Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Exam Practice Test
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Questions and Answers
According to CVSS, which condition is required for attack complexity metrics?
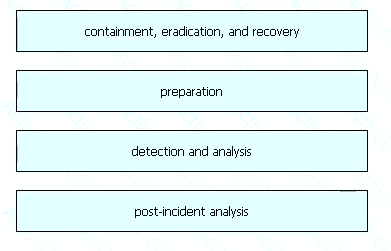
A network engineer informed a security team of a large amount of traffic and suspicious activity from an unknown source to the company DMZ server The security team reviewed the data and identified a potential DDoS attempt According to NIST, at which phase of incident response is the security team?
A CMS plugin creates two files that are accessible from the Internet myplugin html and exploitable php A newly discovered exploit takes advantage of an injection vulnerability m exploitable php To exploit the vulnerability an HTTP POST must be sent with specific variables to exploitable php A security engineer notices traffic to the webserver that consists of only HTTP GET requests to myplugin html Which category does this activity fall under?
Which two attacks are denial-of-service (DoS) attacks? (Choose two.)
Which evasion technique is a function of ransomware?
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
Refer to the exhibit.

Which event is occurring?
What is a difference between SI EM and SOAR security systems?
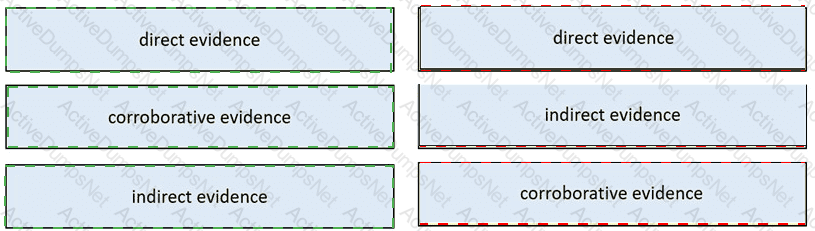
Drag and drop the type of evidence from the left onto the description of that evidence on the right.

How is SQL injection prevented?
Which type of verification consists of using tools to compute the message digest of the original and copied data, then comparing the similarity of the digests?
Which of these is a defense-in-depth strategy principle?
An engineer is analyzing a recent breach where confidential documents were altered and stolen by the receptionist. Further analysis shows that the threat actor connected an externa USB device to bypass security restrictions and steal data. The engineer could not find an external USB device Which piece of information must an engineer use for attribution in an investigation?
What is a benefit of using asymmetric cryptography?
Which data type is necessary to get information about source/destination ports?
What is the advantage of agent-based protection compared to agentless protection?

Refer to the exhibit. What is occurring?
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
What is a collection of compromised machines that attackers use to carry out a DDoS attack?
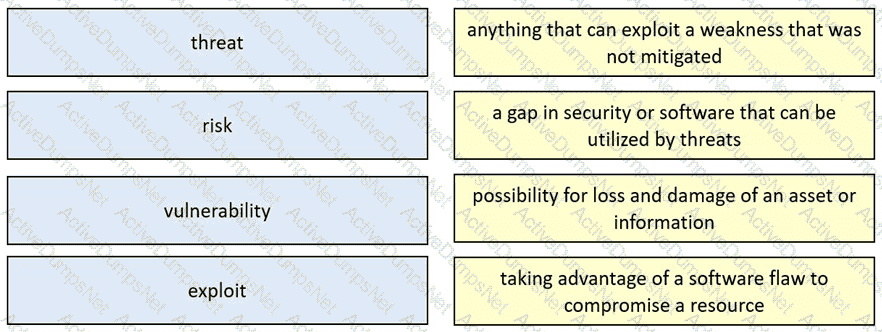
What is a difference between a threat and a vulnerability?
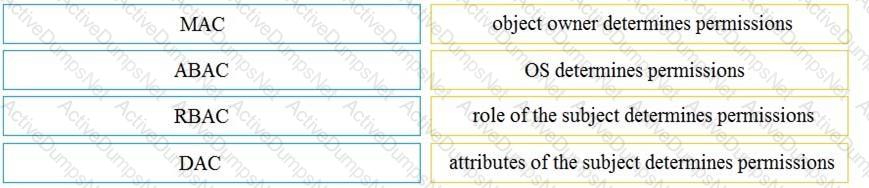
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
Which two elements are used for profiling a network? (Choose two.)
Drag and drop the access control models from the left onto the correct descriptions on the right.
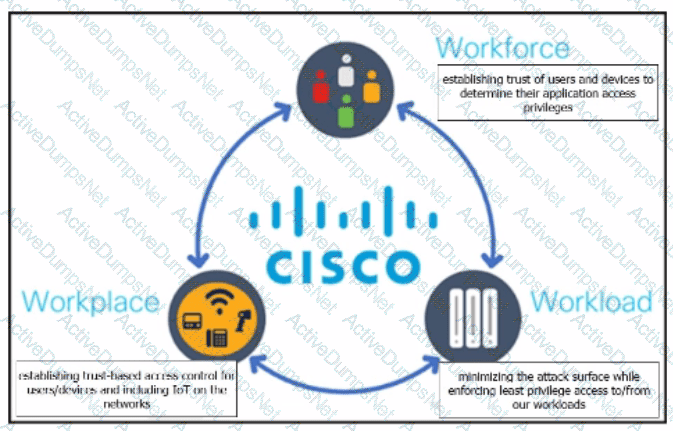
Which security model assumes an attacker within and outside of the network and enforces strict verification before connecting to any system or resource within the organization?
Refer to the exhibit.

Which type of evidence is this file?
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
What are two denial-of-service (DoS) attacks? (Choose two)
According to CVSS, what is a description of the attack vector score?
What describes the difference when comparing attack surface and vulnerability in practice?
How can TOR impact data visibility inside an organization?
What is a difference between tampered and untampered disk images?
What is used to maintain persistent control of an exploited device?
If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
According to CVSS, what is attack complexity?
Which information must an organization use to understand the threats currently targeting the organization?
Refer to the exhibit.
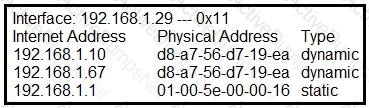
What is occurring in this network?
Refer to the exhibit.

What is the outcome of the command?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load What is the next step the engineer should take to investigate this resource usage7
Which HTTP header field is used in forensics to identify the type of browser used?
What is the difference between deep packet inspection and stateful inspection?
Which action matches the weaponization step of the Cyber Kill Chain model?
Refer to the exhibit.
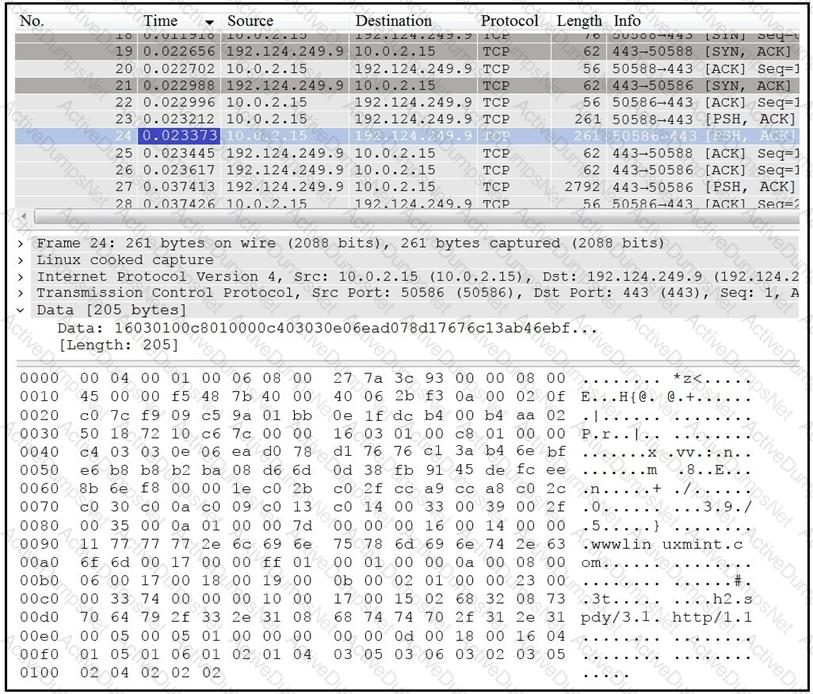
Which application protocol is in this PCAP file?

Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
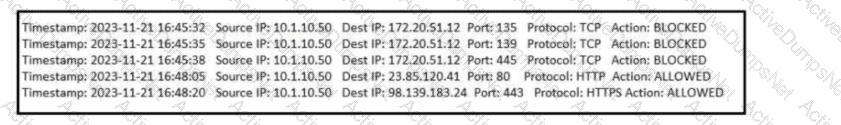
Refer to the exhibit. What type of event is occurring?
What is a difference between tampered and untampered disk images?
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
Refer to the exhibit.
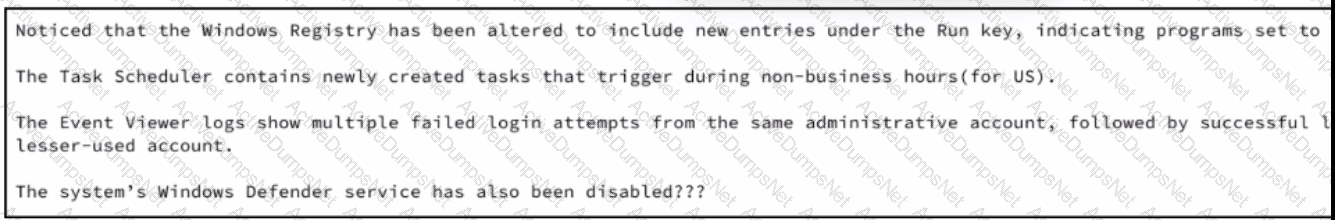
A security analyst wraps up the shift and passed open ticket notes to the night shift SOC team analyst. The ticket name in question is "Investigating suspicious activity on a Windows Server’’. Which operating system components must the analyst prioritize to uncover the attacker's persistence mechanisms?
Which difficulty occurs when log messages are compared from two devices separated by a Layer 3 device that performs Network Address Translation?
What is the difference between inline traffic interrogation and traffic mirroring?
Which risk approach eliminates activities posing a risk exposure?
What describes the concept of data consistently and readily being accessible for legitimate users?
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
Refer to the exhibit.
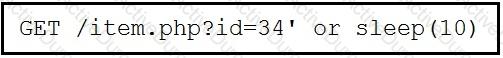
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
What is the difference between antimalware and antivirus solutions?
What should an engineer use to aid the trusted exchange of public keys between user tom0411976943 and dan1968754032?
Which technology prevents end-device to end-device IP traceability?
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Which system monitors local system operation and local network access for violations of a security policy?
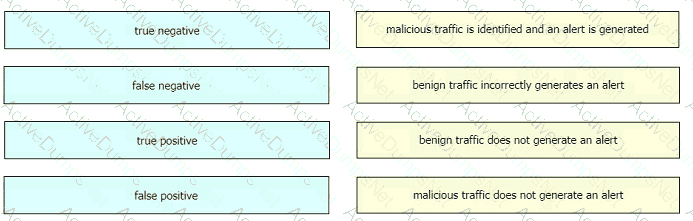
Which statement describes indicators of attack?
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?
An engineer is sharing folders and files with different departments and got this error: "No such file or directory". What must the engineer verify next?
What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
What is the difference between deep packet inspection and stateful inspection?
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
Drag and drop the security concept from the left onto the example of that concept on the right.
An engineer configured regular expression “.”\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall. What does this regular expression do?
What is the difference between authentication and authorization?
A forensic investigator is analyzing a recent breach case. An external USB drive was discovered to be connected and transmitting the data outside of the organization, and the owner of the USB drive could not be identified. Video surveillance shows six people during a two-month period had close contact with the affected asset. How must this type of evidence be categorized?
What is the difference between a threat and a risk?
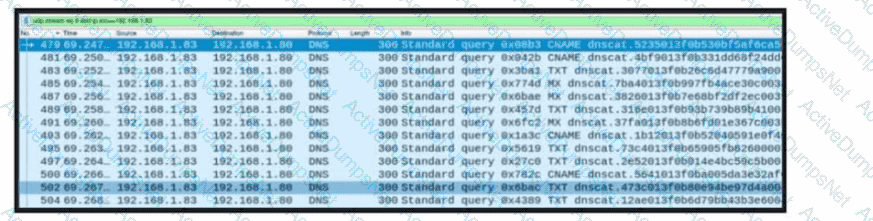
Refer to the exhibit. A network engineer received a report that a host is communicating with unknown domains on the internet. The network engineer collected packet capture but could not determine the technique or the payload used. What technique is the attacker using?
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
What is a scareware attack?
Refer to the exhibit.
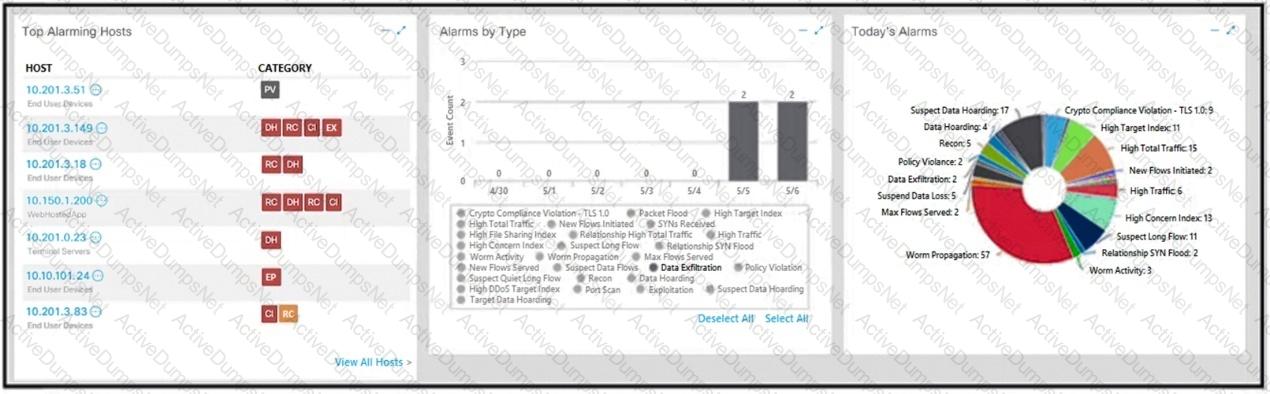
What is the potential threat identified in this Stealthwatch dashboard?
Why should an engineer use a full packet capture to investigate a security breach?
Which action prevents buffer overflow attacks?
Drag and drop the event term from the left onto the description on the right.
What is the purpose of a ransomware attack?
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
If the process is unsuccessful, a negative value is returned.
If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?
A compliance analyst receives a complaint from a customer regarding personal data being unlawfully retained despite a deletion request. The company is based in Europe and must comply with GDPR. The only data collected is the email address 0524l9i75@gmail.com. How should the compliance analyst act?
Which regular expression matches "color" and "colour"?
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
What does this regular expression do?
192|172).(168|1[6-9]|2[0-9]|3[0-1]).[0-9]{1,3}.[0-9]{1,3}\b
Why is HTTPS traffic difficult to screen?
Refer to the exhibit.
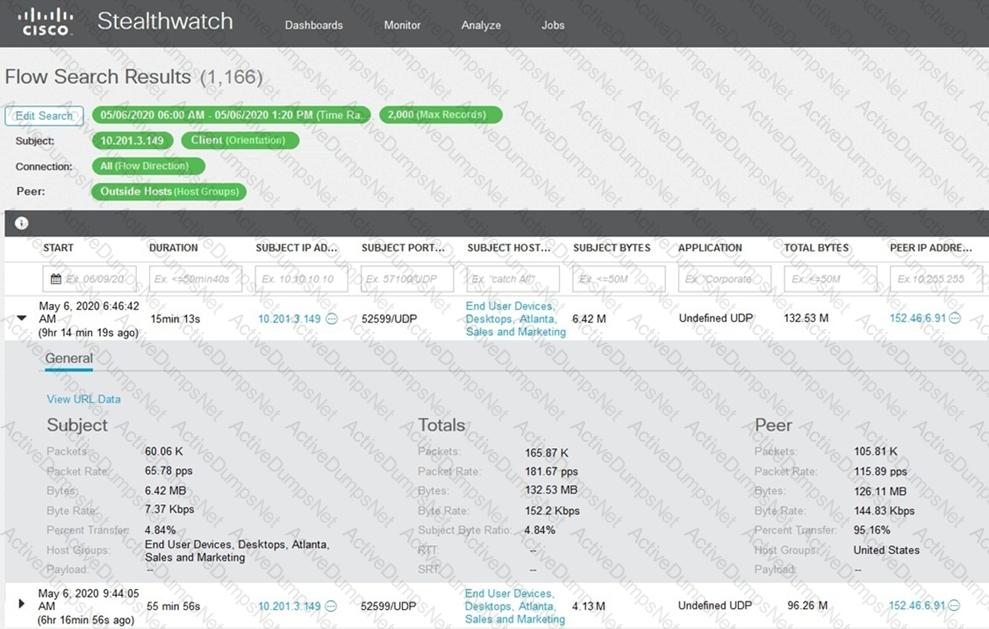
What is the potential threat identified in this Stealthwatch dashboard?
Which category relates to improper use or disclosure of PII data?
What is the difference between deep packet inspection and stateful inspection?
Refer to the exhibit.
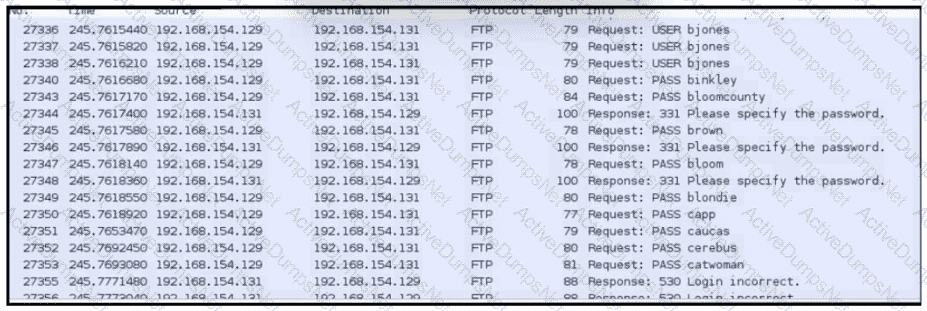
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
Refer to the exhibit.
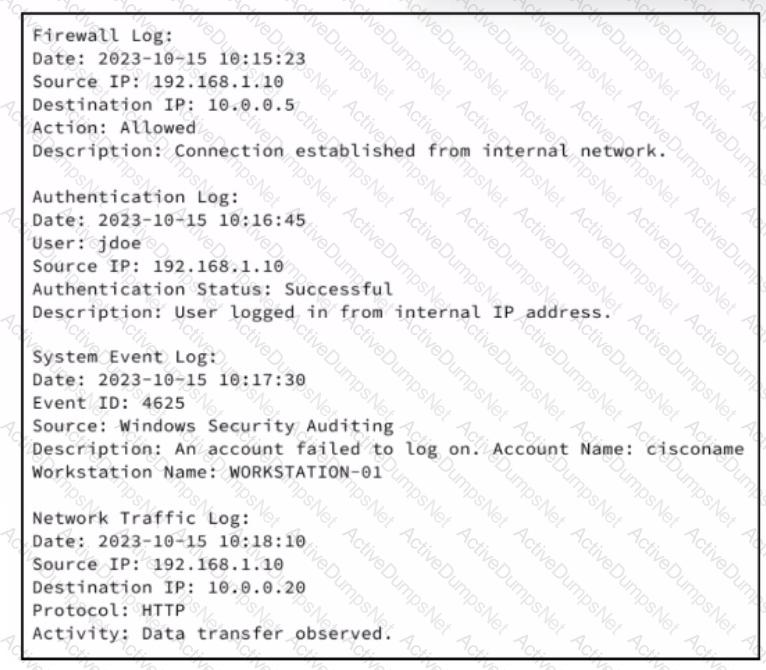
An analyst receives an IDS alert pertaining to a possible data exfiltration attempt. An additional set of logs is collected from different systems and analyzed. Which type of evidence do the logs provide in relation to the primary alert from the IDS?
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
Which management concept best describes developing, operating, maintaining, upgrading, and disposing of all resources?
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
An analyst performs traffic analysis to detect data exfiltration and identifies a high frequency of DNS requests in a small period of time Which technology makes this behavior feasible?
During a quarterly vulnerability scan, a security analyst discovered unused uncommon ports open and in a listening state. Further investigation showed that the unknown application was communicating with an external IP address on an encrypted channel. A deeper analysis revealed a command and control communication on an infected server. At which step of the Cyber Kill Chain was the attack detected?
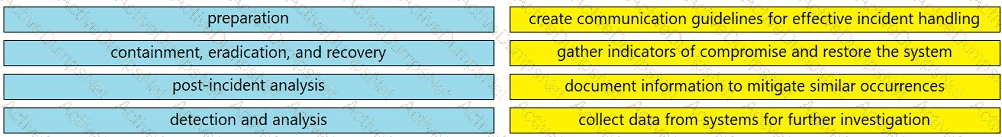
Drag and drop the elements from the left into the correct order for incident handling on the right.
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Which classification of cross-site scripting attack executes the payload without storing it for repeated use?
After a large influx of network traffic to externally facing devices, a security engineer begins investigating what appears to be a denial of service attack When the packet capture data is reviewed, the engineer notices that the traffic is a single SYN packet to each port Which type of attack is occurring?
Which security principle requires more than one person is required to perform a critical task?
What is an example of social engineering attacks?
Which regex matches only on all lowercase letters?
Refer to the exhibit.
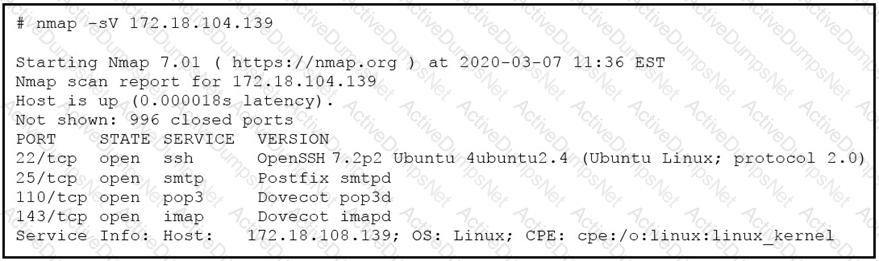
What does the output indicate about the server with the IP address 172.18.104.139?
An employee of a company receives an email with an attachment. They notice that this email is from a suspicious source, and they decide not to open the attached file. After further investigation, a security analyst concludes that this file is malware. To which category of the Cyber Kill Chain model does this event belong?
Refer to the exhibit.
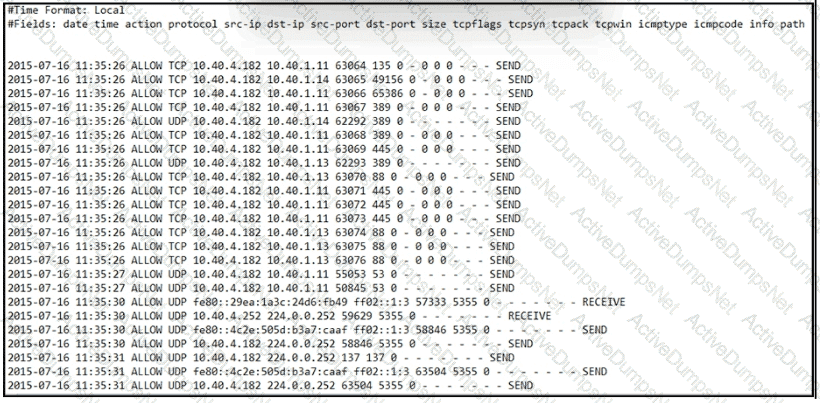
An engineer received an event log file to review. Which technology generated the log?
What is the purpose of command and control for network-aware malware?
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
What is rule-based detection when compared to statistical detection?
An automotive company provides new types of engines and special brakes for rally sports cars. The company has a database of inventions and patents for their engines and technical information Customers can access the database through the company's website after they register and identify themselves. Which type of protected data is accessed by customers?
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
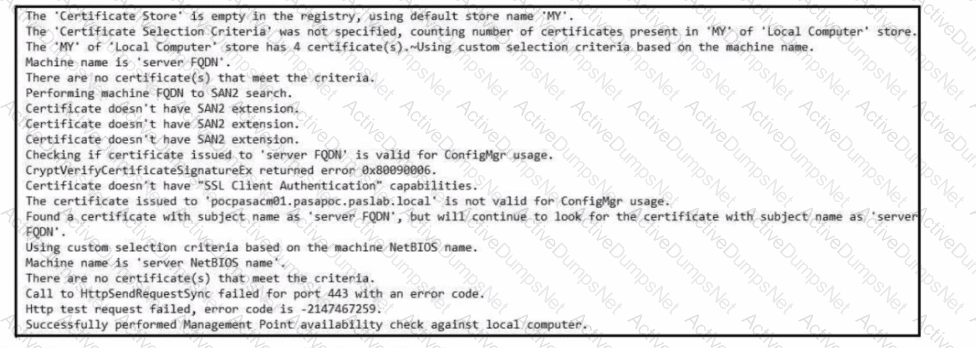
Refer to the exhibit. Which set of actions must an engineer perform to identify and fix this issue?
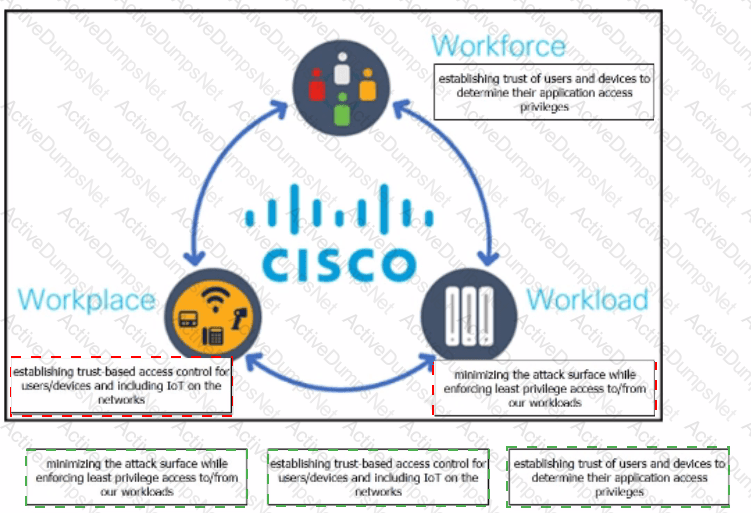
The Cisco Zero Trust Architecture simplifies the zero trust journey into three critical areas. Drag and drop the definitions onto the graphic to describe zero trust from the Cisco perspective.
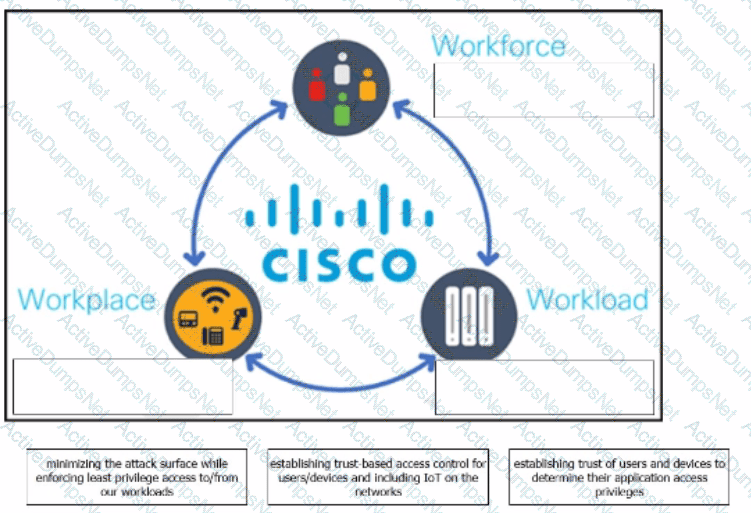
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
What are two social engineering techniques? (Choose two.)
Refer to the exhibit.
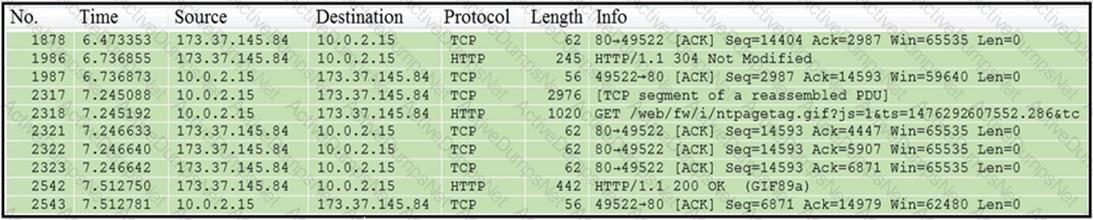
Which packet contains a file that is extractable within Wireshark?
Which utility blocks a host portscan?
What specific type of analysis is assigning values to the scenario to see expected outcomes?
A suspicious user opened a connection from a compromised host inside an organization. Traffic was going through a router and the network administrator was able to identify this flow. The admin was following 5-tuple to collect needed data. Which information was gathered based on this approach?
Refer to the exhibit.
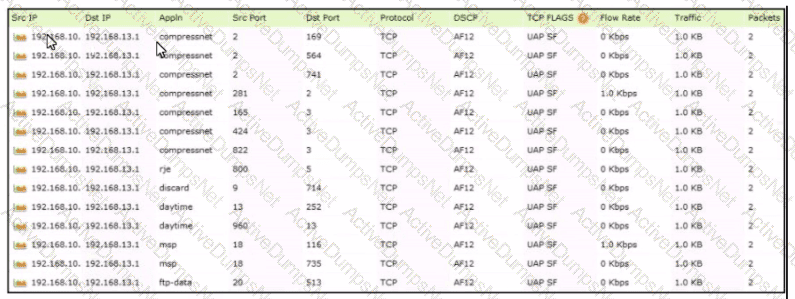
Which tool was used to generate this data?
What is a description of "phishing" as a social engineering attack"?
Which attack method intercepts traffic on a switched network?
Refer to the exhibit.
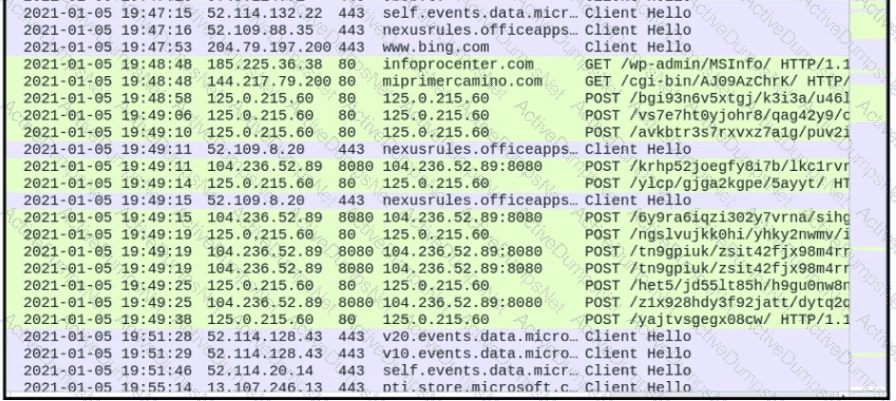
What is occurring?
Which statement describes patch management?
What is a difference between inline traffic interrogation and traffic mirroring?
Which technology on a host is used to isolate a running application from other applications?
An engineer received a ticket to investigate a potentially malicious file detected by a malware scanner that was trying to execute multiple commands. During the initial review, the engineer discovered that the file was created two days prior. Further analyses show that the file was downloaded from a known malicious domain after a successful phishing attempt on an asset owner. At which phase of the Cyber Kill Chain was this attack mitigated?
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
What is a ransomware attack?
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Which items is an end-point application greylist used?
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
How does an attack surface differ from an attack vector?
Refer to the exhibit.
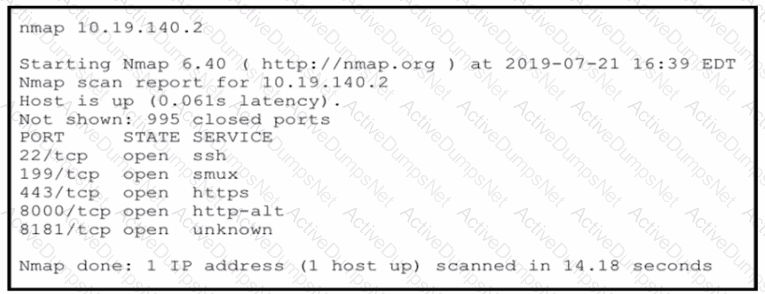
An attacker gained initial access to the company s network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data Which two elements can an attacker identify from the scan? (Choose two.)
What is a difference between SIEM and SOAR?
Which tool gives the ability to see session data in real time?
What is the functionality of an IDS'?

Refer to the exhibit. A SOC team member receives a case from his colleague with notes attached. The artifacts and alerts associated with the case must be analyzed and a conclusion must be provided. What is the cause of the alert?
An analyst received a ticket regarding a degraded processing capability for one of the HR department's servers. On the same day, an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
What is the virtual address space for a Windows process?
Which evasion method involves performing actions slower than normal to prevent detection?

 Graphical user interface, application Description automatically generated
Graphical user interface, application Description automatically generated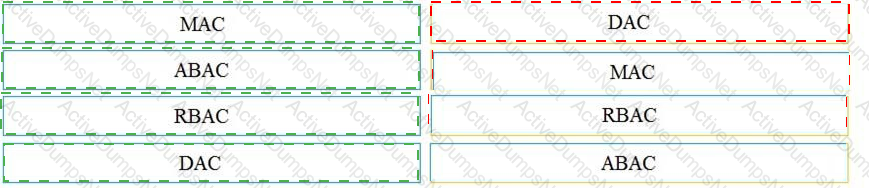
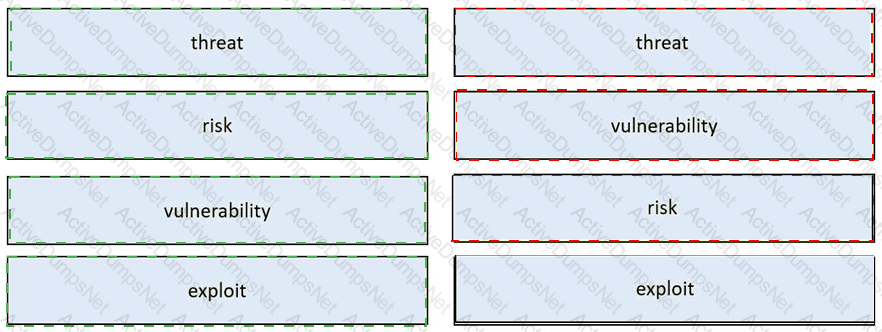
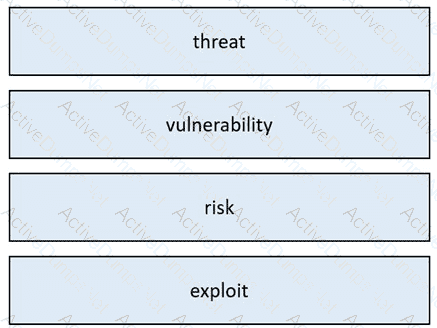 Table Description automatically generated
Table Description automatically generated
 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated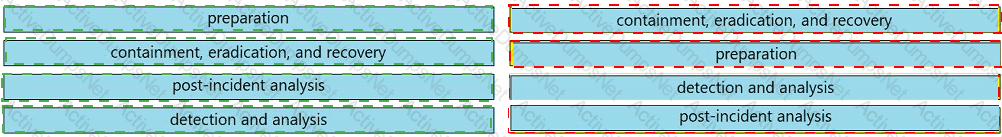
 A close-up of several blue rectangular boxes Description automatically generated
A close-up of several blue rectangular boxes Description automatically generated