APICS CPIM-8.0 Certified in Planning and Inventory Management (CPIM 8.0) Exam Practice Test
Certified in Planning and Inventory Management (CPIM 8.0) Questions and Answers
Which of the below represents the GREATEST cloud-specific policy and organizational risk?
In a make-to-order (MTO) production environment, fluctuations in sales volumes are managed by adjustments to the:
Corporate fraud has historically been difficult to detect. Which of the following methods has been the MOST helpful in unmasking embezzlement?
A company’s Marketing and Sales departments have identified an opportunity to develop a new market for a product family and requested an increase in the production plan. Which of the following actions would be most appropriate to account for the new market opportunity?
What should an organization do to prepare for Disaster Recovery (DR) efforts?
An organization received a notification from a Commercial Off-The-Shelf (COTS) provider that one of its products will no longer be supported. Using obsolescence progression stages, which of the following risk trigger points was activated in this case?
An organization is designing a new Disaster Recovery (DR) site. What is the BEST option to harden security of the site?
Which of the following BEST characterizes the operational benefit of using immutable workloads when working on a cloud-based project?
What function prevents unauthorized devices from gaining access to a network?
A hot Disaster Recovery (DR) data center is the victim of a data breach. The hackers are able to access and copy 10GB of clear text confidential information. Which of the following could have decreased the amount of exposure from this data breach?
When the discrete available-to-promise (ATP) method is used, the master production receipt quantity is committed to:
A security engineer needs to perform threat modeling on a microprocessor design for an Internet of Things (IoT) application. Using the MITRE Common Weakness Enumeration (CWE) catalog for hardware, a risk analysis is performed. What kind of threat modeling approach would be BEST to identify entry points into the system based on motivation?
A statistical safety stock calculation would be appropriate for:
What is the MAIN privacy risk raised by federated identity solutions?
Which of the following design considerations would offer the BEST protection against unauthorized access to the facility?
A vendor has been awarded a contract to supply key business software. The vendor has declined all requests to have its security controls audited by customers. The organization insists the product must go live within 30 days. However, the security team is reluctant to allow the project to go live.
What is the organization's BEST next step?
A company implementing a localized multi-country strategy to increase market share should engage in which of the following actions?
After a recent threat modeling workshop, the organization has requested that the Chief Information Security Officer (CISO) implement zero trust (ZT) policies. What was the MOST likely threat identified in the workshop?
A large retail organization will be creating new Application Programming Interfaces (API) as part of a customer-facing shopping solution. The solution will accept information from users both inside and outside of the organization. What is the safest software development practice the team can follow to protect the APIs against Structured Query Language Injection (SQLi) attacks?
The question below is based on the following alternative schedules for a lot of 1,200.
A company works 8-hour, single-shift days. Setups are 4 hours for Operation 20 and 4 hours for Operation 40. Each operation has multiple machines available.
Which of the following statements is correct?
Which of the following tools shows process changes and random variation over time?
During an onsite audit, an assessor inspected an organization’s asset decommission practice. Which of the following would MOST likely be a finding from a security point of view?
A financial services organization wants to deploy a wireless network. Which of the following is the WEAKEST option for ensuring a secure network?
Which of the following actions best supports a company's strategic focus on delivery speed to improve competitive advantage?
An organization wants to establish an information security program and has assigned a security analyst to put it in place. What is the NEXT step?
Which of the following concepts MOST accurately refers to an organization's ability to fully understand the health of the data in its system at every stage of the lifecycle?
Which security concept states that a subject (user, application, or asset) be given only the access needed to complete a task?
The primary benefit that results from the cross-training of employees is:
An organization has decided to give decommissioned computers to a school in a developing country. The company data handling policy prohibits the storage of confidential and sensitive data. What would be the BEST technique to use to avoid data remanence, and to minimize the operational burden for the inheriting school?
What can help a security professional assess and mitigate vulnerabilities of an embedded device?
Company A has acquired Company B. Company A has decided to start a project to convert Company B's enterprise resource planning (ERP) software to the same ERP software that Company A uses. What is a likely reason for this decision?
Which of the following mechanisms are PRIMARILY designed to thwart side channel attacks?
A cybersecurity analyst is responsible for identifying potential security threats and vulnerabilities in the organization's software systems. Which action BEST demonstrates the understanding and application of threat modeling concepts and methodologies?
The demand for an item has increasing forecast error, whereas all other factors remain constant. Which of the following remains constant while maintaining the same customer service level?
An organization's security policy requires remote hosts to be authenticated before they can access network resources. Which of the following is the BEST option for the organization to enforce its policy?
Which of the following methods is most often used to manage inventory planning variability across the supply chain?
Which of the following should be done FIRST when implementing an Identity And Management (IAM) solution?
An organization undergoing acquisition merged IT departments and infrastructure. During server decommissioning, some servers still in use by customers were mistakenly removed, causing order processing failures. Which type of review would have BEST avoided this scenario?
A logistics manager Is faced with delivering an order via rail or truck. Shipping via rail costs S300 and takes 14 days. Shipping via truck costs $600 and takes 3 days. If the holding cost is $40 per day, what is the cost to deliver the order?
An attacker was able to identify an organization’s wireless network, collect proprietary network resource information, and capture several user credentials. The attacker then used that information to conduct a more sophisticated and impactful attack against the organization. Which method did the attacker MOST likely use to gather the initial information?
An organizations is developing a new software package for a financial institution. What is the FIRST step when modeling threats to this new software package?
An organization has decided to leverage open source software for its latest application development project. Which of the following would be the MOST effective way to ensure the open source software can be used securely while still meeting business requirements?
Which of the following measurements indicates there may be bias In the forecast model?
An example of a flexibility metric for an organization Is:
Which of the following actions provides the BEST evidence for forensic analysis of powered-off device?
An organization wants to control access at a high-traffic entrance using magnetic-stripe cards for identification. Which of the following is the BEST for the organization to utilize?
In pyramid forecasting, the "roll up" process begins with:
Which of the following should be performed FIRST in the course of a digital forensics investigation?
Which specification enables organizations to ensure penetration test results are documented using open, machine-readable standards?
A security consultant is working with an organization to help evaluate a proposal received from a new managed security service provider. There are questions about the confidentiality and effectiveness of the provider's system over a period of time. Which of the following System And Organization Controls (SOC) report types should the consultant request from the provider?
When assessing a new vendor as a possible business partner, what would BEST demonstrate that the vendor has a proactive approach to data security compliance?
An organization is considering options to outsource their Information Technology (IT) operations. Although they do not sell anything on the Internet, they have a strong requirement in uptime of their application. After evaluating the offerings received by the Cloud Service Provider (CSP), the IT manager decided it was mandatory to develop processes to continue operations without access to community or public cloud-based applications. Which of the following arguments MOST likely led the IT manager to make this decision?
A security team is analyzing the management of data within the human resources systems, as well as, the intended use of the data, and with whom and how the data will be shared. Which type of assessment is the team MOST likely performing?
Which of the following are compromised in an untrusted network using public key cryptography when a digitally signed message is modified without being detected?
Zombieload, Meltdown, Spectre, and Fallout are all names of bugs that utilized which of the following types of attack?
In order to meet retention requirements, it may be necessary to migrate digital records to different media because of which of the following issues?
Which of the following provides that redundancy and failover capabilities are built into a system to maximize its uptime?
Which of the following presents the GREATEST benefit to an organization's security posture when a change management process is implemented?
A security professional is accessing an organization-issued laptop using biometrics to remotely log into a network resource. Which type of authentication method is described in this scenario?
Which of the following trade-offs should be evaluated when determining where to place inventory in a multi-echelon supply chain network?
An organization is preparing to deploy Multi-Factor Authentication (MFA) to its workforce. The primary concerns of the organization are cost and security. The organization realizes that their entire workforce has computers and smartphones. Which of the following is BEST suited to address the organization's concerns?
What is the FIRST element that must be evaluated in a security governance program?
A manufacturer begins production of an item when a customer order is placed. This is an example of a(n):
Which of the following is the MAIN element in achieving a successful security strategy?
Which of the following actions hinders the transition from a push system to a pull system?
An organization has been struggling to improve their security posture after a recent breach.
Where should the organization focus their efforts?
A large organization wants to implement a vulnerability management system in its internal network. A security professional has been hired to set up a vulnerability scanner on premises and to execute the scans periodically. Which of the following should be the FIRST action performed by the security professional?
Which of the following is the BEST option for a security director to use in order to mitigate the risk of inappropriate use of credentials by individuals with administrative rights?
An organization is looking to integrate security concepts into the code development process early in development to detect issues before the software is launched. Which advantage does the organization gain from using Static Application Security Testing (SAST) techniques versus dynamic application security testing techniques?
An attacker wants to decrypt a message and has no knowledge of what may have been in the original message. The attacker chooses to use an attack that will exhaust the keyspace in order to decrypt the message. What type of cryptanalytic attack is the attacker using?
According to quality function deployment (QFD), customer needs are gathered through:
During an emergency management and planning session, an organization is discussing how to identify, prevent, prepare for, or respond to emergencies. Which of the following will provide the BEST possible outcome?
APerform drills on a recurring basis.
B.Harden all critical facilities.
C.Outsource to an external organization.
D.Allocate 100% of required funds.
The help desk received a call from a user noting the digital certificate on the organization-issued security identification card was invalid. Which is the BEST reason the certificate stopped working?
In the context of mobile device security, which of the following BEST describes why a walled garden should be implemented?
Which of the following actions will result In lower inventory levels?
Which of the following production activity control (PAC) techniques focuses on optimizing output?
A computer forensic analyst is examining suspected malware from a computer system post-attack. Upon reverse engineering the code, the analyst sees several concerning instructions. One of those concerning instructions is that it installs a Unified Extensible Firmware Interface Basic Input/Output System (BIOS) rootkit, and when the system is then rebooted, the BIOS checks for a certain unknown program to be installed. Which security feature MOST likely would have detected and prevented this type of attack if already on the system?
What is the process when a security assessor compiles potential targets from the attacker’s perspective, such as data flows, and interactions with users?
What is the MOST important security benefit of comprehensive asset management?
A United States (US)-based online gaming provider, which operates in Germany, collects and uses a large amount of user behavioral data. A customer from Germany requests a copy of all their personal data.
What is the MOST appropriate course of action for the organization to take?
An organization has network services in a data center that are provisioned only for internal use, and staff at offices and staff working from home both use the services to store sensitive customer data. The organization does not want the Internet Protocol (IP) address of the service to receive traffic from users not related to the organization. Which technology is MOST useful to the organization in protecting this network?
In which of the following environments is capable-to-promise (CTP) more appropriate than available-to-promise (ATP)?
Which of the following situations is most likely to occur when using a push system?
A financial institution is implementing an Information Technology (IT) asset management system. Which of the following capabilities is the MOST important to include?
Which of the following is the benefit of using Security Content Automation Protocol (SCAP) version 2 on endpoint devices?
In Company XYZ, transaction-costing capability has been Integrated into the shop floor reporting system. A batch of 20 units was started in production. At the fourth operation, 20 units are reported as complete. At the fifth operation, 25 units are reported as complete. When all operations are complete, 20 units are checked into the stockroom. If the error at the fifth operation is undetected, which of the following conditions will be true?
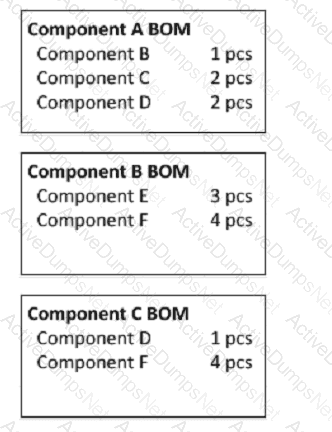
Given the bill of material (BOM) information below and independent requirements of 10 pieces (pcs) per week of Component A and 20 pieces (pcs) per week of Component B, what is the weekly gross requirement of component F?
After a data loss event, an organization is reviewing its Identity and Access Management (IAM) governance process. The organization determines that the process is not operating effectively. What should be the FIRST step to effectively manage the IAM governance process?
A semiconductor manufacturer is writing a physical asset handling policy. Which of the following is MOST likely to be the rationale for the policy?
An organization is migrating some of its applications to the cloud. The Chief Information Security Officer (CISO) is concerned about the accuracy of the reports showing which application should be migrated and how many applications reside on each server. As a result, the CISO is looking to establish asset management requirements. Which of these elements should be considered part of asset management requirements?
Zombieload, Meltdown, Spectre, and Fallout are all names of bugs that utilized which of the following types of attack?
An order winner during the growth stage of a product's life cycle is:
Which of the following Internet Protocol Security (IPSec) components provides the MOST confidentiality for the information that is being transmitted?
In which of the following situations would you use an X-bar chart?
During a manual source code review, an organization discovered a dependency with an open-source library that has a history of being exploited. Which action should the organization take FIRST to assess the risk of depending on the open-source library?
Which of the physiological biometric scanning methods is considered the MOST invasive?
A web application is found to have SQL injection (SQLI) vulnerabilities. What is the BEST option to remediate?
A newly hired Chief Information Security Officer (CISO) is now responsible to build a third-party assurance for their organization. When assessing a third-party, which of the following questions needs to be answered?
What FIRST step should a newly appointed Data Protection Officer (DPO) take to develop an organization's regulatory compliance policy?
Which of the following planes directs the flow of data within a Software-Defined Networking (SDN) architecture?
When an organization is recruiting for roles within the organization, at which stage of the employee life cycle are termination procedures incorporated?
The master schedule is an Important tool in the sales and operations planning (S&OP) process because it:
A security engineer must address resource sharing between various applications without adding physical hardware to the environment. Which secure design principle is used to BEST segregate applications?
Which of the following statements is true about total productive maintenance (TPM)?
If fixed costs are §200,000 and 20,000 units are produced, a unit's fixed cost is §10. This is an example of:
In which cloud computing model is Identify And Access Management (IAM) the responsibility of a service provider?
Which of the following regarding authentication protocols is a PRIMARY consideration when designing an authentication and key management system?
A company uses planning bills of material (BOMs) in its planning process extensively. Which of the following scenarios would present the biggest challenge to this planning process?
An advertising agency is working on a campaign for a prospective client. Competitors are working on a similar campaign and are interested in knowing what the firm has designed. What should the advertising agency do to BEST ensure intellectual property does not leave the organization?
A large volume of outbound Transmission Control Protocol (TCP) connections from the same source Internet Protocol (IP) address was observed at a satellite office firewall. Which of the following is the MOST likely explanation?
Internet Small Computer Systems Interface (iSCSI) protocol relies on Transmission Control Protocol/Internet Protocol (TCP/IP). Which can be used maliciously to interrupt the flow of data. Which Information Technology (IT) component would be impacted by such a disruption?
What is the MAIN reason security is considered as part of the system design phase instead of deferring to later phases?
What is the PRIMARY benefit an organization obtains by cybersecurity framework to their cybersecurity program?
Marketing has requested a significant change in the mix for a product family. The requested change falls between the demand and the planning time fences. The most appropriate action by the master scheduler is to:
A disadvantage of a capacity-lagging strategy may be:
Which of the following provides for continuous improvement of the change control process?
If all other factors remain the same, when finished goods inventory investment is increased, service levels typically will:
Which of the following does a federated Identity Provider (IDP) need in order to grant access to identity information?
Which of the following benefits typically will be realized when switching from a functional to a cellular layout?
Which of the following may authorize an organization to monitor an employee’s company computer and phone usage?
Open Authorized (OAuth) has been chosen as technology to use across applications in the enterprise. Which of the following statements is TRUE about an OAuth token?
An organization wants to ensure the security of communications across its environment. What is the BEST way to provide confidentiality of data from handheld wireless devices to the internal network?
The question below is based on the following information:
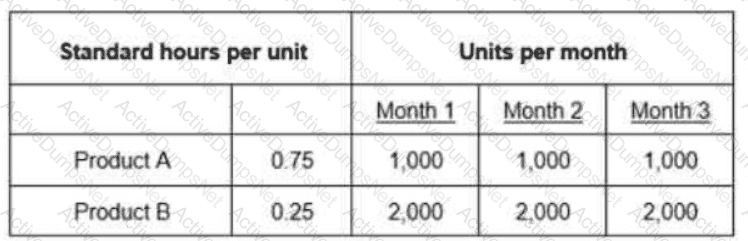
Work Center 1 has an available capacity of 1,200 hours per month. Which of the following amounts represents the cumulative difference between the required capacity and the available capacity of Months 1 through 3?
A company confirms a customer order based on available capacity and inventory, even though the current production plan does not cover the entire order quantity. This situation is an example of what type of order fulfillment policy?
Which of the following BEST describes the responsibility of an information System Security Officer?
The primary reason for tracing a component with scheduling problems to Its master production schedule (MPS) item is to:
Which of the following statements correctly describes the relationship between the strategic plan and the business plan?
A security officer has been tasked with performing security assessments on the organization’s in the current calendar year. While collecting data, the officer realizes that more than one business until will be engaged in the assessment. What activity MUST be included in the data collection phase?
An organizational policy requires that any data from organization-issued devices be securely destroyed before disposal. Which method provides the BEST assurance of data destruction?
During the initiation phase of a project to acquire a customer relation management system, what is the FIRST step a project team will take for early integration of security?
In restoring the entire corporate email system after a major outage and data loss, an email administrator reads a few email message exchanges between the human resources manager and a candidate for an open position. Which of the following BEST describes the behavior of the email administrator, and why?
Which of the following BEST describes the purpose of black hat testing during an assessment?
Which if the following is the FIRST control step in provisioning user rights and privileges?
A cybersecurity analyst has recently been assigned to work with a product development team. The team has usually needed to perform a lot of rework late in the development cycle on past projects due to application security concerns. They would like to minimize the amount of rework necessary. Which would be the BEST option to enable secure code review early in the product development?
Which of the following is the GREATEST threat for a Border Gateway Protocol (BGP) deployment on the internet?
How would a master production schedule (MPS) be used In an assemble-to-order (ATO) manufacturing environment?
An organization is transitioning from a traditional server-centric infrastructure to a cloud-based Infrastructure. Shortly after the transition, a major breach occurs to the organization's databases. In an Infrastructure As A Service (IaaS) model, who would be held responsible for the breach?
Additional requirements that are outside the original design are being added to a project, increasing the timeline and cost of the project.
What BEST describes the requirement changes that are happening?
Which of the following conditions is most likely to result in planned production that is greater than the total demand over the sales and operations planning (S&OP) horizon for a product family that is
made to stock?
An organization wants to ensure a risk does not occur. The action taken is to eliminate the attack surface by uninstalling vulnerable software. Which risk response strategy did the organization take?
An audit of antivirus server reports shows a number of workstations do not have current signatures installed. The organization security standard requires all systems to have current antivirus signatures. What distinct part of the audit finding did the auditor fail to include?
We have observed the inventory system does not handle plastic parts well." What should be added to the problem statement to make it more useful?
Which of the following product design approaches are likely to reduce time to market for a global supply chain?
A Software As A Service (SaaS) solution was compromised due to multiple missing security controls. The SaaS deployment was rushed and the Software Development Life Cycle (SDLC) was not followed. Which SDLC phase would have been MOST effective in preventing this failure?
Which approach will BEST mitigate risks associated with root user access while maintaining system functionality?
Which of the following is the workflow of the identity and access provisioning lifecycle?
What BEST describes the end goal of a Disaster Recovery (DR) program?
An organization’s external auditors have issued a management letter identifying significant deficiencies related to the effectiveness of the previous year’s global access certification. The organization wants to move from a department-based access control system to a Role-Based Access Control (RBAC) system. In addition to quickly and securely provisioning users by granting membership into predefined and approved roles, which of these presents the BEST reason to do so?
One of the most useful tools for analyzing the sustainable footprint is:
A team is tasked with developing new email encryption software. To ensure security, what will be the PRIMARY focus during the initial phase of development?
An organization currently has a network with 55,000 unique Internet Protocol (IP) addresses in their private Internet Protocol version 4 (IPv4) network range and has acquired another organization and must integrate their 25,000 endpoints with the existing, flat network topology. If subnetting is not implemented, which network class is implied for the organization’s resulting private network segment?
Asymmetric cryptography uses which type of key to encrypt data?
The question below is based on the following standard and actual data of a production order
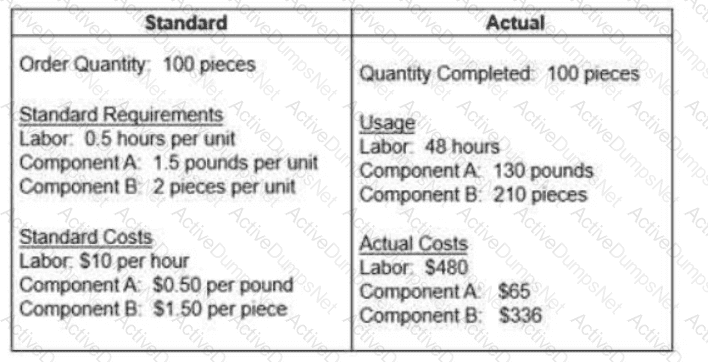
Which of the following statements about variances is true?
A company assembles kits of hand tools after receipt of the order from distributors and uses two-level master scheduling. The appropriate levels of detail for the forecasts that are input to master scheduling would be total number of kits and:
Which of the following methods would be appropriate for forecasting the demand for a product family when there is a significant trend and seasonality in the demand history?
A vendor has been awarded a contract to supply key business software. The vendor has declined all requests to have its security controls audited by customers. The organization insists the product must go live within 30 days. However, the security team is reluctant to allow the project to go live. What is the organization's BEST next step?
Which Virtual Private Network (VPN) protocol provides a built-in encryption?
The Business Continuity Plan (BCP) has multiple components. The information security plan portion must prioritize its efforts. Which 3 aspects of information security MUST be prioritized?
An organization starts to develop a drone inspection and defect detection system includes different subsystems running at different clouds from different service providers. During the architectural design phase, which security architecture principle should be the MOST important for the security engineer to apply?
Privacy requirements across national boundaries MOST often require protection of which data types?
Which of the following is the MOST effective practice for tracking organizational assets when removed from the premises?
Following the setting of an organization’s risk appetite by senior management, a risk manager needs to prioritize all identified risks for treatment. Each risk has been scored based on its Annualized Loss Expectancy (ALE). Management has asked for an immediate risk mitigation plan focusing on top risks. Which is the MOST effective approach for the risk manager to quickly present a proposal to management?
What is a strategic process that is aimed at considering possible attack scenarios and vulnerabilities within a proposed or existing application environment for the purpose of clearly identifying risk and impact levels?
Which of the common vulnerabilities below can be mitigated by using indexes rather than actual portions of file names?
Which of the following terms below BEST describes the measure of confidence that the security features, practices, procedures, and architecture of an information system accurately mediates and enforces security policy?
Which of the following vulnerability types is also known as a serialization flaw and affects the integrity of two processes interacting with the same resource at the same time?
An organization provides customer call center operations for major financial service organizations around the world. As part of a long-term strategy, the organization plans to add healthcare clients to the portfolio. In preparation for contract negotiations with new clients, to which cybersecurity framework(s) should the security team ensure the organization adhere?
An information system security manager is tasked with properly applying risk management principle to their cloud information system as outlined by the National Institute of Standards and Technology (NIST).
Which of the following is the INITIAL step?
A Managed Service Provider (MSP) provides hardware and software support for system maintenance and upgrades to a client organization. Who is MOST responsible for auditing security controls related to the hardware and software?
What is the BEST item to consider when designing security for information systems?
In the sales and operations planning (S&OP) process, the demand management function provides:
What is the BEST preventive measure against employees abusing access privileges?
When developing information security policies, What is the PRIMARY concern?
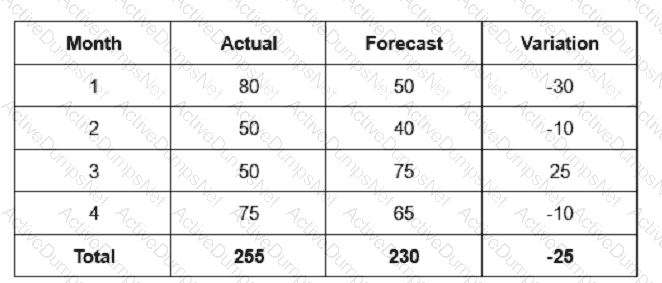
Based on the above table, calculate the mean absolute deviation (MAD).
Which of the following is the BEST type of fire extinguisher for a data center environment?
