A security analyst receives a mobile device with symptoms of a virus infection. The virus is morphing whenever it is from sandbox to sandbox to analyze. Which of the following will help to identify the number of variations through the analysis life cycle?
An analyst identifies multiple instances of node-to-node communication between several endpoints within the 10.200.2.0/24 network and a user machine at the IP address 10.200.2.5. This user machine at the IP address 10.200.2.5 is also identified as initiating outbound communication during atypical business hours with several IP addresses that have recently appeared on threat feeds.
Which of the following can be inferred from this activity?
An organization has a policy prohibiting remote administration of servers where web services are running. One of the Nmap scans is shown here:
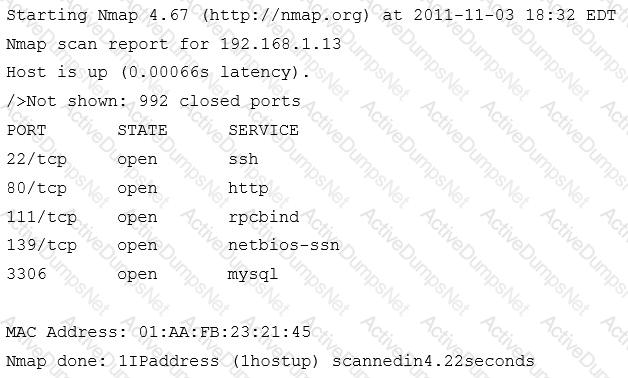
Given the organization’s policy, which of the following services should be disabled on this server?
A security analyst is concerned that a default administrator account on workstations will make it easy for a threat actor to move laterally throughout the domain. The security analyst has the approval to remediate the risk. Which of the following solutions would achieve this objective? (Select TWO.)
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has received the following output from the latest scan:
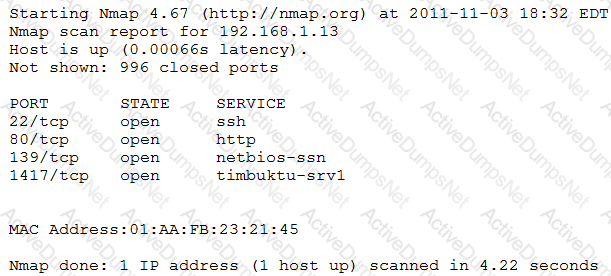
The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
Creating an isolated environment in order to test and observe the behavior of unknown software is also known as:
In comparison to non-industrial IT vendors, ICS equipment vendors generally:
A security analyst is creating ACLs on a perimeter firewall that will deny inbound packets that are from internal addresses, reversed external addresses, and multicast addresses. Which of the following is the analyst attempting to prevent?
A hacker issued a command and received the following response:
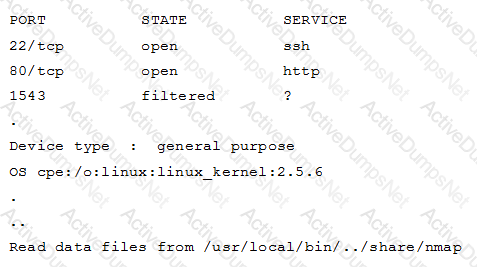
Which of the following describes what the hacker is attempting?
A security analyst is performing ongoing scanning and continuous monitoring of the corporate datacenter. Over time, these scans are repeatedly showing susceptibility to the same vulnerabilities and an increase in new vulnerabilities on a specific group of servers that are clustered to run the same application. Which of the following vulnerability management processes should be implemented?
A cybersecurity analyst develops a regular expression to find data within traffic that will alarm on a hit.
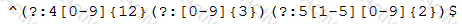
The SIEM alarms on seeing this data in cleartext between the web server and the database server.
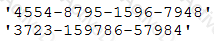
Which of the following types of data would the analyst MOST likely to be concerned with, and to which type of data classification does it belong?
A security analyst received an alert from the antivirus software identifying a complex instance of malware on a company’s network. The company does not have the resources to fully analyze the malware and determine its effect on the system. Which of the following is the BEST action to take in the incident recovery and post-incident response process?
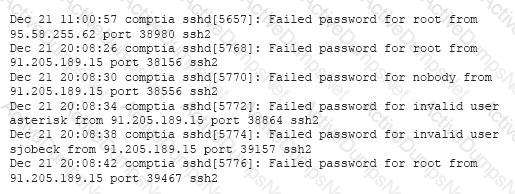
A security analyst Is reviewing the overnight authentication activity and sees the following set of logs from last evening:
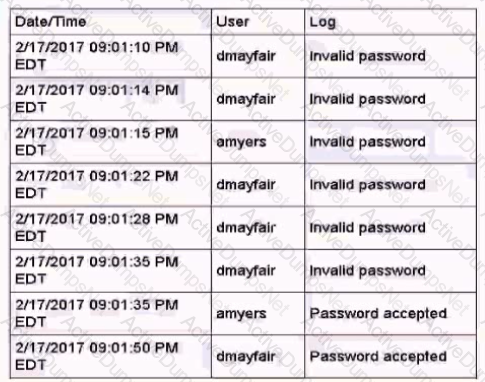
Which of the following should the analyst do NEXT?
A security analyst has discovered that an outbound SFTP process is occurring at the same time of day for the past several days. At the time this was discovered, large amounts of business critical data were delivered. The authentication for this process occurred using a service account with proper credentials. The security analyst investigated the destination IP for this transfer and discovered that this new process is not documented in the change management log. Which of the following would be the BEST course of action for the analyst to take?
Ransomware is identified on a company's network that affects both Windows and MAC hosts. The command and control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1. Iholdbadkeys.com, which resolves to IP address 72.172.16.2.
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?
A company uses a managed IDS system, and a security analyst has noticed a large volume of brute force password attacks originating from a single IP address. The analyst put in a ticket with the IDS provider, but no action was taken for 24 hours, and the attacks continued. Which of the following would be the BEST approach for the scenario described?
After reading about data breaches at a competing company, senior leaders in an organization have grown increasingly concerned about social engineering attacks. They want to increase awareness among staff regarding this threat, but do not want to use traditional training methods because they regard these methods as ineffective. Which of the following approaches would BEST meet the requirements?
An organization wants to perform network scans to Identify active hosts and vulnerabilities. Management places the highest priority on scans that mimic how an attack would progress. Iftime and resources allow, subsequent scans can be performed using different techniques and methods. Which of the following scan types and sequences would BEST suit the organization's requirements?
A security analyst has been asked to scan a subnet. During the scan, the following output was generated:
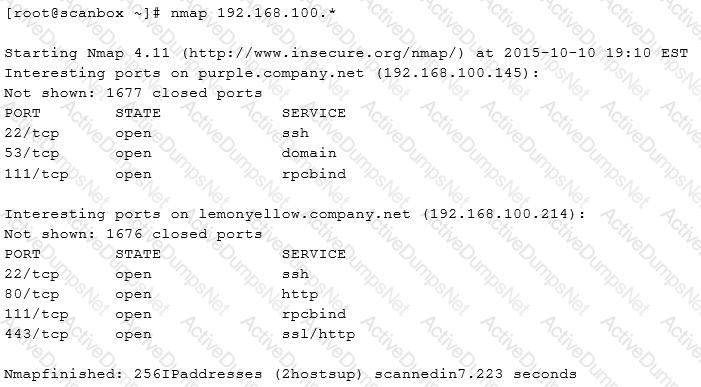
Based on the output above, which of the following is MOST likely?
During a physical penetration test at a client site, a local law enforcement officer stumbled upon the test questioned the legitimacy of the team.
Which of the following information should be shown to the officer?
An analyst was investigating the attack that took place on the network. A user was able to access the system without proper authentication. Which of the following will the analyst recommend, related to management approaches, in order to control access? (Choose three.)
While reviewing three months of logs, a security analyst notices probes from random company laptops going to SCADA equipment at the company’s manufacturing location. Some of the probes are getting responses from the equipment even though firewall rules are in place, which should block this type of unauthorized activity. Which of the following should the analyst recommend to keep this activity from originating from company laptops?
A security analyst is assisting in the redesign of a network to make it more secure. The solution should be low cost, and access to the secure segments should be easily monitored, secured, and controlled. Which of the following should be implemented?
Which of the following is MOST effective for correlation analysis by log for threat management?
Which of the following BEST describes the offensive participants in a tabletop exercise?
A security analyst is reviewing IDS logs and notices the following entry:
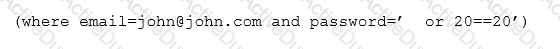
Which of the following attacks is occurring?
An application development company released a new version of its software to the public. A few days after the release, the company is notified by end users that the application is notably slower, and older security bugs have reappeared in the new release. The development team has decided to include the security analyst during their next development cycle to help address the reported issues. Which of the following should the security analyst focus on to remedy the existing reported problems?
A security analyst has been asked to remediate a server vulnerability. Once the analyst has located a patch for the vulnerability, which of the following should happen NEXT?
Which of the following actions should occur to address any open issues while closing an incident involving various departments within the network?
A reverse engineer was analyzing malware found on a retailer’s network and found code extracting track data in memory. Which of the following threats did the engineer MOST likely uncover?
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS.
If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean.
If the vulnerability is valid, the analyst must remediate the finding.
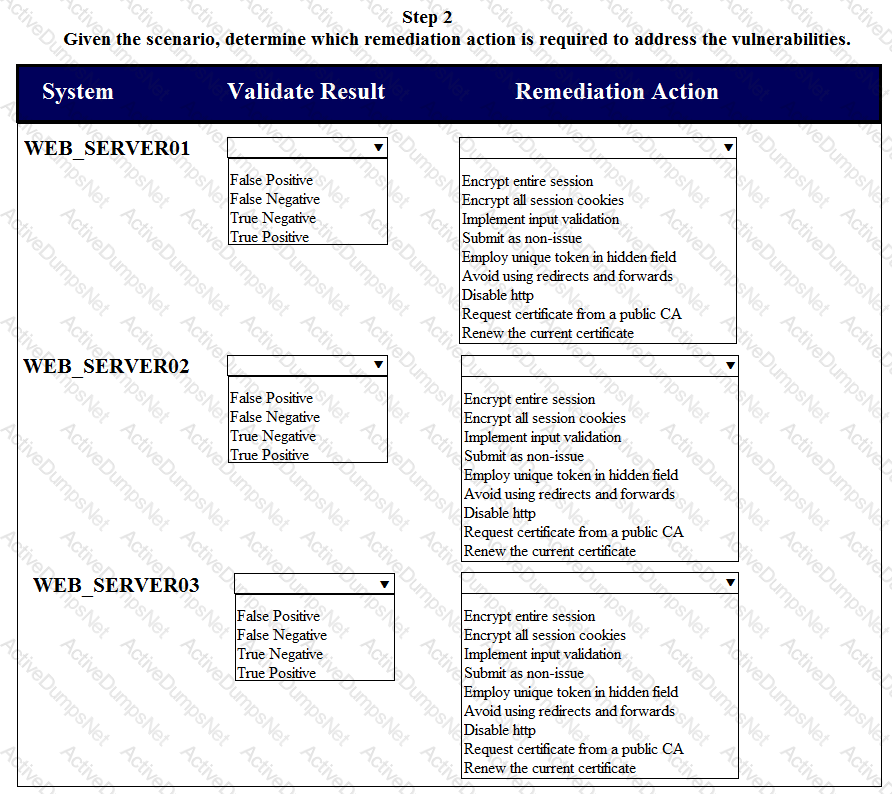
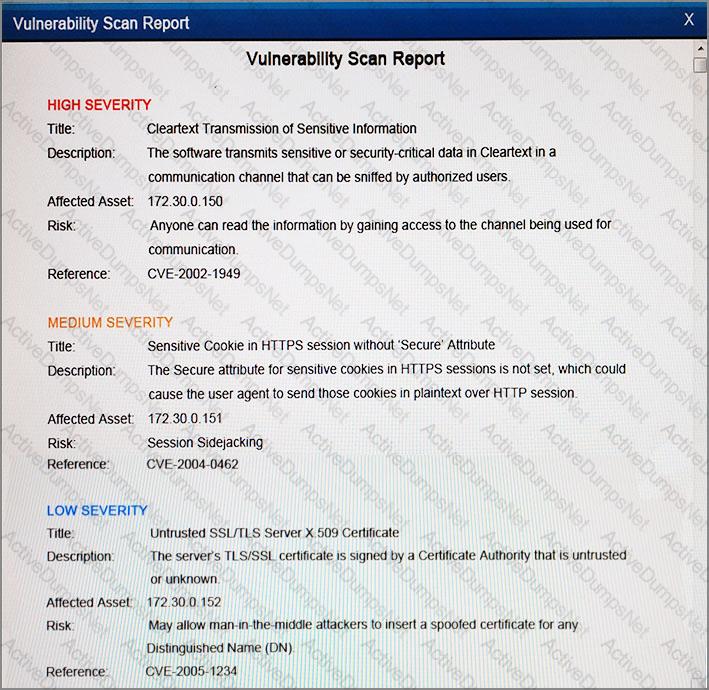
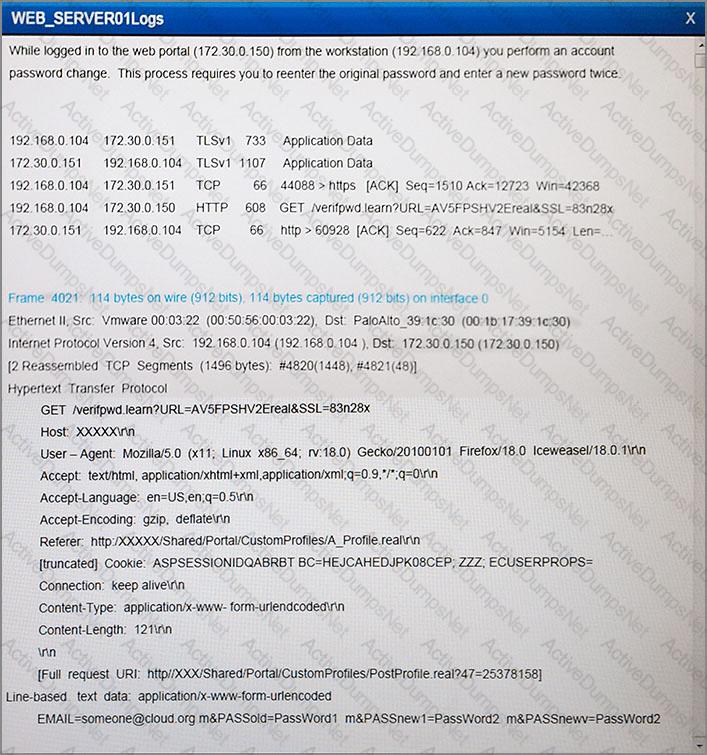
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
Instructions
STEP 1: Review the information provided in the network diagram.
STEP 2: Given the scenario, determine which remediation action is required to address the vulnerability.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button.
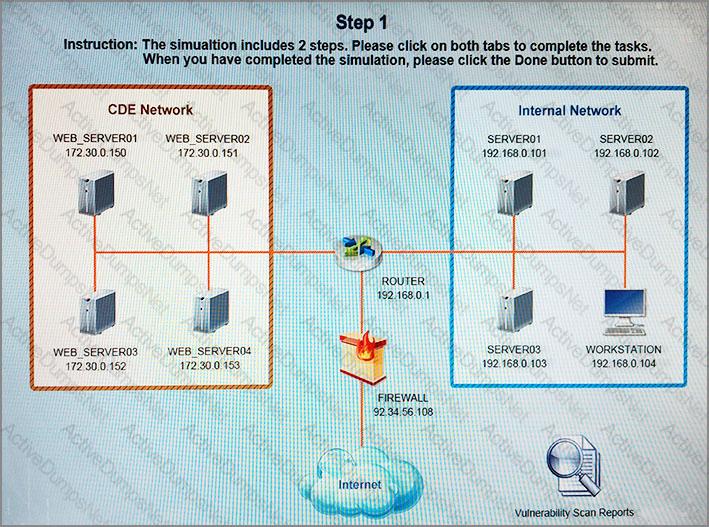
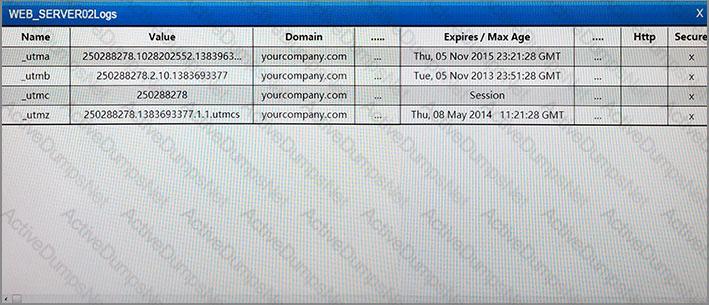
Law enforcement has contacted a corporation’s legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media. The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
A security analyst has created an image of a drive from an incident. Which of the following describes what the analyst should do NEXT?
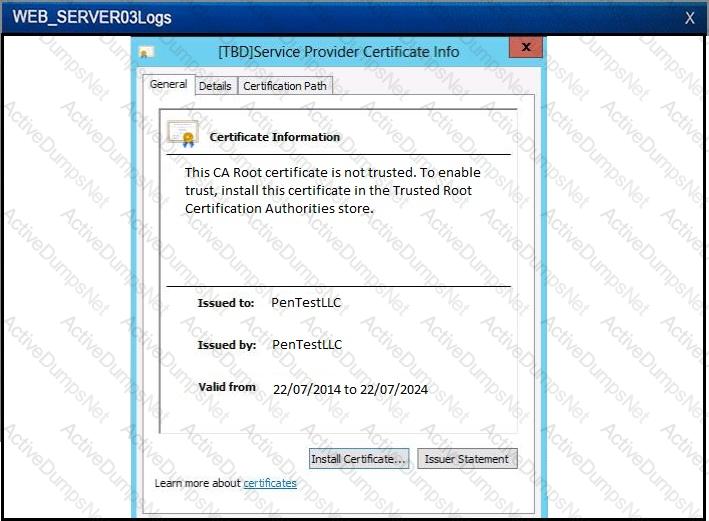
A security analyst is reviewing the following log after enabling key-based authentication.
Given the above information, which of the following steps should be performed NEXT to secure the system?
A company wants to update its acceptable use policy (AUP) to ensure it relates to the newly implemented password standard, which requires sponsored authentication of guest wireless devices. Which of the following is MOST likely to be incorporated in the AUP?
A security analyst is performing a forensic analysis on a machine that was the subject of some historic SIEM alerts. The analyst noticed some network connections utilizing SSL on non-common ports, copies of svchost.exe and cmd.exe in %TEMP% folder, and RDP files that had connected to external IPs. Which of the following threats has the security analyst uncovered?
After analyzing and correlating activity from multiple sensors, the security analyst has determined a group from a high-risk country is responsible for a sophisticated breach of the company network and continuous administration of targeted attacks for the past three months. Until now, the attacks went unnoticed. This is an example of:
An administrator has been investigating the way in which an actor had been exfiltrating confidential data from a web server to a foreign host. After a thorough forensic review, the administrator determined the server’s BIOS had been modified by rootkit installation. After removing the rootkit and flashing the BIOS to a known good state, which of the following would BEST protect against future adversary access to the BIOS, in case another rootkit is installed?
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port. Which of the following should the analyst use?
A vulnerability scan has returned the following information:
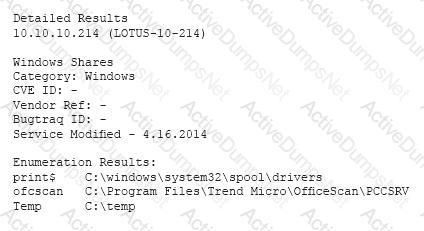
Which of the following describes the meaning of these results?
A cybersecurity analyst has received an alert that well-known “call home” messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the alert was a true positive, which of the following represents the MOST likely cause?
A security administrator determines several months after the first instance that a local privileged user has been routinely logging into a server interactively as “root” and browsing the Internet. The administrator determines this by performing an annual review of the security logs on that server. For which of the following security architecture areas should the administrator recommend review and modification? (Select TWO).
Using a heuristic system to detect an anomaly in a computer’s baseline, a system administrator was able to detect an attack even though the company signature based IDS and antivirus did not detect it. Further analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely occurred?
A cybersecurity analyst has several SIEM event logs to review for possible APT activity. The analyst was given several items that include lists of indicators for both IP addresses and domains. Which of the following actions is the BEST approach for the analyst to perform?
When network administrators observe an increased amount of web traffic without an increased number of financial transactions, the company is MOST likely experiencing which of the following attacks?
An analyst has received unusual alerts on the SIEM dashboard. The analyst wants to get payloads that the hackers are sending toward the target systems without impacting the business operation. Which of the following should the analyst implement?
A company has received the results of an external vulnerability scan from its approved scanning vendor. The company is required to remediate these vulnerabilities for clients within 72 hours of acknowledgement of the scan results.
Which of the following contract breaches would result if this remediation is not provided for clients within the time frame?
When reviewing network traffic, a security analyst detects suspicious activity:
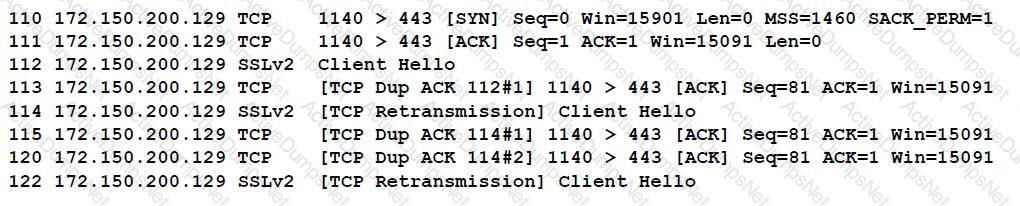
Based on the log above, which of the following vulnerability attacks is occurring?
An organization is experiencing degradation of critical services and availability of critical external resources. Which of the following can be used to investigate the issue?
A security analyst is concerned that employees may attempt to exfiltrate data prior to tendering their resignations. Unfortunately, the company cannot afford to purchase a data loss prevention (DLP) system. Which of the following recommendations should the security analyst make to provide defense-in-depth against data loss? (Select THREE).
A SIEM analyst noticed a spike in activities from the guest wireless network to several electronic health record (EHR) systems. After further analysis, the analyst discovered that a large volume of data has been uploaded to a cloud provider in the last six months. Which of the following actions should the analyst do FIRST?
A business-critical application is unable to support the requirements in the current password policy because it does not allow the use of special characters. Management does not want to accept the risk of a possible security incident due to weak password standards. Which of the following is an appropriate means to limit the risks related to the application?
A cybersecurity analyst was asked to discover the hardware address of 30 networked assets. From a command line, which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for accomplishing the task?
A new zero-day vulnerability was discovered within a basic screen capture app, which is used throughout the environment. Two days after discovering the vulnerability, the manufacturer of the software has not announced a remediation or if there will be a fix for this newly discovered vulnerability. The vulnerable application is not uniquely critical, but it is used occasionally by the management and executive management teams. The vulnerability allows remote code execution to gain privileged access to the system. Which of the following is the BEST course of actions to mitigate this threat?
The primary difference in concern between remediating identified vulnerabilities found in general-purpose IT network servers and that of SCADA systems is that:
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a special platform was discovered, allowing an attacker to capture the data between the end user and the web server providing these services. After investigating the platform vulnerability, it was determined that the web services provided are being impacted by this new threat.
Which of the following data types are MOST likely at risk of exposure based on this new threat? (Choose two.)
Given the following access log:
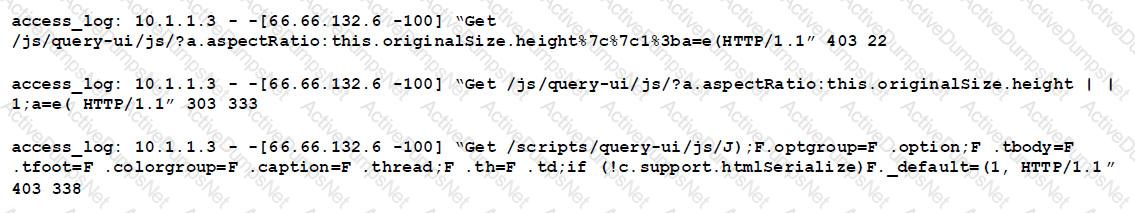
Which of the following accurately describes what this log displays?
A systems administrator is trying to secure a critical system. The administrator has placed the system behind a firewall, enabled strong authentication, and required all administrators of this system to attend mandatory training.
Which of the following BEST describes the control being implemented?
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
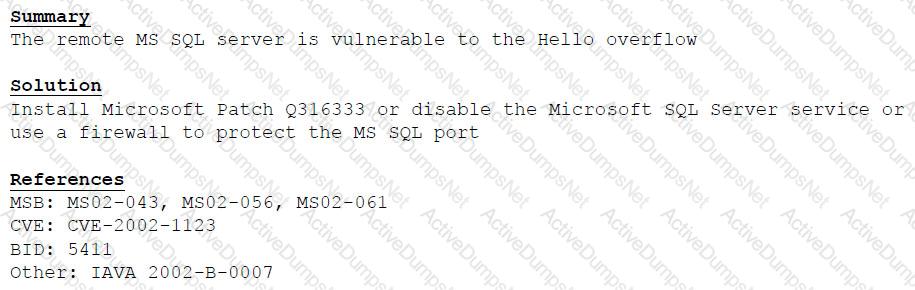
Based on the above information, which of the following should the system administrator do? (Select TWO).
A security analyst has noticed that a particular server has consumed over 1TB of bandwidth over the course of the month. It has port 3333 open; however, there have not been any alerts or notices regarding the server or its activities. Which of the following did the analyst discover?
A company has been a victim of multiple volumetric DoS attacks. Packet analysis of the offending traffic shows the following:

Which of the following mitigation techniques is MOST effective against the above attack?
A cybersecurity analyst is reviewing the following outputs:
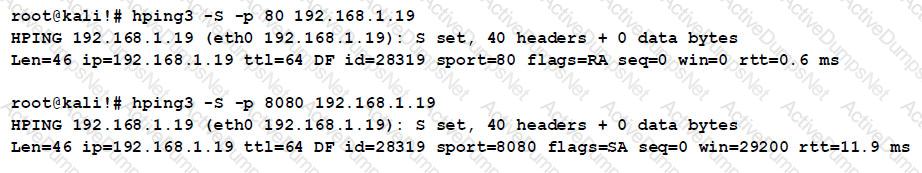
Which of the following can the analyst infer from the above output?
A security analyst wants to scan the network for active hosts. Which of the following host characteristics help to differentiate between a virtual and physical host?
A recently issued audit report highlighted exceptions related to end-user handling of sensitive data and access credentials. A security manager is addressing the findings. Which of the following activities should be implemented?
Three similar production servers underwent a vulnerability scan. The scan results revealed that the three servers had two different vulnerabilities rated “Critical”.
The administrator observed the following about the three servers:
Which of the following assessments is valid and what is the most appropriate NEXT step? (Select TWO).
A new policy requires the security team to perform web application and OS vulnerability scans. All of the company’s web applications use federated authentication and are accessible via a central portal. Which of the following should be implemented to ensure a more thorough scan of the company’s web application, while at the same time reducing false positives?
A security analyst begins to notice the CPU utilization from a sinkhole has begun to spike. Which of the following describes what may be occurring?
An organization wants to harden its web servers. As part of this goal, leadership has directed that vulnerability scans be performed, and the security team should remediate the servers according to industry best practices. The team has already chosen a vulnerability scanner and performed the necessary scans, and now the team needs to prioritize the fixes. Which of the following would help to prioritize the vulnerabilities for remediation in accordance with industry best practices?