A desktop technician is responsible for the OS migration of 300 end users. As part of the migration, the technician must save the end users* data to a temporary shared drive. The data must include any hidden files to ensure 100% of the data is retained. Which of the following commands will achieve this result by default?
The medical records department of a local hospital recently upgraded its computers. A technician needs to ensure the data stored on the hard drives is unrecoverable. Which of the following methods should the technician use to meet the requirement?
Which of the following uses a remote access server to forward a user's logon password to an authentication server, allowing or denying access to a system?
A systems administrator creates a new folder in the user profile. The administrator wants it to have different NTFS permissions than its parent folder. Which of the following settings should the administrator change?
A technician needs to connect to a network switch in a remote location. The technician wants to make sure the data passed over the wire is encrypted so it cannot be read by someone using a sniffer. Which of the following connection protocols should the technician use?
A user is working on a shared computer and attempts to open the email application, which freezes when opened. A technician logs into the computer, and the email application works without issue. The technician has the user log back in, but the application still freezes when opened. Which of the following is the NEXT step the technician should take to resolve the issue?
A technician is attempting to recover data from a damaged laptop that was running Windows 10. The technician removes the drive and places it in a known-good computer. The computer boots and sees the drive, but no data is displayed. Which of the following is the reason the technician is experiencing this issue?
A technician must manually modify the HOSTS system file in order to resolve a website address to a specified
local destination. Which of the following utilities should the technician use to BEST accomplish the task?
A technician is in the process of removing a recently discovered Trojan horse application from a users laptop. Which of the following should the technician complete to prevent reinfection of the same machine?
A technician needs to manage a Linux workstation remotely. This workstation contains highly sensitive data, and therefore, it must be accessed in the most secure method possible Which of the following technologies should the technician use to manage this system?
An application is installed and configured locally on a workstation, but it writes all the save files to a different workstation on the network. Which of the following accurately describes the configuration of the application?
A Chief Executive Officer (CEO) is giving a presentation at an industry conference but forgot to bring a laptop. The company has emailed several large presentation files and the links to several videos that will be streamed during the presentation. While showing the last video, it starts to buffer, times out. and will not display The CEO restarts the phone that is being used for the presentation and verifies there is enough free storage space, but the video still will not play Which of the following is MOST likely causing the Issue?
A user is surprised that a newly installed third-party smartphone application requires permissions to access the camera, location, and microphone. Unaware of a reason why permissions are needed for the application to function as advertised, the user contacts the help desk for assistance. Which of the following should the help desk team recommend the user do in this situation?
Several users at an office have noticed their computers have been behaving erratically over the past hour. A technician suspects there may be a network worm or a hardware failure because all the affected computers were purchased together. Which of the following should the technician perform FIRST?
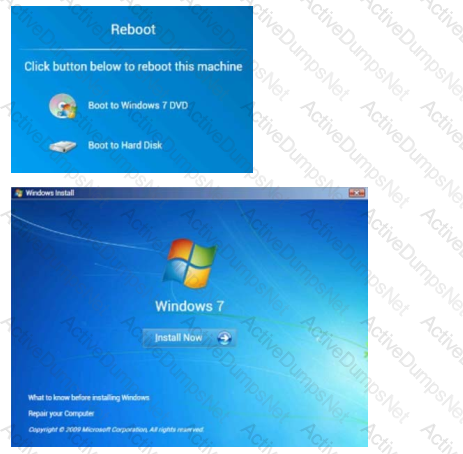
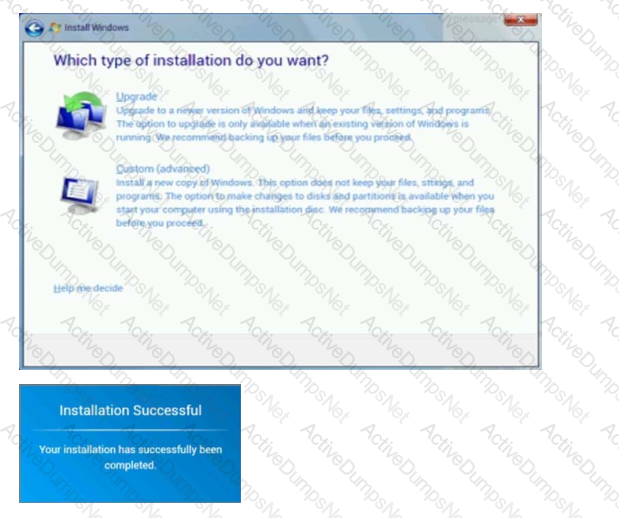
A Windows 7 machine appears to have a failure. Every time it is rebooted, the message “BOOTMGR is missing” appears.
You have previously inserted a Windows 7 installation DVD into the DVD-ROM.D18912E1457D5D1DDCBD40AB3BF70D5D
Please repair this failure without overwriting the customers’ local user profiles.
INSTRUCTIONS
Use the Windows recovery and repair utilities to remediate the issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A technician is having issues with the WiFi connection while working on a Mac. The technician wants to check which SSID the computer is connected to and some statistics about the connection. Which of the following terminal commands should the technician use?
A security administrator does some network testing and identifies significant issues with security on desktop computers. As part of remediation, the network administrator is developing documentation based on best practices for applying updates to end users’ computers. The network administrator must create the process documentation needed to submit back to the security administrator for approval. Which of the following process documents would the network administrator MOST likely create? (Choose two.)
A user updated an iOS smartphone and is now having issues connecting to the Internet. The phone shows 1x for signal strength while making calls. Which of the following are the MOST likely causes of these issues?
(Choose two.)
Ann, a network engineer, wants to use FTP to back up and push configurations to several switches she is updating. Ann starts the FTP service on her PC and places the new configuration in the correct directory. However, she cannot communicate with the PC using FTP from the switch. Which of the following must Ann do to allow FTP communications?
A SOHO user calls a technician and wants to secure a home network. The SOHO user needs to have protection from physical connections and ensure that employees cannot access applications or personal emails. Which of the following would the technician MOST likely configure on the new network device to accommodate this SOHO user’s request? (Select TWO).
A user is staying at a hotel that only offers Fast Ethernet connectivity to the network. The user’s laptop is
currently using the corporate network for access to network resources as well as the cloud. Which of the
following should the help desk recommend performing prior to using the hotel network?
A workstation needs to be hardened against brute force attacks. It also needs to be protected if a user walks away and leaves the computer unlocked. Which of the following would harden the workstation as required? (Select TWO).
A technician receives a call from an end user in the human resources department who needs to load an older stand-alone application on a computer to retrieve employee information. The technician explains the application can be run in compatibility mode, but it will need to be removed as soon as the user obtains the required information. Which of the following BEST describes the technician’s concern with loading this application on the user’s computer?
Ann, an end user, is utilizing a stylus on her tablet. The recognition point is off when she uses the stylus, but it registers in the correct spot when she uses her finger.
Which of the following would be the BEST resolution to Ann’s issue?
A technician wants to deploy a solution to manage a computer remotely. The technician is not allowed to modify any network configuration and is not able to forward any ports on the router to internal devices. Which of the following remote access technologies would be BEST suited for this situation?
A customer recently lost data because it was accidentally deleted The customer calls a technician and asks to have a Windows backup solution installed The customer needs to ensure all company data is backed up and quickly recoverable every time a change Is made. Which of the following solutions would the technician MOST likely recommend? (Select TWO)
A technician is securing a server room by implementing a two-factor authentication solution Which of the following should the technician implement to provide the BEST security for the server room?
A home user reports slow computer performance and application crashes after clicking a "repair" button on a pop-up warning while browsing the Internet Which of the following are the FIRST steps a technician should take to identify and resolve the issue? (Select TWO).
During a network server outage, the administrators computer received an IP address of 169.254.0.10 and had no access to internal or external resources. Which of the following should be configured to ensure the administrator's computer retains network access?
The IT department has installed new software in the folder C:\Program Files\Business Application\. Ann, a user, runs the business application and tries to save her work. When doing so, Ann receives the following error:
Cannot save file C: \Program Files\Business Application\file1.wrk – Access is denied.
Which of the following would be the MOST secure solution to this error?
Which of the following steps should a technician perform when the Included Windows driver for a video card does not have the needed features?
A technician is alerted to a virus on a PC. The technician isolates the PC from the network. After verifying there are no other infected PCs on the network, which of the following is the SAFEST method for the technician to use to clean the infected PC?
Joe, a user, believes his computer is infected with malware. The device is having difficulty accessing some
websites, and web services are not responding from any of the web browsers, although Joe can access these
services from his smartphone without issue. The computer’s malware scanner has the latest definitions
installed. Which of the following would BEST explain why the computer is functioning this way?
Which of the following is the MOST common method of allowing outside access through a wireless SOHO router for specific program access?
Which of the following is a Device that stores a copy of a certificate that is used for authentication?
A technician is setting up network adapter settings on Windows clients that have static IP address assignments. The technician has more than 100 workstation to complete and wants to automate the process. The requirements for the adapter settings are as follows:
* They must utilize a command line utility
* The technician has no access to Group Policy
* All workstation should have an IP address assigned by the DHCP.
Which of the following steps should the technician perform to meet these requirements?
Ann, a user, has asked technician for help with her computer. Ann has been trying to speed it up with simple Upgrades but has not been successful. She added memory and removed unnecessary applications that were no longer in use. After removing the applications, however, the computer seemed to get slower. Which of the following is the BEST solution?
A technician is selling up a new virtualization server which will be initially used to host a client VM that will manage print jobs. The client, however, has future plans lo utilize the server to host other VMs. Which of the following should the technician implement to ensure maximum uptime of the client VM?
A company recently experienced a security incident in which an unauthorized user was able to insert a USB flash drive into a kiosk, launch a non-native OS. and deliver malicious payloads across the network. Which of the following security measures would have been BEST to prevent the attack from being executed in the first place' (Select TWO)
A technician is removing a virus from a user’s Windows workstation. The virus was installed by the user while downloading pirated software from the Internet. Which of the following should the technician do to address this issue?
Which of the following would MOST likely be connected to a computer Id provide electricity in case of a blackout?
A technician encounters a previously unidentified issue. The technician conducts some research, finds a solution, and resolves the issue. According to best practices, which of the following should the technician do so the issue can be addressed if it is encountered again?
A user’s antivirus recently expired, so the user downloaded and installed a free system protection application. The application found numerous rootkits, Trojans, viruses, and missing critical patches. It was unable to fix all the issues, however, and suggested the user call technical support. Which of the following is the FIRST step to begin repairing the computer?
A help desk technician needs to make administrative changes securely on a remote user's machine. The user must be logged off when the changes are made. Which of the following tools would the technician MOST likely use?
Joe, a mobile device user, reached his monthly quota of data about halfway through the current billing cycle. Joe contacts a technician to identify potential issues with the mobile device, as his usage patterns have not changed over the past month. Which of the following is MOST likely causing this issue?
Joe, a user, did not receive emails over the weekend like he usually does. Productivity software is functioning properly. Joe never powers off his computer and typically leaves all applications open. No other users are reporting
email issues. Which of the following is MOST likely the cause of the issue?
A user cannot print to a network printer. A technician runs the Windows 10 troubleshooting utility, but it does not find any errors. Which of the following printer settings should the technician check NEXT?
Some of a company’s computers were manually configured to bypass the DNS servers for connections to a connections to a fileshare server. A technician needs to ensure at the computers use DNS to reach resources on the network. Which of the following should the technician do to confirm all the computers use only DNS?
A technician notices a workstation is connecting to an IP address on the network and wants to determine the machine name that belongs to that IP address. Which of the following commands should the technician use?
A user's laptop screen goes black after five minutes of not being used. Which of the following Windows Control Panel utilities should be used to modify the user experience?
A systems administrator created a policy that should create a shortcut on a user's desktop Shortly after the policy was created, a technician inspects the user's desktop and notices the shortcut is not present. The administrator verifies that the policy was created correctly and that it is being applied to the user's account. Which of the following will MOST Likely resolve the issue Immediately without interrupting the user's session?
Which of the following would be used to protect technicians from dust particles when they are entering a datacenter located near a construction site?
A technician needs to open a laptop chassis to perform an upgrade. Which of the following procedures must be technician follow FIRST? (Select Two.)
Which of the following is an example of PHI?
An issue with a user's computer was addressed several times by multiple technicians, but the User has continued to experience the issue. The User calls the help desk and insists on speaking to a supervisor; however, the
supervisor is away at lunch. Which of the following should the technician perform FIRST?
An administrator is loading a new Linux server. Which of the following filesystems will the administrator MOST likely select for the primary partition?
A user's desktop icons appear much larger than before, and the display colors look unusual A technician runs hardware diagnostics but finds no issues. The system logs show the update service ran last night; however, no new applications were installed. Which of the following is me BEST solution?
An employee is taking a credit card payment over the phone, but the payment system has a temporary outage. To avoid inconveniencing the customer, the employee writes down the credit card number and expiration date on a notepad to be entered later This is in violation of:
A user tries to open a client/server application, but a prompt appears for the username and password The user is able to open and use the email client with no issues. The user's workstation is a loaner laptop Everyone at the company is given administrator rights on their individual workstations. Which of the following is MOST likely preventing the user from running this program?
A technician needs to format a 64GB flash drive. Which of the following formats will the technician MOST likely use?
A technician needs to make changes to a production system. Before doing so, which of the following should be completed in case the changes have unintended consequences beyond their original scope?
A technician recently built a gaming PC with a multicode CPU, 32GB DDR4 memory, a 1TB SSD. and a high-end GPU The technician installed the OS and a new game but noticed the frame-rate performance was much lower than expected Which of the following should the technician do NEXT to address the performance issues?
A smartphone user has been receiving unsolicited emails that contain Pl in the webmail inbox associated with the device. Which of the following steps should the user take FIRST to identify the cause of the issue?
Which of the following identifies changes in the environment, such as alternating current failure?
An end user contacts the help desk to report a browser issue. When the user selects a hyperlink to a POF file within the browser, nothing happens. The user notes the browser is otherwise working properly. Which of the following should a technician direct the user to do FIRST?
Which of the following is a risk to computer equipment when the humidity is low?
A security team is auditing a company’s network logs and notices that a USB drive was previously inserted into several of the servers. Many login attempts were then successfully performed using common login information.
Which of the following actions should be taken to close the vulnerability? (Select two.)
A technician needs to deploy a remote access technology to be able to access desktop computers. When a technician logs in to a user's computer, the user and the technician must be able to see the desktop simultaneously and use the mouse and keyboard. Which of the following would be BEST suited for this task?
Joe. a technician, receives notification that a share for production data files on the network Is encrypted. Joe suspects a crypto virus Is active. He checks the rights of the network share to see which departments have access. He then searches the user directories of those departmental users who are looking for encrypted files. He narrows his search to a single user's computer. Once the suspected source of the virus is discovered and removed from the network, which of the following should Joe do NEXT?
A user's personal settings are not saving, and a technician suspects the user's local Windows profile is corrupt. The technician wants to check the size of the ntuser.dat file, but It does not appear in the user's profile directory. Which of the following Control Panel utilities should the technician use to correct this?
A user’s smartphone is making the camera shutter noise even when the user is not taking pictures. When the user opens the photo album, there are no new pictures. Which of the following steps should be taken FIRST to determine the cause of the issue?
Corporate management is concerned about the security of the company’s mobile phones, in the event they are lost or stolen. Management instructs the IT staff to ensure the data on the devices is not accessible by unauthorized users. Which of the following would provide the BEST level of protection in this scenario? (Choose two.)
A user is attempting to install an application and receives an error stating there is not enough space to install the application. Which of the following did the user overlook?
Which of the following BEST describes the purpose of an ESD mat?
A small office calls a technician to investigate some “invalid certificate” errors from a concerned user. The technician observes that whenever the user to access a secure website from the Windows desktop, this error is encountered. No other users in the office are experiencing this error. Which of the following should the technician do NEXT? (Choose two.)
Which of the following user types should be used in a Windows environment to grant Internet access without allowing the permanent storage of files on the system?
A technician repaired a laptop for a customer. The customer then complained the repair took too long and questioned the steps the technician took to fix the problem. Which of the following should the technician do NEXT?
Which of the following is a reason to use WEP over WPA?
Which of the following Windows OS technologies is used to store remote data accessed via a WAN connection on local servers for user access?
A network administrator recently learned users have been accessing websites that are restricted based on content by the firewall. To prevent users from circumventing the firewall rules, which of the following Windows settings should the administrator locks to prevent them from being changed?
A systems administrator needs to add security to the server room.
Which of the following would provide the BEST security for the room? (Choose two.)
Joe, a user, returns his computer to the technician who performed a virus removal on it the week before. Joe states that several symptoms have returned.
Which of the following should the technician have covered previously as part of the original repair?
A technician is contacted by a user who is working from home but is unable to connect to any office resources (e.g., files, printers). The user is able to access the Internet.
Which of the following should the technician check FIRST?
A SOHO technician recently moved some data from one server to another to increase storage capacity. Several users are now reporting they cannot access certain shares on the network. When the users attempt to access the shares, they get the following error: Access Denied. The technician confirms the users are all in the proper security groups and have the proper access, but they are still unable to access the shares. Which of the following are the MOST likely reasons for these issues? (Select two.)
Which of the following devices provides protection against brownouts?
Which of the following steps should a technician take FIRST to prevent an electrical hazard when repairing a PC?
A technician is installing the latest OS on a user’s system. The user wants all of the settings and file to remain intact during the installation.
Which of the following upgrade methods should the technician use?
An employee reported that a suspicious individual was looking through the recycle bin. Which of the following types of social engineering threats is this?
While attempting to install a new program, an end user is notified the workstation meets the memory requirements, but it does not meet the requirements for free space. Due to time constraints the user needs a quick way to install and access the program. Which of the following is the BEST option given the solution?
Which of the following can be applied directly to an organizational unit In Active Directory to provide security to both the user and the machine?
Joe, a technician, has his daily plans forwarded to him by his supervisor. Upon arrival to the external to the second support call of the day, Joe realizes the issue will require much more time than initially scheduled, and several support calls will not be completed. Which of the following would be the appropriate action for Joe?
Which of the following should be enacted to reduce a company's liability and exposure to a potential lawsuit?
Which of the following would a technician use to store memory chips from a laptop safely after an upgrade?
Which of the following would MOST likely contain troubleshooting guides?
An end user’s PC is taking a long time to boot. Which of the following operations would be the BEST to resolve this issue with minimal expense? (Select two.)
A technician has identified malware on a user’s system. Which of the following should the technician do NEXT according to malware removal best practices?
A user Is unable to access a network share out can access email. A technician has confirmed the user has the appropriate permissions to access the share. Which of the following commands should the technician use FIRST?
Joe, a customer, calls a technician to report a remote computer is demonstrate erratic behavior while he is working on it. The technician verifies the files and directories Joe is working on locally cannot be open in any application, and the computer is extremely slow. Which of the following is the MOST likely cause of this issue?
Which of the following is the maximum RAM limit of a Windows 32-bit version?