Checkpoint 156-315.81 Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) Exam Practice Test
Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) Questions and Answers
CoreXL is NOT supported when one of the following features is enabled: (Choose three)
What component of Management is used tor indexing?
SmartEvent uses it's event policy to identify events. How can this be customized?
Can Check Point and Third-party Gateways establish a certificate-based Site-to-Site VPN tunnel?
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ________ .
Firewall polices must be configured to accept VRRP packets on the GAiA platform if it Firewall software. The Multicast destination assigned by the internet Assigned Number Authority (IANA) for VRRP is:
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway.
What is Dynamic Balancing?
SmartConsole R81 x requires the following ports to be open for SmartEvent.
Which of the following is NOT a component of a Distinguished Name?
identity Awareness allows easy configuration for network access, and auditing based on what three items?
How many interfaces can you configure to use the Multi-Queue feature?
Which Check Point process provides logging services, such as forwarding logs from Gateway to Log Server, providing Log Export API (LEA) & Event Logging API (EL-A) services.
Which of the following is NOT a valid type of SecureXL template?
What are the available options for downloading Check Point hotfixes in Gala WebUI (CPUSE)?
In SmartConsole, objects are used to represent physical and virtual network components and also some logical components. These objects are divided into several categories. Which of the following is NOT an objects category?
What is the main objective when using Application Control?
In Threat Prevention, you can create new or clone profiles but you CANNOT change the out-of-the-box profiles of:
Kofi, the administrator of the ALPHA Corp network wishes to change the default Gaia WebUI Portal port number currently set on the default HTTPS port. Which CLISH commands are required to be able to change this TCP port?
What should the admin do in case the Primary Management Server is temporary down?
Which of the following is a task of the CPD process?
In CoreXL, the Firewall kernel is replicated multiple times. Each replicated copy or instance can perform the following:
In the Check Point Security Management Architecture, which component(s) can store logs?
Fill in the blank: The IPS policy for pre-R81 gateways is installed during the _______ .
What are the Threat Prevention software components available on the Check Point Security Gateway?
What are the main stages of a policy installation?
Fill in the blank: Authentication rules are defined for ________ .
You want to gather data and analyze threats to your mobile device. It has to be a lightweight app. Which application would you use?
To enable Dynamic Dispatch on Security Gateway without the Firewall Priority Queues, run the following command in Expert mode and reboot:
Which software blade does NOT accompany the Threat Prevention policy?
The “Hit count” feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits if the Track option is set to “None”?
Which statement is false in respect of the SmartConsole after upgrading the management server to R81.20?
To find records in the logs that shows log records from the Application & URL Filtering Software Blade where traffic was dropped, what would be the query syntax?
Which is the command to identify the NIC driver before considering about the employment of the Multi-Queue feature?
Which process handles connection from SmartConsole R81?
Which of the following blades is NOT subscription-based and therefore does not have to be renewed on a regular basis?
What mechanism can ensure that the Security Gateway can communicate with the Management Server with ease in situations with overwhelmed network resources?
When Configuring Endpoint Compliance Settings for Applications and Gateways within Mobile Access, which of the three approaches will allow you to configure individual policies for each application?
What needs to be configured if the NAT property ‘Translate destination or client side’ is not enabled in Global Properties?
What is a possible command to delete all of the SSH connections of a gateway?
Bob has finished io setup provisioning a secondary security management server. Now he wants to check if the provisioning has been correct. Which of the following Check Point command can be used to check if the security management server has been installed as a primary or a secondary security management server?
After finishing installation admin John likes to use top command in expert mode. John has to set the expert-password and was able to use top command. A week later John has to use the top command again, He detected that the expert password is no longer valid. What is the most probable reason for this behavior?
What is required for a certificate-based VPN tunnel between two gateways with separate management systems?
When defining QoS global properties, which option below is not valid?
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ____ all traffic. However, in the Application Control policy layer, the default action is ______ all traffic.
In which VPN community is a satellite VPN gateway not allowed to create a VPN tunnel with another satellite VPN gateway?
GAIA greatly increases operational efficiency by offering an advanced and intuitive software update agent, commonly referred to as the:
Which view is NOT a valid CPVIEW view?
CPM process stores objects, policies, users, administrators, licenses and management data in a database. The database is:
Which of the following process pulls application monitoring status?
Which command is used to set the CCP protocol to Multicast?
Which Mobile Access Application allows a secure container on Mobile devices to give users access to internal website, file share and emails?
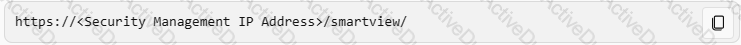
How can SmartView application accessed?
Fill in the blank: The command ___________________ provides the most complete restoration of a R81 configuration.
Which command would disable a Cluster Member permanently?
In R81 spoofing is defined as a method of:
Which method below is NOT one of the ways to communicate using the Management API’s?
Which statement is NOT TRUE about Delta synchronization?
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
Which of the SecureXL templates are enabled by default on Security Gateway?
You have successfully backed up Check Point configurations without the OS information. What command would you use to restore this backup?
Where you can see and search records of action done by R81 SmartConsole administrators?
What are the three components for Check Point Capsule?
What is the difference between an event and a log?
Which is NOT an example of a Check Point API?
Which command collects diagnostic data for analyzing customer setup remotely?
When requiring certificates for mobile devices, make sure the authentication method is set to one of the following, Username and Password, RADIUS or ________.
Advanced Security Checkups can be easily conducted within:
What Factor preclude Secure XL Templating?
SSL Network Extender (SNX) is a thin SSL VPN on-demand client that is installed on the remote user’s machine via the web browser. What are the two modes of SNX?
Which of the following statements is TRUE about R81 management plug-ins?
The fwd process on the Security Gateway sends logs to the fwd process on the Management Server via which 2 processes?
Which statement is correct about the Sticky Decision Function?
Fill in the blank: The R81 utility fw monitor is used to troubleshoot ______________________.
Which command can you use to enable or disable multi-queue per interface?
If you needed the Multicast MAC address of a cluster, what command would you run?
What makes Anti-Bot unique compared to other Threat Prevention mechanisms, such as URL Filtering, Anti-Virus, IPS, and Threat Emulation?
What is true about the IPS-Blade?
There are 4 ways to use the Management API for creating host object with R81 Management API. Which one is NOT correct?
Check Point recommends configuring Disk Space Management parameters to delete old log entries when available disk space is less than or equal to?
What are the attributes that SecureXL will check after the connection is allowed by Security Policy?
In order to get info about assignment (FW, SND) of all CPUs in your SGW, what is the most accurate CLI command?
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
Tom has been tasked to install Check Point R81 in a distributed deployment. Before Tom installs the systems this way, how many machines will he need if he does NOT include a SmartConsole machine in his calculations?
The Security Gateway is installed on GAIA R81. The default port for the Web User Interface is ______ .
The Firewall kernel is replicated multiple times, therefore:
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
On R81.20 when configuring Third-Party devices to read the logs using the LEA (Log Export API) the default Log Server uses port:
Connections to the Check Point R81 Web API use what protocol?
Which features are only supported with R81.20 Gateways but not R77.x?
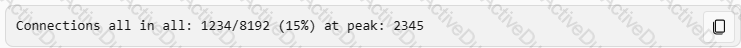
Which command can you use to verify the number of active concurrent connections?
The Firewall Administrator is required to create 100 new host objects with different IP addresses. What API command can he use in the script to achieve the requirement?
In a Client to Server scenario, which inspection point is the first point immediately following the tables and rule base check of a packet coming from outside of the network?
What are the different command sources that allow you to communicate with the API server?
When gathering information about a gateway using CPINFO, what information is included or excluded when using the “-x” parameter?
You find one of your cluster gateways showing “Down” when you run the “cphaprob stat” command. You then run the “clusterXL_admin up” on the down member but unfortunately the member continues to show down. What command do you run to determine the cause?
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enabled which path is handling the traffic?
Which of the following will NOT affect acceleration?
When simulating a problem on ClusterXL cluster with cphaprob –d STOP -s problem -t 0 register, to initiate a failover on an active cluster member, what command allows you remove the problematic state?
SmartEvent does NOT use which of the following procedures to identify events:
What is the main difference between Threat Extraction and Threat Emulation?
Both ClusterXL and VRRP are fully supported by Gaia R81.20 and available to all Check Point appliances. Which the following command is NOT related to redundancy and functions?
What is the purpose of extended master key extension/session hash?
Which of the following is NOT a component of Check Point Capsule?
What is the command to see cluster status in cli expert mode?
Which of the following is NOT a type of Check Point API available in R81.x?
SandBlast has several functional components that work together to ensure that attacks are prevented in real-time. Which the following is NOT part of the SandBlast component?
In SmartEvent, what are the different types of automatic reactions that the administrator can configure?
: 156
VPN Link Selection will perform the following when the primary VPN link goes down?
John detected high load on sync interface. Which is most recommended solution?
An administrator would like to troubleshoot why templating is not working for some traffic. How can he determine at which rule templating is disabled?
What is considered Hybrid Emulation Mode?
What are the blades of Threat Prevention?
Which process is available on any management product and on products that require direct GUI access, such as SmartEvent and provides GUI client communications, database manipulation, policy compilation and Management HA synchronization?
How do you enable virtual mac (VMAC) on-the-fly on a cluster member?
Which of the following describes how Threat Extraction functions?
To enable Dynamic Dispatch on Security Gateway without the Firewall Priority Queues, run the following command in Expert mode and reboot:
You have existing dbedit scripts from R77. Can you use them with R81.20?
Which GUI client is supported in R81?
Which command gives us a perspective of the number of kernel tables?
What is the most recommended way to install patches and hotfixes?
SmartConsole R81 requires the following ports to be open for SmartEvent R81 management:
Automation and Orchestration differ in that:
How would you deploy TE250X Check Point appliance just for email traffic and in-line mode without a Check Point Security Gateway?
Which web services protocol is used to communicate to the Check Point R81 Identity Awareness Web API?
Which of the following links will take you to the SmartView web application?
Which one of the following is true about Capsule Connect?
What is the command to check the status of the SmartEvent Correlation Unit?
What is the difference between SSL VPN and IPSec VPN?
Which of these is an implicit MEP option?
What are the main stages of a policy installations?
What information is NOT collected from a Security Gateway in a Cpinfo?
SmartEvent has several components that function together to track security threats. What is the function of the Correlation Unit as a component of this architecture?
Which one of the following is true about Threat Emulation?
You want to store the GAIA configuration in a file for later reference. What command should you use?
When installing a dedicated R81 SmartEvent server. What is the recommended size of the root partition?
When setting up an externally managed log server, what is one item that will not be configured on the R81 Security Management Server?
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
: 131
Which command is used to display status information for various components?
How do Capsule Connect and Capsule Workspace differ?
What component of R81 Management is used for indexing?
SmartEvent provides a convenient way to run common command line executables that can assist in investigating events. Right-clicking the IP address, source or destination, in an event provides a list of default and customized commands. They appear only on cells that refer to IP addresses because the IP address of the active cell is used as the destination of the command when run. The default commands are:
Which command would you use to set the network interfaces’ affinity in Manual mode?
You need to change the number of firewall Instances used by CoreXL. How can you achieve this goal?
What does it mean if Deyra sees the gateway status? (Choose the BEST answer.)
What is correct statement about Security Gateway and Security Management Server failover in Check Point R81.X in terms of Check Point Redundancy driven solution?
What is true of the API server on R81.20?
Which of the following is NOT a VPN routing option available in a star community?
You notice that your firewall is under a DDoS attack and would like to enable the Penalty Box feature, which command you use?
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ________ .
What is the responsibility of SOLR process on R81.20 management server?
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
What are the methods of SandBlast Threat Emulation deployment?
In the Firewall chain mode FFF refers to:
How many layers make up the TCP/IP model?
What is the recommended number of physical network interfaces in a Mobile Access cluster deployment?
What is the Implicit Clean-up Rule?
The SmartEvent R81 Web application for real-time event monitoring is called:
You have a Gateway is running with 2 cores. You plan to add a second gateway to build a cluster and used a device with 4 cores.
How many cores can be used in a Cluster for Firewall-kernel on the new device?
Check Point APIs allow system engineers and developers to make changes to their organization’s security policy with CLI tools and Web Services for all the following except:
With MTA (Mail Transfer Agent) enabled the gateways manages SMTP traffic and holds external email with potentially malicious attachments. What is required in order to enable MTA (Mail Transfer Agent) functionality in the Security Gateway?
You want to verify if your management server is ready to upgrade to R81.20. What tool could you use in this process?
Which is not a blade option when configuring SmartEvent?
What is not a purpose of the deployment of Check Point API?
What CLI command compiles and installs a Security Policy on the target’s Security Gateways?
Which statement is most correct regarding about “CoreXL Dynamic Dispatcher”?
What is the most ideal Synchronization Status for Security Management Server High Availability deployment?
Which is NOT an example of a Check Point API?
Vanessa is firewall administrator in her company. Her company is using Check Point firewall on a central and several remote locations which are managed centrally by R77.30 Security Management Server. On central location is installed R77.30 Gateway on Open server. Remote locations are using Check Point UTM-1570 series appliances with R75.30 and some of them are using a UTM-1-Edge-X or Edge-W with latest available firmware. She is in process of migrating to R81.
What can cause Vanessa unnecessary problems, if she didn’t check all requirements for migration to R81?
You can access the ThreatCloud Repository from:
What are the types of Software Containers?
Fill in the blank: The R81 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows then as prioritized security events.
The ____ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
Which application should you use to install a contract file?
Pamela is Cyber Security Engineer working for Global Instance Firm with large scale deployment of Check Point Enterprise Appliances using GAiA/R81.20. Company’s Developer Team is having random access issue to newly deployed Application Server in DMZ’s Application Server Farm Tier and blames DMZ Security Gateway as root cause. The ticket has been created and issue is at Pamela’s desk for an investigation. Pamela decides to use Check Point’s Packet Analyzer Tool-fw monitor to iron out the issue during approved Maintenance window.
What do you recommend as the best suggestion for Pamela to make sure she successfully captures entire traffic in context of Firewall and problematic traffic?
What is UserCheck?
Which is NOT a SmartEvent component?
For best practices, what is the recommended time for automatic unlocking of locked admin accounts?
What statement best describes the Proxy ARP feature for Manual NAT in R81.20?
Capsule Connect and Capsule Workspace both offer secured connection for remote users who are using their mobile devices. However, there are differences between the two.
Which of the following statements correctly identify each product's capabilities?
Which SmartConsole tab is used to monitor network and security performance?
How many policy layers do Access Control policy support?
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
What kind of information would you expect to see using the sim affinity command?
Joey wants to upgrade from R75.40 to R81 version of Security management. He will use Advanced Upgrade with Database Migration method to achieve this.
What is one of the requirements for his success?
Which path below is available only when CoreXL is enabled?
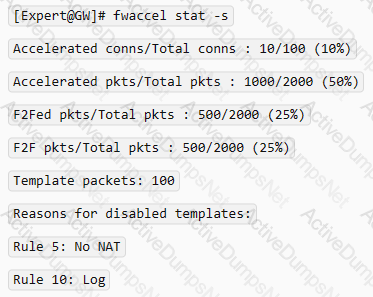
What will be the effect of running the following command on the Security Management Server?
Which file gives you a list of all security servers in use, including port number?


 Firewall
Firewall Firewall
Firewall Firewall
Firewall