A new identity management program was recently initialed to reduce risk and improve the employee experience. The environment is complex it does not support rest APIs but has multiple identity stores Password resets are the help desk's top ticket item and it takes the organization weeks to manually create access for new employees. The applications in the scope of the program are the enterprise service bus SaaS web portals and internal web portal. The goals of the program include
• Reducing costs by centralizing authentication and authorization
• Streamlining business processes
• Enabling employees to have immediate access
• Reducing password reset tickets by 90%
To meet the above goals and the business case which of the following authentication and authorization capabilities does the security architect need to implement?
A group of security consultants is conducting an assessment of a customer's network across multiple physical locations. To save time, the customer has allowed the consultants to install a single server inside the network perimeter. In addition to open-source intelligence gathering and social engineering, which of the following BEST describes the technique the consultants are employing?
During an audit, an information security analyst discovers accounts that are stil assigned to employees who no longer work for the company and new accounts that need to be verified against a list of authorized users. This type of auditing supports the development of:
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS -
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
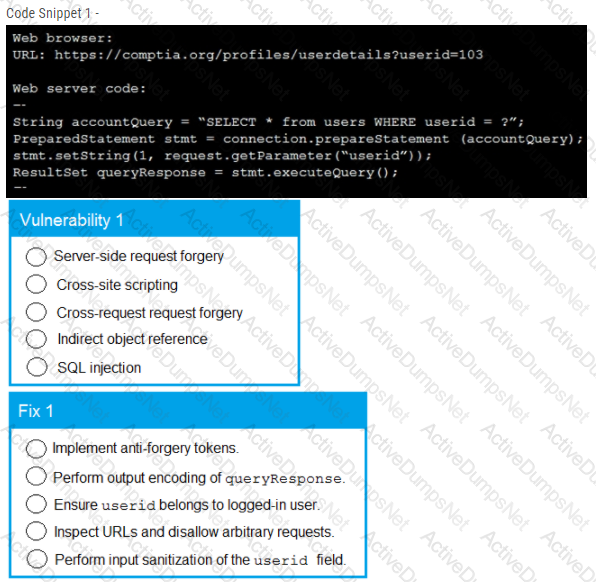
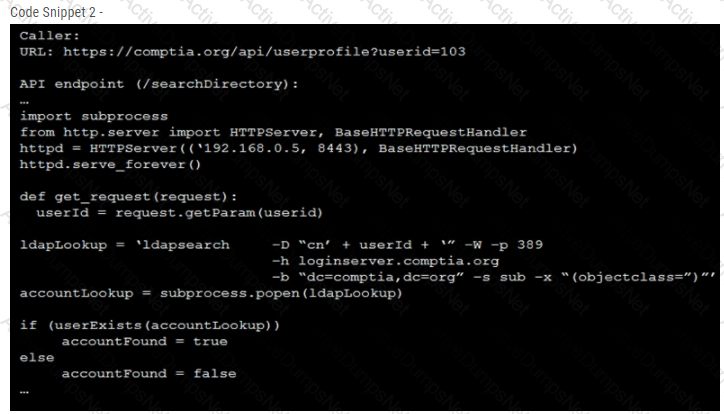
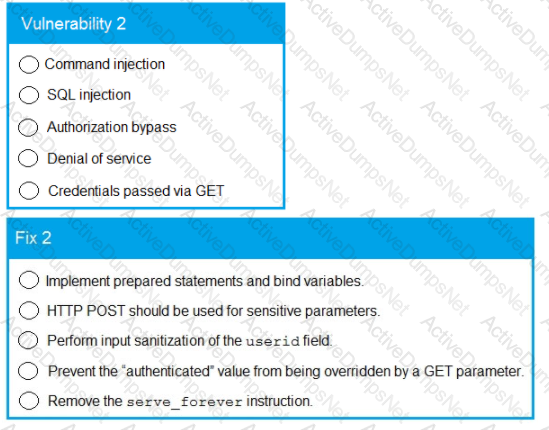
A line-of-business manager has deeded in conjunction with the IT and legal departments, that outsourcing a specific function to a third-party vendor would be the best course of action for the business to increase efficiency and profit Which of the following should the Chief Security Officer (CSO) perform before signing off on the third-party vendor?
A company s design team is increasingly concerned about intellectual property theft Members of the team often travel to suppliers' offices where they collaborate and share access to their sensitive data. Which of the following should be implemented?
A large organization suffers a data breach after one staff member inadvertently shares a document on a corporate-approved, file-sharing, cloud-collaboration service. The security administrator must implement controls to reduce the likelihood of a similar event, via another channel, from occurring again. The controls also must assist with early detection and remediation should the event reoccur.
The organization has the following enterprise constraints:
1. On-premises proxies are used to control access to websites.
2 Some staff work remotely from home and connect directly to the Internet without a VPN.
3. Corporate firewalls send logs to a central log aggregator.
4. More than 40,000 staff members are distributed across two core buildings and 100 small branches.
Which of the following would BEST meet the requirements? (Select THREE).
A corporation with a BYOO policy is very concerned about issues that may arise from data ownership. The corporation is investigating a new MOM solution and has gathered the following requirements as part of the requirements-gathering phase
• Each device must be issued a secure token of trust from the corporate PKl
• Al corporate applications and local data must be able to be deleted from a central console.
• Access to corporate data must be restricted on international travel
• Devices must be on the latest OS version within three weeks of an OS release
Which of the following should be features in the new MDM solution to meet these requirements? (Select TWO)
A company protects privileged accounts by using hardware keys as a second factor. A security engineer receives an error while attempting to authenticate with a hardware key for the first time. The engineer confirms the credentials are valid by logging Into a system while MFA is disabled. Which of the following is the MOST likely reason the login is failing?
An engineering team is developing and deploying a fleet of mobile devices to be used for specialized inventory management purposes. These devices should:
* Be based on open-source Android for user familiarity and ease.
* Provide a single application for inventory management of physical assets.
* Permit use of the camera be only the inventory application for the purposes of scanning
* Disallow any and all configuration baseline modifications.
* Restrict all access to any device resource other than those requirement ?
Over the last 90 days, many storage services has been exposed in the cloud services environments, and the security team does not have the ability to see is creating these instance. Shadow IT is creating data services and instances faster than the small security team can keep up with them. The Chief information security Officer (CIASO) has asked the security officer (CISO) has asked the security lead architect to architect to recommend solutions to this problem.
Which of the following BEST addresses the problem best address the problem with the least amount of administrative effort?
A factory-floor system uses critical legacy, and unsupported application software to enable factory operations A latent vulnerability was recently exposed, which permitted attackers to send a specific string of characters followed by arbitrary code for execution Patches are unavailable, as the manufacturer is no longer m business Which of the following would be the BEST approach the company should take to mitigate the risk of this vulnerability and other latent vulnerability exploits'' (Select TWO)
The Chief information Officer (CIO) wants to establish a non-banding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a format partnership. Which of the follow would MOST likely be used?
Company policy mandates the secure disposal of sensitive data at the end of the useful lifespan of IT equipment. The IT department donates old devices to charity and recycles truly obsolete equipment In addition to deleting workstations from the systems responsible for monitoring network connections which of the following actions should the company implement? (Select TWO)
A security engineer is performing a routine audit of a company's decommissioned devices. The current process involves a third-party firm removing the hard drive from a company device, wiping it using a seven-pass software placing it back into the device and tagging the device for reuse or disposal. The audit reveals sensitive information is present m the hard drive duster tips. Which of the following should the third-party firm implement NEXT to ensure all data is permanently removed''
An aircraft manufacturer is developing software that will perform automatic flight control (auto-pilot) Given the high safety criticality of the software the developer can BEST prove software correctness to a requirement’s specification by employing:
The Chief Information Security Officer (CISO) developed a robust plan to address both internal and external vulnerabilities due to an increase in ransomware attacks on the networks However the number of successful attacks continues to increase. Which of the following is the MOST likely failure?
A security engineer needs (o implement controls that will prevent the theft of data by insiders who have valid credentials Recent modems were earned out with mobile and wearable devices that were used as transfer vectors In response USB data transfers are now tightly controlled and require executive authorization Which of the following controls will further reduce the likelihood of another data theft?
A major OS vendor implements an IDE-integrated tool that alerts developers on the use of insecure and deprecated C code functions Using which of the following functions would yield an alert to the developer?
A cloud architect is moving a distributed system to an external cloud environment. The company must be able to
•Administer the server software at OS and application levels
• Show the data being stored is physically separated from other tenants
• Provide remote connectivity for MSSPs
Which of the following configurations and architectures would BEST support these requirements?
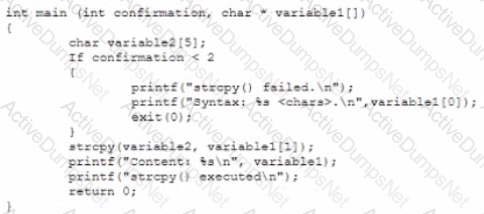
Which of the following vulnerabilities did the analyst uncover?
A company wants to analyze internal network traffic for IOCs. The security solution consists of a network collector appliance and a separate server which security analysts access via a browser to visualize and review the alerts generated from the network traffic. The company uses a collapsed core operating at Layer 2 at 100Gbps. The server win be placed in the datacenter. Which of the following architectures should be used to ensure the solution can provide visibility into all the company's internal network traffic including DNS and URL requests without impacting network traffic flow?
The Chief information Security Officer (CISO) of a small locate bank has a compliance requirement that a third-party penetration test of the core banking application must be conducted annually. Which of the following services would fulfill the compliance requirement with the LOWEST resource usage?
A product owner is working w*h a security engineer to improve the security surrounding certificate revocation which is important for the clients using a web application. The organization is currently using a CRL configuration to manage revocation, but it is looking for a solution that addresses the reporting delays associated with CRLs. The security engineer recommends OCSP but the product owner is concerned about the overhead associated with its use Which of the following would the security engineer MOST likely suggest to address the product owner's concerns?
The Chief Information Security Officer (CISO) of a power generation facility s concerned about being able to detect missing security updates on the critical infrastructure in use at the facility Most of this critical infrastructure consists of ICS and SCADA systems that are maintained by vendors, and the vendors have warned the CISO that proxying network traffic is likely to cause a DoS condition. Which of the following would be BEST to address the CISO s concerns while keeping the critical systems functional?
A company needs to deploy a home assistant that has the following requirement:
1. Revalidate identity when sensitive personal information is accessed and when there is a change m device state. 2 Authenticate every three months and upon registration 3. Support seamless access on all channel
Which of the following actions would be BEST to support the above requirements securely? (Select TWO).
A security analyst is classifying data based on input from data owners and other stakeholders. The analyst has identified three data types:
The analyst proposes that the data be protected in two major groups, with further access control separating the financially sensitive data from the sensitive project data. The normal project data will be stored in a separate, less secure location. Some stakeholders are concerned about the recommended approach and insist that commingling data from different sensitive projects would leave them vulnerable to industrial espionage.
Which of the following is the BEST course of action for the analyst to recommend?
A Chief Information Security Officer (CISO) recently changed jobs into a new industry. The CISO’s first task is to write a new, relevant risk assessment for the organization. Which of the following help to the CISO find relevant risks to the organization? (Choose two.)
An organization is moving internal core data-processing functions related to customer data to a global public cloud provider that uses aggregated services from other partner organizations. Which of the following compliance issues will MOST likely be introduced as a result of the migration?
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded and unmanaged HVAC controller, which is used to monitor the company's datacenter
Port state
161/UDP open
162/UDP open
163/TCP open
The enterprise monitoring service requires SNMP and SNMPTRAP connectivity to operate. Which of the following should the security administrator implement to harden the system?
Staff members are reporting an unusual number of device thefts associated with time out of the office. Thefts increased soon after the company deployed a new social networking app. Which of the following should the Chief Information Security Officer (CISO) recommend implementing?
A remote user reports the inability to authenticate to the VPN concentrator. During troubleshooting, a security administrate captures an attempted authentication and discovers the following being presented by the user's VPN client:
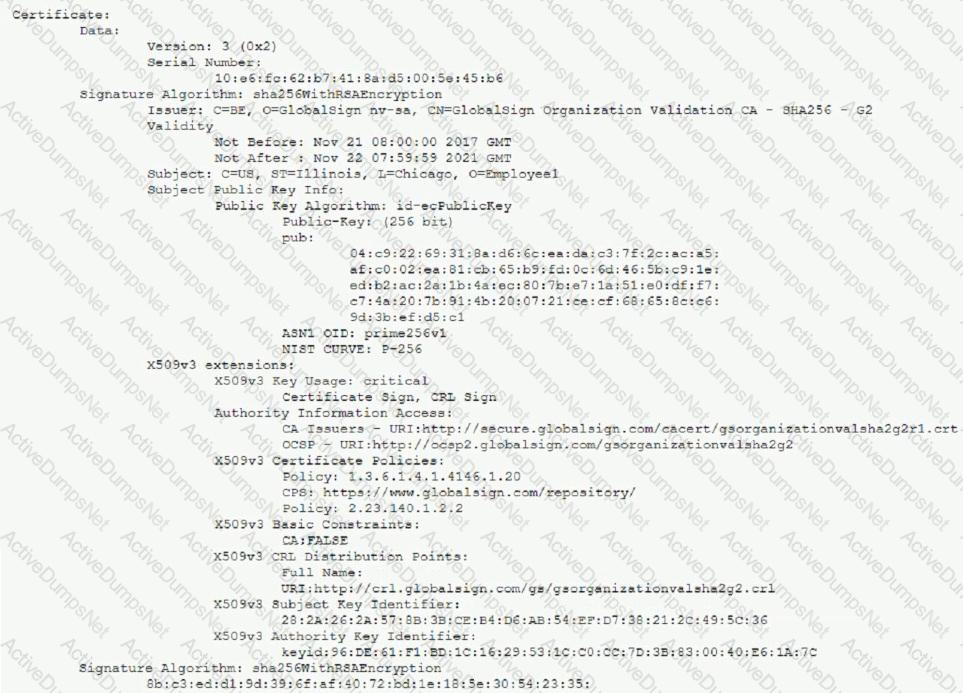
Which of the following BEST describes the reason the user is unable to connect to the VPN service?
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created.
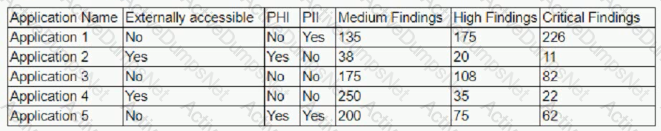
The findings are then categorized according to the following chart:
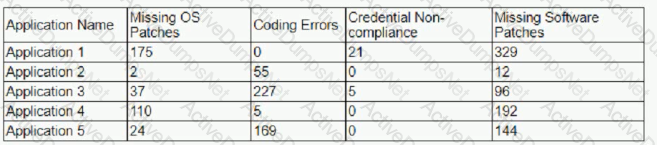
Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Select TWO)
A company’s user community is being adversely affected by various types of emails whose authenticity cannot be trusted. The Chief Information Security Officer (CISO) must address the problem.
Which of the following solutions would BEST support trustworthy communication solutions?
Which of the following is a feature of virtualization that can potentially create a single point of failure?
A corporate forensic investigator has been asked to acquire five forensic images of an employee database application. There are three images to capture in the United States, one in the United Kingdom, and one in Germany. Upon completing the work, the forensics investigator saves the images to a local workstation. Which of the following types of concerns should the forensic investigator have about this work assignment?
A manufacturing company's security engineer is concerned a remote actor may be able to access the ICS that is used to monitor the factory lines. The security engineer recently proposed some techniques to reduce the attack surface of the ICS to the Chief Information Security Officer (CISO). Which of the following would BEST track the reductions to show the CISO the engineer's plan is successful during each phase?
First responders, who are part of a core incident response team, have been working to contain an outbreak of ransomware that also led to data loss in a rush to isolate the three hosts that were calling out to the NAS to encrypt whole directories, the hosts were shut down immediately without investigation and then isolated. Which of the following were missed? (Choose two.)
An analyst is investigating behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the “compose” window.
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
A security administrator is updating a company’s SCADA authentication system with a new application. To ensure interoperability between the legacy system and the new application, which of the following stakeholders should be involved in the configuration process before deployment? (Choose two.)
A networking administrator was recently promoted to security administrator in an organization that handles highly sensitive data. The Chief Information Security Officer (CISO) has just asked for all IT security personnel to review a zero-day vulnerability and exploit for specific application servers to help mitigate the organization’s exposure to that risk. Which of the following should the new security administrator review to gain more information? (Choose three.)
A cybersecurity analyst has received an alert that well-known "call home" messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the massages. After determining the alert was a true positive, which of the following represents OST likely cause?
Company leadership believes employees are experiencing an increased number of cyber attacks; however, the metrics do not show this. Currently, the company uses “Number of successful phishing attacks” as a KRI, but it does not show an increase.
Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
After an employee was terminated, the company discovered the employee still had access to emails and attached content that should have been destroyed during the off-boarding. The employee’s laptop and cell phone were confiscated and accounts were disabled promptly. Forensic investigation suggests the company’s DLP was effective, and the content in question was not sent outside of work or transferred to removable media. Personality owned devices are not permitted to access company systems or information.
Which of the following would be the MOST efficient control to prevent this from occurring in the future?
A Chief Information Security Officer (CISO) implemented MFA for all accounts in parallel with the BYOD policy. After the implementation, employees report the increased authentication method is causing increased time to tasks. This applies both to accessing the email client on the workstation and the online collaboration portal. Which of the following should be the CISO implement to address the employees’ concerns?
A technician uses an old SSL server due to budget constraints and discovers performance degrades dramatically after enabling PFS The technician cannot determine why performance degraded so dramatically A newer version of the SSL server does not suffer the same performance degradation. Performance rather than security is the main priority for the technician
The system specifications and configuration of each system are listed below:
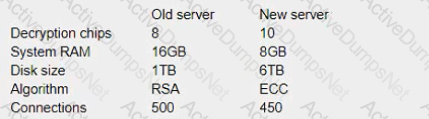
Which of the following is MOST likely the cause of the degradation in performance and should be changed?
A penetration tester is trying to gain access to a remote system. The tester is able to see the secure login page and knows one user account and email address, but has not yet discovered a password.
Which of the following would be the EASIEST method of obtaining a password for the known account?
A Chief Information Security Officer (CISO) needs to establish a KRI for a particular system. The system holds archives of contracts that are no longer in use. The contracts contain intellectual property and have a data classification of non-public. Which of the following be the BEST risk indicator for this system?
An organization is integrating an ICS and wants to ensure the system is cyber resilient. Unfortunately, many of the specialized components are legacy systems that cannot be patched. The existing enterprise consists of mission-critical systems that require 99.9% uptime. To assist in the appropriate design of the system given the constraints, which of the following MUST be assumed?
A company’s security policy states any remote connections must be validated using two forms of network-based authentication. It also states local administrative accounts should not be used for any remote access. PKI currently is not configured within the network. RSA tokens have been provided to all employees, as well as a mobile application that can be used for 2FA authentication. A new NGFW has been installed within the network to provide security for external connections, and the company has decided to use it for VPN connections as well. Which of the following should be configured? (Choose two.)
A manufacturing company employs SCADA systems to drive assembly lines across geographically dispersed sites. Therefore, the company must use the Internet to transport control messages and responses. Which of the following architectural changes when integrated will BEST reduce the manufacturing control system's attack surface? (Select TWO)
Designing a system in which only information that is essential for a particular job task is allowed to be viewed can be accomplished successfully by using:
Following the successful response to a data-leakage incident, the incident team lead facilitates an exercise that focuses on continuous improvement of the organization’s incident response capabilities. Which of the following activities has the incident team lead executed?
A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices.
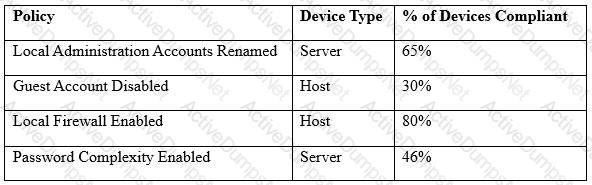
Which of the following tools is the security engineer using to produce the above output?
A recent CRM upgrade at a branch office was completed after the desired deadline. Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded.
Which of the following should be used to identify weak processes and other vulnerabilities?
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.
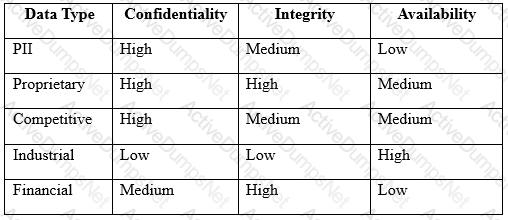
Based on the data classification table above, which of the following BEST describes the overall classification?
The legal department has required that all traffic to and from a company’s cloud-based word processing and email system is logged. To meet this requirement, the Chief Information Security Officer (CISO) has implemented a next-generation firewall to perform inspection of the secure traffic and has decided to use a cloud-based log aggregation solution for all traffic that is logged. Which of the following presents a long-term risk to user privacy in this scenario?
An organization is considering the use of a thin client architecture as it moves to a cloud-hosted environment. A security analyst is asked to provide thoughts on the security advantages of using thin clients and virtual workstations. Which of the following are security advantages of the use of this combination of thin clients and virtual workstations?
A recent assessment identified that several users’ mobile devices are running outdated versions of endpoint security software that do not meet the company’s security policy. Which of the following should be performed to ensure the users can access the network and meet the company’s security requirements?
An organization wants to arm its cybersecurity defensive suite automatically with intelligence on zero-day threats shortly after they emerge. Acquiring tools and services that support which of the following data standards would BEST enable the organization to meet this objective?
The marketing department has developed a new marketing campaign involving significant social media outreach. The campaign includes allowing employees and customers to submit blog posts and pictures of their day-to-day experiences at the company. The information security manager has been asked to provide an informative letter to all participants regarding the security risks and how to avoid privacy and operational security issues. Which of the following is the MOST important information to reference in the letter?
The Chief Information Officer (CIO) wants to increase security and accessibility among the organization’s cloud SaaS applications. The applications are configured to use passwords, and two-factor authentication is not provided natively. Which of the following would BEST address the CIO’s concerns?
After the departure of a developer under unpleasant circumstances, the company is concerned about the security of the software to which the developer has access. Which of the following is the BEST way to ensure security of the code following the incident?
An SQL database is no longer accessible online due to a recent security breach. An investigation reveals that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent this type of breach in the future, which of the following security controls should be put in place before bringing the database back online? (Choose two.)
The director of sales asked the development team for some small changes to increase the usability of an application used by the sales team. Prior security reviews of the code showed no significant vulnerabilities, and since the changes were small, they were given a peer review and then pushed to the live environment. Subsequent vulnerability scans now show numerous flaws that were not present in the previous versions of the code. Which of the following is an SDLC best practice that should have been followed?
Following a security assessment, the Chief Information Security Officer (CISO) is reviewing the results of the assessment and evaluating potential risk treatment strategies. As part of the CISO’s evaluation, a judgment of potential impact based on the identified risk is performed. To prioritize response actions, the CISO uses past experience to take into account the exposure factor as well as the external accessibility of the weakness identified.
Which of the following is the CISO performing?
A Chief Information Security Officer (CISO) is reviewing the controls in place to support the organization’s vulnerability management program. The CISO finds patching and vulnerability scanning policies and procedures are in place. However, the CISO is concerned the organization is siloed and is not maintaining awareness of new risks to the organization. The CISO determines systems administrators need to participate in industry security events. Which of the following is the CISO looking to improve?
Given the code snippet below:

Which of the following vulnerability types in the MOST concerning?
An organization is currently performing a market scan for managed security services and EDR capability. Which of the following business documents should be released to the prospective vendors in the first step of the process? (Select TWO).
As a result of an acquisition, a new development team is being integrated into the company. The development team has BYOD laptops with IDEs installed, build servers, and code repositories that utilize SaaS. To have the team up and running effectively, a separate Internet connection has been procured. A stand up has identified the following additional requirements:
1. Reuse of the existing network infrastructure
2. Acceptable use policies to be enforced
3. Protection of sensitive files
4. Access to the corporate applications
Which of the following solution components should be deployed to BEST meet the requirements? (Select three.)
A recent penetration test identified that a web server has a major vulnerability. The web server hosts a critical shipping application for the company and requires 99.99% availability. Attempts to fix the vulnerability would likely break the application. The shipping application is due to be replaced in the next three months. Which of the following would BEST secure the web server until the replacement web server is ready?
After significant vulnerabilities and misconfigurations were found in numerous production web applications, a security manager identified the need to implement better development controls.
Which of the following controls should be verified? (Select two).
A security technician receives a copy of a report that was originally sent to the board of directors by the Chief Information Security Officer (CISO).
The report outlines the following KPVKRI data for the last 12 months:
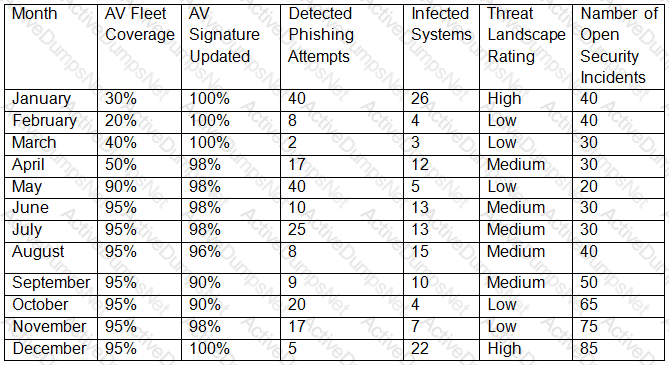
Which of the following BEST describes what could be interpreted from the above data?
A security consultant is attempting to discover if the company is utilizing databases on client machines to store the customer data. The consultant reviews the following information:
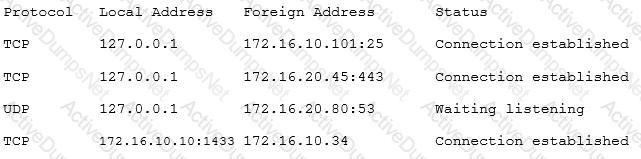
Which of the following commands would have provided this output?
The Chief Information Security Officer (CISO) suspects that a database administrator has been tampering with financial data to the administrator’s advantage. Which of the following would allow a third-party consultant to conduct an on-site review of the administrator’s activity?
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization’s file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system.
Which of the following is MOST likely to be reviewed during the assessment? (Select two.)
A Chief Information Security Officer (CISO is reviewing and revising system configuration and hardening guides that were developed internally and have been used several years to secure the organization’s systems. The CISO knows improvements can be made to the guides.
Which of the following would be the BEST source of reference during the revision process?
A server (10.0.0.2) on the corporate network is experiencing a DoS from a number of marketing desktops that have been compromised and are connected to a separate network segment. The security engineer implements the following configuration on the management router:
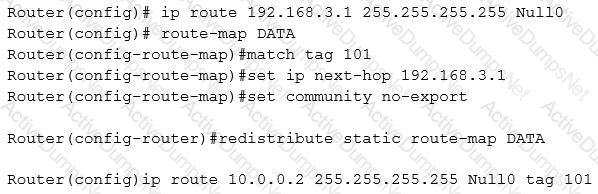
Which of the following is the engineer implementing?
Several days after deploying an MDM for smartphone control, an organization began noticing anomalous behavior across the enterprise Security analysts observed the following:
• Unauthorized certificate issuance
• Access to mutually authenticated resources utilizing valid but unauthorized certificates
• Granted access to internal resources via the SSL VPN
To address the immediate problem security analysts revoked the erroneous certificates. Which of the following describes the MOST likely root cause of the problem and offers a solution?
A security administrator is performing an audit of a local network used by company guests and executes a series of commands that generates the following output:
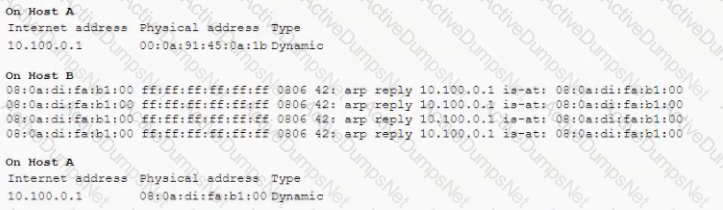
Which of the following actions should the security administrator take to BEST mitigate the issue that transpires from the above information?
Users have reported that an internally developed web application is acting erratically, and the response output is inconsistent. The issue began after a web application dependency patch was applied to improve security. Which of the following would be the MOST appropriate tool to help identify the issue?
The Chief Executive Officer (CEO) of a company has considered implementing a cost-saving measure that
might result in new risk to the company. When deciding whether to implement this measure, which of the
following would be the BEST course of action to manage the organization’s risk?
Which of the following may indicate a configuration item has reached end-of-life?
A security analyst is comparing two virtual servers that were bum from the same image and patched at the same regular intervals Server A is used to host a public-facing website, and Server B runs accounting software inside the firewalled accounting network. The analyst runs the same command and obtains the following output from Server A and Server B. respectively:
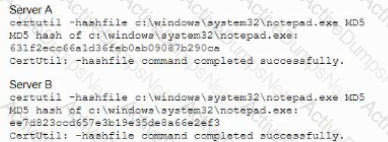
Which of the following will the analyst most likely use NEXT?
A financial services company wants to migrate its email services from on-premises servers to a cloud-based email solution. The Chief information Security Officer (CISO) must brief board of directors on the potential security concerns related to this migration. The board is concerned about the following.
* Transactions being required by unauthorized individual
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attacker using email to distribute malware and ransom ware.
* Exfiltration of sensitivity company information.
The cloud-based email solution will provide an6-malware, reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the board’s concerns for this email migration?
A penetration tester is given an assignment lo gain physical access to a secure facility with perimeter cameras. The secure facility does not accept visitors and entry is available only through a door protected by an RFID key and a guard stationed inside the door Which of the following would be BEST for the penetration tester to attempt?
An organization is creating requirements for new laptops that will be issued to staff One of the company's key security objectives is to ensure the laptops nave hardware-enforced data-at-rest protection tied to permanent hardware identities. The laptops must also provide attestation for secure boot processes To meet these demands, which of the following BEST represent the features that should be included in the requirements set? (Select TWO.)
A company’s IT department currently performs traditional patching, and the servers have a significant longevity that may span over five years. A security architect is moving the company toward an immune server architecture in which servers are replaced rather than patched. Instead of having static servers for development, test, and production, the severs will move from environment to environment dynamically. Which of the following are required to move to this type of architecture? (Select Two.)
A company requires a task to be carried by more than one person concurrently. This is an example of:
A developer has executed code for a website that allows users to search for employees’ phone numbers by last
name. The query string sent by the browser is as follows:
http://www.companywebsi te.com/search.php?q=SMITH
The developer has implemented a well-known JavaScript sanitization library and stored procedures, but a
penetration test shows the website is vulnerable to XSS. Which of the following should the developer implement
NEXT to prevent XSS? (Choose two.)
A security manager wants to implement a policy that will management with the ability to monitor employees’ activities with minimum impact to productivity. Which of the following policies Is BEST suited for this scenario?
A system administrator recently conducted a vulnerability scan of the internet. Subsequently, the organization was successfully attacked by an adversary. Which of the following in the MOST likely explanation for why the organization network was compromised?
Following the merger of two large companies the newly combined security team is overwhelmed by the volume of logs flowing from the IT systems The company's data retention schedule complicates the issue by requiring detailed logs to be collected and available for months. Which of the following designs BEST meets the company's security and retention requirement?
A small company needs to reduce its operating costs. vendors have proposed solutions, which all focus on management of the company’s website and services. The Chief information Security Officer (CISO) insist all available resources in the proposal must be dedicated, but managing a private cloud is not an option. Which of the following is the BEST solution for this company?
Following the most recent patch deployment, a security engineer receives reports that the ERP application is no longer accessible. The security engineer reviews the situation and determines a critical security patch that was applied to the ERP server is the cause. The patch is subsequently backed out Which of the following security controls would be BEST to implement to mitigate the threat caused by the missing patch?
A company in the financial sector receives a substantial number of customer transaction requests via email. While doing a root-cause analysis conceding a security breach, the CIRT correlates an unusual spike in port 80 traffic from the IP address of a desktop used by a customer relations employee who has access to several of the compromised accounts. Subsequent antivirus scans of the device do not return an findings, but the CIRT finds undocumented services running on the device. Which of the following controls would reduce the discovery time for similar in the future.
A financial institution would like to store its customer data in a cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would BEST meet the requirement?
A company recently experienced a period of rapid growth, and it now needs to move to a more scalable cloud-based solution Historically. salespeople have maintained separate systems for information on competing customers to prevent the inadvertent disclosure of one customer's information to another customer Which of the following would be the BEST method to provide secure data separation?
A developer implement the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?
A security administrator wants to implement an MDM solution to secure access to company email and files in a BYOD environment. The solution must support the following requirements:
* Company administrators should not have access to employees' personal information.
* A rooted or jailbroken device should not have access to company sensitive information.
Which of the following BEST addresses the associated risks?
A new security policy slates all wireless and wired authentication must include the use of certificates when connecting to internal resources within the enterprise LAN by all employees Which of the following should be configured to comply with the new security policy? (Select TWO).
A company suspects a web server may have been infiltrated by a rival corporation. The security engineer reviews the web server logs and finds the following:

The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run:
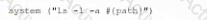
Which of the following is an appropriate security control the company should implement?