Amazon Web Services SOA-C01 AWS Certified SysOps Administrator - Associate Exam Practice Test
AWS Certified SysOps Administrator - Associate Questions and Answers
A company is releasing a now static website hosted on Amazon S3. The static website hosting feature was enabled on the bucket and content was uploaded, however, upon navigating to the site, the following error message is received:
403 Forbiddan - Access Denied
What change should be made to fix this error'?
A SysOps Administrator created an AWS CloudFormation template for the first time. The stack failed with a status of ROLLBACK_COMPLETE. The Administrator identified and resolved the template issue causing the failure.
How should the Administrator continue with the stack deployment?
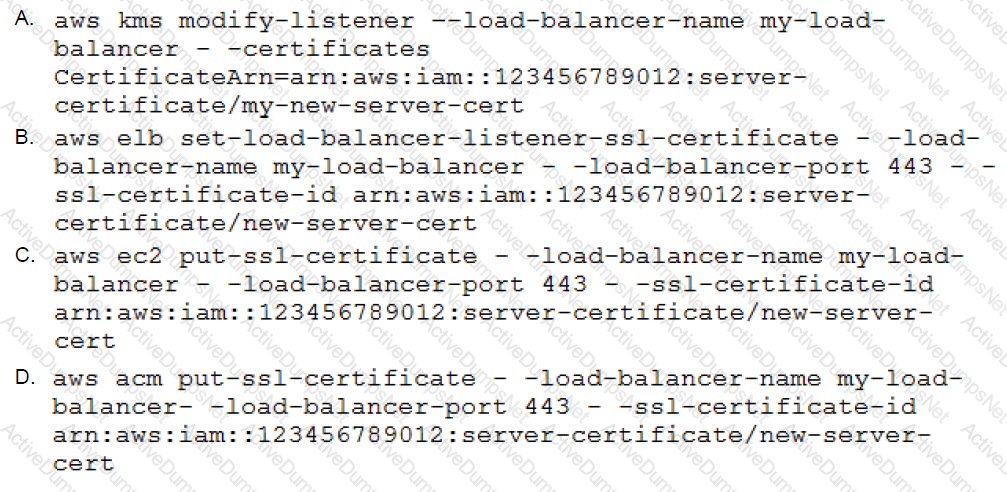
A SysOps Administrator has been able to consolidate multiple, secure websites onto a single server, and each site is running on a different port. The Administrator now wants to start a duplicate server in a second Availability Zone and put both behind a load balancer for high availability.
What would be the command line necessary to deploy one of the sites’ certificates to the load balancer?
A company's IT department noticed an increase in the spend of their Developer AWS account. There are over 50 Developers using the account and the Finance Tram wants to determine the service costs incurred by each Developer.
What should a SysOps Administrator do to collect this information? (Select TWO)
A user accidentally deleted a file from an Amazon EBS volume. The SysOps Administrator identified a recent snapshot for the volume.
What should the Administrator do to restore the user's file from the snapshot?
A company’s Information Security team has requested information on AWS environment compliance for Payment Card Industry (PCI) workloads. They have requested assistance in understanding what specific areas of the PCI standards are the responsibility of the company.
Which AWS tool will provide the necessary information?
A SysOps Administrator is maintaining a web application using an Amazon Cloud Front web distribution, an Application Load Balancer (ALB), Amazon RDS, and Amazon EC2 in a VPC. All services have services have logging enabled. The Administrator needs to investigate HTTP Layer 7 status codes from the web application.
Which log source contain the status codes? (Select TWO.)
A sysops administrator is reviewing AWS Trusted Advisor warnings and encounters a warning for an S3 bucket policy that has open access permissions. While discussing the issue with the bucket owner, the administrator realizes the S3 bucket is an origin for an Amazon CloudFront web distribution.
A SysOps Administrator is responsible for maintaining an Amazo EC2 instance that acts as a bastion host. The Administrator can sucessfully connect to the instance using SSH, but attempts to ping the instance result in a timeout.
What is one reason for the issue?
A SysOps Administrator is troubleshooting an AWS CloudFormation template whereby multiple Amazon EC2 instances are being created. The template is working in us-east-1, but it is failing in us-west-2 with the error code:
AMI [ami-12345678] does not exist.
How should the Administrator ensure that the AWS CloudFormation template is working in every region?
A company is running an application on Amazon EC2 instances. The company needs to stop all development instances during non-business hours to reduce costs. The instances must be started again at trie beginning of each business day.
Which solution meets these requirements with the LEAST administrative overhead?
A company developed and now runs a memory-intensive application on multiple Amazon EC2 Linux instances. The memory utilization metrics of the EC2 Linux instances must be monitored every minute.
How should the SysOps Administrator publish the memory metrics? (Choose two.)
A company monitors its account activity using AWS CloudTrail, and is concerned that some log files are being tampered with after the logs have been delivered to the account’s Amazon S3 bucket.
Moving forward, how can the SysOps Administrator confirm that the log files have not been modified after being delivered to the S3 bucket.
An application running on Amazon EC2 instances in an Auto Scaling group across multiple Availability Zones was deployed using an AWS CloudFormation template. A sysops administrator has patched the Amazon Machine Image (AMI) version and must update all the EC2 instances to use the new AMI.
How should Ihe administrator use CloudFormation to apply the new AMI while maintaining a minimum level of active instances to ensure service continuity?
A company has a web application that runs both on-premises and on Amazon EC2 instances. Over time both the on-premises servers and EC2 instances begin crashing A sysops administrator suspects a memory leak in the application and wants a unified method to monitor memory utilization over time.
How can the Administrator track both the EC2 memory utilization and on-premises server memory utilization over time?
A company has a business application hosted on Amazon EC2 instances behind an Application Load
Balancer. Amazon CloudWatch metrics show that the CPU utilization on the EC2 instances is very high. There are also reports from users that receive HTTP 503 and 504 errors when they try to connect to the application.
Which action will resolve these issues?
A company has several accounts between different teams and wants to increase its auditing and compliance capabilities The accounts are managed through AWS Organizations. Management wants to provide the security team with secure access to the account logs while also restricting the possibility for the logs to be modified.
How can a sysops administrator achieve this is with the LEAST amount of operational overhead?
A company has deployed its infrastructure using AWS CloudFormation Recently the company made manual changes to the infrastructure. A SysOps Administrator is tasked with determining what was changed and updating the CloudFormation template
Which solution will ensure all the changes are captured?
An organization has developed a new memory-intensive application that is deployed to a large Amazon EC2 Linux fleet. There is concern about potential memory exhaustion, so the Development team wants to monitor memory usage by using Amazon CloudWatch.
What is the MOST efficient way to accomplish this goal?
A sysops administrator runs a web application that is using a microservices approach whereby different responsibilities of the application have been divided in a separate microservice running on a different Amazon EC2 instance The administrator has been tasked with reconfiguring the infrastructure to support this approach
How can the administrator accomplish this with the LEAST administrative overhead?
A popular auctioning platform requires near-real-time access to dynamic bidding information. The platform must be available at all times The current Amazon RDS instance often reaches 100% CPU utilization during the weekend auction and can no longer be resized. To improve application performance, a sysops administrator is evaluating Amazon ElastiCache and has chosen Redis (cluster mode enabled) instead of Memcached
What are reasons for making this choice? (Select TWO.)
A SysOps Administrator is using AWS KMS with AWS-generated key material to encrypt an Amazon EBS volume in a company’s AWS environment. The Administrator wants to rotate the KMS keys using automatic key rotation, and needs to ensure that the EBS volume encrypted with the current key remains readable.
What should be done to accomplish this?
A company has several business units that want to use Amazon EC2. The company wants to require all business units to provision their EC2 instances by using only approved EC2 instance configurations
What should a SysOps administrator do to implement this requirement?
A company's application infrastructure was deployed using AWS CloudFormation and is composed of Amazon EC2 instances behind an Application Load Balancer. The instances run an EC2 Auto Scaling group across multiple Availability Zones. When releasing a new version of the application, the update deployment must avoid DNS changes and allow rollback.
Which solution should a sysops administrator use to meet the deployment requirements for this new release?
An HTTP web application is launched on Amazon EC2 instances behind an ELB Application Load Balancer. The EC2 instances run across multiple Availability Zones. A network ACL and a security group for the load balancer and EC2 instances allow inbound traffic on port 80. After launch, the website cannot be reached over the internet.
What additional step should be taken?
A SysOps Administrator created an Application Load balancer (ALB) and placed two Amazon EC2 instances in the same subnet behind the ALB. During monitoring, the Administrator observes HealthyHostCount drop to 1 in Amazon CloudWatch.
What is MOST likely causing this issue?
A company needs to ensure that all IAM users rotate their password on a regular basis.
Which action should be taken to implement this?
A chief financial officer has asked for a breakdown of costs per project in a single AWS account using cost explorer.
Which combination of options should be set to accomplish this? (Select two)
An application is being migrated to AWS with the requirement that archived data be retained for at least 7 years.
What Amazon Glacier configuration option should be used to meet this compliance requirements?
A company received its latest bill with a large increase in the number of requests against Amazon SQS as compared to the month prior. The company is not aware of any major changes in its SQA usage. The company is concerned about the cost increase and who or what was making these calls.
What should a sysops administrator use to validate the calls mode to SQS?
An enterprise is using federated Security Assertion Markup Language (SAML) to access the AWS Management Console.
How should the SAML assertion mapping be configured?
An application is running on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances are configured in an Amazon EC2 Auto Scaling group. A SysOps Administrator must configure the application to scale based on the number of incoming requests.
Which solution accomplishes this with the LEAST amount of effort?
A company's application running on Amazon EC2 Linux recently crashed because it ran out ot available memory. Management wants to be alerted if this ever happens again. Which combination of steps will accomplish this? (Select TWO.)
A company has attached the following policy to an IAM user.
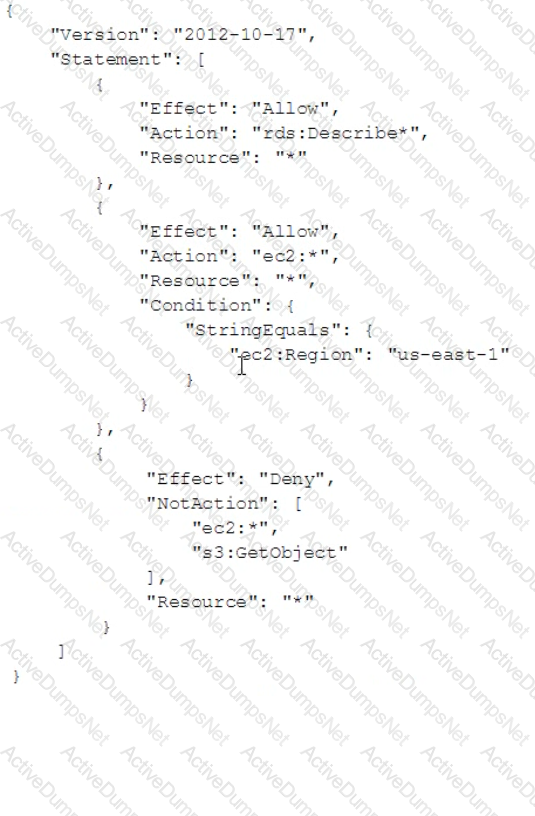
What of the following actions are allowed for the IAM user?
A company is operating a multi-account environment under a single organization using AWS Organizations. The Security team discovers that some employees are using AWS services in ways that violate company policies. A SysOps Administrator needs to prevent all users of an account, including the root user, from performing certain restricted actions.
What should be done to accomplish this?
An Applications team has successfully deployed an AWS CloudFormation stack consisting of 30 t2-medium Amazon EC2 instances in the us-west-2 Region. When using the same template to launch a stack in us-east-2, the launch failed and rolled back after launching only 10 EC2 instances.
What is a possible cause of this failure?
A SysOps Administrator needs to monitor all the object upload and download activity of a single Amazon S3 bucket. Monitoring most include tracking the AWS account of the catier, the IAM user role of the caller, the time of the API call, and the IP address of the API.
Where can the administrator find this information?
A SysOps Administrator has configured a CloudWatch agent to send custom metrics to Amazon CloudWatch and is now assembling a CloudWatch dashboard to display these metrics.
What steps should be the Administrator take to complete this task?
A fleet of servers must send local logs to Amazon CloudWatch.
How should the servers be configured to meet this requirement?
