A customer has submitted a request for a new wireless connection In the main office so visitors can reach the Internet to check their email. The customer is concerned about security and does not want visitors to be able to access the internal finance server. Which of the following BEST describes the correct configuration?
A network technician has deployed a new 802.11ac network and discovers some of the legacy POS equipment only supports WPA and 802.11a. Which of the following is the MOST secure method of connecting all devices while avoiding a performance impact to modern wireless devices?
A network extension needs to be run to a location 500ft (152m) from the nearest switch. Which of the following solutions would work BEST? (Select TWO).
Log files show the admin user has logged into a public-facing device on several occasions in the evening. None of the technicians admit to doing any after-hours work, and the password has been changed several times but failed to prevent the logins. Which of the following should be the NEXT step to attempt to harden the device?
Which of the following should be configured to allow for IP-to-name resolutions?
A network administrator is installing a campus network of two routers, 24 switches, 76 APs, and 492 VoIP phone sets. Which of the following additional devices should the administrator install to help manage this network?
A human resources manager notifies the IT manager the night before an employee will be terminated so the employee's access rights can be removed. Which of the following policies is being exercised?
A vulnerability that would allow an unauthenticated, remote attacker to originate a DoS attack was found in a DHCP client implementation of a switch. Which of the following would BEST resolve the issue?
A few weeks after starting a new position, Joe, a junior network administrator, receives a call from an internal number asking for his username and password to update some records. Joe realizes this may be a type of attack on the network, since he has full access to network resources. Which of the following attacks is described?
A company hires another firm to test the integrity of its information security controls. This is an example of
A technician is troubleshooting intermittent connectivity on a line-of-sight wireless bridge. Which of the following tools should the technician use to determine the cause of the packet loss?
A network technician sets up a new schedule on the backup server. Management has informed the technician that a full backup does not need to be completed every day. The technician sets up weekly full backups. Which of the following should the technician configure for the remaining days to MINIMIZE the daily backup size?
A network administrator reviews the following command output while troubleshooting a system that is unable to connect to the www.comptia.com website:
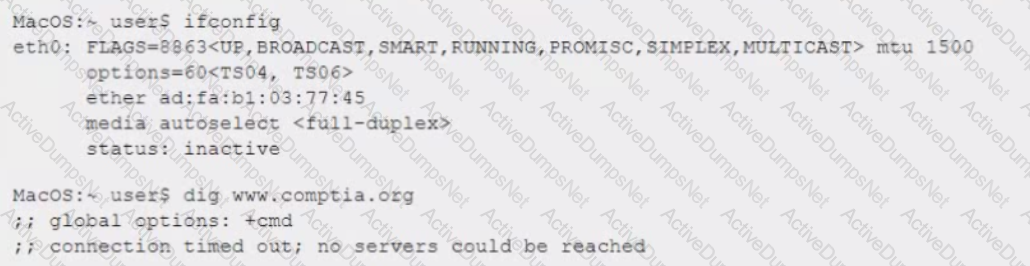
Which of the following is the reason the system cannot connect?
A network technician is configuring network addresses and port numbers for a router ACL to block a peer-to-peer application. Which of the following is the HIGHEST layer of the OSI model at which this router ACL operates?
A company has just installed a new cloud VoIP solution, however, users occasionally report poor call quality or dead air being present. Which of the following describes the NEXT troubleshooting step the technician should take?
After several changes to the network, a technician needs to ensure a client is checking for new hostname and IP pairings. Which of the following commands should the technician use to force new lookups?
A network technician is performing an initial configuration of a new network switch. Per company policy, the only authorized manner for remotely administering the switch is through a command line. Which of the following protocols should the technician disable to adhere to the company policy?
A network technician is reviewing switch ACLs to determine if they are causing communication issues with one PC. The PC’s IP address is 192.168.12.66. Which of the following is the network range found in the ACL that could have affected this PC?
Which of the following Is a network device that is responsible for separating collision domains?
A technician is preparing to dispose of old network devices. Which of the following policies and best practices would outline procedures for removing sensitive information and configurations from surplus equipment?
A network engineer is working on a network connectivity problem between a site in California and a site in New York The connection went down overnight and the engineer is unsure where the connection failed The technician is logged into the primary switch in the customer's network, which is also the company's connection to the WAN. Which of the following toots should the technician use to determine the last available network hop?
Ann. a user, reports that her desktop phone is not working on one cable. However, that cable provides connectivity to her laptop. A technician determines PoE is not provided to the end device. Which of the following is MOST likely the cause?
A network technician arrives at a remote office and is unable to connect a laptop to corporate resources using the wireless network. After checking the IP address, the network technician notices the assigned IP address does not belong to the corporate network IP scheme. Which of the following has the network technician discovered?
A network technician is installing and configuring a new router for the sales department. Once the task is complete, which of the following needs to be done to record the change the technician is masking to the company network?
A network administrator has deployed a secure wireless network that authenticates using Active Directory network credentials so individual users are uniquely identified when connected to the WLAN. Which of the following wireless technologies has the administrator configured?
A network technician receives a switch that is configured to support VLANs on its ports. At which of the following layers is this switch operating?
A technician discovered a company computer had a virus but was unable to remove it. The technician decided to erase the hard drive to eliminate the threat .Which of the following policies did the technician violate'?
A network technician needs to configure a device with an embedded OS so it can be connected to a wireless handheld scanner. Which of the following technologies should be configured on the OS to create the wireless connection?
A network technician is troubleshooting a problem with a user’s client-to-site VPN connection. The user is unable to establish a connection to the server, but the error message that appears on screen does not contain useful information. Which of the following should the technician do NEXT to troubleshoot the issue?
A company hires some temporary workers. On day one, the temporary employees report they are unable to connect to the network. A network technician uses a packet analysis tool and finds that many clients are continuously sending out requests for an IP address, but many of them are not receiving a response. Which of the following could be the cause of this issue?
A network technician notices that switches of the same model have different commands and security features while administering them. Which of the following hardening techniques should the technician perform on a regular schedule to ensure all switches have the same features and security functionality?
A network technician is reading a network diagram and looking for the edge router. Which of the following is MOST likely the symbol used for the router?
A company wants to implement a wireless infrastructure on its campus to meet the needs of its BYOD initiative. The company has users with legacy devices and wants to accommodate them while delivering speed to other users who have modern systems.
Which of the following standards BEST fits these requirements?
A shop owner wants to ensure that only a specified group of devices can access the wireless network. Which of the following methodologies will BEST ensure unauthorized devices cannot consume the shop owner’s limited Internet bandwidth?
A network technician is designing a network cable upgrade in a newly acquired office space. The IT manager wants to install a standardized twisted pair cable solution that supports speeds up to 1 Gbps and terminates with a standard RJ45 connector. Which of the following cable types should the technician suggest?
A company wants to provide its sales representatives with an easy-to-use method of securely connecting to the corporate network from any client network. Which of the following methods should the network technician implement?
Which of the following may state: "Employees may hot browse social media websites from company-owned computers?
Which of the following protocols would enable a company to upgrade its Internet connection by acquiring its own public IP prefixes and autonomous system number?
A user has received a new machine with The organization's standard baseline with no changes and the DHCP reservation is updated. The user now reports being unable to connect to the partner company's database. The network technician reviews the logs and sees this user was previously able to access the remote database without issue. Which of the following should the network technician check NEXT?
Which of the following allows for connectionless communications?
An office network consists of one two-port router connected to a 12-port switch. A four-port hub is also connected to the switch. On this particular network, which of the following is the number of collision domains that exist?
A company wants to implement a large number of WAPs throughout its building and allow users to be able to move around the building without dropping their connections Which of the following pieces of equipment would be able to handle this requirement?
Which of the following represents where the ISP's WAN connection is handed off to the local network?
A wireless administrator needs to implement an authentication method that provides individualized, scalable security for the users of a WLAN where roaming is a regular event. PKI is not available. Which of the following BEST addresses the requirements of this topology?
A technician is planning a network wiring installation and must ensure all cabling meets the installation requirements for air-handling spaces in the celling in case of a fire. Which of the following characteristics does
plenum cabling have to meet this requirement?
A network administrator is troubleshooting a connectivity issue to a remote switch. The administrator suspects the settings on the switch have been changed, causing the issue. Which of the following should the administrator reference to confirm the change?
A network technician is investigating an IP phone that does not register in the VoIP system Although it received an IP address, it did not receive the necessary DHCP options The information that is needed for the registration is distributes by the OHCP scope All other IP phones are working properly. Which of the following does the technician need to verify?
A small company decided to use a single virtual appliance to filter spam as well as a reverse proxy to filter traffic to its internal web server. Which of the following did the company MOST likely deploy?
A network technician is investigating a device that has been reported as responding slowly. Which of the following should the technician check FIRST?
A technician needs a way to allow clients to access a new application server on the network. Which of the following should the technician set up to achieve this objective? (Select TWO)
Which of the following technologies requires a username and password to authenticate to a backbone network?
A network technician needs to install network devices in a new building. The building will be a pan of the corporate network and has the connection to the core network already. Which of the following devices must be configured in the new building?
Which of the following accurately describes a warm site in datacenter disaster recovery?
The management team has instituted a 48-hour RTO as part of the disaster recovery plan. Which of the following procedures would meet the policy’s requirements?
A network manager is drafting a document mat outlines what employees can and cannot do when using personal tablets that are connected to the network. Which of the following is the manager drafting?
A security team needs to restrict access to a wireless network in a certain area. Which of the following would be used to enforce this restriction?
A switch needs to be configured to carry three VLANs across on a single port. Which of the following switching features should be used and which of the following terms is given to the VLANs?
A network technician receives a call from Joe, a user about slow speeds when he copies large files from the file server Other users can copy the same files in a matter of seconds. Prior to experiencing the slow speeds, Joe moved the computer farther from the network jack and built his own Cat5 cable During troubleshooting the on-site network technician observes Joe is only getting a 10Mbps connection speed while everyone else who is connected to the switch is getting 1000Mbps. Which of the following should the network technician check NEXT? (Select TWO)
A lab environment hosts Internet-facing web servers and other experimental machines, which technicians use for various tasks A technician installs software on one of the web servers to allow communication to the company's file server, but it is unable to connect to it Other machines in the building are able to retrieve files from the file server. Which of the following is the MOST likely reason the web server cannot retrieve the files, and what should be done to resolve the problem?
A network administrator needs to extend an organization's network to a nearby building that has unused SMF already installed. The network administrator has decided to create a switch-to-switch uplink. Which of the following standards would be the BEST to use?
A company moved to a new building that was designed with WiFi only. During the first month, users reported good WiFi coverage. However, after the first month, users began reporting slow speeds and constant disconnects. Upon investigation, an engineer determines the SNR is currently 10dB compared to a baseline SNR of 42dB. Which of the following MOST likely causing the WAFI issues?
A document outlining the types of actions allowed on the corporate network would be BEST defined as an:
Which of the following DNS record types assists with the routing of email?
A systems administrator has received a new appliance to monitor the health and status of internal servers that are not located in the organization's DMZ, The monitored servers are secured and restricted for specific use cases. The systems administrator activates email alerts for when a status exceeds a certain threshold. However, during testing, emails are not reaching the recipients as expected. The systems administrator has confirmed the messages are queued in the appliance. Which of the following would be the MOST likely cause of the issue?
A network technician built a wireless network in a ten-story office building but has found it does not perform well. The technician performed the following steps during the installation:
* Researched and decided that 802.11ac would be the best technology
* Ensured the switch supports PoE+
* Purchased an AP for each floor and spare APs in case of failure
* Put each AP into non-overlapping channels
Which of the following is the MOST likely reason users are experiencing poor performance?
A company's users have been reporting excessive latency when connecting to the Internet. The network administration team submitted a change request to upgrade all the obsolete network equipment from 100Mbps to 1Gbps and It was approved. Which of the following documentation types will be needed to measure the success or failure of the upgrade project?
Some similar devices are experiencing system crashes on the same day of every month. Which of the following is the MOST efficient approach to detect the probable cause of the recurring incidents?
A network administrator is attempting to limit the installation of malware on company workstations. The administrator wants to remove root access from the user accounts. Which of the following is this an example of?
A network technician is installing a new SOHO wireless router for a client. After configuring and securing the wireless network, the technician begins hardening the wireless router. Which of the following should the network technician do FIRST?
A systems administrator is running a VoIP network and is experiencing jitter and high latency. Which of the following would BEST help the administrator determine the cause of these issues?
Which of the following allows for file-level network storage?
When trying to determine why users are unable to access a web-based application that was working the previous day, which of the following should be the FIRST QUESTION NO: to ask to determine the scope of the issue?
An attacker quickly gains administrative access to a network device. Which of the following MOST likely allowed the attacker to guess the password?
A network technician is coordinating the upgrade of the company’s WAP firmware with all the remote locations. The company has occasionally experienced errors when transferring large files to some of the remote offices. Which of the following should be used to ensure files arrive without modifications?
A technician is asked to provide centralized SSID management across the entire WAN. The BEST solution would be to:
A network technician needs to install the latest firmware on the switch to address a recently discovered vulnerability. Which of the following should the technician do to have a rollback plan in case of issues with the new firmware? (Choose two.)
A network technician needs to upgrade a production Windows server to the latest service pack. In which of the following should the work plan and recovery procedure be documented?
A consulting company was hired to project and deploy a new datacenter in a different city. This new facility must have the same components installed as the current datacenter to be ready to take over all the network services as soon as the primary site becomes unavailable. Which of the following describes what will be deployed in the new location?
A security administrator wants to implement the ability to prevent an authorized user from tailgating into the office building. Which of the following should be implemented?
A network technician needs to subnet the network. The marketing department has 28 devices. Which of the following private IP address spaces should be used to ensure the MINIMUM number of unused IP addresses?
Which of the following would block access to an untagged port when connected to a Layer 2 device?
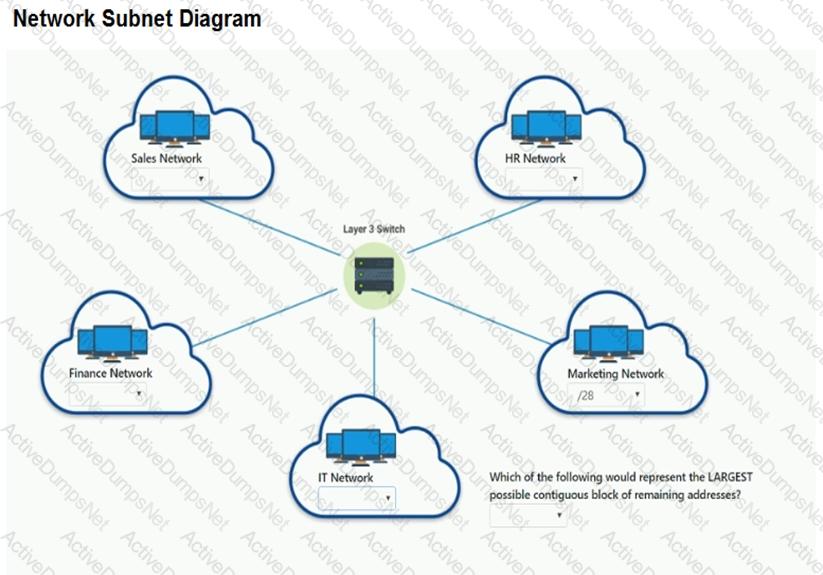
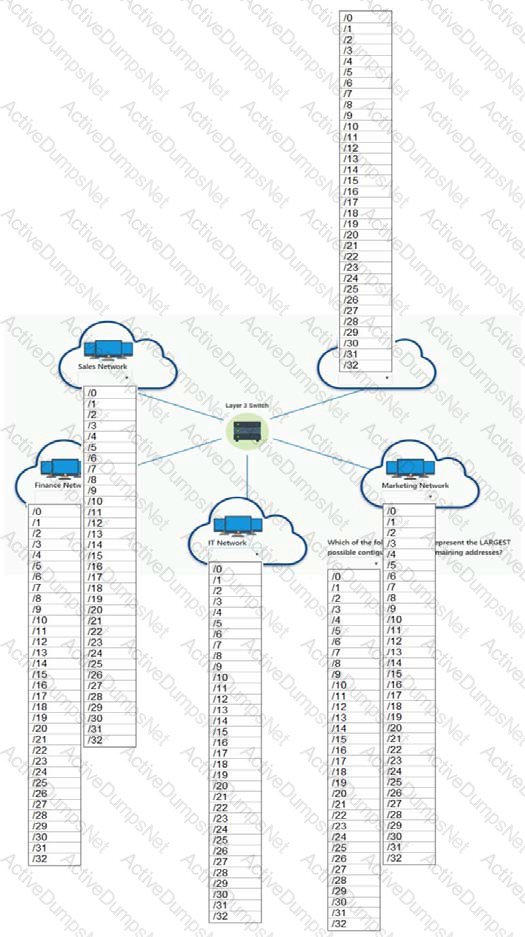
Corporate headquarters provided your office a portion of their class B subnet to use at a new office location.
Range Given: 172.30.232.0/24
INSTRUCTIONS
Allocate the minimum number of addresses (using CIDR notation) needed to accommodate each department.
After accommodating each department, identify the unused portion of the subnet by responding to the question on the graphic.
All drop downs must be filled.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network engineer wants to change how employees authenticate to the wireless network. Rather than providing a pre-shared key, the engineer wants employees to be able to authenticate with the same unique company user ID and password they use for accessing other services, such as email and document sharing. The engineer also wants to receive daily reports of login attempts on the wireless network. Which of the following should be installed to achieve this goal?
Which of the following provides information about how often some devices fail so the IT department can take proactive measures?
In the past, users brought personal laptops to the office to bypass some of the security protocols on their desktops. Due to new security initiatives, management has asked that users not be allowed to attach personal devices to the network. Which of the following should a technician use to BEST meet this goal?
A new DSL circuit was installed to replace the cable service and is not functioning. A network administrator needs to create a cable to connect the circuit. Which of the following connector types should the network administrator use on the cable?
Multiple users are experiencing slow performance when downloading large files from a specific site. Which of the following should the technician do to check the connection to the external site?
Which of the following routing conventions is known as a link-state protocol?
A company’s Chief Information Security Officer (CISO) has decided to increase overall network security by implementing two-factor authentication. All users already have username/password combinations and require an additional factor of authentication. Which of the following would satisfy the requirements?
Which of the following statements about the OSI model is true?
A security administrator wants to implement the ability to prevent an unauthorized user from tailgating into the office building. Which of the following should be implemented?
A network administrator is configuring a new Internet connection. The ISP provided a fiber-optic handoff, but the company’s firewall only supports copper Ethernet interfaces. The administrator wants to connect the devices as easily as possible. Which of the following would be the BEST way to provide the connectivity needed?
A network administrator needs to implement a new IP subnet containing 29 hosts. It is possible that the number of hosts in that subnet could eventually double. The company only has a single, unused public IP network left to work with: 164.10.12.0/24. Which of the following would be the BEST way to divide this network without wasting addresses?
Which of the following is used to purposely attack a system to exploit vulnerabilities?
A network technician is adding a 10/100 switch with RJ45 connectors to the company network to accommodate new computers being added to a network segment. There is no auto-MDIX port on the switch that needs to be connected to the existing switch on the segment. Which of the following should the technician use to make the connection?
A network analyst is providing access to an FTP server that stores files that are needed by external contractors who are working on a project. In which of the following network locations should the FTP server be placed to achieve the MOST secure environment?
Which of the following additional capabilities does a next generation firewall provide beyond a standard network firewall? (Choose two.)
A network technician is setting up a new web server on the company network. One of the requirements for the web server is to ensure the end users can securely authenticate to the application to perform their job duties. Which of the following ports should the network technician request from the firewall team to comply with this requirement?
Company policy dictates that full backups are taken every Sunday evening, and incremental backups occur Monday through Saturday in the evening. If data loss were to occur on a Thursday before the backup window, which of the following is the number of backup sets that would be needed to retrieve the lost data come Friday morning?
Which of the following would be BEST for continually monitoring and alerting of possible attacks on a network?
A switch vendor recently released a patch to fix a critical vulnerability found in its switch OS. Which of the following should a network administrator do NEXT according to best practices?
A new technician has been tasked with checking the status of a switchport. The technician needs to find the information quickly without the use of command-line utilities. Which of the following remote management methods would help the technician?
Joe, a network technician, has received a report that one of his clients is experiencing an issue connecting to the network. Joe observes two clients are connected to a hub, which is connected to separate wall jacks. Which of the following has MOST likely occurred?