Checkpoint 156-215.81 Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) Exam Practice Test
Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) Questions and Answers
Which of the following is a valid deployment option?
Which default Gaia user has full read/write access?
The competition between stateful inspection and proxies was based on performance, protocol support, and security. Considering stateful Inspections and Proxies, which statement is correct?
Which of the following methods can be used to update the trusted log server regarding the policy and configuration changes performed on the Security Management Server?
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
When configuring LDAP with User Directory integration, changes applied to a User Directory template are:
Name the file that is an electronically signed file used by Check Point to translate the features in the license into a code?
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
Fill in the blank: An Endpoint identity agent uses a ___________ for user authentication.
What is the best sync method in the ClusterXL deployment?
Which of the following is NOT an option to calculate the traffic direction?
To enforce the Security Policy correctly, a Security Gateway requires:
Fill in the blanks: Gaia can be configured using the ____ or ____
Under which file is the proxy arp configuration stored?
A network administrator has informed you that they have identified a malicious host on the network, and instructed you to block it. Corporate policy dictates that firewall policy changes cannot be made at this time. What tool can you use to block this traffic?
In which scenario is it a valid option to transfer a license from one hardware device to another?
Fill in the blank Once a license is activated, a___________should be installed.
Most Check Point deployments use Gaia but which product deployment utilizes special Check Point code (with unification in R81.10)?
Fill in the blank RADIUS Accounting gets_____data from requests generated by the accounting client
Which of the following is used to initially create trust between a Gateway and Security Management Server?
Which of the completed statements is NOT true? The WebUI can be used to manage Operating System user accounts and
Choose what BEST describes a Session
Which two of these Check Point Protocols are used by ?
In order to see real-time and historical graph views of Security Gateway statistics in SmartView Monitor, what feature needs to be enabled on the Security Gateway?
Customer’s R80 management server needs to be upgraded to R80.10. What is the best upgrade method when the management server is not connected to the Internet?
What is the default shell of Gaia CLI?
What Identity Agent allows packet tagging and computer authentication?
In which scenario will an administrator need to manually define Proxy ARP?
Which command shows the installed licenses?
Fill in the blanks: A Security Policy is created in_____, stored in the_____ and Distributed to the various
Which Check Point Software Wade provides visibility of users, groups and machines while also providing access control through identity-based policies?
What data MUST be supplied to the SmartConsole System Restore window to restore a backup?
What object type would you use to grant network access to an LDAP user group?
Which of the following log queries would show only dropped packets with source address of 192.168.1.1 and destination address of 172.26.1.1?
What is the BEST method to deploy Identity Awareness for roaming users?
What command from the CLI would be used to view current licensing?
Which of the following is NOT a policy type available for each policy package?
You want to verify if there are unsaved changes in GAiA that will be lost with a reboot. What command can be used?
When configuring LDAP User Directory integration, Changes applied to a User Directory template are:
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
What default layers are included when creating a new policy layer?
When should you generate new licenses?
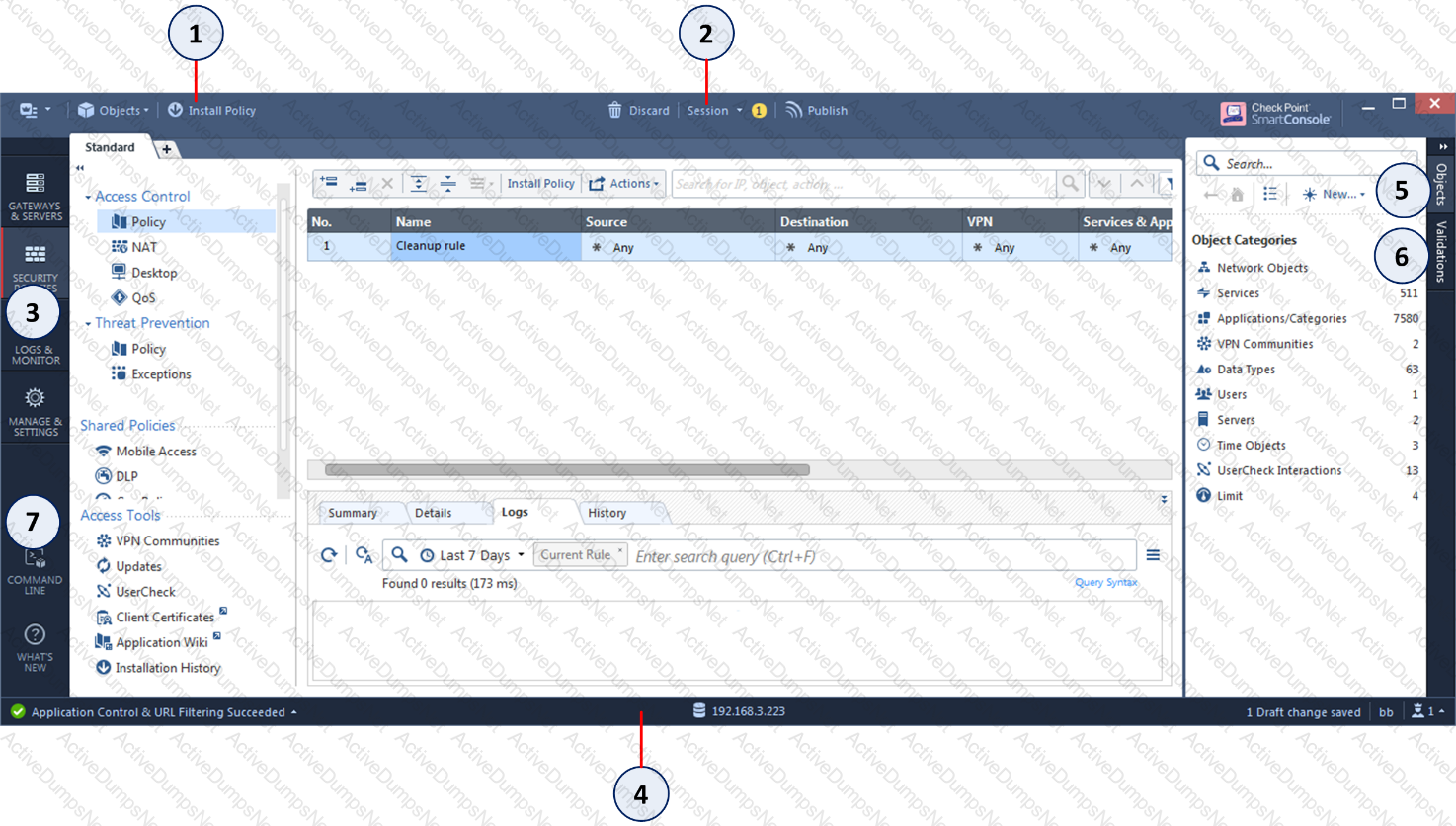
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
Name one limitation of using Security Zones in the network?
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
Which of the following is an authentication method used for Identity Awareness?
When you upload a package or license to the appropriate repository in SmartUpdate. where is the package or license stored?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
Which command shows detailed information about VPN tunnels?
Using R80 Smart Console, what does a “pencil icon” in a rule mean?
You have enabled "Extended Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
What is NOT an advantage of Stateful Inspection?
How are the backups stored in Check Point appliances?
How Capsule Connect and Capsule Workspace differ?
Which SmartConsole application shows correlated logs and aggregated data to provide an overview of potential threats and attack patterns?
When enabling tracking on a rule, what is the default option?
Which key is created during Phase 2 of a site-to-site VPN?
Fill in the blank: Service blades must be attached to a ______________.
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
Fill in the blank: With the User Directory Software Blade, you can create user definitions on a(n) ___________ Server.
What kind of NAT enables Source Port Address Translation by default?
When installing a dedicated R80 SmartEvent server, what is the recommended size of the root partition?
When dealing with rule base layers, what two layer types can be utilized?
What are the Threat Prevention software components available on the Check Point Security Gateway?
Which type of attack can a firewall NOT prevent?
To increase security, the administrator has modified the Core protection ‘Host Port Scan’ from ‘Medium’ to ‘High’ Predefined Sensitivity. Which Policy should the administrator install after Publishing the changes?
The default shell of the Gaia CLI is cli.sh. How do you change from the cli.sh shell to the advanced shell to run Linux commands?
When configuring Anti-Spoofing, which tracking options can an Administrator select?
What is the purpose of the CPCA process?
What is the purpose of Captive Portal?
Which of the following is NOT an identity source used for Identity Awareness?
A security zone is a group of one or more network interfaces from different centrally managed gateways. What is considered part of the zone?
Which configuration element determines which traffic should be encrypted into a VPN tunnel vs. sent in the clear?
Which of the following is NOT supported by Bridge Mode on the Check Point Security Gateway?
What are the two elements of address translation rules?
From SecureXL perspective, what are the tree paths of traffic flow:
When comparing Stateful Inspection and Packet Filtering, what is a benefit that Stateful Inspection offers over Packer Filtering?
What are the steps to configure the HTTPS Inspection Policy?
Which of the following commands is used to monitor cluster members in CLI?
What is the Transport layer of the TCP/IP model responsible for?
: 370
What technologies are used to deny or permit network traffic?
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enable which path is handling the traffic?
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
Fill in the blank: By default, the SIC certificates issued by R80 Management Server are based on the ____________ algorithm.
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
Choose what BEST describes users on Gaia Platform.
In the Check Point Security Management Architecture, which component(s) can store logs?
How is communication between different Check Point components secured in R80? As with all questions, select the best answer.
Access roles allow the firewall administrator to configure network access according to:
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.
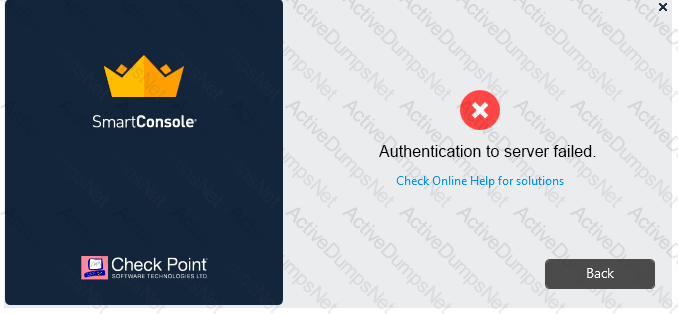
What is the most likely reason?
Fill in the blank: When tunnel test packets no longer invoke a response, SmartView Monitor displays _____________ for the given VPN tunnel.
Which is a main component of the Check Point security management architecture?
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
Which of the following is considered to be the more secure and preferred VPN authentication method?
What is a reason for manual creation of a NAT rule?
Which option, when applied to a rule, allows all encrypted and non-VPN traffic that matches the rule?
Which type of Check Point license ties the package license to the IP address of the Security Management Server?
Which of the following Windows Security Events will NOT map a username to an IP address in Identity Awareness?
Fill in the blank: A(n)_____rule is created by an administrator and configured to allow or block traffic based on specified criteria.
In a Distributed deployment, the Security Gateway and the Security Management software are installed on what platforms?
Which two Identity Awareness daemons are used to support identity sharing?
Which command shows detailed information about VPN tunnels?
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
What licensing feature automatically verifies current licenses and activates new licenses added to the License and Contracts repository?
When URL Filtering is set, what identifying data gets sent to the Check Point Online Web Service?
Which of these is NOT a feature or benefit of Application Control?
What is the RFC number that act as a best practice guide for NAT?
When a Security Gateway sends its logs to an IP address other than its own, which deployment option is installed?
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
Which of the following is NOT a method used by Identity Awareness for acquiring identity?
Why is a Central License the preferred and recommended method of licensing?
After a new Log Server is added to the environment and the SIC trust has been established with the SMS what will the gateways do?
In SmartEvent, a correlation unit (CU) is used to do what?
Core Protections are installed as part of what Policy?
Which of the following is NOT a component of Check Point Capsule?
Which statement describes what Identity Sharing is in Identity Awareness?
What is the difference between SSL VPN and IPSec VPN?
Where can alerts be viewed?
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
Fill in the blank: Authentication rules are defined for ____________.
Which of the following is NOT a valid deployment option for R80?
Fill in the blank: The _____ feature allows administrators to share a policy with other policy packages.
What is the most recommended installation method for Check Point appliances?