Cisco 100-160 Cisco Certified Support Technician (CCST) Cybersecurity Exam Practice Test
Cisco Certified Support Technician (CCST) Cybersecurity Questions and Answers
During an incident response, the security team needs to isolate a compromised server from the rest of the network but still allow forensic analysis. Which action should they take?
An administrator wants to ensure that any files downloaded from the internet are automatically scanned for malicious code before execution. Which security control should be implemented?
You need a software solution that performs the following tasks:
Compiles network data
Logs information from many sources
Provides orchestration in the form of case management
Automates incident response workflows
What product should you use?
A restaurant installs a second wireless router that only employees can use.
Which statement describes how to securely configure the new router?
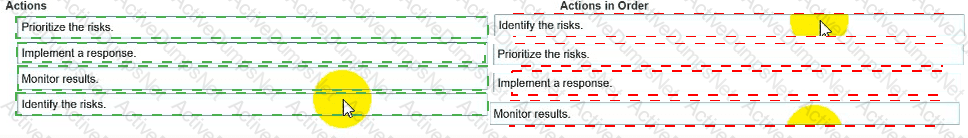
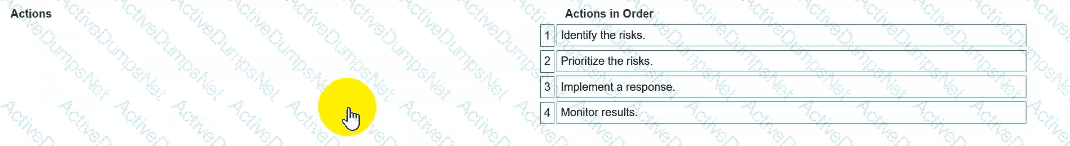
You need to manage security risks at your company. In which order should you complete the actions?
Move all the actions to the answer area and place them in the correct order.

Which wireless security protocol provides the strongest protection for a home or small business network?
How do threat actors launch ransomware attacks on organizations?
Which network security technology passively monitors network traffic and compares the captured packet stream with known malicious signatures?
You are reviewing the Application log on a Windows computer. You see an event with an error-level message as shown.
What can you determine about the application that generated the event message?
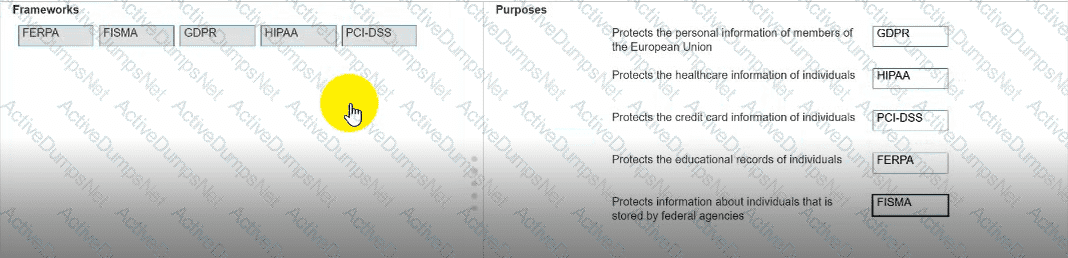
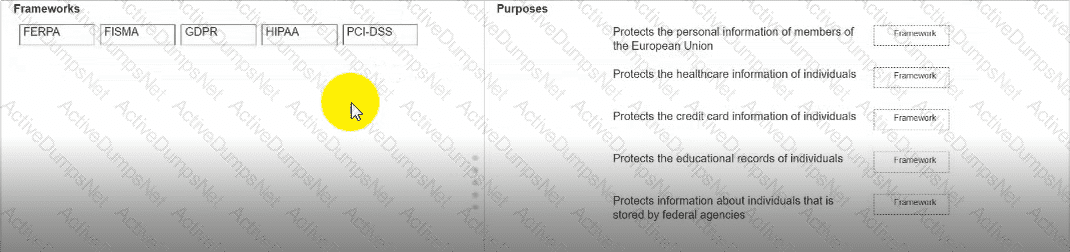
Move each framework from the list on the left to the correct purpose on the right.
Note: You will receive partial credit for each correct answer.
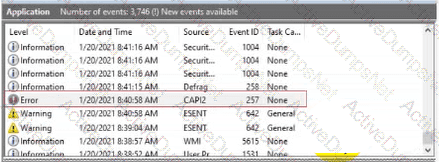
Your supervisor suspects that someone is attempting to gain access to a Windows computer by guessing user account IDs and passwords. The supervisor asks you to use the Windows Event Viewer security logs to verify the attempts.
Which two audit policy events provide information to determine whether someone is using invalid credentials to attempt to log in to the computer?(Choose 2.)
Note: You will receive partial credit for each correct selection.
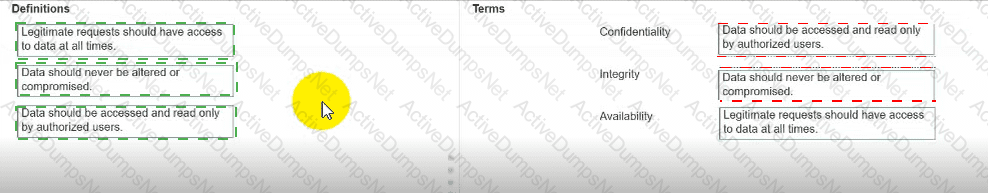
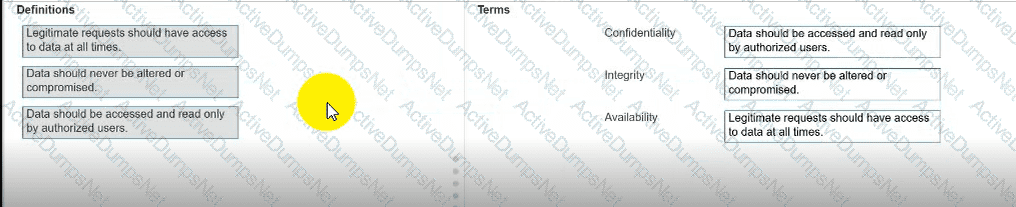
Move each definition from the list on the left to the correct CIA Triad term on the right.
Note: You will receive partial credit for each correct answer.
Why is it necessary to update firmware to the latest version?
Your manager asks you to review the output of some vulnerability scans and report anything that may require escalation.
Which two findings should you report for further investigation as potential security vulnerabilities?(Choose 2.)
Move each NIST Incident Response Lifecycle phase from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.