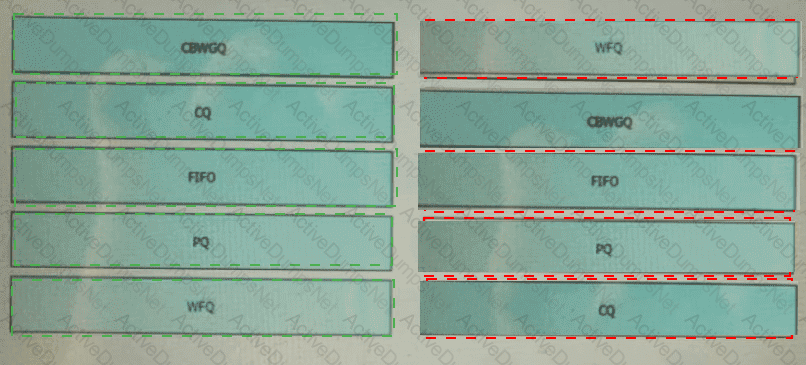
Which two QoS tools provide congestion management? (Choose two.)
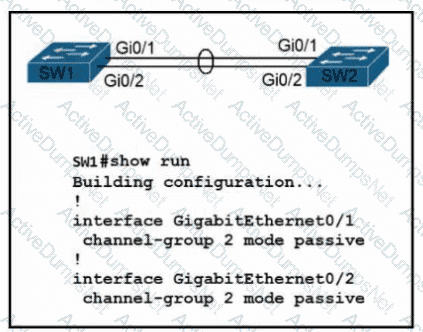
Refer to the exhibit. Which configuration enables SW2 to establish an LACP EtherChannel?
How does MAC learning function?
Which two northbound APIs are found in a software-defined network? (Choose two.)
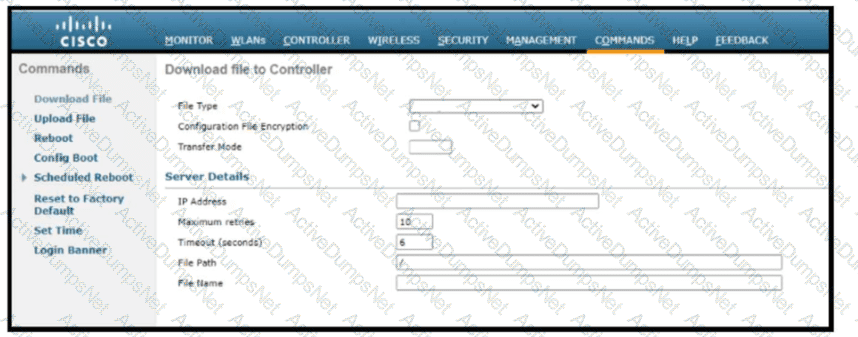
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
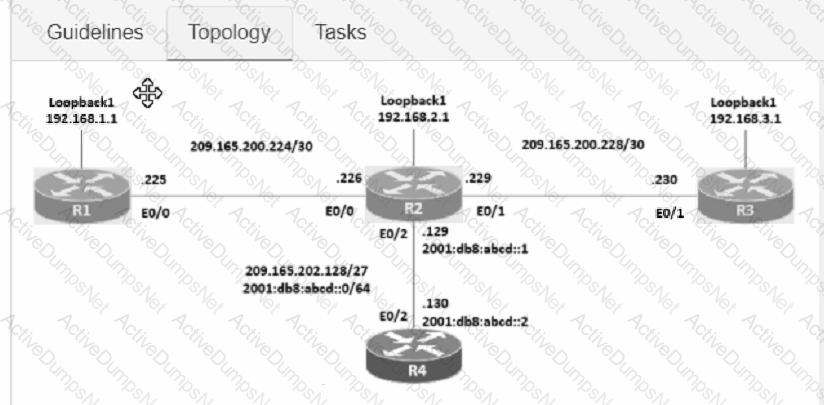
Configure IPv4 and IPv6 connectivity between two routers. For IPv4, use a /28 network from the 192.168.1.0/24 private range. For IPv6, use the first /64 subnet from the 2001:0db8:aaaa::/48 subnet.
1. Using Ethernet0/1 on routers R1 and R2, configure the next usable/28 from the 192.168.1.0/24 range. The network 192.168.1.0/28 is unavailable.
2. For the IPv4 /28 subnet, router R1 must be configured with the first usable host address.
3. For the IPv4 /28 subnet, router R2 must be configured with the last usable host address.
4. For the IPv6 /64 subnet, configure the routers with the IP addressing provided from the topology.
5. A ping must work between the routers on the IPv4 and IPv6 address ranges.

What is a role of wireless controllers in an enterprise network?
Refer to the exhibit.
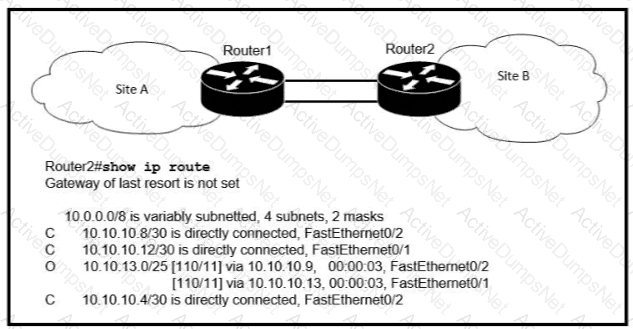
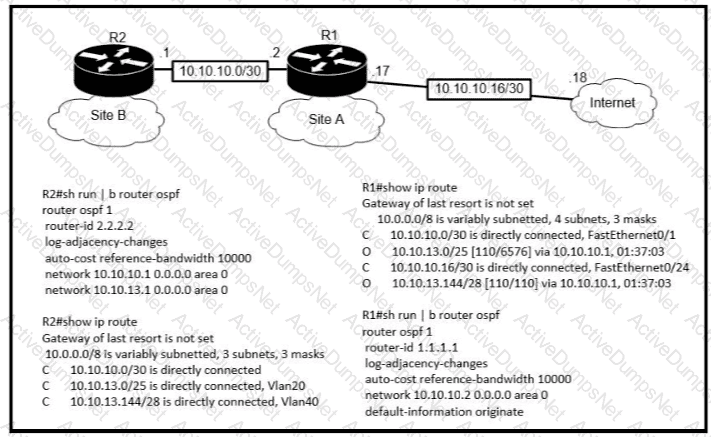
If OSPF is running on this network, how does Router 2 handle traffic from Site B to 10.10.13/25 at Site A?
Which action does the router take as it forwards a packet through the network?
Which command entered on a switch configured with Rapid PVST* listens and learns for a specific time period?
An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
Refer to the exhibit.

Which type of configuration is represented in the output?
An engineer must configure a/30 subnet between two routers. Which usable IP address and subnet mask combination meets this criteria?
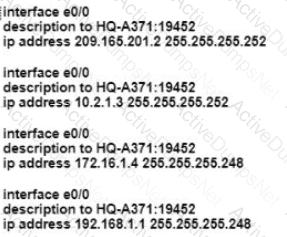
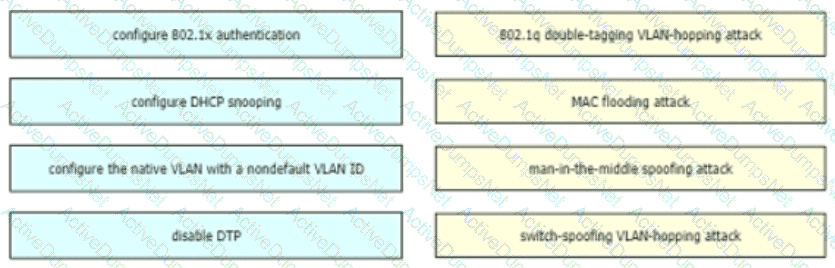
How are VLAN hopping attacks mitigated?
In software-defined architecture, which place handles switching for traffic through a Cisco router?
An engineer is asked to protect unused ports that are configured in the default VLAN on a switch.
Which two steps will fulfill the request? (Choose two)
What is a recommended approach to avoid co-channel congestion while installing access points that use the 2.4 GHz frequency?
What is the maximum bandwidth of a T1 point-to-point connection?
Refer to the exhibit.

A router reserved these five routes from different routing information sources.
Which two routes does the router install in its routing table? (Choose two)
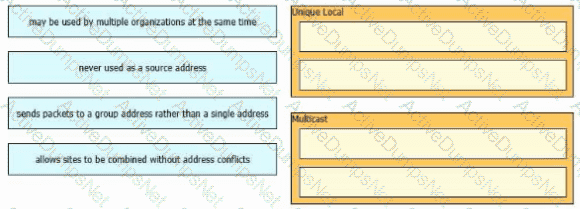
Which IPv6 address block sends packets to a group address rather than a single address?
Refer to the exhibit Router R1 Fa0/0 is unable to ping router R3 Fa0'1. Which action must be taken in router R1 to help resolve the configuration issue?
Which global command encrypt all passwords in the running configuration?
Several new coverage cells are required to improve the Wi-Fi network of an organization. Which two standard designs are recommended? (choose two.)
What is the benefit of using FHRP?
What uses HTTP messages to transfer data to applications residing on different hosts?
What occurs when overlapping Wi-Fi channels are implemented?
After installing a new Cisco ISE server, which task must the engineer perform on the Cisco WLC to connect wireless clients on a specific VLAN based on their credentials?
Refer to the exhibit.
Which switch becomes the root of the spanning tree for VLAN 110?

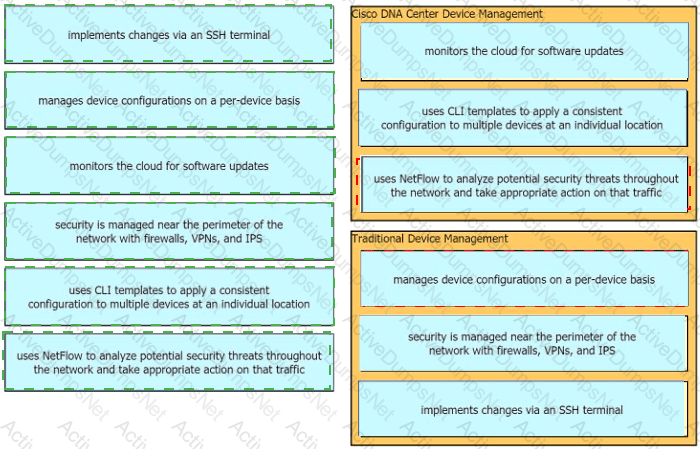
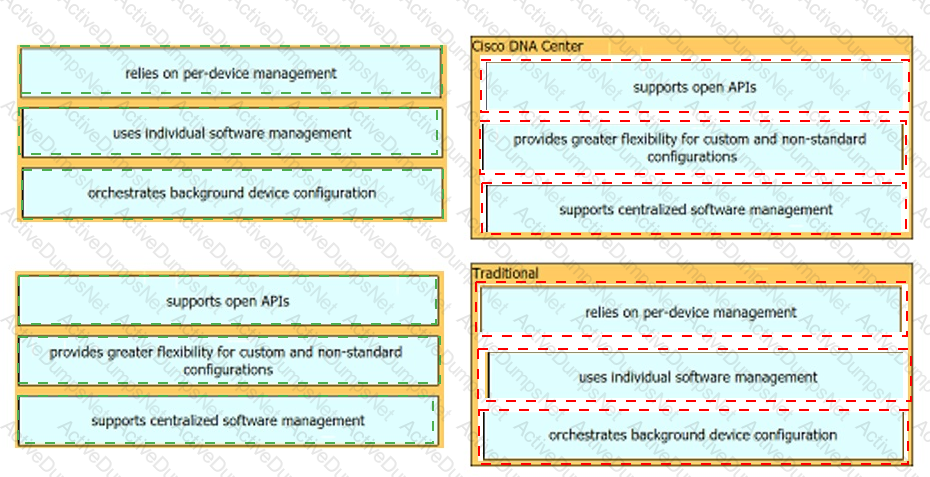
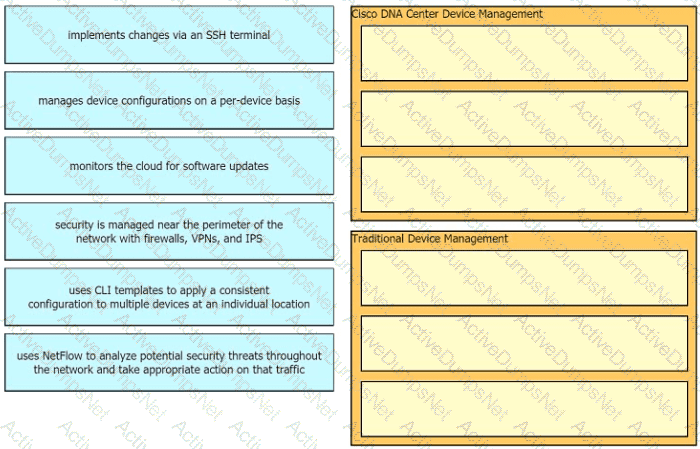
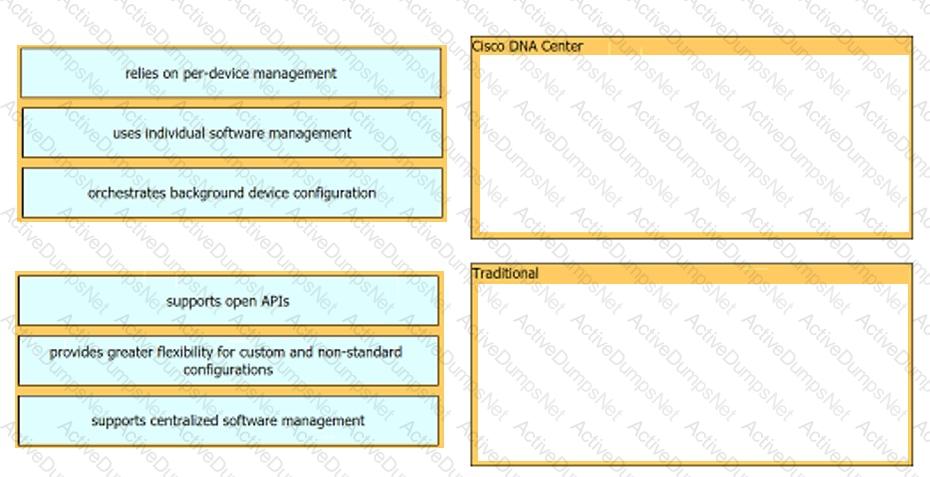
What is an advantage of Cisco DNA Center versus traditional campus device management?
When configuring IPv6 on an interface, which two IPv6 multicast groups are joined? (Choose two)
What is a DHCP client?
Which resource is able to be shared among virtual machines deployed on the same physical server?
How do servers connect to the network in a virtual environment?
An engineer must configure the IPv6 address 2001:0db8:0000:0000:0700:0003:400F:572B on the serial0/0 interface of the HQ router and wants to compress it for easier configuration. Which command must be issued on the router interface?
What is recommended for the wireless infrastructure design of an organization?
Which type of attack can be mitigated by dynamic ARP inspection?
Which two capacities of Cisco DNA Center make it more extensible as compared to traditional campus device management? (Choose two)
Refer to the exhibit.
An access list is required to permit traffic from any host on interface G0/0 and deny traffic from interface G/0/1. Which access list must be applied?

Refer to the exhibit.
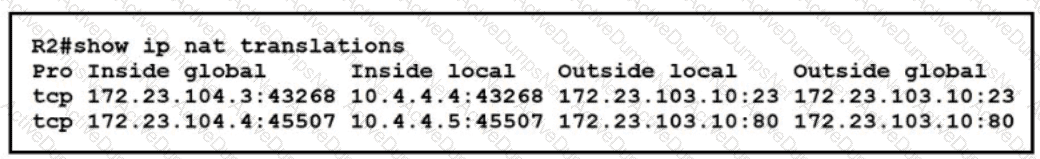
An engineer configured NAT translations and has verified that the configuration is correct.
Which IP address is the source IP?
Which type of wireless encryption is used for WPA2 in preshared key mode?
What is a characteristic of a SOHO network?
Which access layer threat-mitigation technique provides security based on identity?
Which two events occur automatically when a device is added to Cisco DNA Center? (Choose two. )
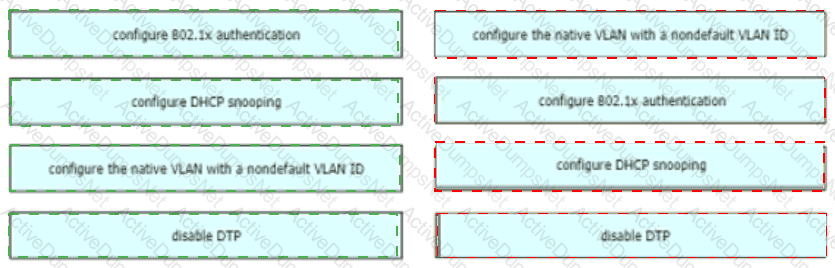
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
What is a DNS lookup operation?
Which command automatically generates an IPv6 address from a specified IPv6 prefix and MAC address of an interface?
An engineer needs to add an old switch back into a network. To prevent the switch from corrupting the VLAN database which action must be taken?
What are two similarities between UTP Cat 5e and Cat 6a cabling? (Choose two.)
How are the switches in a spine-and-leaf topology interconnected?
When a floating static route is configured, which action ensures that the backup route is used when the primary route fails?
Which WAN topology provides a combination of simplicity quality, and availability?
In QoS, which prioritization method is appropriate for interactive voice and video?
What protocol allows an engineer to back up 20 network router configurations globally while using the copy function?
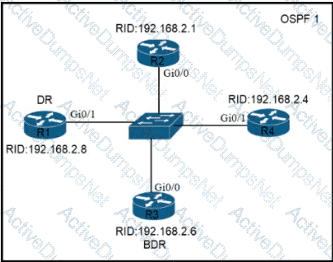
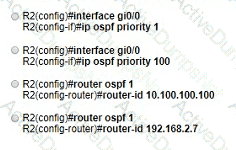
Refer to the exhibit. All routers in the network are configured R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configure on R2 to Be elected as the DR in the network?
How does a switch process a frame received on Fa0/1 with the destination MAC address of 0e38.7363.657b when the table is missing the address?
Which API is used in controller-based architectures to interact with edge devices?
in Which way does a spine and-leaf architecture allow for scalability in a network when additional access ports are required?
Which network allows devices to communicate without the need to access the Internet?
Drag and drop the QoS congestion management terms from the left onto the description on the right.

Refer to the exhibit.
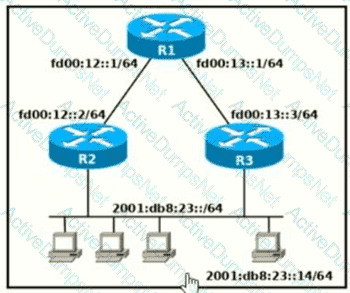
Which two commands, when configured on router R1, fulfill these requirements? (Choose two.)
Packets towards the entire network 2001:db8:2::/64 must be forwarded through router R2.
Packets toward host 2001:db8:23::14 preferably must be forwarded through R3.
What causes a port to be placed in the err-disabled state?
What is a function of the Cisco DNA Center Overall Health Dashboard?
What mechanism carries multicast traffic between remote sites and supports encryption?
When DHCP is configured on a router, which command must be entered so the default gateway is automatically distributed?
In software defined architectures, which plane is distributed and responsible for traffic forwarding?
Drag and drop the functions of DHCP from the left onto any of the positions on the right Not all functions are used

Refer to the exhibit.
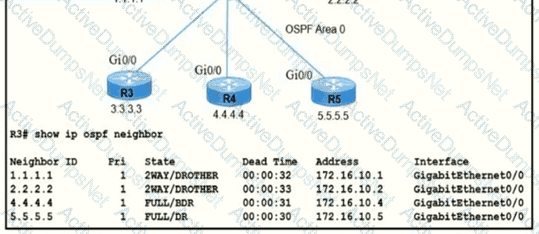
R5 is the current DR on the network, and R4 is the BDR. Their interfaces are flapping, so a network engineer wants the OSPF network to elect a different DR and BDR. Which set of configurations must the engineer implement?
A)

B)

C)

D)

What are two characteristics of the distribution layer in a three-tier network architecture? (Choose two.)
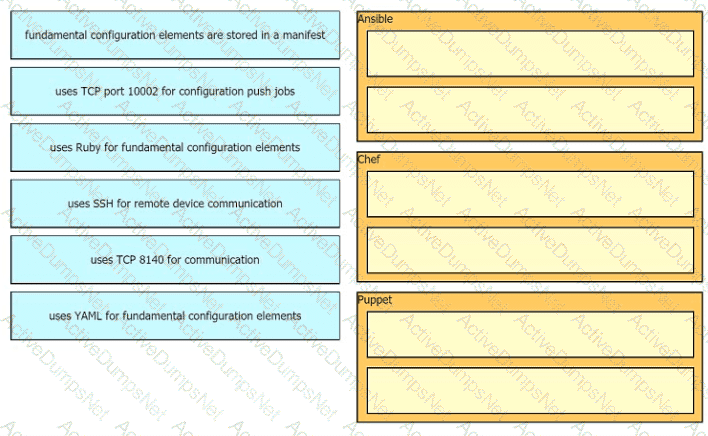
Drag drop the descriptions from the left onto the correct configuration-management technologies on the right.
What is a DHCP client?
Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
What are two roles of Domain Name Services (DNS)? (Choose Two)
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
Which two WAN architecture options help a business improve scalability and reliability for the network? (Choose two.)
What is a characteristic of cloud-based network topology?
Refer to the exhibit.
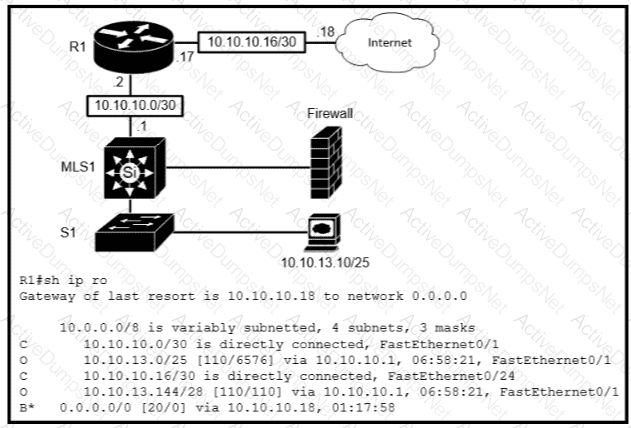
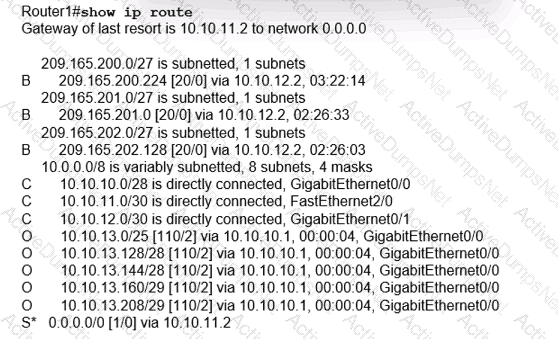
Which type of route does R1 use to reach host 10.10.13.10/32?
How do TCP and UDP differ in the way they guarantee packet delivery?
Refer to the exhibit.
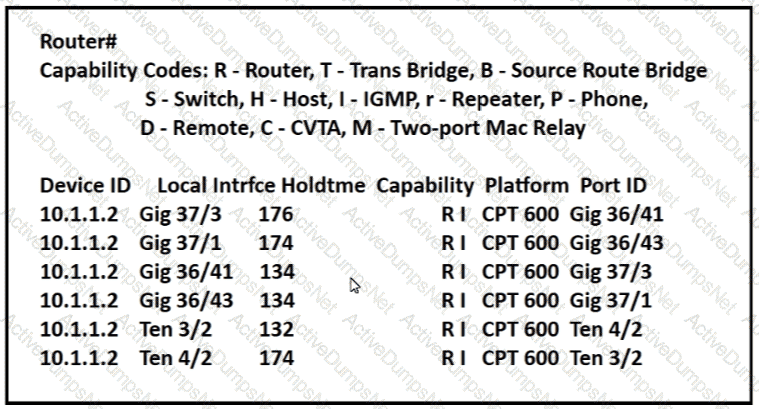
Which command provides this output?
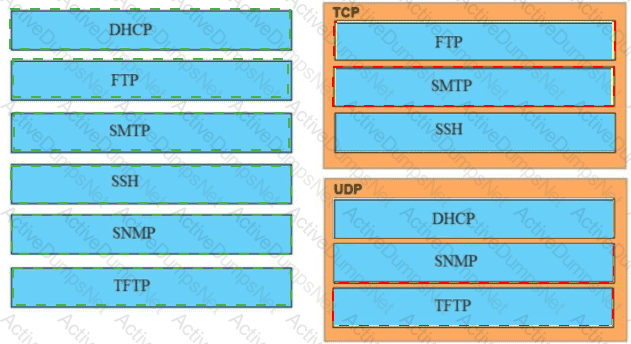
Drag and drop the TCP/IP protocols from the left onto the transmission protocols on the right
What does an SDN controller use as a communication protocol to relay forwarding changes to a southbound API?
Which type of organization should use a collapsed-core architecture?
Refer to the exhibit.
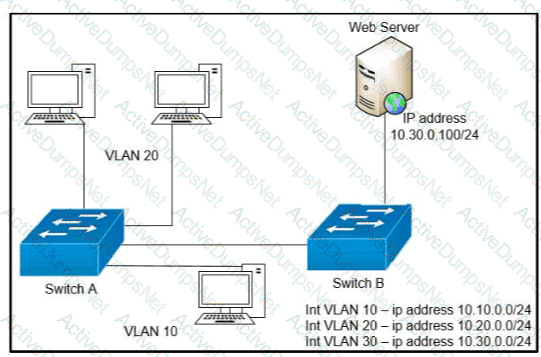
A network engineer must block access for all computers on VLAN 20 to the web server via HTTP All other computers must be able to access the web server Which configuration when applied to switch A accomplishes this task?

What is the benefit of configuring PortFast on an interface?
Refer to the exhibit.
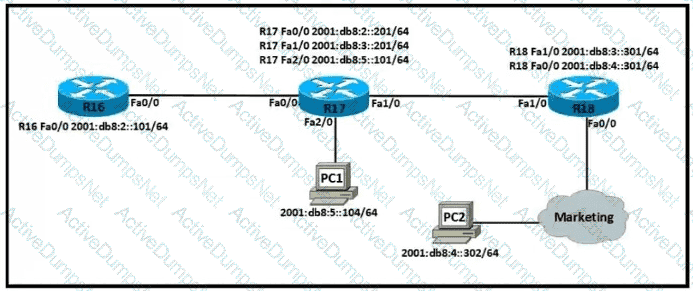
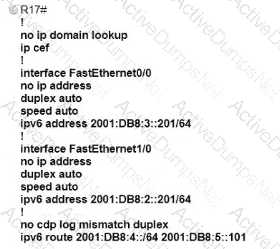
Which IPv6 configuration is required for R17 to successfully ping the WAN interface on R18?
A)
B)
C)

D)
Where does a switch maintain DHCP snooping information?
When the active router in an HSRP group fails, what router assumes the role and forwards packets?
Drag and drop the application protocols from the left onto the transport protocols that it uses on the right
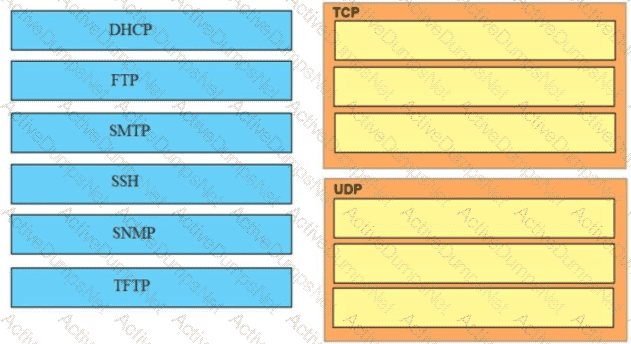
Which function does an SNMP agent perform?
Refer to the exhibit.
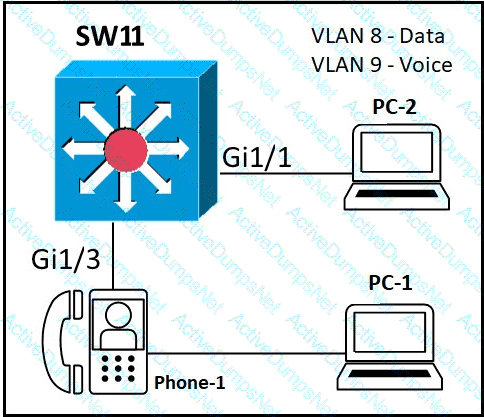
An administrator must configure interfaces Gi1/1 and Gi1/3 on switch SW11 PC-1 and PC-2 must be placed in the Data VLAN and Phone-1 must be placed in the Voice VLAN Which configuration meets these requirements?

What are two characteristics of a controller-based network? (Choose two)
Refer to the exhibit.
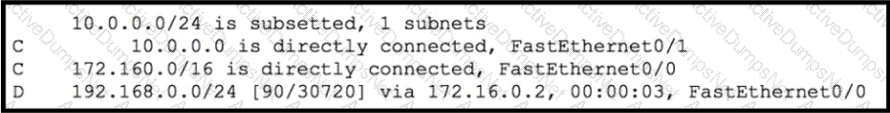
Which route type does the routing protocol Code D represent in the output?
Refer to the exhibit.
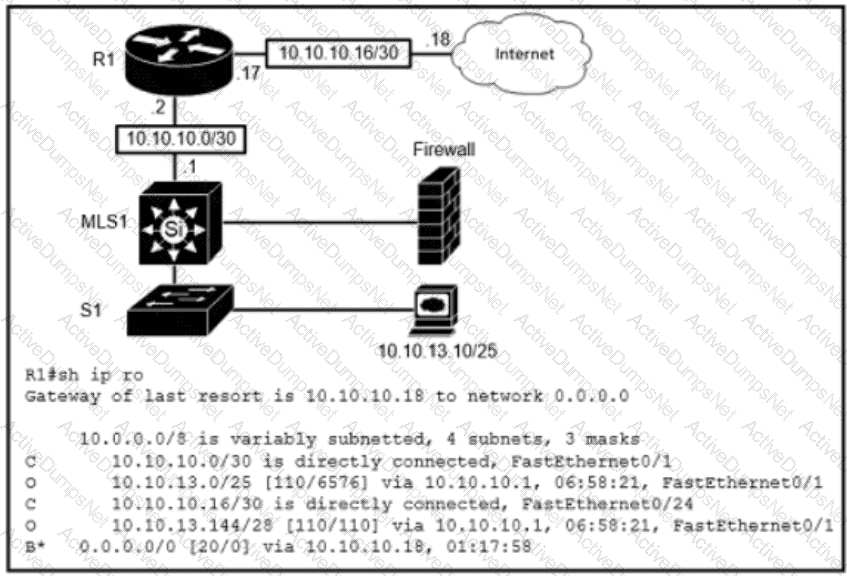
Which route type is configured to reach the internet?
Refer to the exhibit.
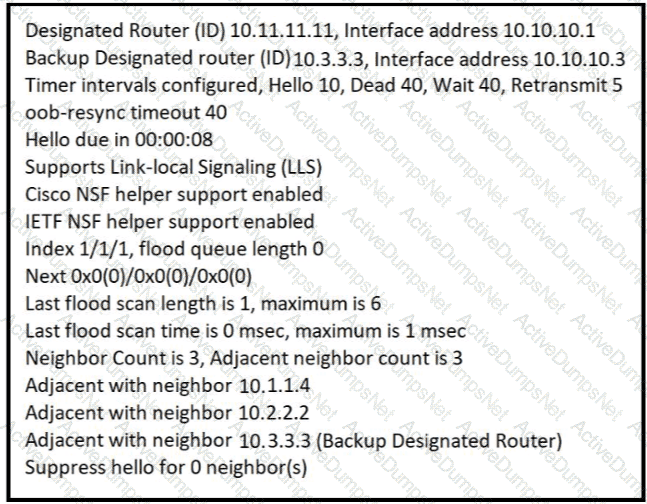
The show ip ospf interface command has been executed on R1 How is OSPF configured?
Which set of action satisfy the requirement for multifactor authentication?
Which two outcomes are predictable behaviors for HSRP? (Choose two)
Which unified access point mode continues to serve wireless clients after losing connectivity to the Cisco Wireless LAN Controller?
Refer to the exhibit.
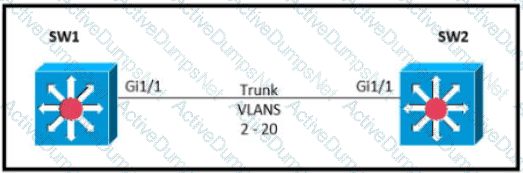
Which command must be executed for Gi1.1 on SW1 to become a trunk port if Gi1/1 on SW2 is configured in desirable or trunk mode?
An engineer is configuring NAT to translate the source subnet of 10.10.0.0/24 to any of three addresses 192.168.30.1, 192.168.3.2, 192.168.3.3 Which configuration should be used?
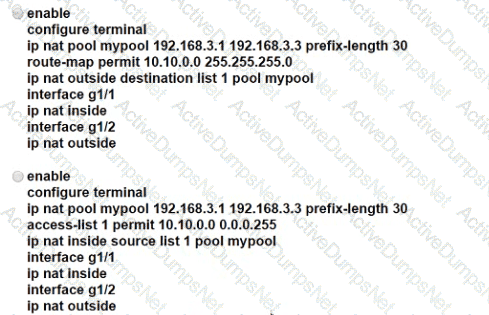
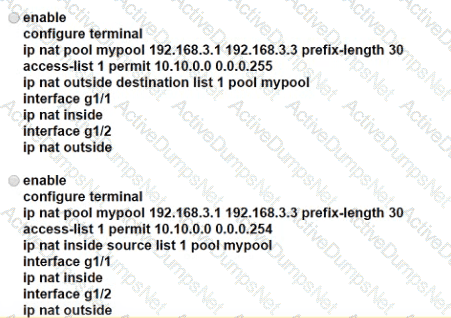
Refer to the exhibit.
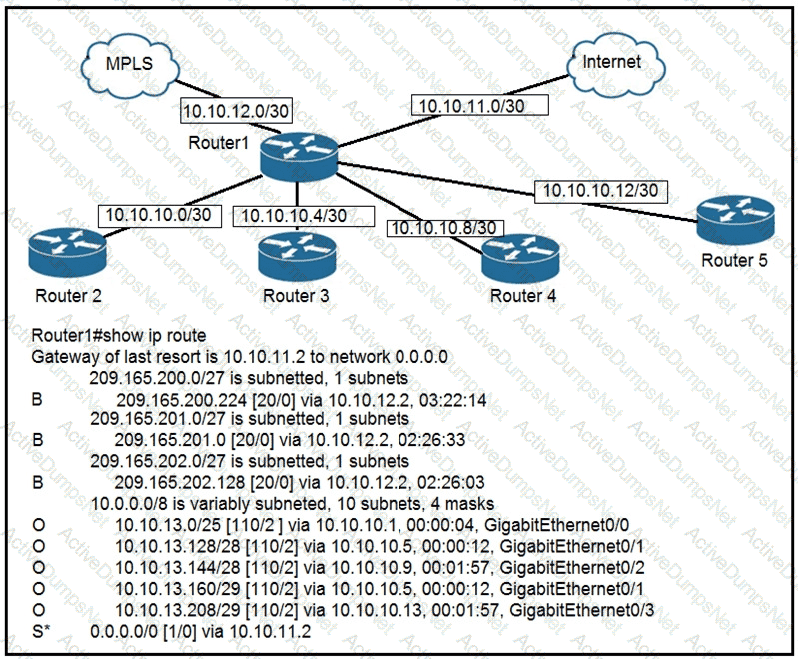
To which device does Router1 send packets that are destined to host 10.10.13.165?
A network administrator needs to aggregate 4 ports into a single logical link which must negotiate layer 2 connectivity to ports on another switch. What must be configured when using active mode on both sides of the connection?
An engineer configures interface Gi1/0 on the company PE router to connect to an ISP Neighbor discovery is disabled
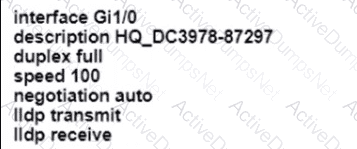
Which action is necessary to complete the configuration if the ISP uses third-party network devices?
What is a capability of FTP in network management operations?
Which goal is achieved by the implementation of private IPv4 addressing on a network?
Refer to the exhibit.
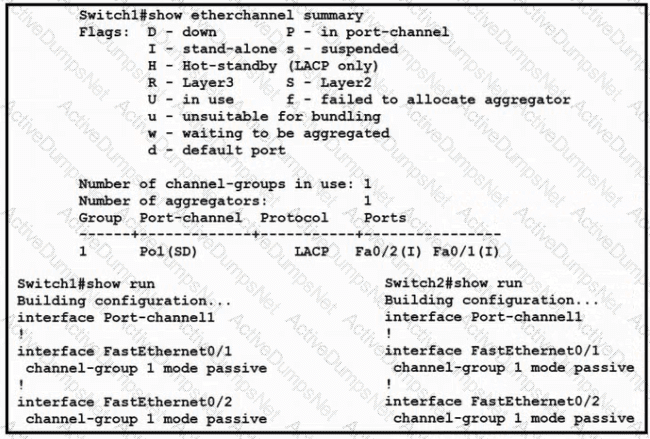
Which change to the configuration on Switch?
allows the two switches to establish an GtherChannel?
Which protocol requires authentication to transfer a backup configuration file from a router to a remote server?
A device detects two stations transmitting frames at the same time. This condition occurs after the first 64 bytes of the frame is received interface counter increments?
Refer to the exhibit.
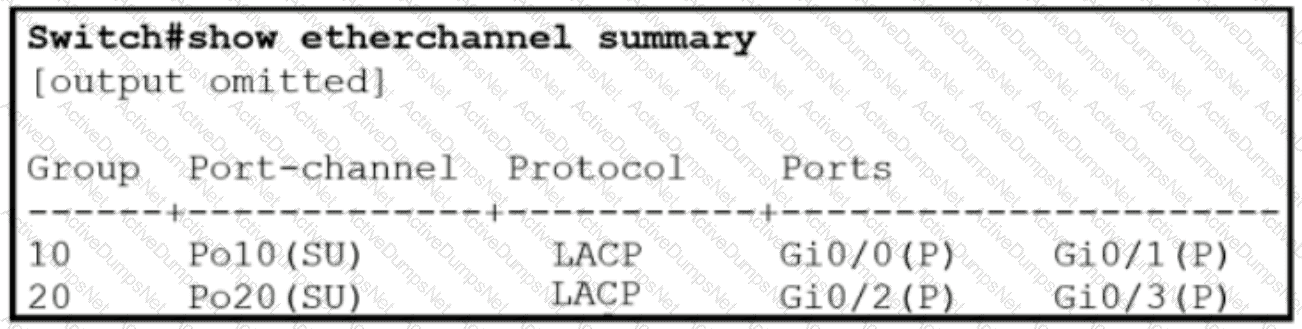
Which two commands were used to create port channel 10? (Choose two )

Refer to the exhibit.
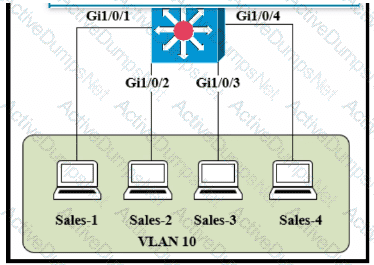
The entire contents of the MAC address table are shown. Sales-4 sends a data frame to Sales-1.
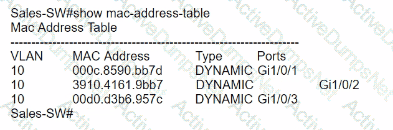
What does the switch do as it receives the frame from Sales-4?
Which configuration management mechanism uses TCP port 22 by default when communicating with managed nodes?
Which two must be met before SSH can operate normally on a Cisco IOS switch? (Choose two)
Using direct sequence spread spectrum, which three 2.4-GHz channels are used to limit collisions?
Which JSON data type is an unordered set of attribute- value pairs?
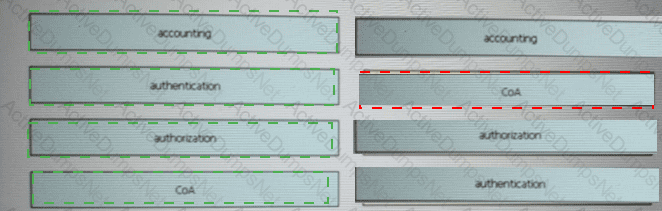
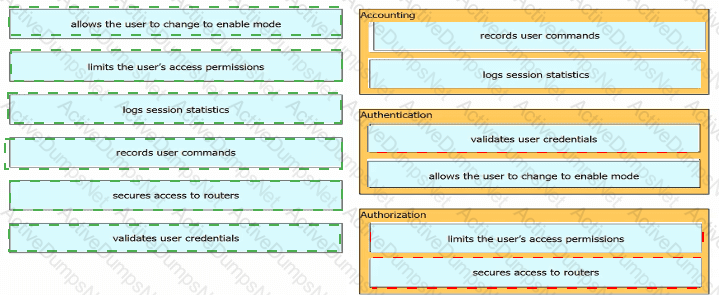
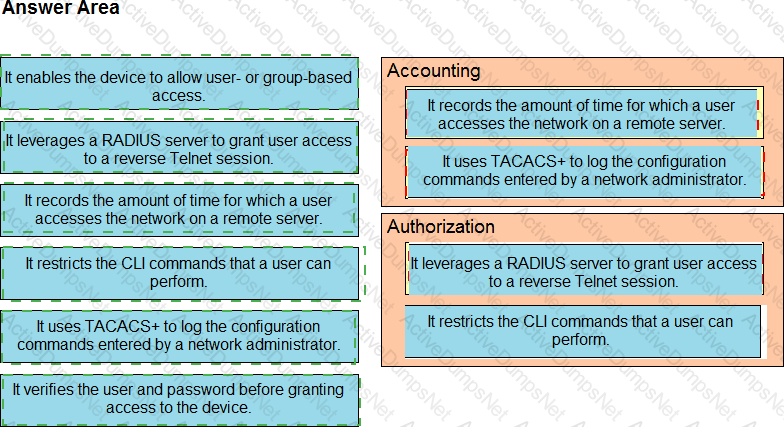
Drag and drop the AAA terms from the left onto the description on the right.

What benefit does controller-based networking provide versus traditional networking?
Refer to the exhibit.
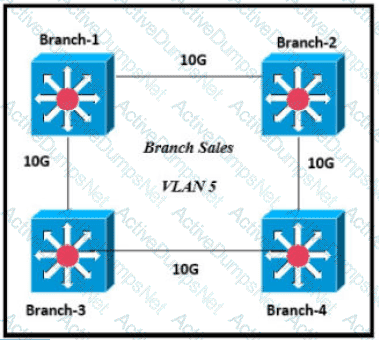
Only four switches are participating in the VLAN spanning-tree process.
Branch-1 priority 614440
Branch-2: priority 39082416
Branch-3: priority 0
Branch-4: root primary
Which switch becomes the permanent root bridge for VLAN 5?
Refer to the exhibit.
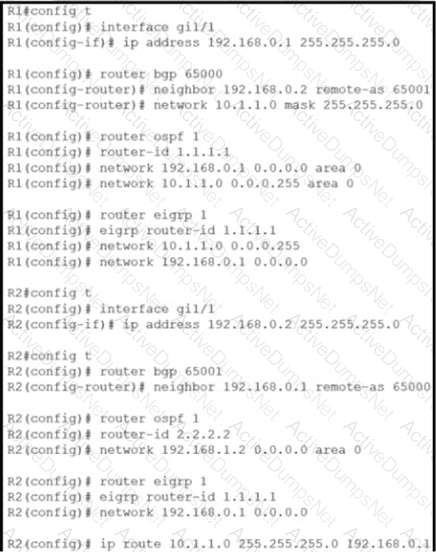
Router R2 is configured with multiple routes to reach network 10 1.1 0/24 from router R1. What protocol is chosen by router R2 to reach the destination network 10.1 1 0/24?
Which two tasks must be performed to configure NTP to a trusted server in client mode on a single network device? (Choose two)
Refer to the exhibit.
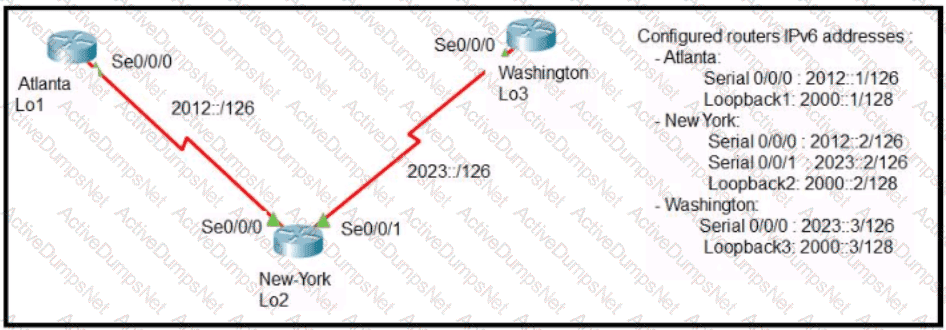
The New York router is configured with static routes pointing to the Atlanta and Washington sites. Which two tasks must be performed so that the Serial0/0/0 interfaces on the Atlanta and Washington routers can reach one another?
(Choose two.)
Refer to the exhibit.
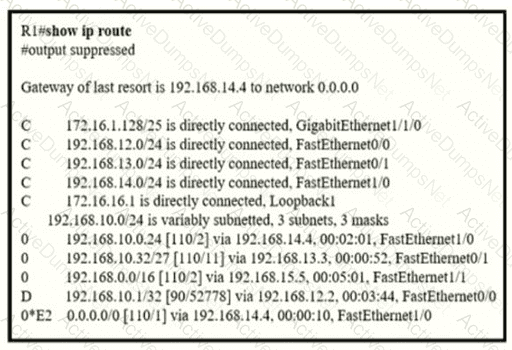
If R1 receives a packet destined to 172.161.1, to which IP address does it send the packet?
Refer to the exhibit.
An engineer is bringing up a new circuit to the MPLS provider on the Gi0/1 interface of Router1 The new circuit uses eBGP and teams the route to VLAN25 from the BGP path What s the expected behavior for the traffic flow for route 10.10.13.0/25?
Which type of IPv6 address is publicly routable in the same way as IPv4 public address?
Which action must be taken to assign a global unicast IPv6 address on an interface that is derived from the MAC address of that interface?
What prevents a workstation from receiving a DHCP address?
Drag the descriptions of device management from the left onto the types of device management on the right.
Refer to the exhibit.

What is the effect of this configuration?
which IPv6 address block forwards packets to a multicast address rather than a unicast address?
What is the effect when loopback interfaces and the configured router ID are absent during the OSPF Process configuration?
A network engineer must create a diagram of a multivendor network. Which command must be configured on the Cisco devices so that the topology of the network can be mapped?
A user configured OSPF in a single area between two routers A serial interface connecting R1 and R2 is running encapsulation PPP By default which OSPF network type is seen on this interface when the user types show ip ospf interface on R1 or R2?
Which QoS tool is used to optimize voice traffic on a network that is primarily intended for data traffic?
Refer to Exhibit.
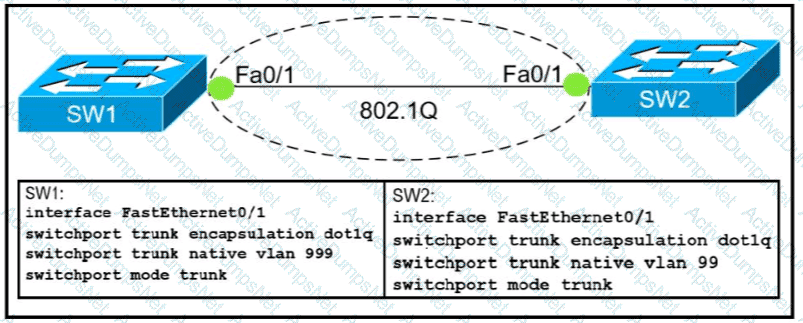
Which action do the switches take on the trunk link?
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
How does WPA3 improve security?
Refer to the exhibit.
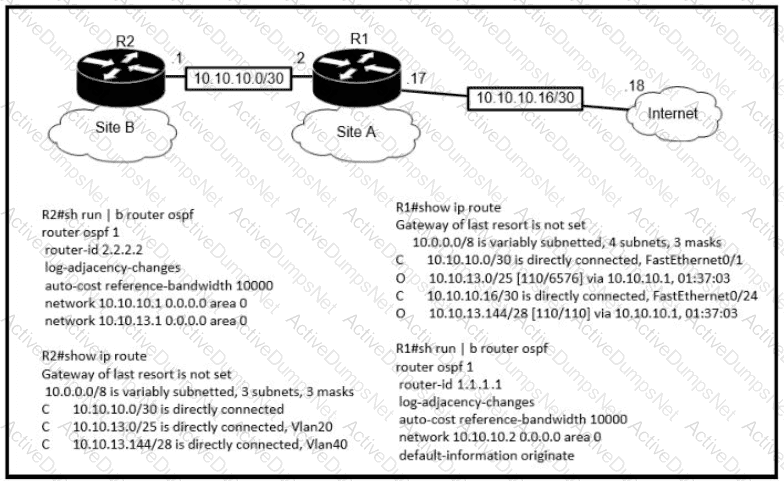
The default-information originate command is configured under the R1 OSPF configuration After testing workstations on VLAN 20 at Site B cannot reach a DNS server on the Internet Which action corrects the configuration issue?
Which technology must be implemented to configure network device monitoring with the highest security?
Refer to the exhibit.
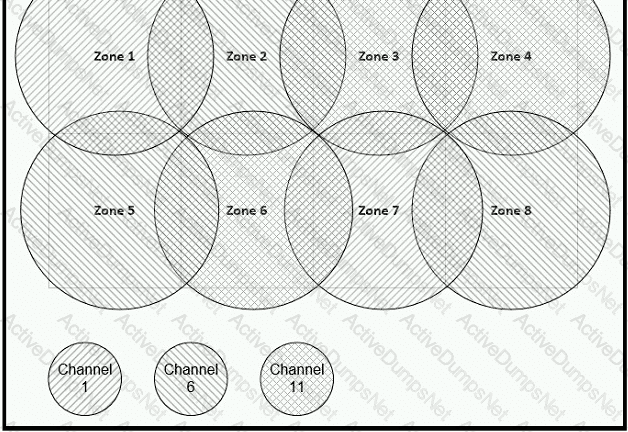
Between which zones do wireless users expect to experience intermittent connectivity?
Refer to the exhibit.
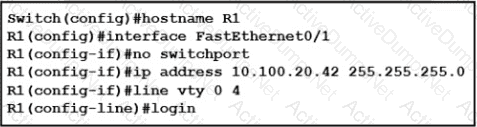
An engineer booted a new switch and applied this configuration via the console port. Which additional configuration must be applied to allow administrators to authenticate directly to enable privilege mode via Telnet using a local username and password?
An implementer is preparing hardware for virtualization to create virtual machines on a host. What is needed to provide communication between hardware and virtual machines?
What is the function of a server?
Which IPv6 address type provides communication between subnets and is unable to route on the Internet?
Refer to the exhibit.
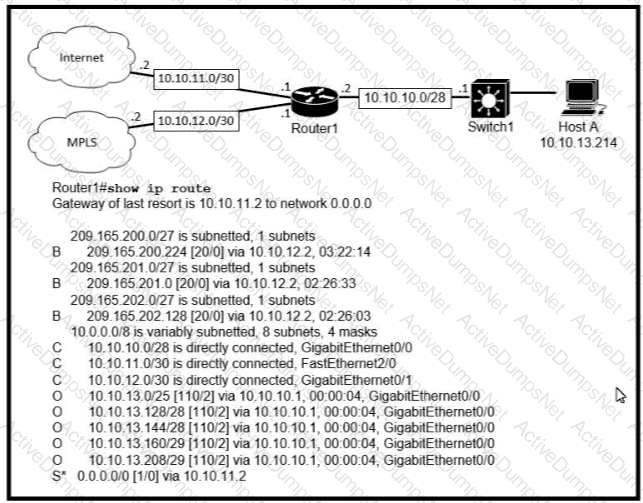
Which prefix does Router 1 use for traffic to Host A?
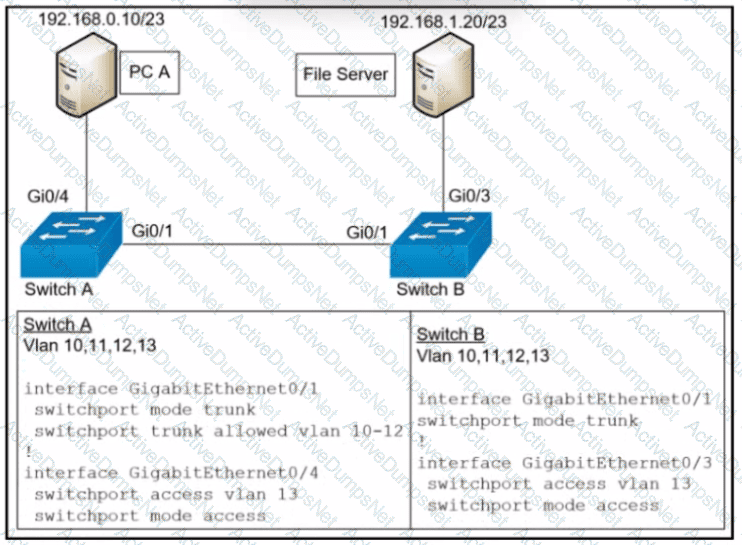
Refer to the exhibit.
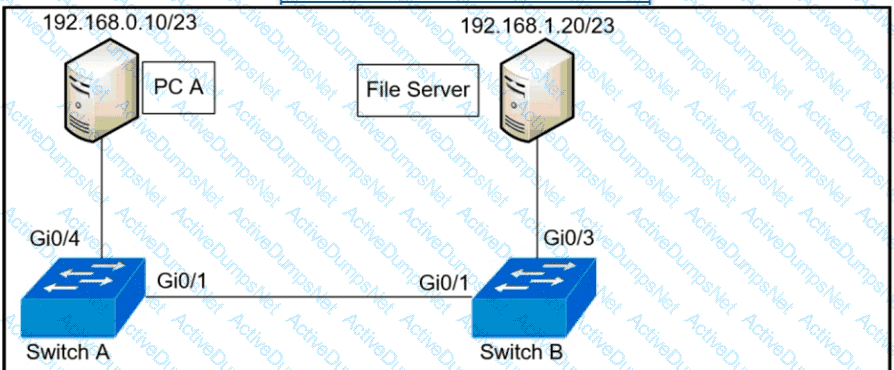
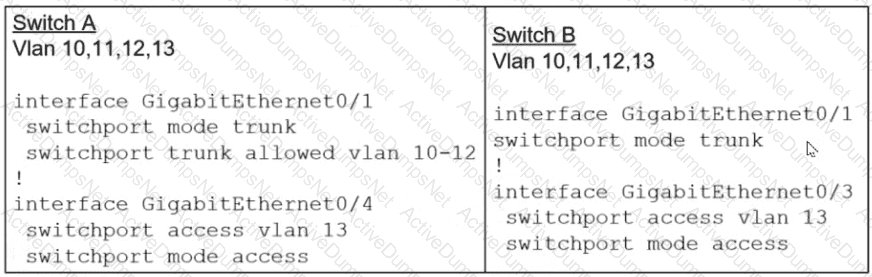
A network administrator assumes a task to complete the connectivity between PC A and the File Server. Switch A and Switch B have been partially configured with VLAN 10, 11, 12, and 13. What is the next step in the configuration?
When OSPF learns multiple paths to a network, how does it select a route?
What are two reasons for an engineer to configure a floating state route? (Choose two)
Refer to Exhibit.
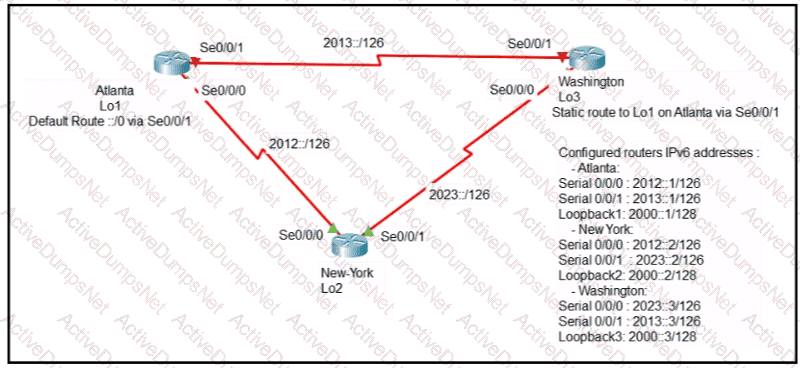
An engineer is configuring the NEW York router to reach the Lo1 interface of the Atlanta router using interface Se0/0/0 as the primary path. Which two commands must be configured on the New York router so that it can reach the Lo1 interface of the Atlanta router via Washington when the link between New York and Atlanta goes down? (Choose two)
Why does a switch flood a frame to all ports?
An office has 8 floors with approximately 30-40 users per floor What command must be configured on the router Switched Virtual Interface to use address space efficiently?
What is a similarly between 1000BASE-LX and 1000BASE-T standards?
Refer to the exhibit.
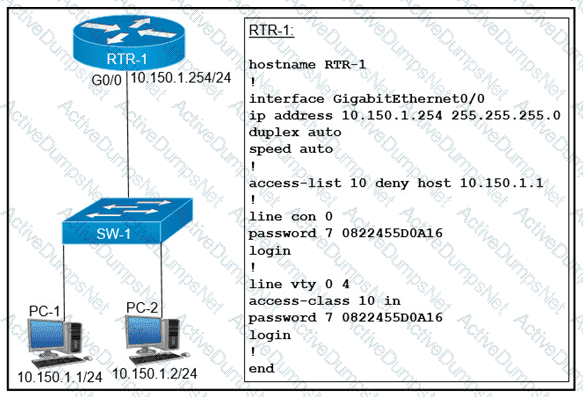
An access list is created to deny Telnet access from host PC-1 to RTR-1 and allow access from all other hosts A Telnet attempt from PC-2 gives this message:"% Connection refused by remote host" Without allowing Telnet access from PC-1, which action must be taken to permit the traffic?
Refer to the exhibit.
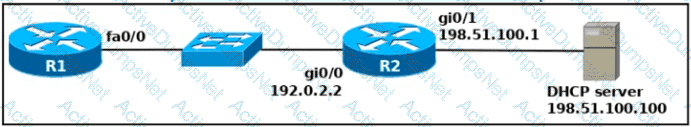
An engineer deploys a topology in which R1 obtains its IP configuration from DHCP. If
the switch and DHCP server configurations are complete and correct. Which two sets of commands must be configured on R1 and R2 to complete the task? (Choose two)
Which interface mode must be configured to connect the lightweight APs in a centralized architecture?
Refer to the exhibit.

A network engineer must update the configuration on Switch2 so that it sends LLDP packets every minute and the information sent via LLDP is refreshed every 3 minutes Which configuration must the engineer apply?
A)

B)
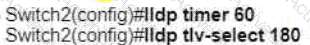
C)
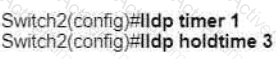
D)
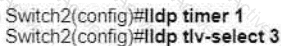
Refer to the exhibit.
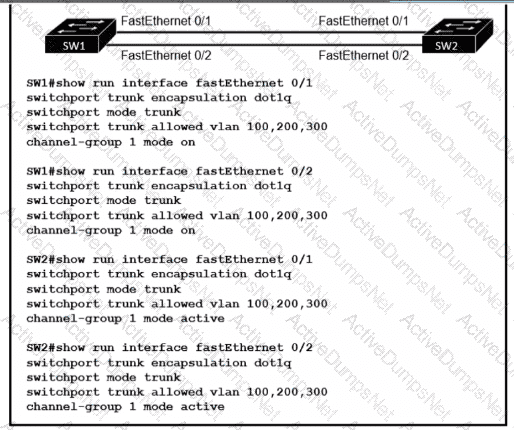
An engineer built a new L2 LACP EtherChannel between SW1 and SW2 and executed these show commands to verify the work. Which additional task allows the two switches to establish an LACP port channel?
Refer to the exhibit.
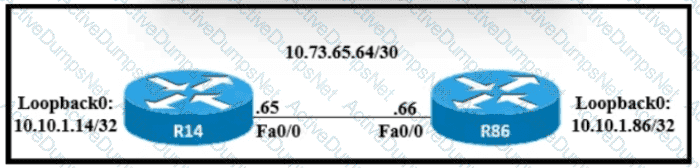
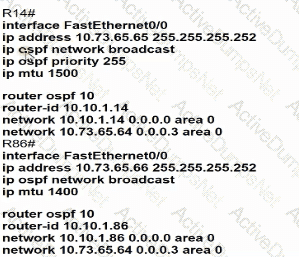
A static route must be configured on R14 to forward traffic for the 172 21 34 0/25 network that resides on R86 Which command must be used to fulfill the request?
What provides centralized control of authentication and roaming In an enterprise network?
Refer to the exhibit.
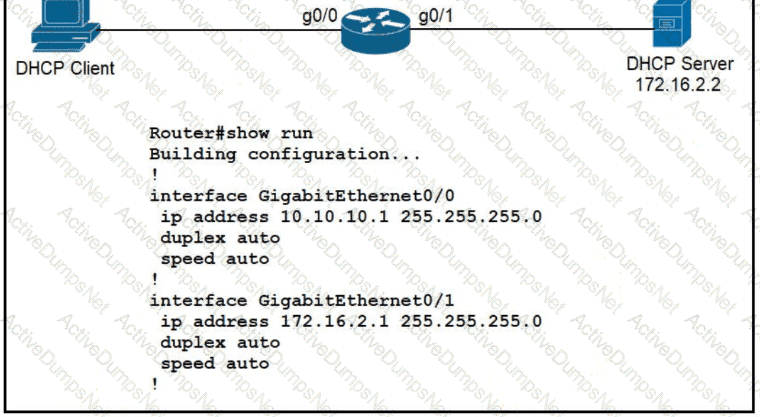
An engineer is configuring a new router on the network and applied this configuration. Which additional configuration allows the PC to obtain its IP address from a DHCP server?
A network engineer must configure two new subnets using the address block 10 70 128 0/19 to meet these requirements:
• The first subnet must support 24 hosts
• The second subnet must support 472 hosts
• Both subnets must use the longest subnet mask possible from the address block
Which two configurations must be used to configure the new subnets and meet a requirement to use the first available address in each subnet for the router interfaces? (Choose two )
Which QoS traffic handling technique retains excess packets in a queue and reschedules these packets for later transmission when the configured maximum bandwidth has been surpassed?
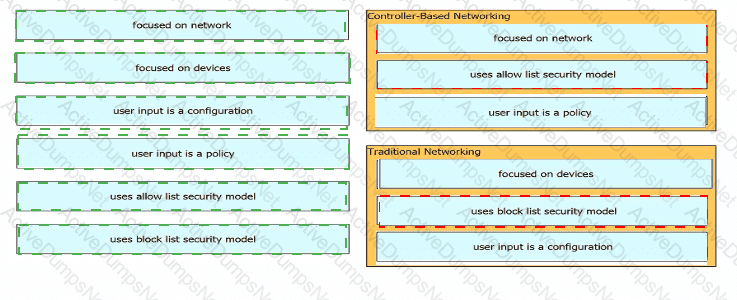
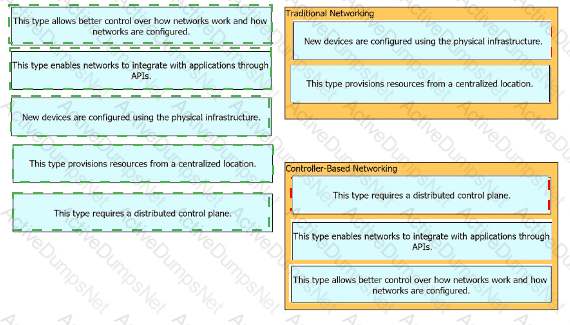
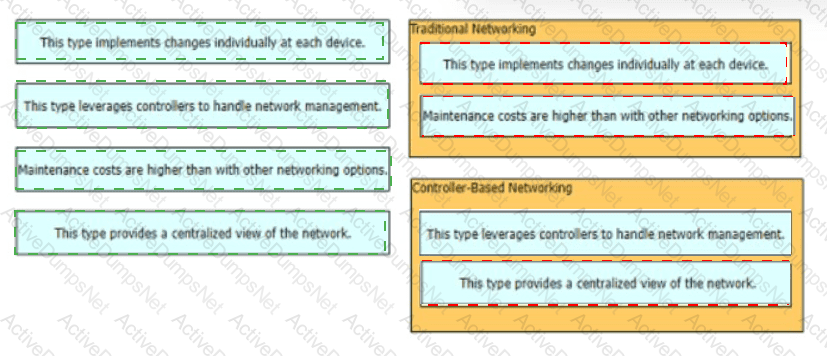
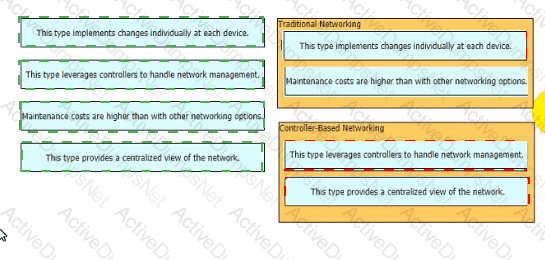
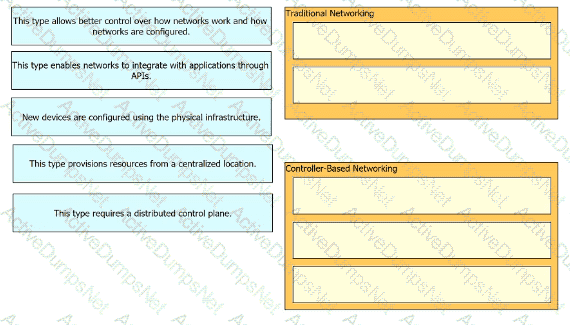
Drag and drop the characteristics of networking from the left onto the networking types on the right.
Which PoE mode enables powered-device detection and guarantees power when the device is detected?
Refer to the exhibit.
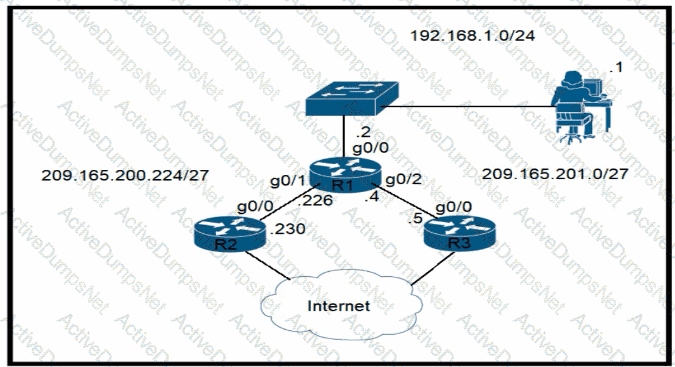
Router R1 currently is configured to use R3 as the primary route to the Internet, and the route uses the default administrative distance settings. A network engineer must configure R1 so that it uses R2 as a backup, but only if R3 goes down. Which command must the engineer configure on R1 so that it correctly uses R2 as a backup route, without changing the administrative distance configuration on the link to R3?
Refer to the exhibit.

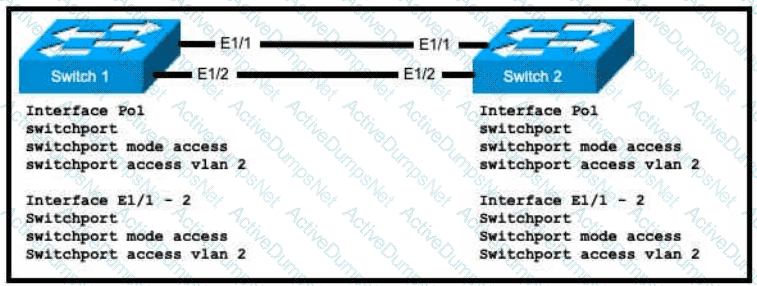
Traffic that is flowing over interface TenGigabitEthernet0/0 experiences slow transfer speeds. What is the reason for the issue?
Refer to the exhibit.
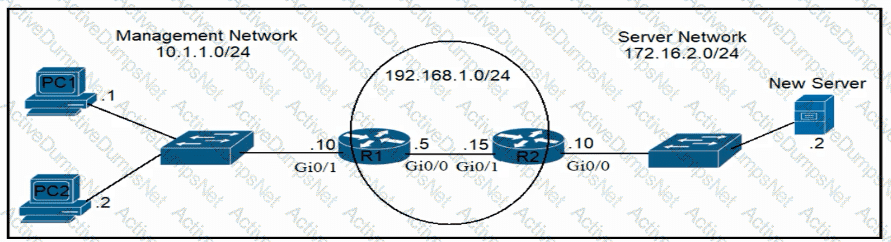
An engineer is updating the R1 configuration to connect a new server to the management network. The PCs on the management network must be blocked from pinging the default gateway of the new server. Which command must be configured on R1 to complete the task?
Refer to the exhibit.
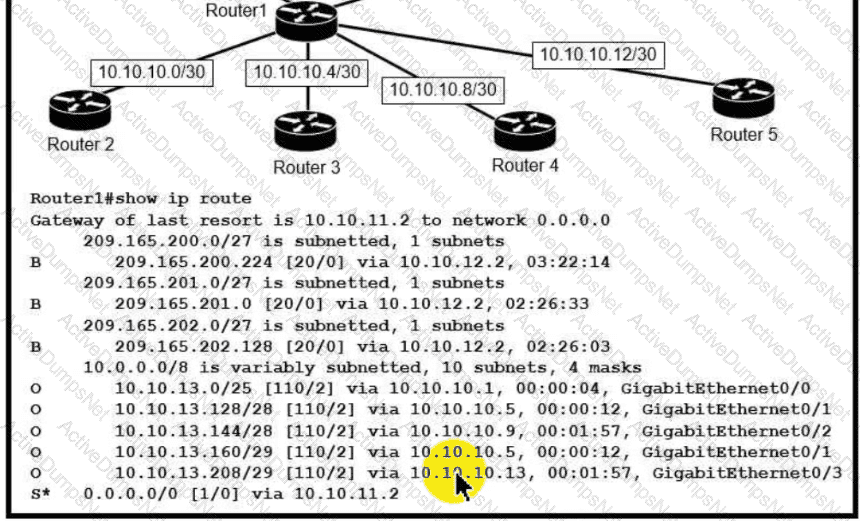
Which next-hop IP address does Routed use for packets destined to host 10 10.13.158?
What is the function of the controller in a software-defined network?
What causes a port to be placed in the err-disabled state?
Which QoS per-hop behavior changes the value of the ToS field in the IPv4 packet header?
Refer to the exhibit.
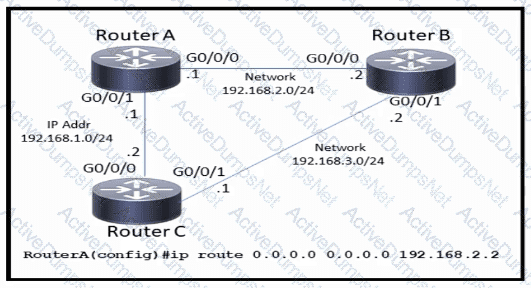
Which command must be issued to enable a floating static default route on router A?
Refer to the exhibit.

The router has been configured with a supernet to accommodate the requirement for 380 users on a subnet The requirement already considers 30% future growth. Which configuration verifies the IP subnet on router R4?
A)
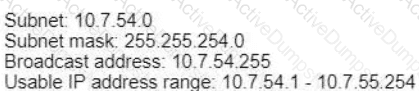
B)
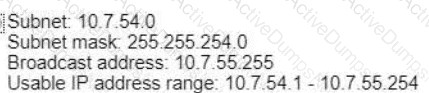
C)
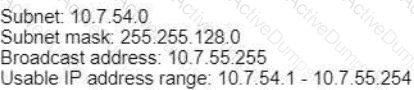
D)
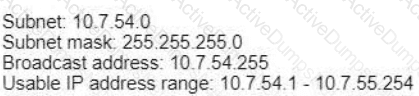
Which action implements physical access control as part of the security program of an organization?
Drag and drop the statements about networking from the left onto the corresponding networking types on the right.
A Cisco engineer is configuring a factory-default router with these three passwords:
• The user EXEC password for console access is p4ssw0rd1
• The user EXEC password for Telnet access is s3cr3t2
• The password for privileged EXEC mode is pnv4t3p4ss Which command sequence must the engineer configured
A)
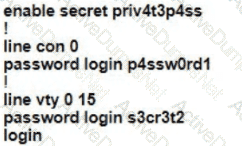
B)
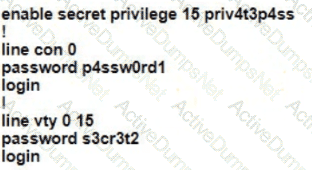
C)
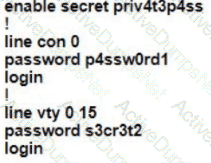
D)

Which Layer 2 switch function encapsulates packets for different VLANs so that the packets traverse the same port and maintain traffic separation between the VLANs?
An engineer must configure R1 for a new user account. The account must meet these requirements:
* It must be configured in the local database.
* The username is engineer.
* It must use the strongest password configurable. Which command must the engineer configure on the router?
Refer to the exhibit.
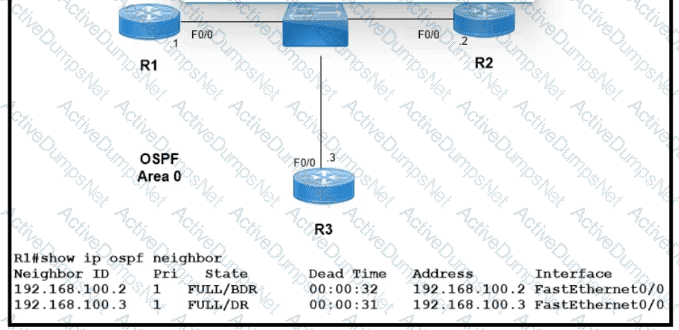
Which two configurations must the engineer apply on this network so that R1 becomes the DR? (Choose two.)
A)

B)

C)
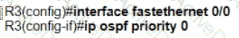
D)

E)

Refer to the exhibit.
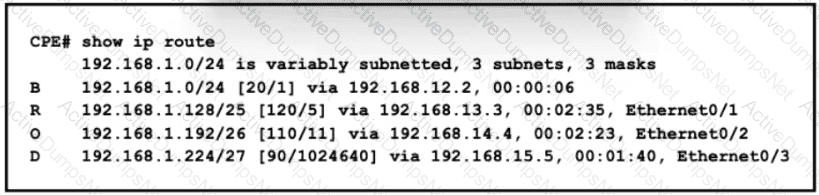
All traffic enters the CPE router from interface Serial0/3 with an IP address of 192 168 50 1 Web traffic from the WAN is destined for a LAN network where servers are load-balanced An IP packet with a destination address of the HTTP virtual IP of 192 1681 250 must be forwarded Which routing table entry does the router use?
Refer to the exhibit.
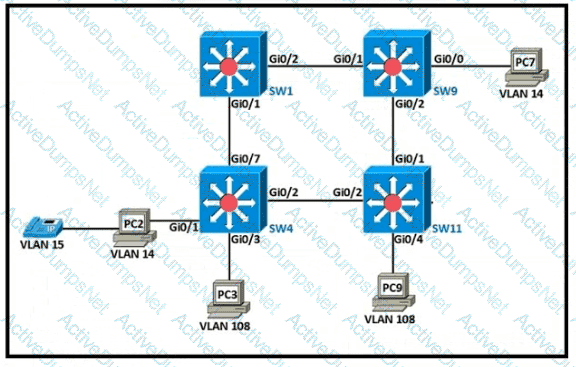
The following must be considered:
• SW1 is fully configured for all traffic
• The SW4 and SW9 links to SW1 have been configured
• The SW4 interface Gi0/1 and Gi0/0 on SW9 have been configured
• The remaining switches have had all VLANs adde d to their VLAN database
Which configuration establishes a successful ping from PC2 to PC7 without interruption to traffic flow between other PCs?
A)

B)

C)

D)

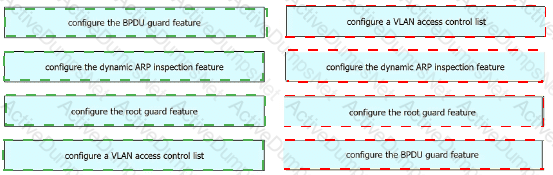
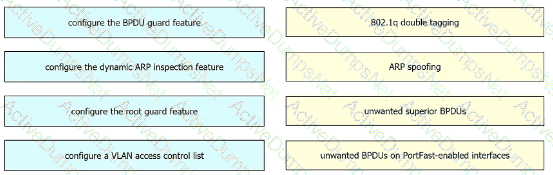
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
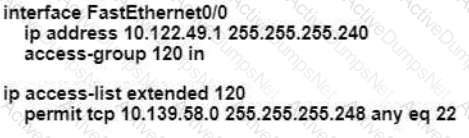
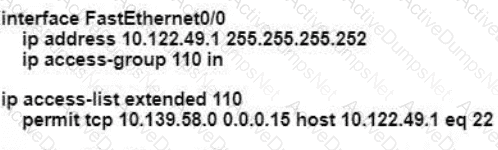
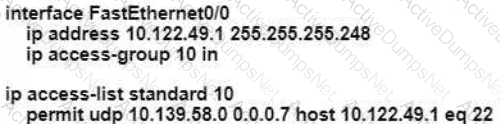
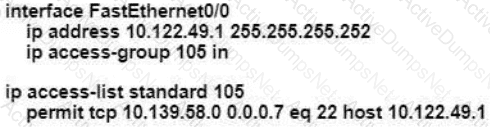
An engineer is configuring remote access to a router from IP subnet 10.139.58.0/28. The domain name, crypto keys, and SSH have been configured. Which configuration enables the traffic on the destination router?
A)
B)
C)
D)
Refer to the exhibit.
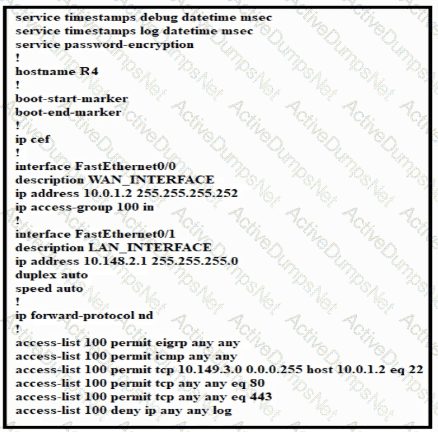
Which configuration enables DHCP addressing for hosts connected to interface FastEthernetO/1 on router R4?
OSPF must be configured between routers R1 and R2. Which OSPF configuration must be applied to router R1 to avoid a DR/BDR election?
Refer to the exhibit.
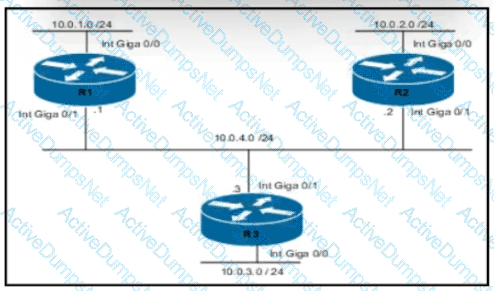
Routers R1 and R3 have the default configuration The router R2 priority is set to 99 Which commands on R3 configure it as the DR in the 10.0 4.0/24 network?
Refer to the exhibit.
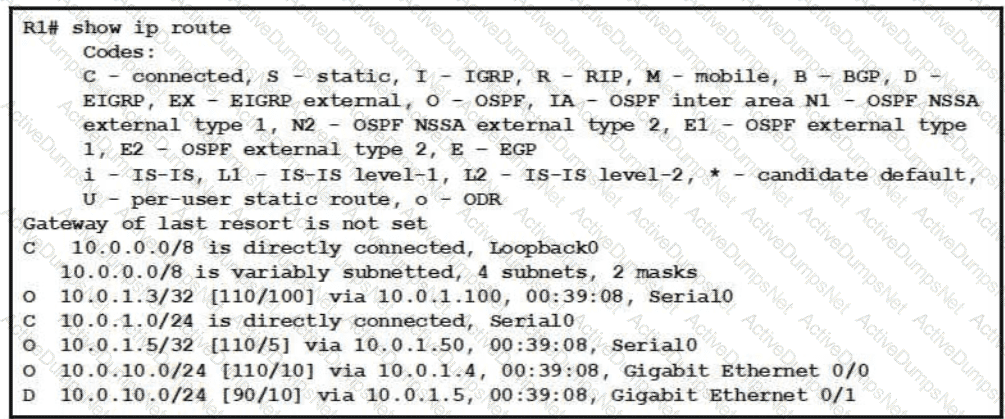
Web traffic is coming in from the WAN interface. Which route takes precedence when the router is processing traffic destined for the LAN network at 10 0.10.0/24?
Which wireless security protocol relies on Perfect Forward Secrecy?
Refer to the exhibit.
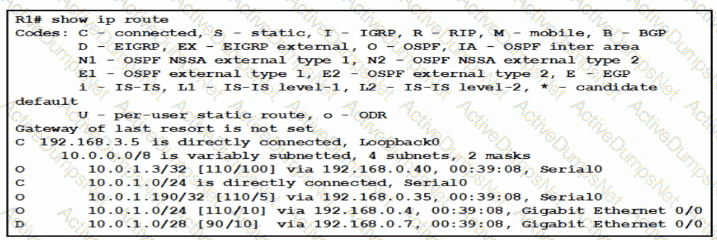
Traffic sourced from the loopback0 Interface is trying to connect via ssh to the host at 10.0.1.15. What Is the next hop to the destination address?
Refer to the exhibit.
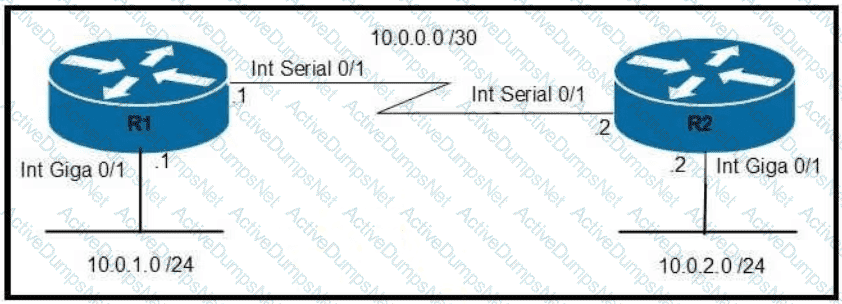
Which command configures OSPF on the point-to-point link between routers R1 and R2?
Which protocol is used for secure remote CLI access?
Refer to the exhibit.
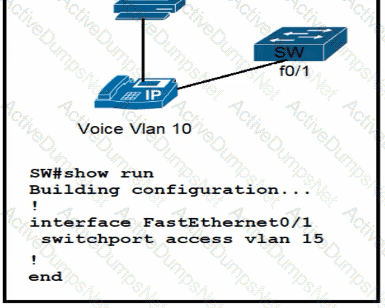
All VLANs are present in the VLAN database. Which command sequence must be applied to complete the configuration?
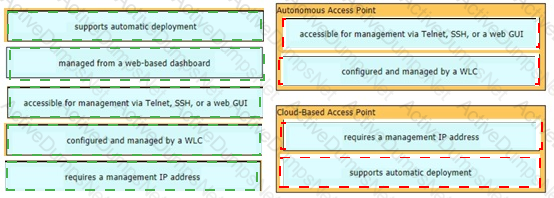
Drag and drop the facts about wireless architectures from the left onto the types of access point on the right. Not all options are used.
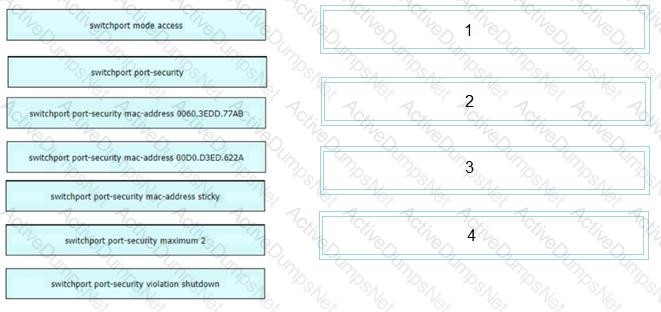
An engineer is tasked to configure a switch with port security to ensure devices that forward unicasts multicasts and broadcasts are unable to flood the port The port must be configured to permit only two random MAC addresses at a time Drag and drop the required configuration commands from the left onto the sequence on the right Not all commands are used.
What are two benefits of FHRPs? (Choose two.)
Refer to the exhibit.
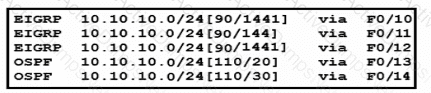
Packets received by the router from BGP enter via a serial interface at 209.165.201.10. Each route is present within the routing table. Which interface is used to forward traffic with a destination IP of 10.10.10.24?
Refer to the exhibit.
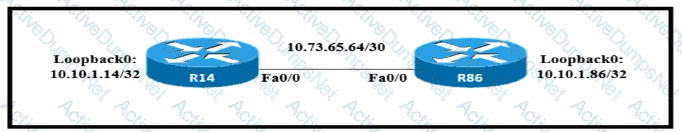
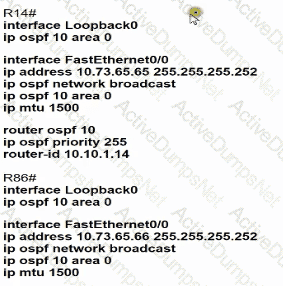
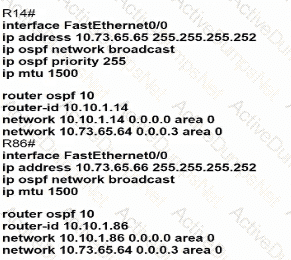
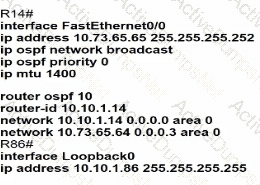
Which configuration allows routers R14 and R86 to form an OSPFv2 adjacency while acting as a central point for exchanging OSPF information between routers?
A)
B)
C)
D)
Which WLC management connection type is vulnerable to man-in-the-middle attacks?
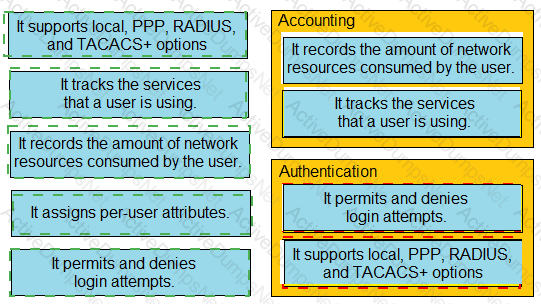
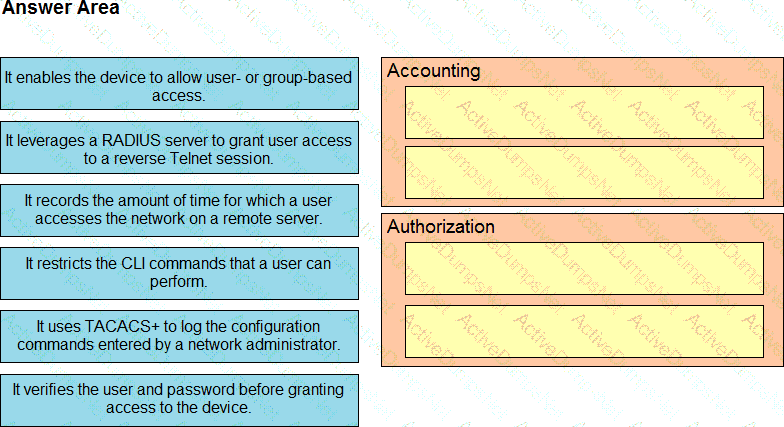
Which characteristic differentiates the concept of authentication from authorization and accounting?
Which type of IPv6 address is similar to a unicast address but is assigned to multiple devices on the same network at the same time?
Refer to the exhibit.
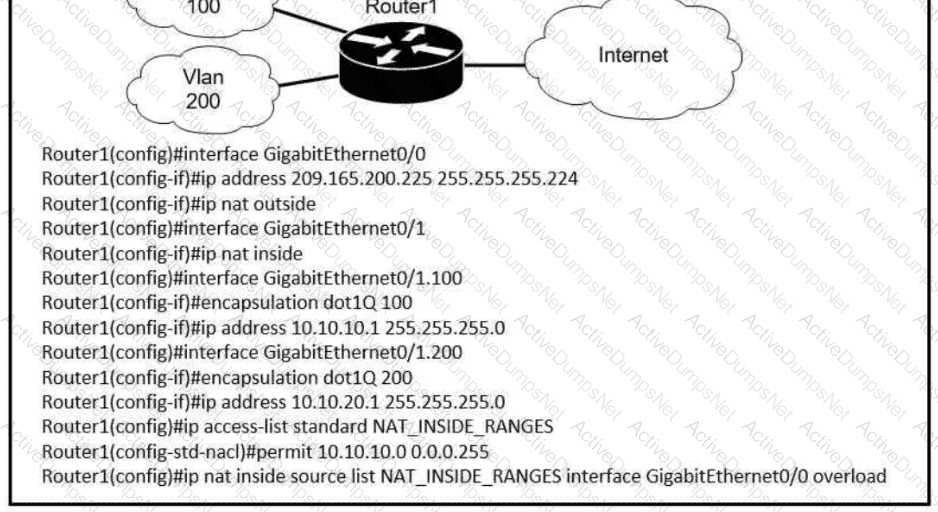
Users on existing VLAN 100 can reach sites on the Internet. Which action must the administrator take to establish connectivity to the Internet for users in VLAN 200?
Refer to the exhibit.
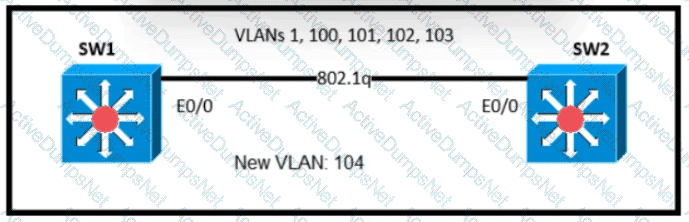
An engineer is asked to insert the new VLAN into the existing trunk without modifying anything previously configured Which command accomplishes this task?
Refer to the exhibit.
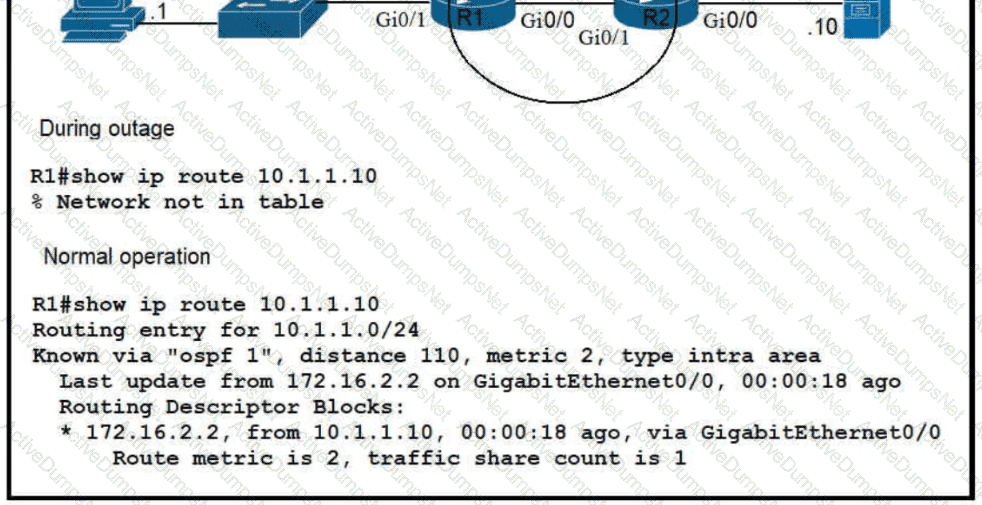
Which route must be configured on R1 so that OSPF routing is used when OSPF is up. but the server is still reachable when OSPF goes down?
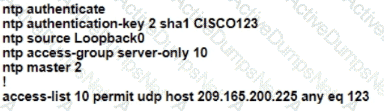
R1 as an NTP server must have:
• NTP authentication enabled
• NTP packets sourced from Interface loopback 0
• NTP stratum 2
• NTP packets only permitted to client IP 209.165 200 225
How should R1 be configured?
A)
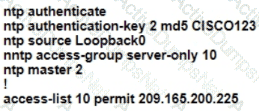
B)
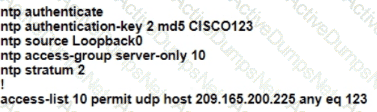
C)
D)
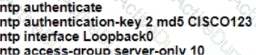
Which type of network attack overwhelms the target server by sending multiple packets to a port until the half-open TCP resources of the target are exhausted?
Refer to the exhibit.
An engineer is configuring an EtherChannel using LACP between Switches 1 and 2 Which configuration must be applied so that only Switch 1 sends LACP initiation packets?
Refer to the exhibit.
What is a reason for poor performance on the network interface?
Refer to the exhibit.
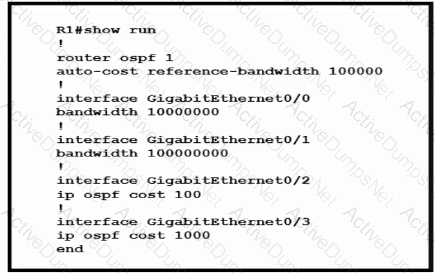
Router R1 resides in OSPF Area 0. After updating the R1 configuration to influence the paths that it will use to direct traffic, an engineer verified that each of the four Gigabit interfaces has the same route to 10.10.0.0/16. Which interface will R1 choose to send traffic to reach the route?
Refer to the exhibit.
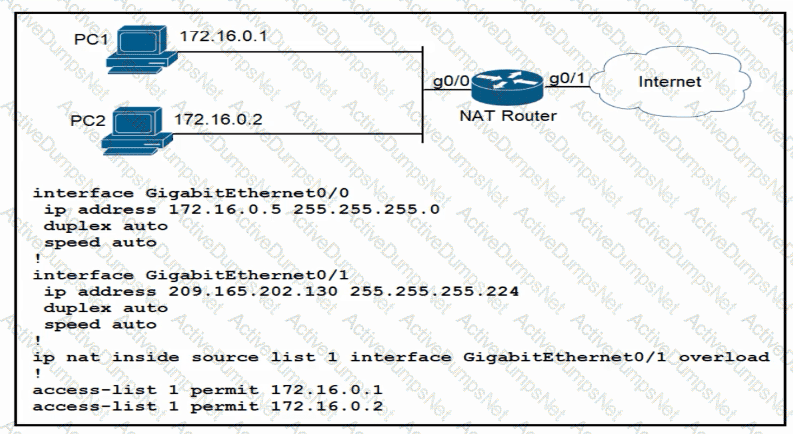
How should the configuration be updated to allow PC1 and PC2 access to the Internet?
Refer to the exhibit.
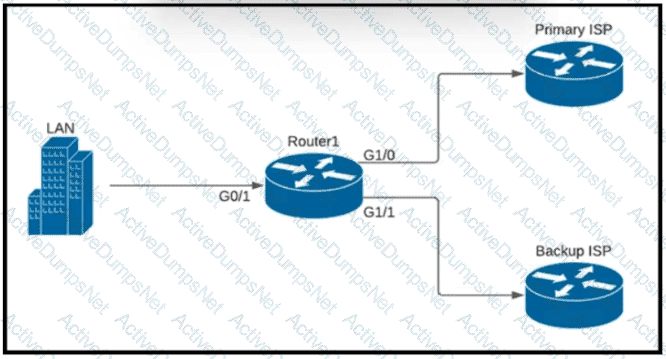
A company is configuring a failover plan and must implement the default routes in such a way that a floating static route will assume traffic forwarding when the primary link goes down. Which primary route configuration must be used?
Refer to the exhibit.
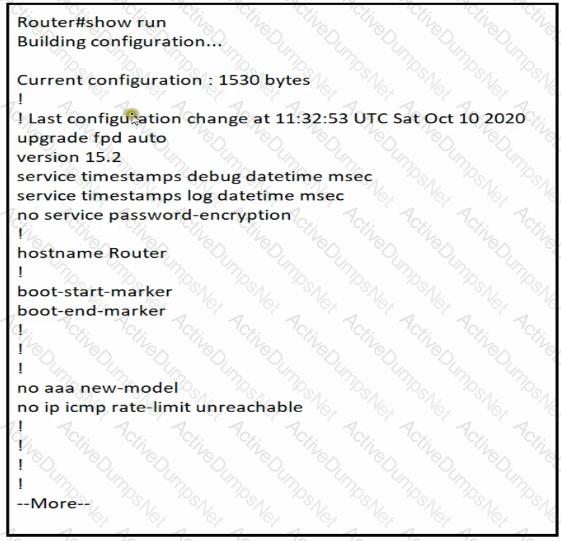
Which minimum configuration items are needed to enable Secure Shell version 2 access to R15?
A)

B)
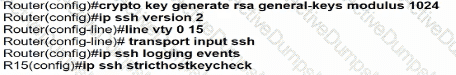
C)

D)

Refer to the exhibit.
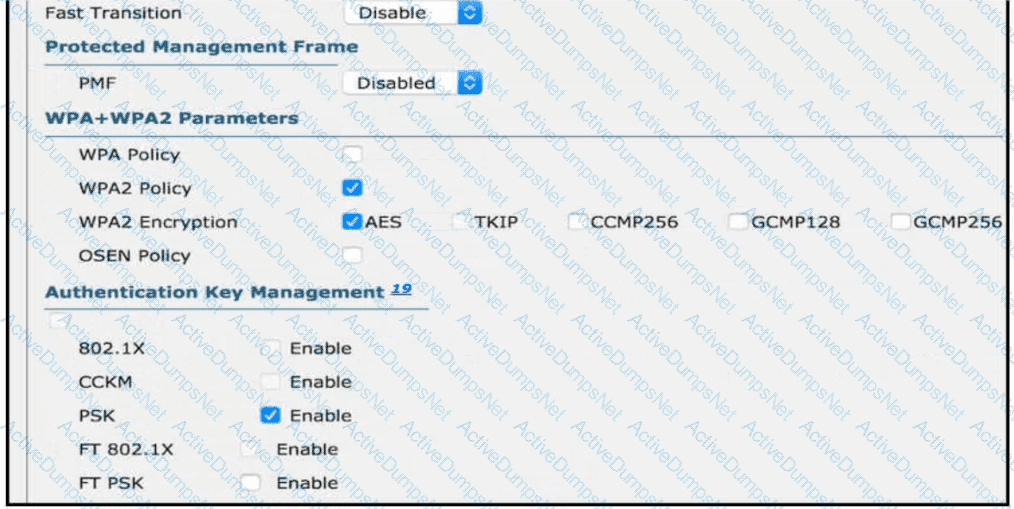
Users need to connect to the wireless network with IEEE 802. 11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building What must be the configuration of the connection?
A network engineer must implement an IPv6 configuration on the vlan 2000 interface to create a routable locally-unique unicast address that is blocked from being advertised to the internet. Which configuration must the engineer apply?
A network engineer is installing an IPv6-only capable device. The client has requested that the device IP address be reachable only from the internal network. Which type of IPv6 address must the engineer assign?
What is one reason to implement LAG on a Cisco WLC?
How does Rapid PVST+ create a fast loop-free network topology?
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
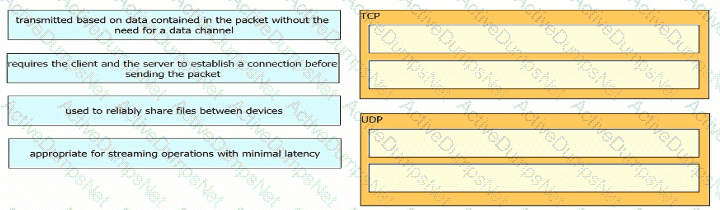
Refer to the exhibit.
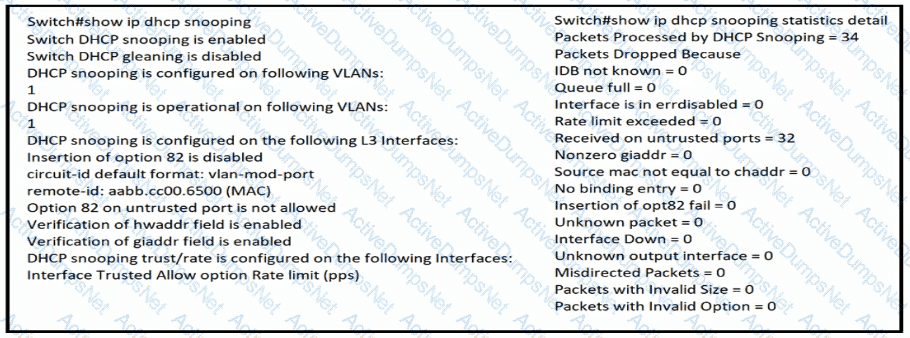
The DHCP server and clients are connected to the same switch. What is the next step to complete the DHCP configuration to allow clients on VLAN 1 to receive addresses from the DHCP server?
A network engineer is configuring a switch so that it is remotely reachable via SSH. The engineer has already configured the host name on the router. Which additional command must the engineer configure before entering the command to generate the RSA key?
What is a function of an endpoint on a network?
Refer to the exhibit.
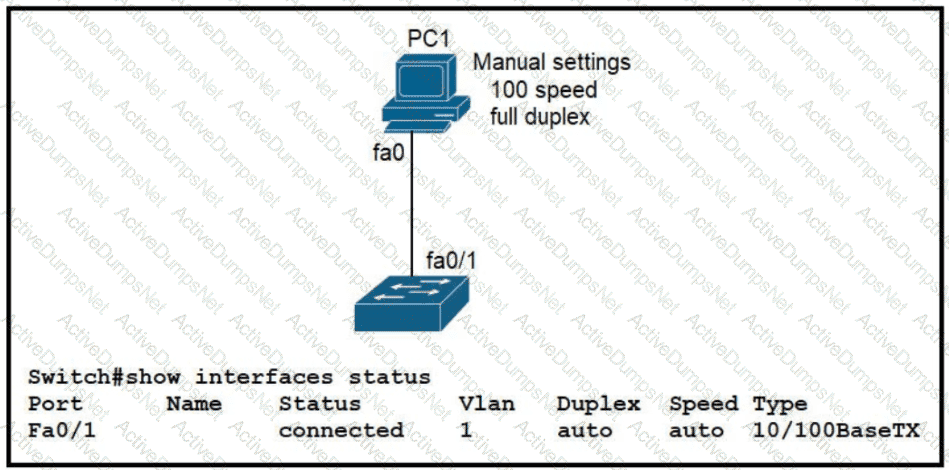
The link between PC1 and the switch is up. but it is performing poorly. Which interface condition is causing the performance problem?
A Cisco engineer must configure a single switch interface to meet these requirements
• accept untagged frames and place them in VLAN 20
• accept tagged frames in VLAN 30 when CDP detects a Cisco IP phone
Which command set must the engineer apply?
A)

B)

C)

D)

Refer to the exhibit.
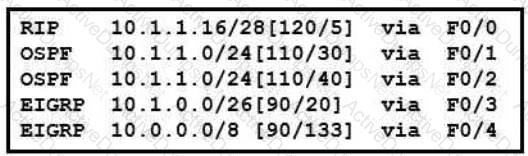
Packets received by the router from BGP enter via a serial interface at 209 165 201 1 Each route is present within the routing table Which interface is used to forward traffic with a destination IP of 10.1.1.19?
Refer to the exhibit.
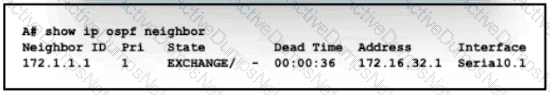
An engineer assumes a configuration task from a peer Router A must establish an OSPF neighbor relationship with neighbor 172 1 1 1 The output displays the status of the adjacency after 2 hours. What is the next step in the configuration process for the routers to establish an adjacency?
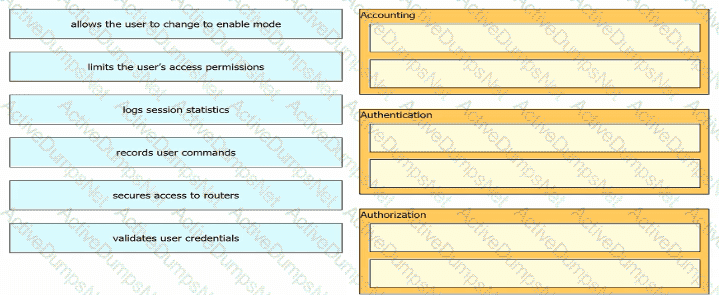
Drag and drop the descriptions of AAA services from the left onto the corresponding services on the right.
Refer to the exhibit.
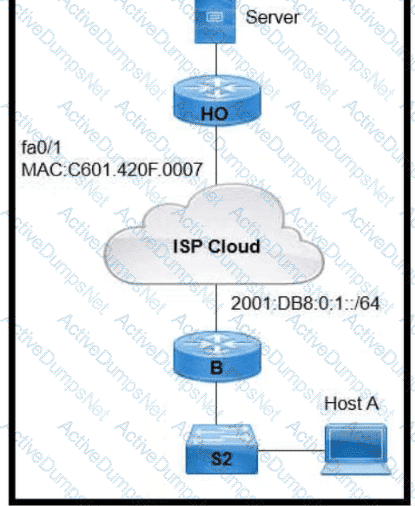
An engineer is configuring the HO router. Which IPv6 address configuration must be applied to the router fa0'1 interface for the router to assign a unique 64-brt IPv6 address to Itself?
Refer to the exhibit.
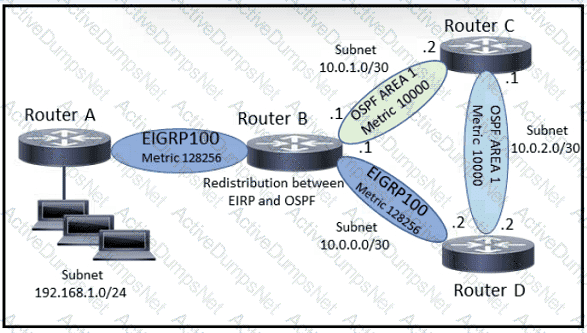
A network engineer executes the show ip route command on router D. What is the next hop to network 192.168 1 0/24 and why?
Refer to the exhibit.
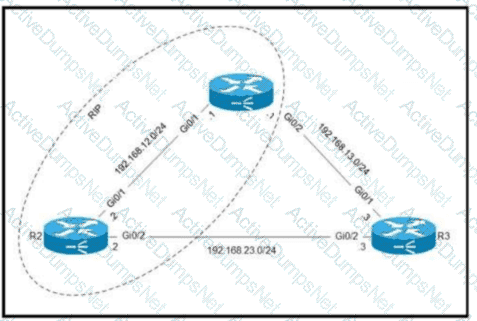
Routers R1 and R2 are configured with RIP as the dynamic routing protocol. A network engineer must configure R1 with a floating static route to serve as a backup route to network 192.168.23.0. Which command must the engineer configure on R1?
What is the put method within HTTP?
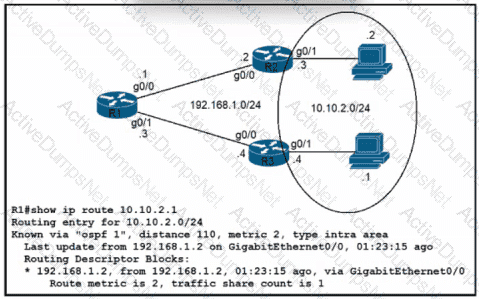
Refer to the exhibit. Traffic from R1 to the 10.10.2.0/24 subnet uses 192.168.1.2 as its next hop. A network engineer wants to update the R1 configuration so that traffic with destination 10.10.2.1 passes through router R3, and all other traffic to the 10.10.2.0/24 subnet passes through R2.
Which command must be used?
A network engineer must configure an interface with IP address 10.10.10.145 and a subnet mask equivalent to 11111111.11111111.11111111.11111000. Which subnet mask must the engineer use?
Refer to the exhibit.
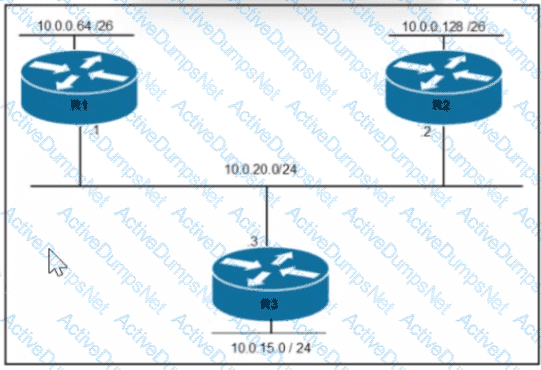
Rooter R1 is added to the network and configured with tie 10 0 0 64/26 and 10.0.20.0/24 subnets However traffic destined for the LAN on R3 is not access. Which command when executed on R1 defines a tunic route to reach the R3 LAN?
A)
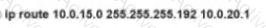
B)
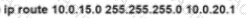
C)
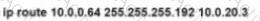
What is a valid IPv6 address record in DNS?
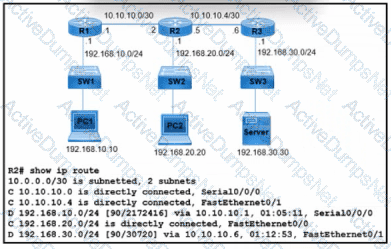
Refer to the exhibit. What is the next-hop IP address for R2 so that PC2 reaches the application server via EIGRP?
Which two IPv6 addresses are used to provide connectivity between two routers on a shared link? (Choose two)
Refer to the exhibit.
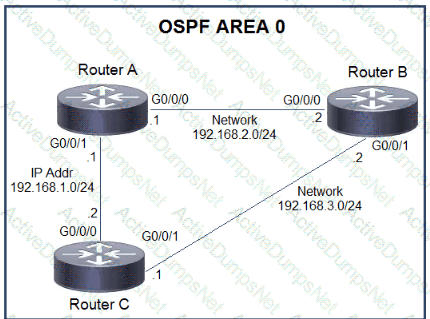
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
Drag and drop the statements about networking from me left onto the corresponding networking types on the right
What must be considered before deploying virtual machines?
What must be considered before deploying virtual machines?
Which functionality is provided by the console connection on a Cisco WLC?
Drag and drop each characteristic of device-management technologies from the left onto the deployment type on the right.
Which syslog severity level is considered the most severe and results in the system being considered unusable?
Refer to the exhibit.
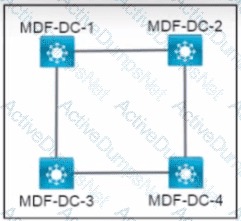
All interfaces are in the same VLAN. All switches are configured with the default STP priorities. During the STP electronics, which switch becomes the root bridge?
Drag and drop the statements about AAA from the left onto the corresponding AAA services on the right. Not all options are used.
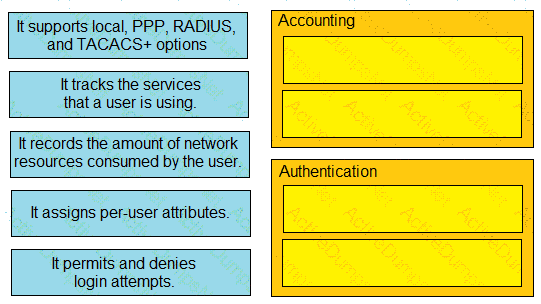
Which is a fact related to FTP?
When should an engineer implement a collapsed-core architecture?
Refer to the exhibit.
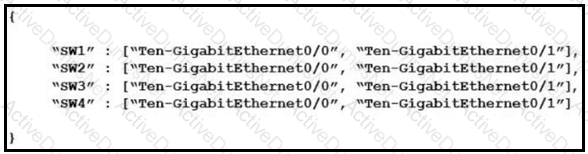
How many JSON objects are presented?
Refer to the exhibit.
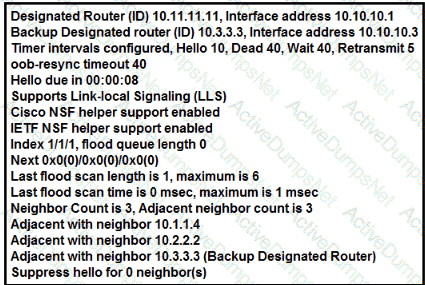
The show ip ospf interface command has been executed on R1. How is OSPF configured?
What must be considered for a locally switched FlexConnect AP if the VLANs that are used by the AP and client access are different?
How does frame switching function on a switch?
Which cipher is supported for wireless encryption only with the WPA2 standard?
Drag and drop the AAA features from the left onto the corresponding AAA security services on the right. Not all options are used.
Refer to the exhibit.
What is the subnet mask of the route to the 10.10.13.160 prefix?
What is a purpose of traffic shaping?
Refer to the exhibit.
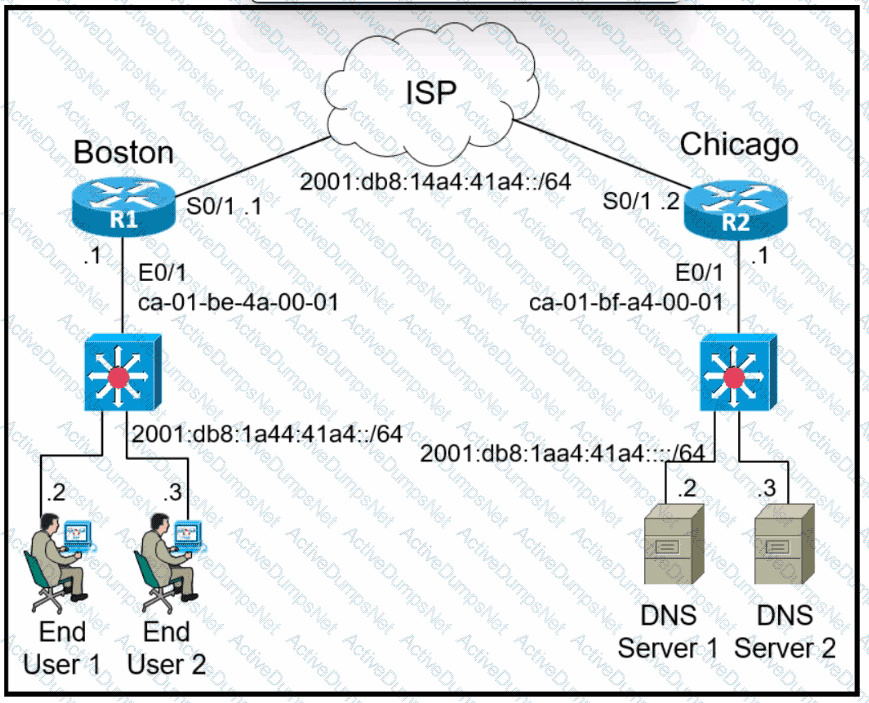
Refer to the exhibit. The IPv6 address for the LAN segment on router R1 must be configured using the EUI-64 format. When configured which ipv6 address is produced by the router?
Refer to the exhibit.
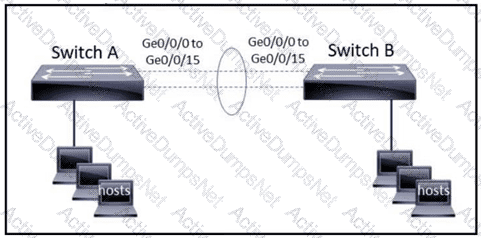
The EtherChannel is configured with a speed of 1000 and duplex as full on both ends of channel group 1. What is the next step to configure the channel on switch A to respond to but not initiate LACP communication?
Drag and drop the statements about networking from the left onto the corresponding networking types on the right
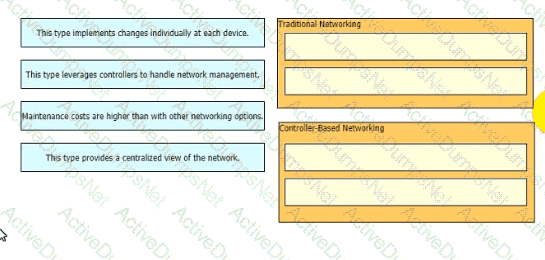
Refer to the exhibit.

All interfaces are in the same VLAN. All switches are configured with the default STP priorities. During the STP electronics, which switch becomes the root bridge?
Refer to the exhibit.
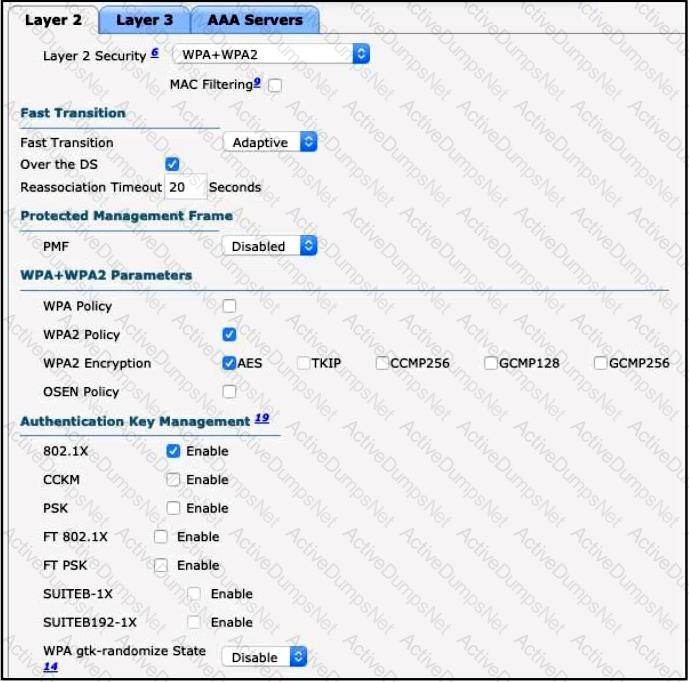
Clients on the WLAN are required to use 802.11r. What action must be taken to meet the requirement?
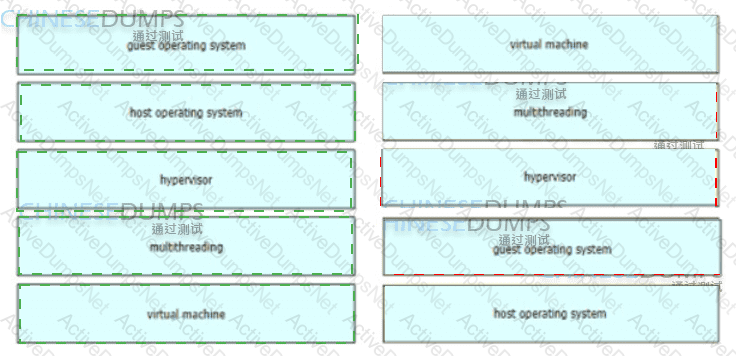
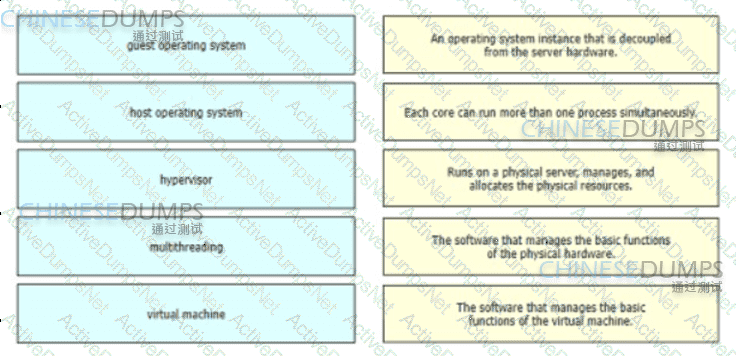
Drag and drop the virtualization concepts from the left onto the matching statements on the right.
Which part of the HTTP request is used in REST API basic authentication to carry credentials?
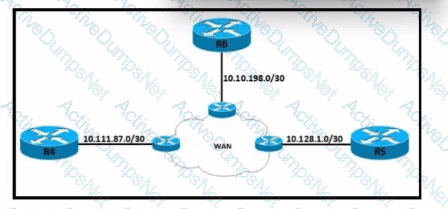
Refer to the exhibit. Local access for R4 must be established and these requirements must be met:
• Only Telnet access is allowed.
• The enable password must be stored securely.
• The enable password must be applied in plain text.
• Full access to R4 must be permitted upon successful login.
Which configuration script meets the requirements?
A)

B)
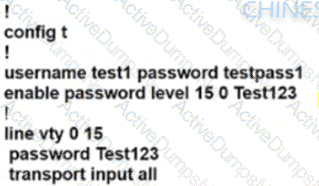
C)
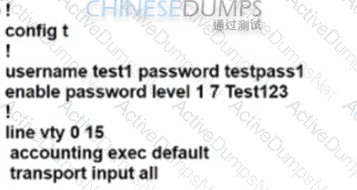
D)
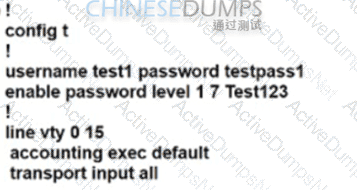
Refer to the exhibit.

A network engineer executes the show ip route command on router D. What is the next hop to network 192.168 1 0/24 and why?
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
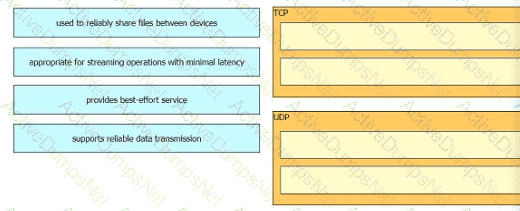
Refer to the exhibit.
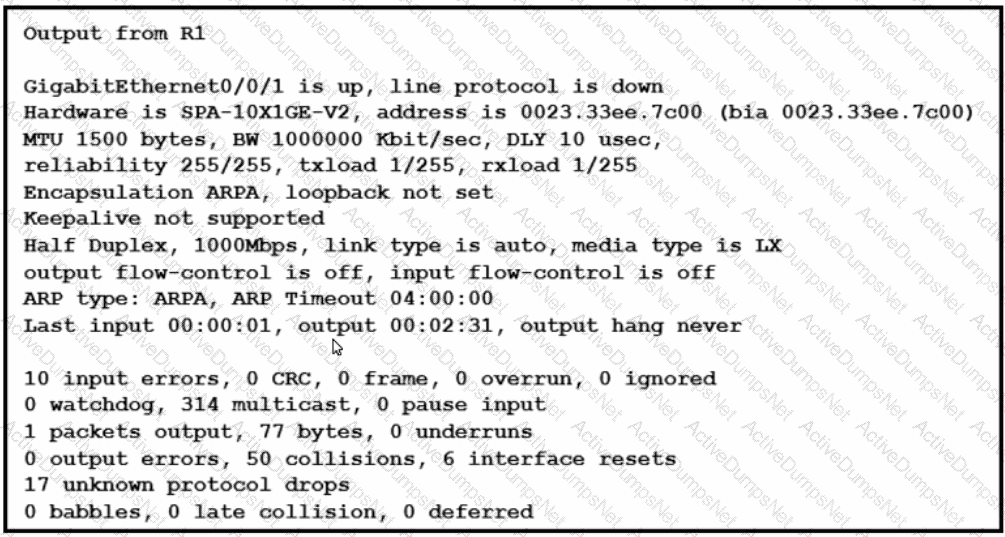
What is the issue with the interface GigabitEthernet0/0/1?
Which interface IP address serves as the tunnel source for CAPWAP packets from the WLC to an AP?
What are two benefits for using private IPv4 addressing? (Choose two.)
What provides connection redundancy increased bandwidth and load sharing between a wireless LAN controller and a Layer 2 switch?
Refer to the exhibit.

Which types of JSON data is shown
Refer to the exhibit.
PC A and the file server. Which commend must be configured on switch A to prevent interruption of other communications?
A network administrator wants the syslog server to filter incoming messages into different files based on their Importance. Which filtering criteria must be used?
Which plane is centralized in software-defined networking (SDN)?
Which remote access protocol provides unsecured remote CLI access?
Which command creates a static NAT binding for a PC address of 10.1.1.1 to the public routable address 209.165.200.225 assigned to the PC?
Refer to the exhibit.
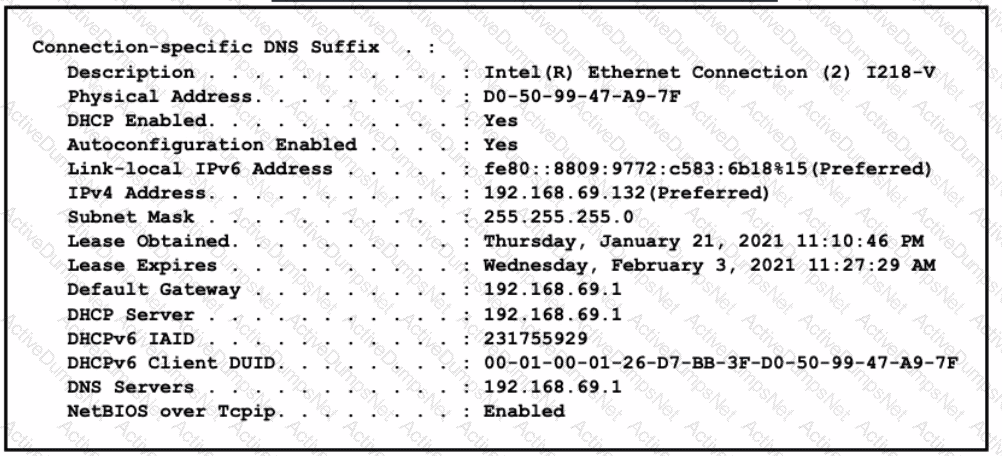
What does the host do when using the IPv4 Preferred function?
What is a benefit of a point-to-point leased line?
Refer to the exhibit.
How does router R1 handle traffic to the 172.16.1.4/30 subnet?
A Cisco engineer notices thai two OSPF neighbors are connected using a crossover Ethernet cable. The neighbors are taking too long to become fully adjacent. Which command must be issued under the interface configuration on each router to reduce the time required for the adjacency to reach the FULL state?

Refer to the exhibit. What is the next-hop IP address for R2 so that PC2 reaches the application server via EIGRP?
Refer to the exhibit.
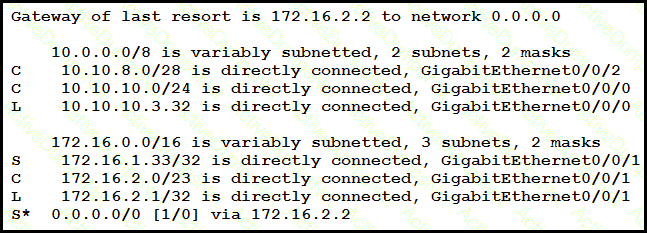
A packet sourced from 10.10.10.1 is destined for 10.10.8.14. What is the subnet mask of the destination route?
What is a function performed by a web server?
What are two reasons lo configure PortFast on a switch port attached to an end host? (Choose two.)
Refer to the exhibit.
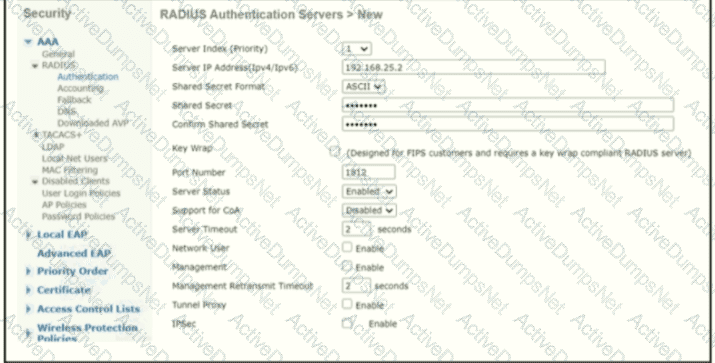
A network engineer configures the Cisco WLC to authenticate local wireless clients against a RADIUS server Which task must be performed to complete the process?
What is the role of nonoverlapping channels in a wireless environment?
Which mechanism carries multicast traffic between remote sites and supports encryption?
What is a benefit of a point-to-point leased line?
When the LAG configuration is updated on a Cisco WLC which additional task must be performed when changes are complete?
What are two benefits for using private IPv4 addressing? (Choose two.)
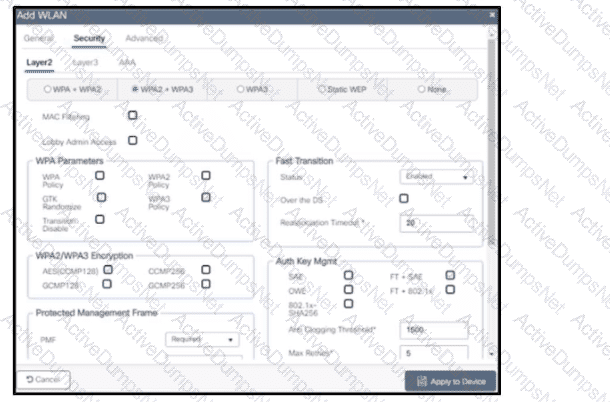
Refer to the exhibit. Which functionalities will this SSID have while being used by wireless clients?
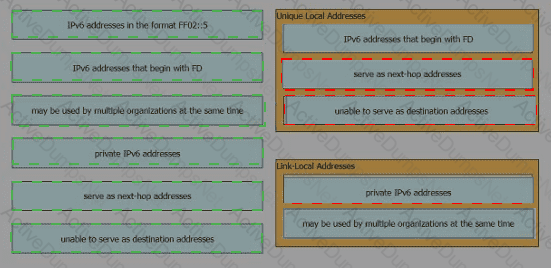
Drag and drop the IPv6 address description from the left onto the IPv6 address types on the right. Not all options are used.

Which command implies the use of SNMPv3?
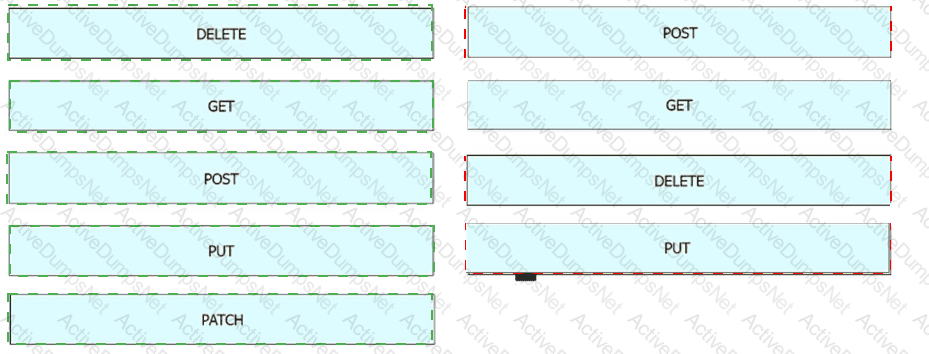
Drag and drop the REST API call method for HTTP from the left onto the action they perform on the right.

A manager asks a network engineer to recommend a cloud service model so that employees do not spend time installing, managing, and updating software that is only used occasionally. Which cloud service model does the engineer recommend?
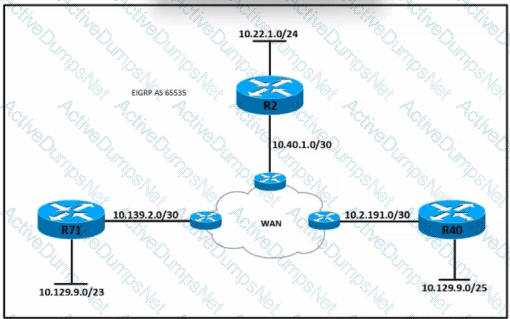
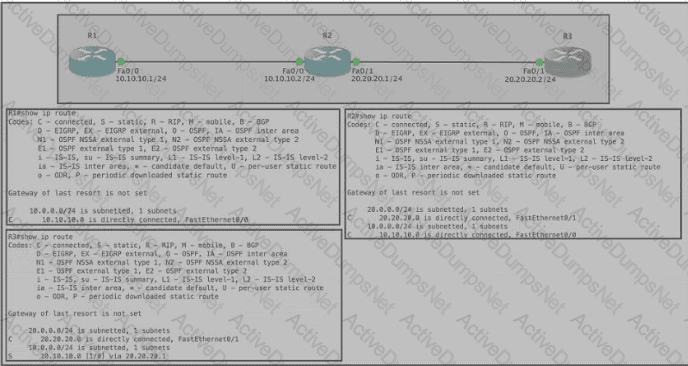
Refer to the exhibit. All routers in the network are configured conrectly, and the expected routes are being exchanged among the routers. Which set of routes are leamed from neighbors and installed on router 2?
How does encryption project the wireless network?
Refer to the exhibit.
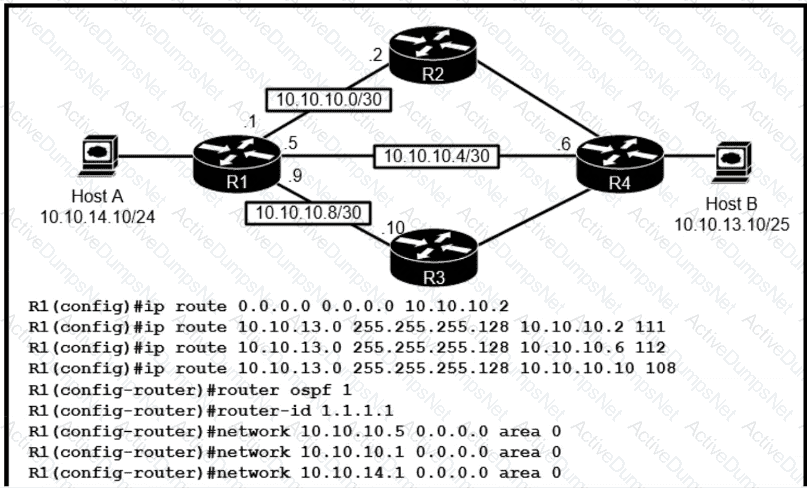
R1 has just received a packet from host A that is destined to host B. Which route in the routing table is used by R1 to reac B?